¶ BloodyAD
https://github.com/CravateRouge/bloodyAD
¶ About
This tool can perform specific LDAP/SAMR calls to a domain controller in order to perform AD privesc.
bloodyAD supports authentication using cleartext passwords, pass-the-hash, pass-the-ticket or certificates and binds to LDAP services of a domain controller to perform AD privesc.
It is designed to be used transparently with a SOCKS proxy.
¶ Usage Examples
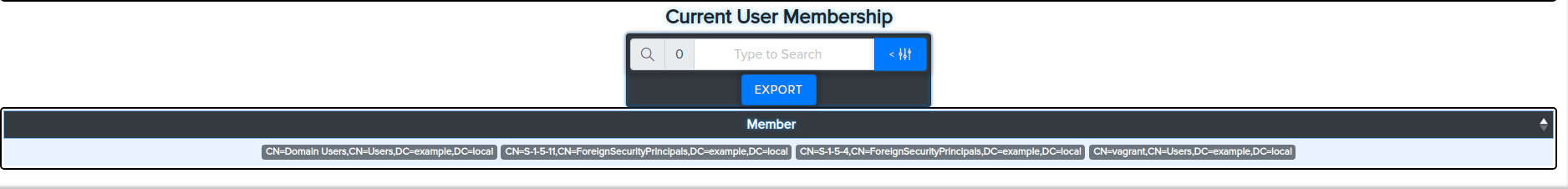
¶ Get current user membership
bloodyAD -u john.doe -d bloody -p Password512! --host 192.168.10.2 getObjectAttributes Users member
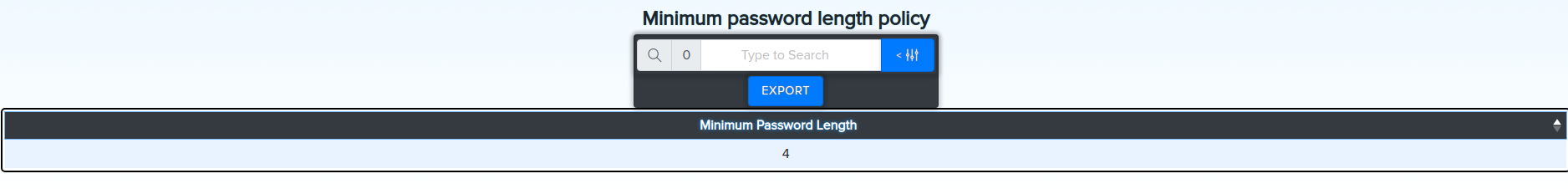
¶ Get minimum password length policy
bloodyAD -u john.doe -d bloody -p Password512! --host 192.168.10.2 getObjectAttributes 'DC=bloody,DC=local' minPwdLength
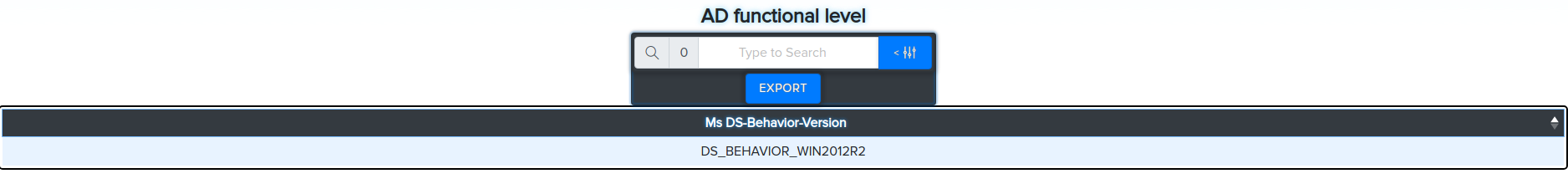
¶ Get AD functional level
bloodyAD -u Administrator -d bloody -p Password512! --host 192.168.10.2 getObjectAttributes 'DC=bloody,DC=local' msDS-Behavior-Version
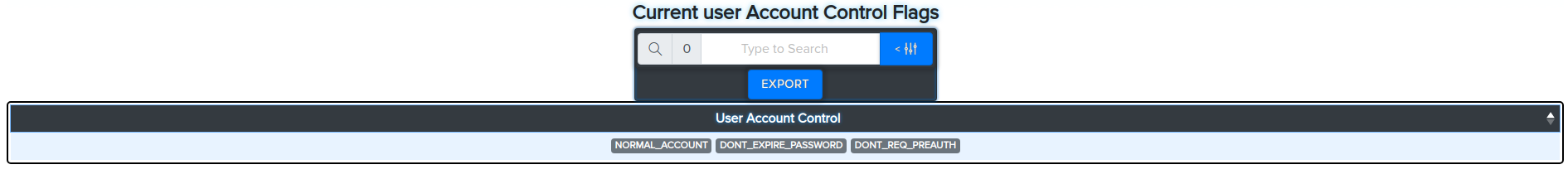
¶ Get UserAccountControl flags
bloodyAD -u Administrator -d bloody -p Password512! --host 192.168.10.2 getObjectAttributes john.doe userAccountControl
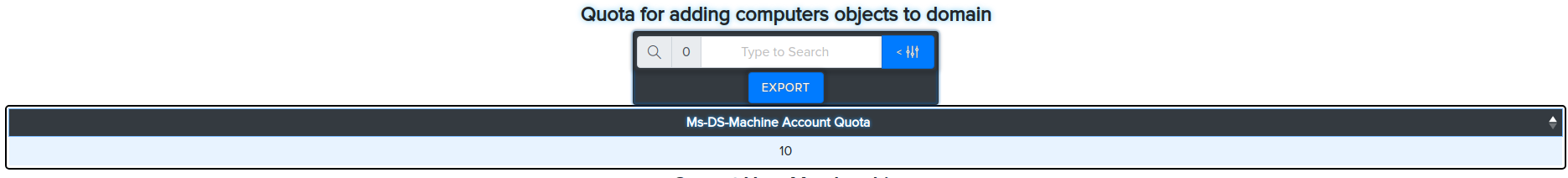
¶ Quota for adding computer objects to domain
bloodyAD -u john.doe -d bloody -p Password512! --host 192.168.10.2 getObjectAttributes 'DC=bloody,DC=local' ms-DS-MachineAccountQuota
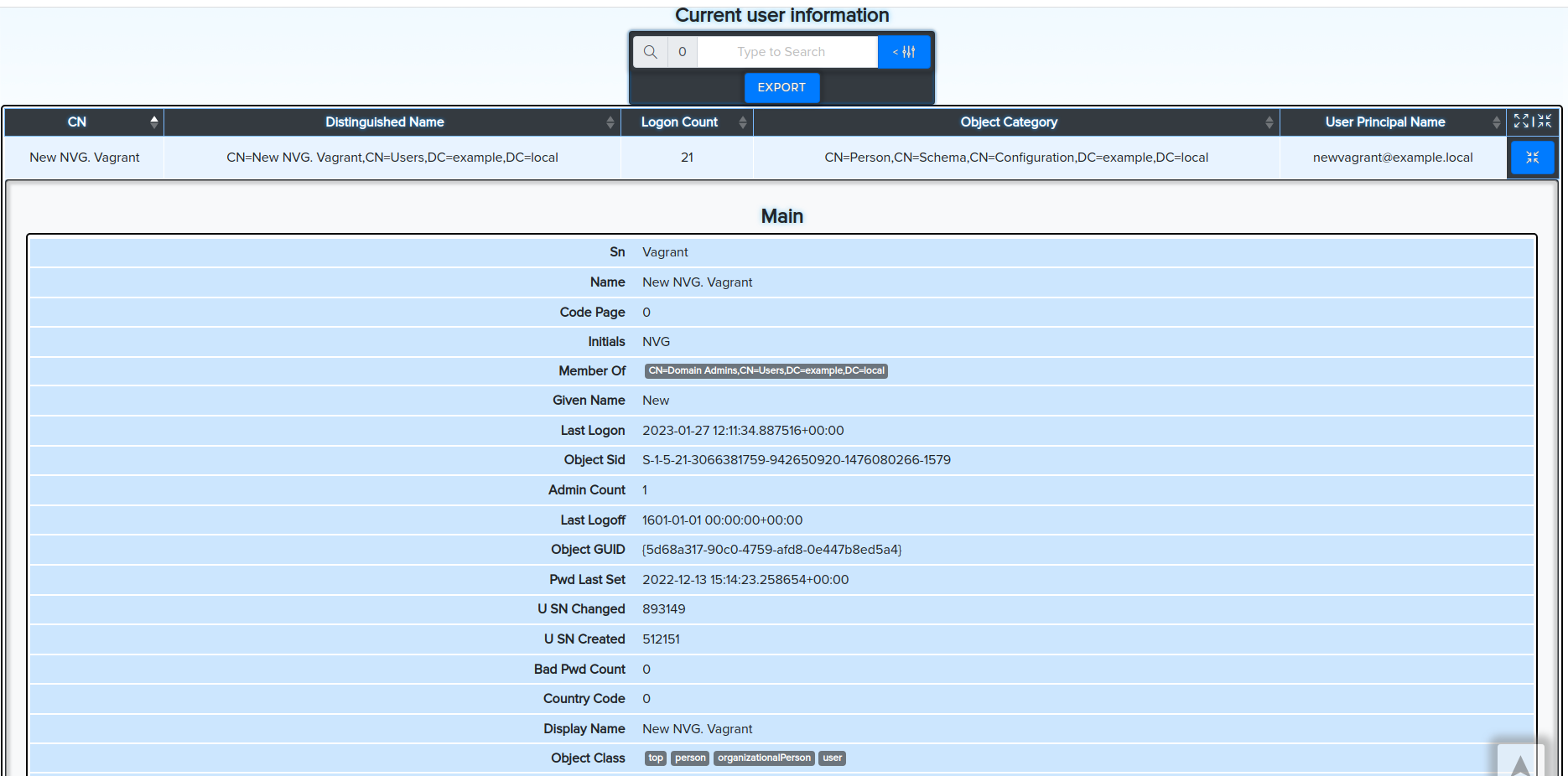
¶ Get current user information
bloodyAD -u john.doe -d bloody -p Password512! --host 192.168.10.2 getObjectAttributes john.doe