¶ Serialator
.____ _ _ _
/ ___| ___ _ __(_) __ _| | __ _| |_ ___ _ __
\___ \ / _ \ '__| |/ _` | |/ _` | __/ _ \| '__|
___) | __/ | | | (_| | | (_| | || (_) | |
|____/ \___|_| |_|\__,_|_|\__,_|\__\___/|_|
During a recent engagement, I found that Nessus was now actively exploiting vulnerabilities for confirmation. When I checked the associated nasl script I found that the payload was generic enough to be used on a standalone script. Hence, I collected the payloads from all the nasl scripts that were part of the same RCE vulnerability (but for separate applications) and wrapped them with Python magic. Next time you see a vulnreable application, use this script.
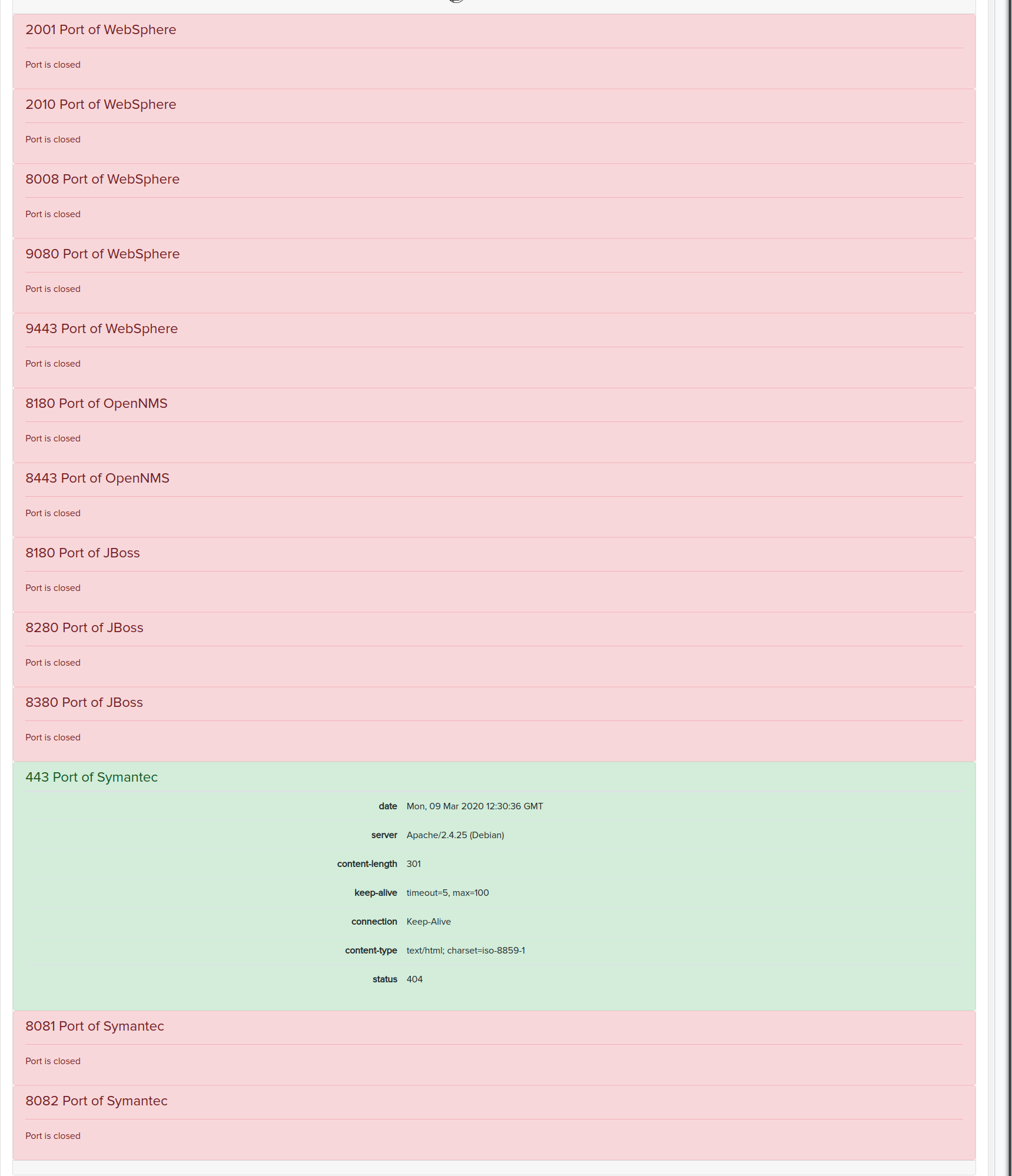
¶ Used facts:
Port 2001, 9443, 9080, 8008, 2010 Websphere
Port 8180, 8443 opennms
Port 8180, 8380, 8280 jboss
Port 443, 8082, 8081 symantec
¶ Screenshots of results:
¶ Category:
Security/Exploit Check
¶ Audit Tags:
¶ DISCLAIMER:
This program is used for educational and ethical purposes only. I take no responsibility for any damages caused from using this program. By downloading and using this software, you agree that you take full responsibility for any damages and liability.