¶ Breach Detection
¶ Breach detection — Briefly about features, modules, and use cases
The main purpose of Breach Detection is to automate the remote breach detection process and alert the user to the potential risk to the asset.
To achieve the purpose, the user is given the opportunity to safely add their assets to the regular monitoring system. For the convenience of using the monitoring system, the user has the ability to configure the frequency of breach detection. If the user deems that monitoring the asset that he has added is no longer practical (useful), the user has the option to delete the corresponding asset.
¶ Frequency of breach detection:
- hour
- day
- week
- month
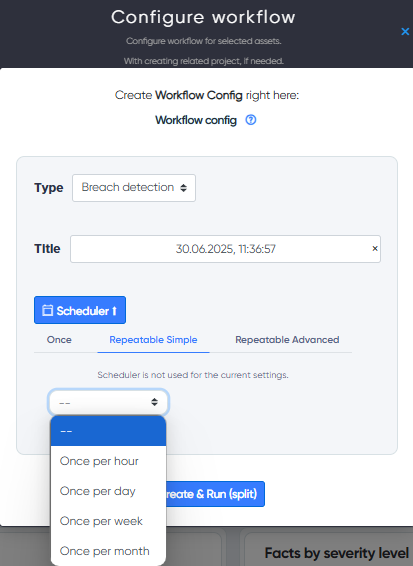
The system has the ability to take action on the results (leaks). This means that the user can make decisions based on the information received and assign a status to the result.
¶ First steps
First of all, you need to add asset from wich you can create a breach detection project.
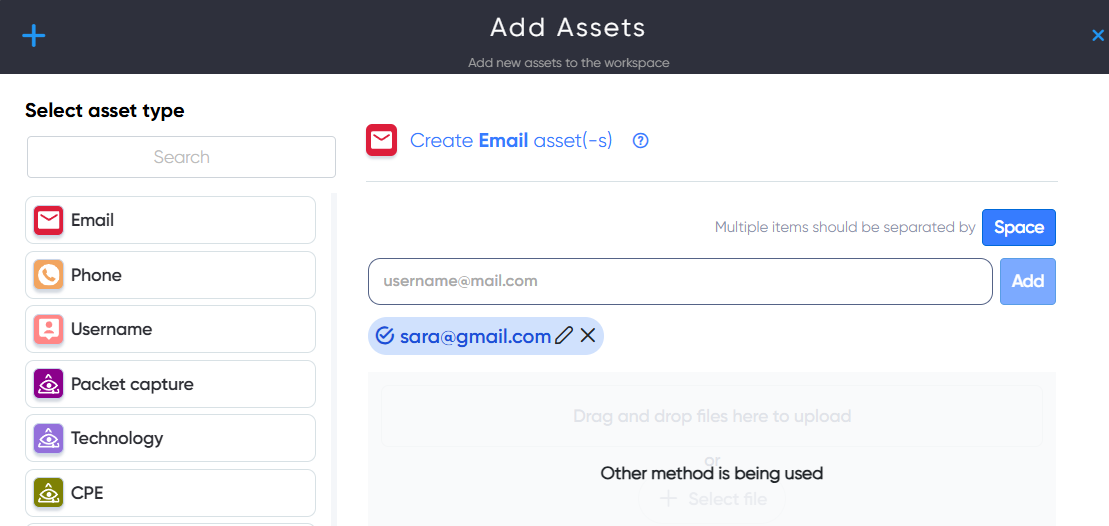
Select all the assets you need and click Configure workflow.
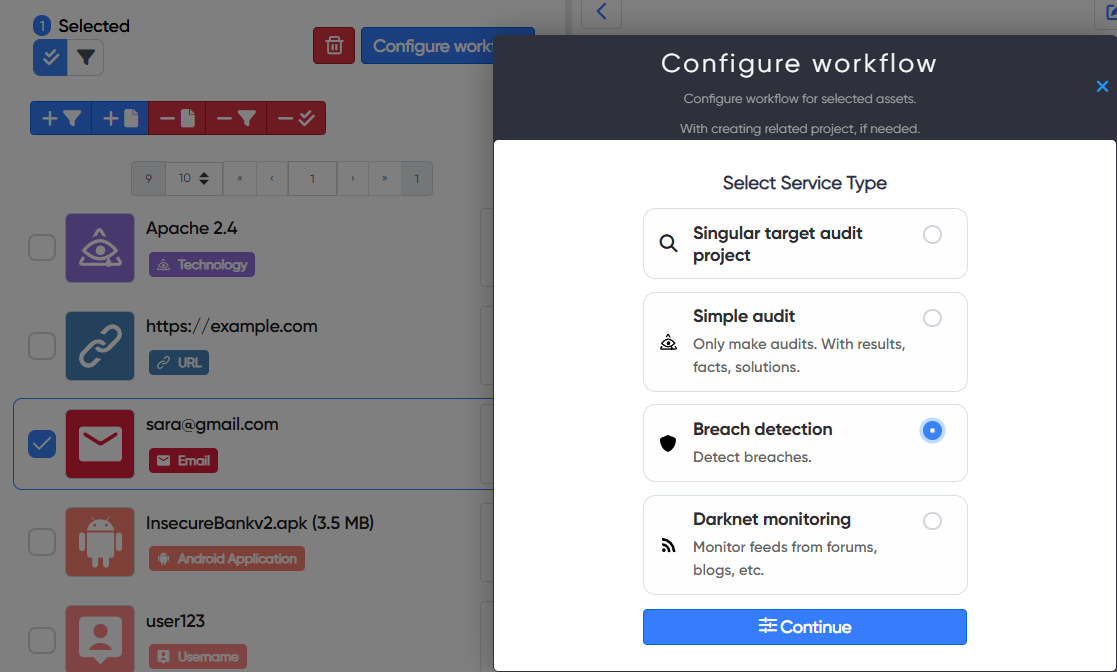
After that, you can adjust the scanning frequency and other parameters.
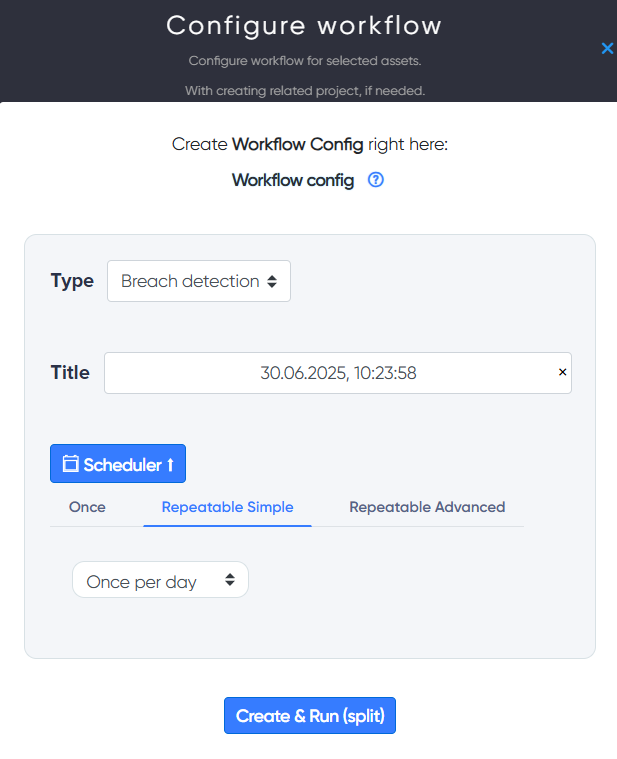
After clicking Create & Run you can see that a project has been created in which we have our workflows to choose from.
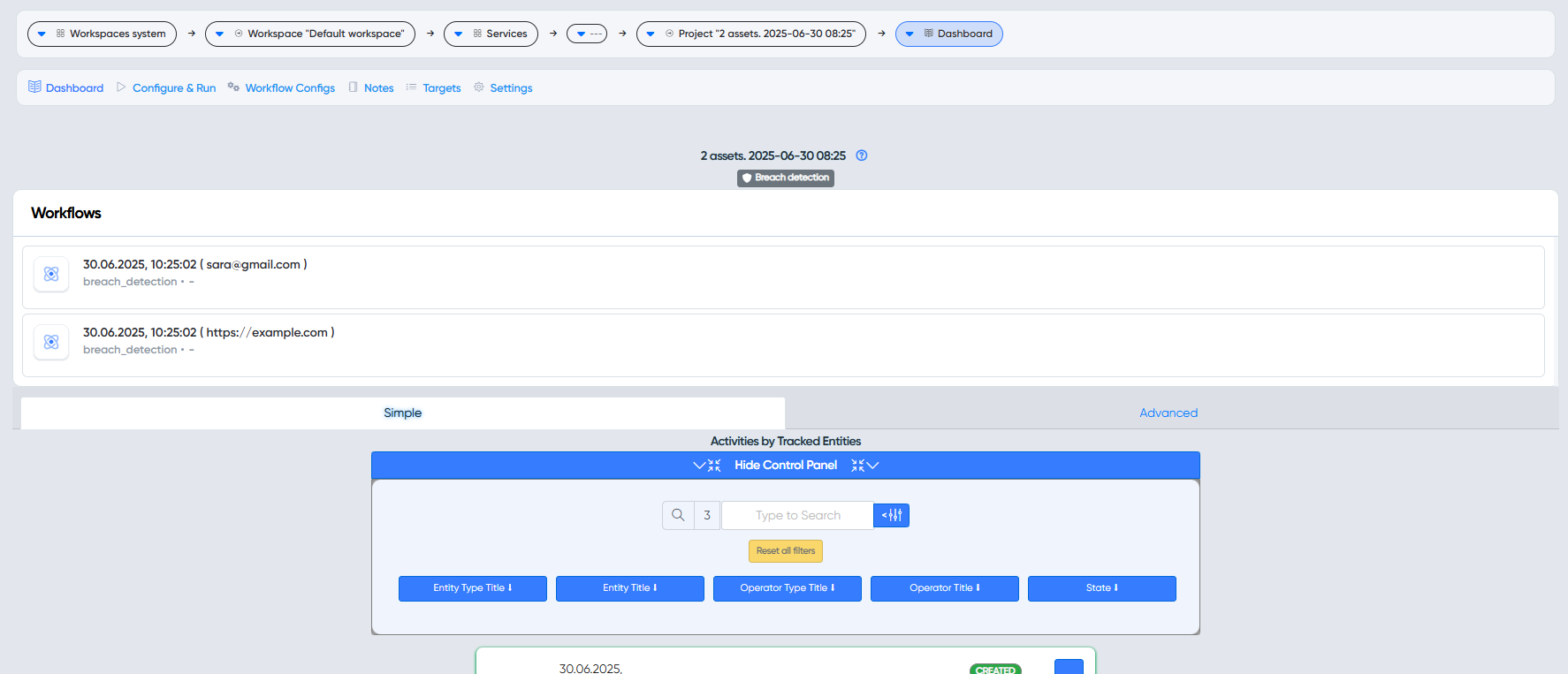
If the workflows do not start automatically, you should manually select the desired workflow and then click Create and Run New Execution

Wait a bit and the discovered vulnerabilities will be displayed.
Once the scan is complete, you can view the results.
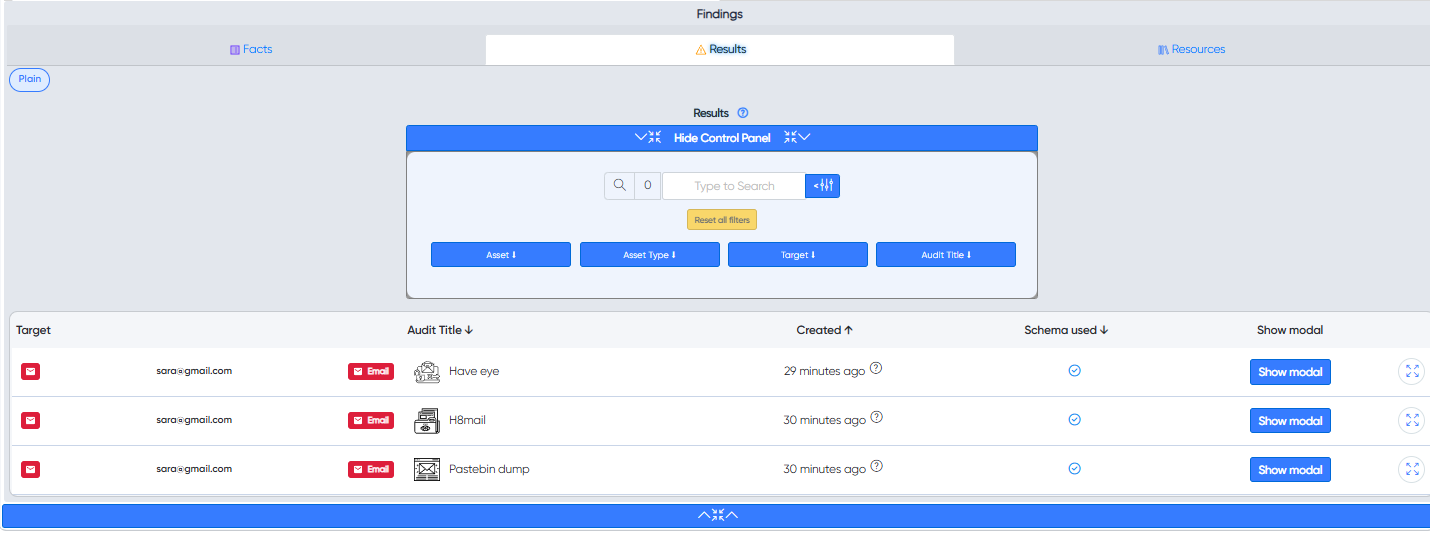
For a more detailed output, click the "Expand" icon.
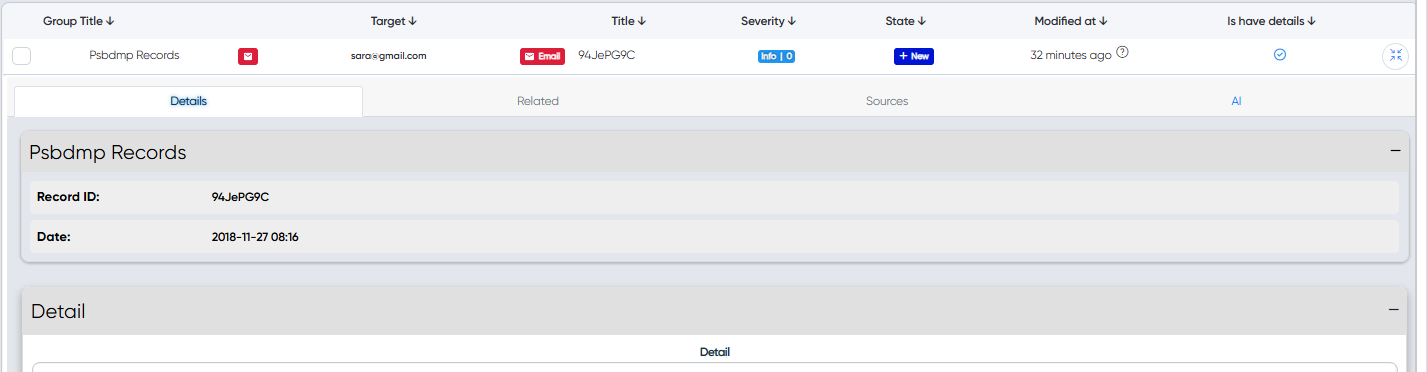
¶ List of audits:
¶ IP or IP range:
Add IP, ASN or CIDR
Has to be covered:
- “Hacked/Defaced”
- “Iframe, third-party js code”
- “News with “leaked”, ”hacked” ”
- “Paste websites”
- “Github”
- “Whois leaked email”
- “File sharing services”
- “Other leaks”
Services:
- http://isithacked.com/
- https://github.com/TheRealFlyingFrog/LeakLookerLib ( most important)
- https://github.com/jonathan6661/P1sty
- https://psbdmp.ws/
- https://infoleaks.cc/
- https://www.zone-h.org/
- Search by RSS feeds. These forum’s RSS feeds and twitters can be used to identify leaks by IP, domain name, and company name:
- https://rsshub.app/telegram/channel/dataleak
- https://rsshub.app/telegram/channel/data1eaks
- https://rsshub.app/telegram/channel/Freedomf0x
- https://rsshub.app/telegram/channel/leaks_db
- https://rsshub.app/twitter/user/Dumps_monitor
- https://xss.is/forums/140/index.rss
- https://raidforums.com/syndication.php?fid=153&limit=50
- https://raidforums.com/syndication.php?fid=216&limit=50
- https://combo-list.com/feed/
- https://sinfulsite.com/syndication.php?fid=61
- https://sinfulsite.com/syndication.php?fid=59
- https://www.crackingpro.com/index.php?/forum/124-other-leaks.xml/
- https://nulledbb.com/syndication.php?fid=30
- https://darksearch.io/apidoc
- https://pastebin.com/doc_api
- Extract email from whois and apply “email” leaks audits.
- Network scan
- ftp - check for anon audit, port: 21
- rsync - run common checks audit, port 873
- smb - check for null session, ports 139, 445
- Scan 4444 and 1337 for Metasploit bind
- https://www.dehashed.com
- https://snusbase.com/
Repo: https://github.com/kevthehermit/PasteHunter
¶ Domain/URL:
Add domain
Has to be covered:
- “Hacked/Defaced”
- “Iframe, third-party js code”
- “News with “leaked”, ”hacked” ”
- “Paste websites”
- “Github”
- “Whois leaked email”
- “Subdomain takeover”
- “Open storages”
- “Is domain expiring”
Services:
- http://isithacked.com/
- https://www.zone-h.org/
- https://github.com/TheRealFlyingFrog/LeakLookerLib ( most important)
- https://github.com/Warflop/Whoisleak
- https://gitlab.com/NightLionSec/noscrape/
- https://github.com/haroonawanofficial/BreachedDataScraper
- https://psbdmp.ws/
- https://pastebin.com/doc_api
- https://infoleaks.cc/
- https://haveibeenpwned.com/
- https://github.com/kevthehermit/PasteHunter
- https://github.com/NaveenRudra/RTTM
- https://github.com/IntelligenceX/SDK
- https://github.com/x0rz/phishing_catcher: Phishing catcher using Certstream
- Extract email from whois and apply “email” leaks audits
- Search by RSS feeds. These forum’s RSS feeds and twitters can be used to identify leaks by IP, domain name, and company name:
- https://rsshub.app/telegram/channel/dataleak
- https://rsshub.app/telegram/channel/data1eaks
- https://rsshub.app/telegram/channel/Freedomf0x
- https://rsshub.app/telegram/channel/leaks_db
- https://rsshub.app/twitter/user/Dumps_monitor
- https://xss.is/forums/140/index.rss
- https://raidforums.com/syndication.php?fid=153&limit=50
- https://raidforums.com/syndication.php?fid=216&limit=50
- https://combo-list.com/feed/
- https://sinfulsite.com/syndication.php?fid=61
- https://sinfulsite.com/syndication.php?fid=59
- https://www.crackingpro.com/index.php?/forum/124-other-leaks.xml/
- https://nulledbb.com/syndication.php?fid=30
- Network scan
- ftp - check for anon audit, port: 21
- rsync - run common checks audit, port 873
- smb - check for a null session, ports 139, 445
- Scan 4444 and 1337 for Metasploit bind
Repo: Tool for checking domain expiration: https://github.com/nixcraft/domain-check-2
¶ Company name:
Add company name
Has to be covered:
- Leaked emails
- “IP addresses”
- “News with “leaked”,”hacked” ”
Services:
- Search by RSS feeds. These forum’s RSS feeds and twitters can be used to identify leaks by IP, domain name, and company name:
- https://cracking.org/forums/other-leaks.248/index.rss
- https://cracking.org/forums/databases.31/index.rss
- https://nulledbb.com/syndication.php?fid=30
- https://www.crackingpro.com/index.php?/forum/124-other-leaks.xml/
- https://www.crackingpro.com/index.php?/forum/17-requests.xml/
- https://solidforums.com/syndication.php?fid=23
- https://solidforums.com/syndication.php?fid=34
- https://sinfulsite.com/syndication.php?fid=61
- https://sinfulsite.com/syndication.php?fid=59
- https://combo-list.com/feed/
- https://raidforums.com/syndication.php?fid=153&limit=50
- https://raidforums.com/syndication.php?fid=216&limit=50
- https://xss.is/forums/140/index.rss
- https://twitter.com/Dumps_monitor
- https://t.me/leaks_db
- https://t.me/freedomf0x
- https://t.me/data1eaks
- https://t.me/dataleak
- Convert the company name to ASN and apply IP/Domain checks if the user confirms that he owns this ASN. This can be done via amass: amass intel -org Tesla and then amass intel -active -asn
Repos: https://github.com/woj-ciech/LeakLooker should be modified to use the “org:” argument.
¶ Phishing detection for domain | username
- https://github.com/nixcraft/domain-check-2
- https://github.com/atenreiro/opensquat
- https://github.com/gfek/Hunting-New-Registered-Domains
¶ Email:
Has to be covered: Leaked emails
Services:
- HaveIBeenPwned(v3)
- Hunter.io
- Snusbase
- Leak-Lookup
- Emailrep.io
- Scylla.sh
- Dehashed.sh
- IntelX.io
Repo and websites:
- https://github.com/khast3x/h8mail
- https://github.com/p4yl0ad/HaveEye
- https://psbdmp.ws/
- https://infoleaks.cc/
- https://haveibeenpwned.com/ and the ones used at services
- Have I Been Pwned API
- WeLeakInfo API
- DeHashed API
- SnusBase API
- https://github.com/IntelligenceX/SDK
¶ Indication of compromise:
- Port 4444 or 1337 open (Nmap check)
- Malicious script on the main page ( virus check main page or authority)
- https://github.com/Neo23x0/Loki
¶ Cloud leaks
Has to be covered:
Bucket name ( azure, amazon, google )
Depending on this choice it will be checked on the cloud provider.
- S3 buckets
- GCP buckets
Actions. Need to find new buckets and check to exist for permissions.
¶ Github and GitLab external
Has to be covered: Github, GitLab secret leaks
- https://github.com/eth0izzle/shhgit we download the repo and check for leaks
- https://github.com/nielsing/yar secret leak
- https://github.com/michenriksen/gitrob
- https://github.com/woj-ciech/LeakLooker
¶ API Keys
Has to be covered:
- Aws key leaks detection ( user provides Access key or list of keys, without secret)
- Azure key ( CLIENT_ID)
- Google cloud
- Github key leaks detection ( user provides Access key or list of keys, without secret)
Services:
- AWS_ACCESS_KEY_ID key to search in GitHub.
- CLIENT_ID, TENANT_ID For Azure
- Client_id or project_id for Google cloud
- Client_id for Github
- idToken For Firebase
- client_id For Facebook
Answer: https://github.com/michenriksen/gitrob can be used to search for these keys if will be tuned. Or use GitHub, GitLab API
Repo: Should be self-made. Idea is to write dorks based on chosen keys. We provide a menu where users add keys for monitoring. The info which is grabbed for monitoring is not confidential.
Reference: https://github.com/streaak/keyhacks
Please see this repo: https://github.com/woj-ciech/LeakLooker-X
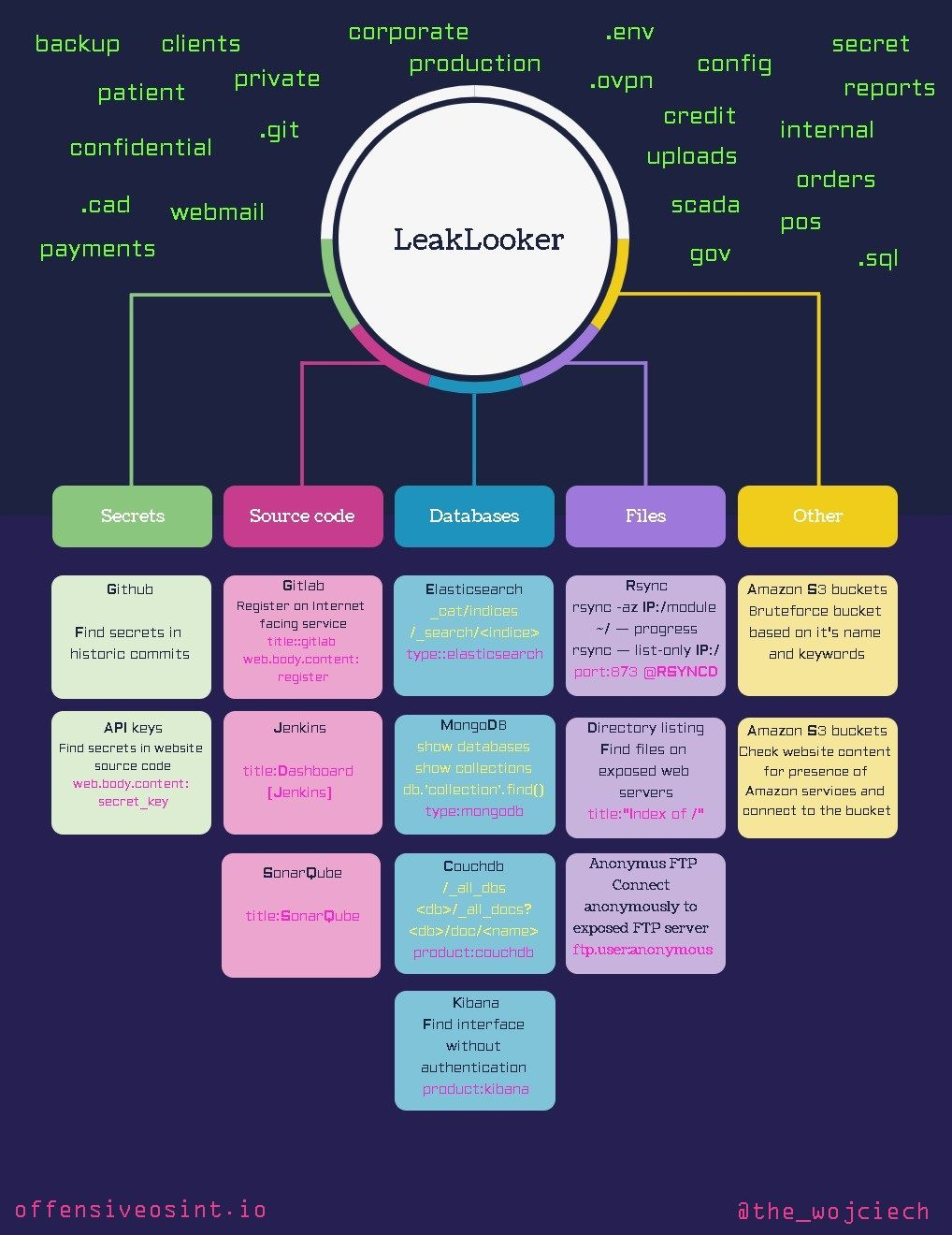
¶ Additional info
Leaks: