¶ Cry-AI
CryAI is an advanced security scanning tool designed to assess the security posture of web applications using artificial intelligence.
¶ How it works
-
Technology Detection:
CryAI automatically identifies the technologies utilized by the target web application, such as web servers, CMS, frameworks, etc.
This process allows the tool to select the most relevant exploit modules specific to the detected technologies. -
Exploit Selection
Based on the collected technology information, CryAI fetches exploit modules from the Exploit Database.
The modules selected are relevant to the specific system and technologies in use.
¶ Automated Scanning
The tool fully automates the process of launching exploits and analyzing their impact.
The scanning process includes both passive and active testing, enabling the identification of vulnerabilities with minimal operator involvement.
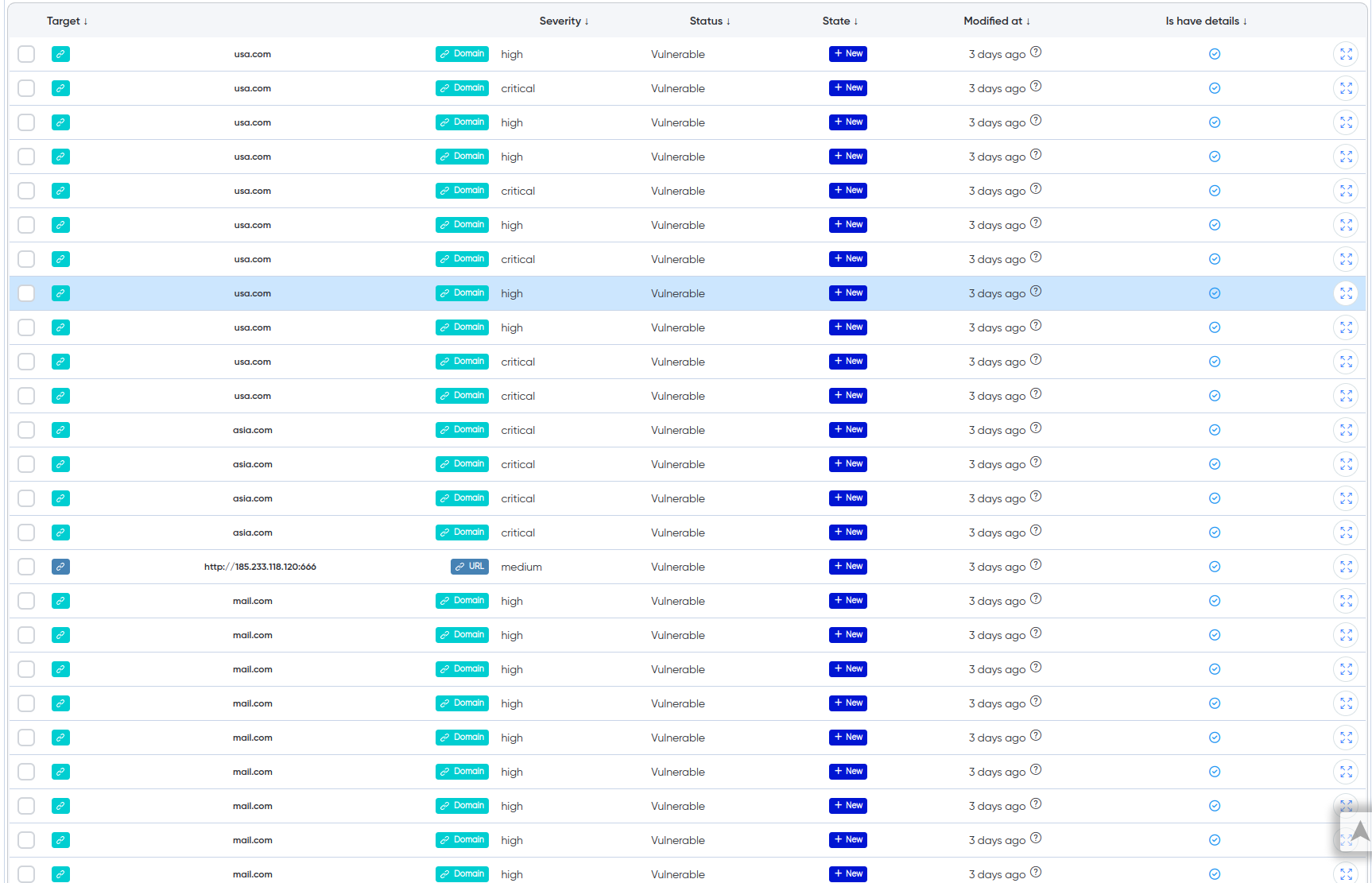
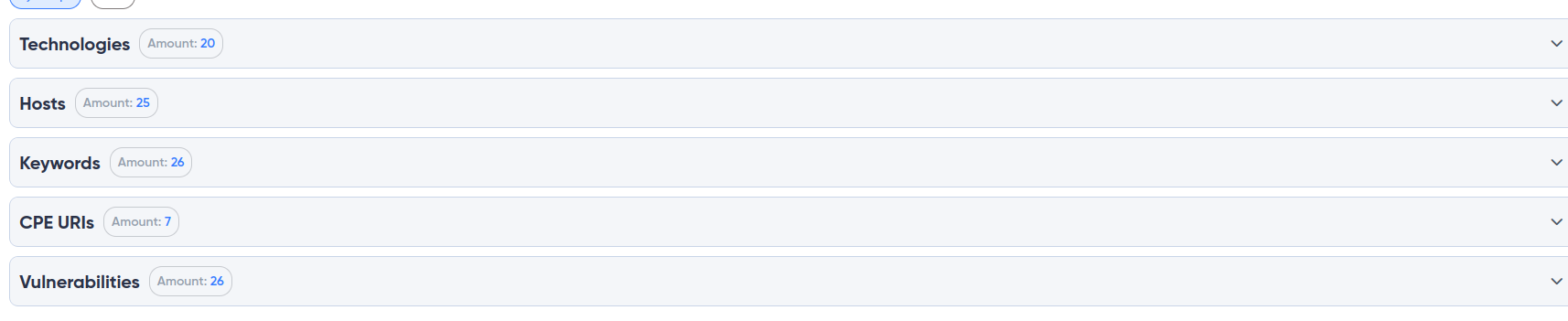
¶ Key Report Findings
-
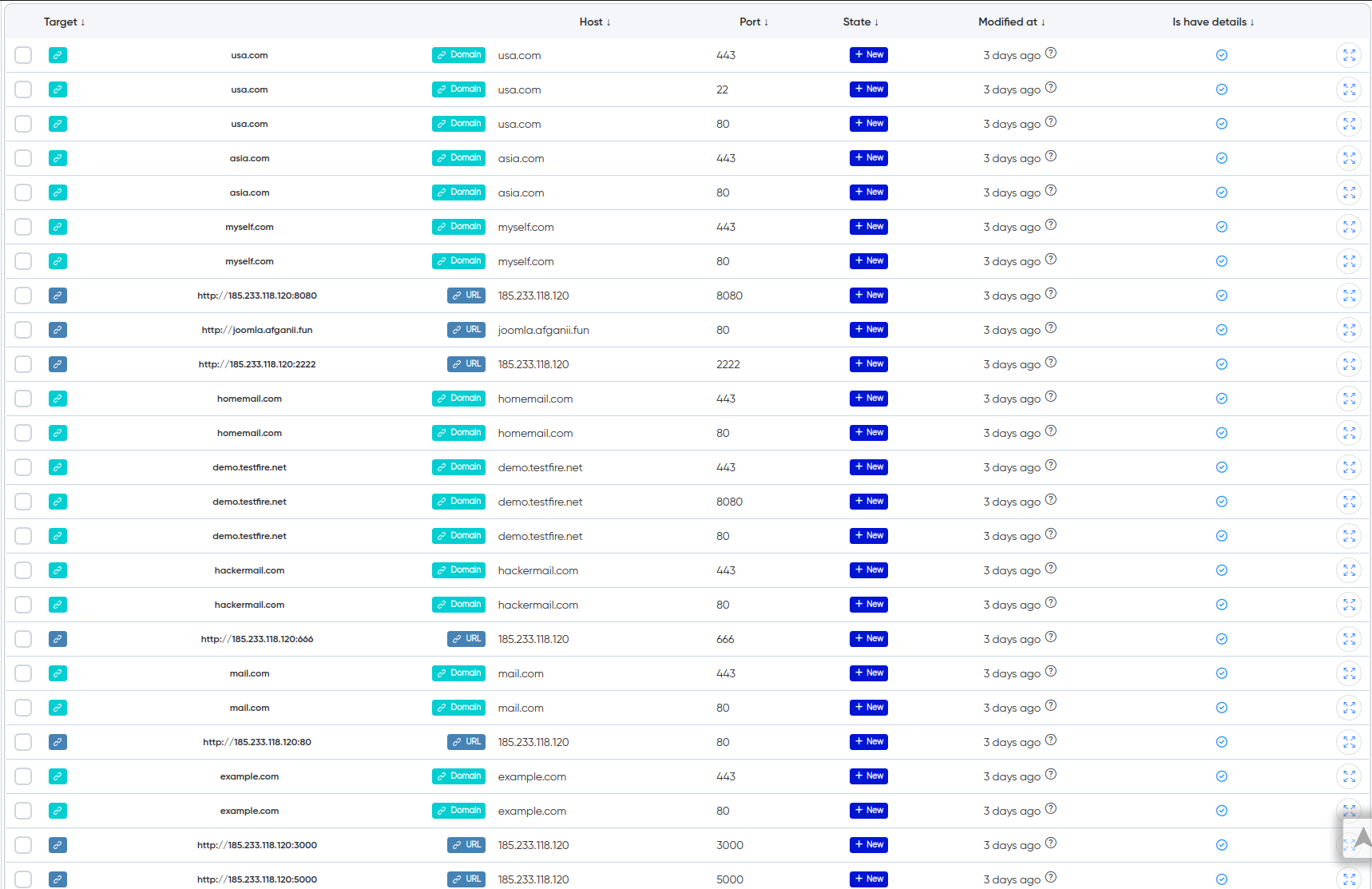
Hosts: Information about all discovered hosts is presented, including IP addresses, open ports, and detected vulnerabilities. This provides a quick assessment of the surface-level state of all targets.
-
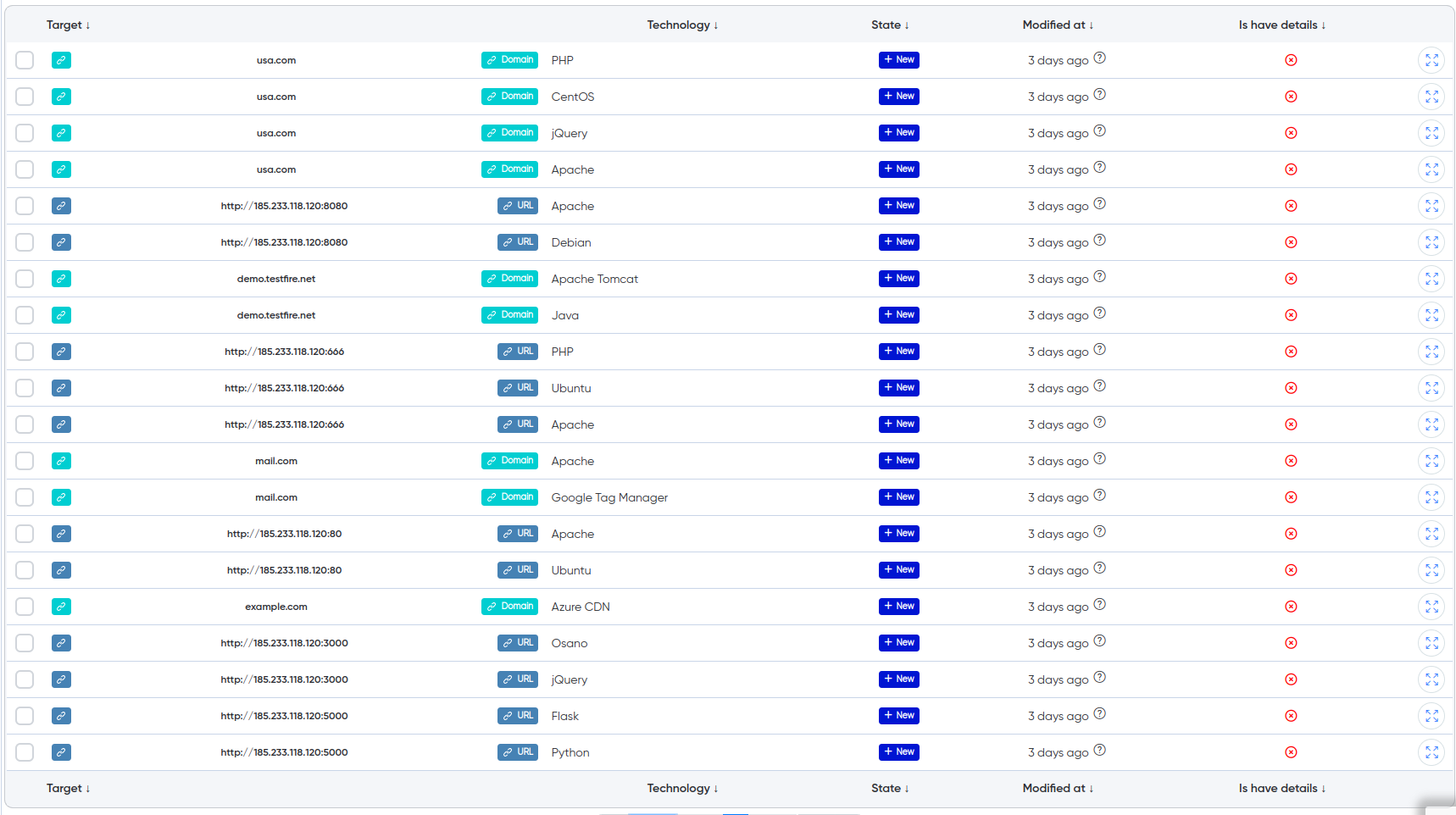
Technologies: Detailed information about the technologies used by each host, such as web servers, frameworks, and CMS. This allows you to understand which exploits may be relevant for further testing.
-
URI: Key URI paths or addresses related to the target application are displayed. These may indicate potential entry points, such as admin panels, APIs, or public directories.
-
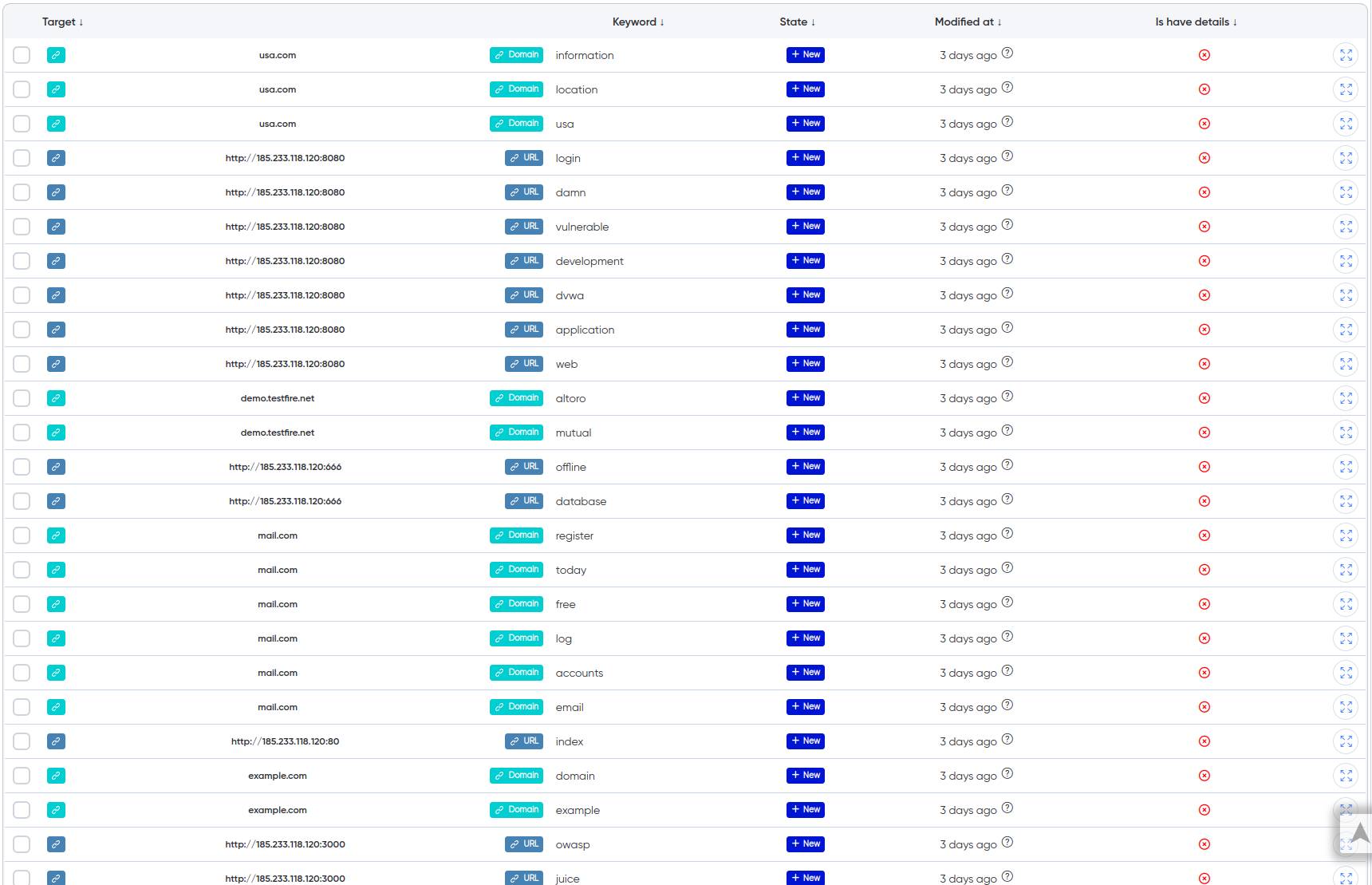
Keywords: A list of detected keywords related to the security of the application. These could include terms such as "admin," "login," or "password," indicating areas of interest for potential attacks.
-
Vulnerabilities: A comprehensive summary of all detected vulnerabilities, including their names, severity, and the number of affected hosts. This allows for a quick evaluation of where the most serious risks are located.
¶ Main Features
- Automatic detection of technologies used by the target application.
- Selection and execution of exploit modules based on identified technologies.
- Generation of detailed reports on vulnerabilities, providing comprehensive insights into security risks.
With CryAI, organizations can enhance their security posture, minimize the risk of cyberattacks, and maintain the integrity and confidentiality of their digital assets.
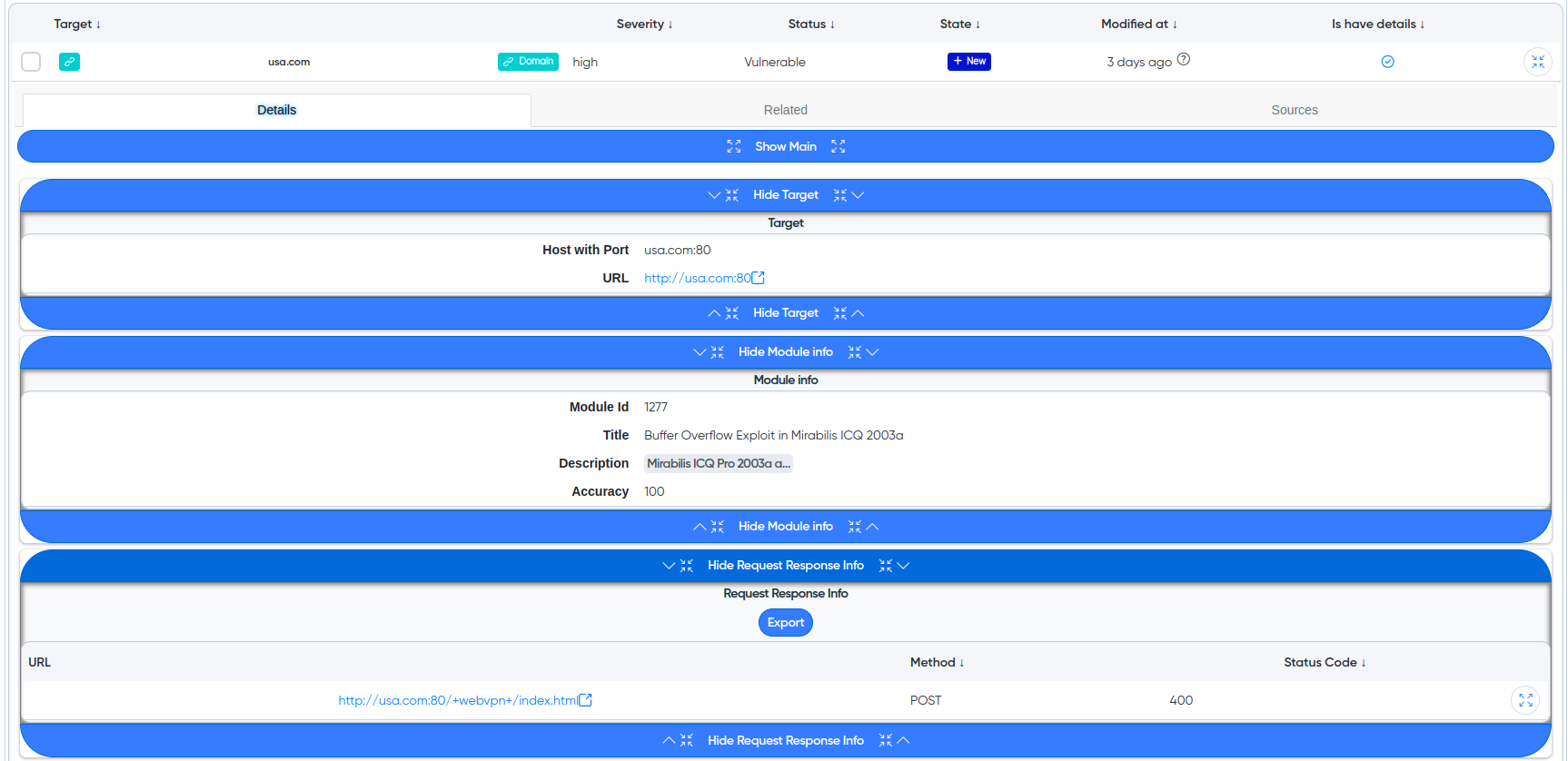
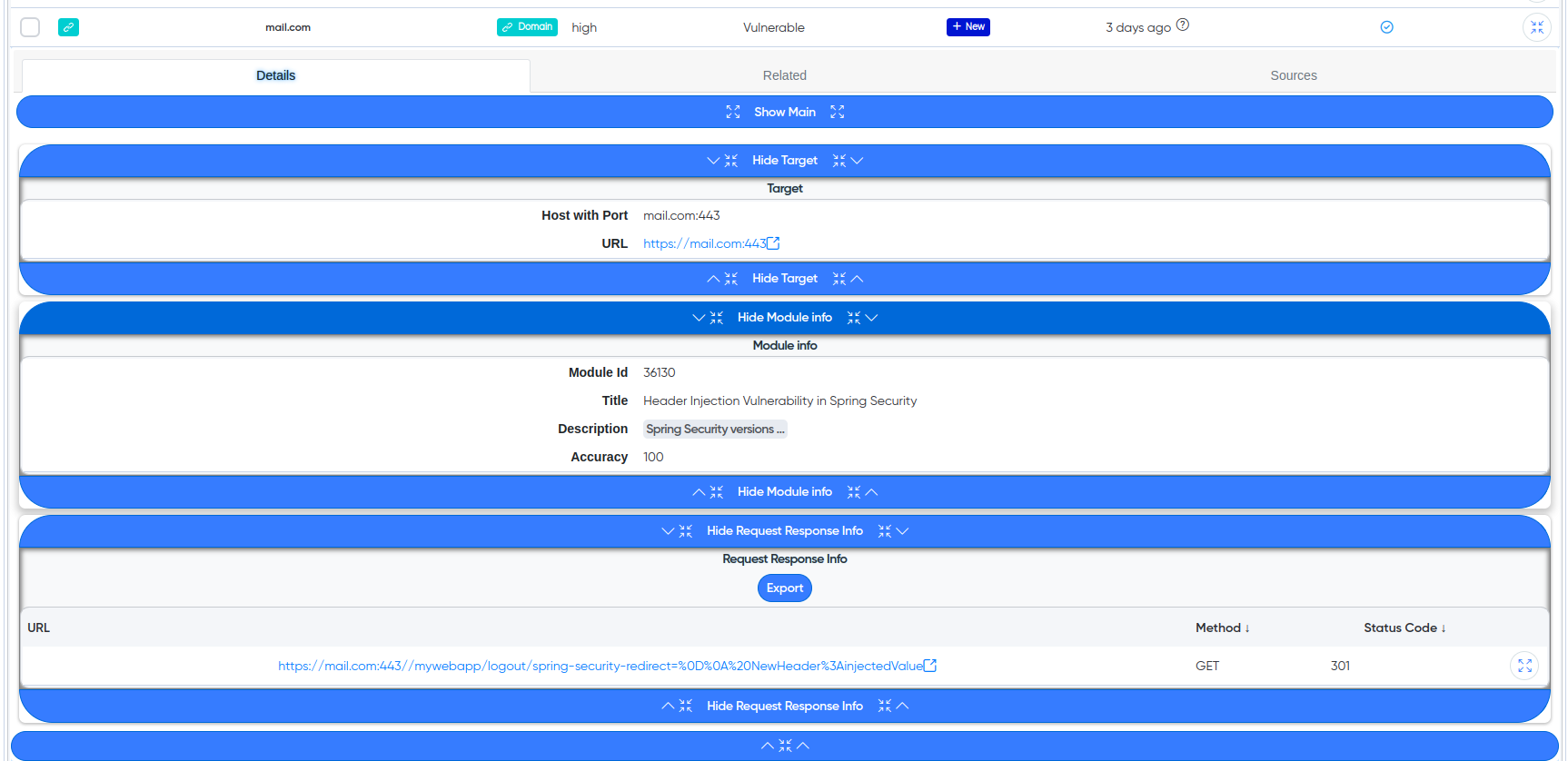
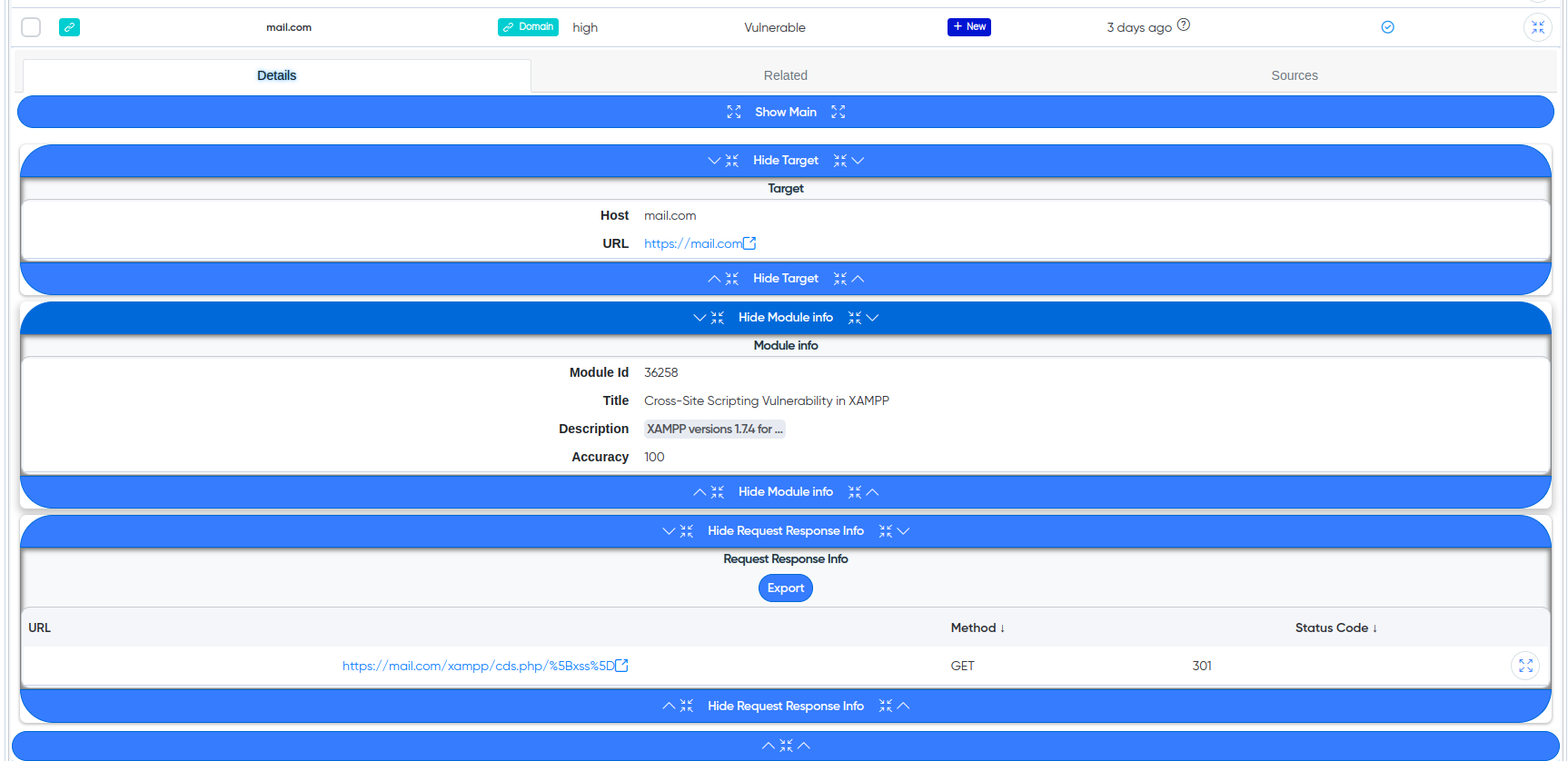
¶ Cry-AI output example
¶ Hosts
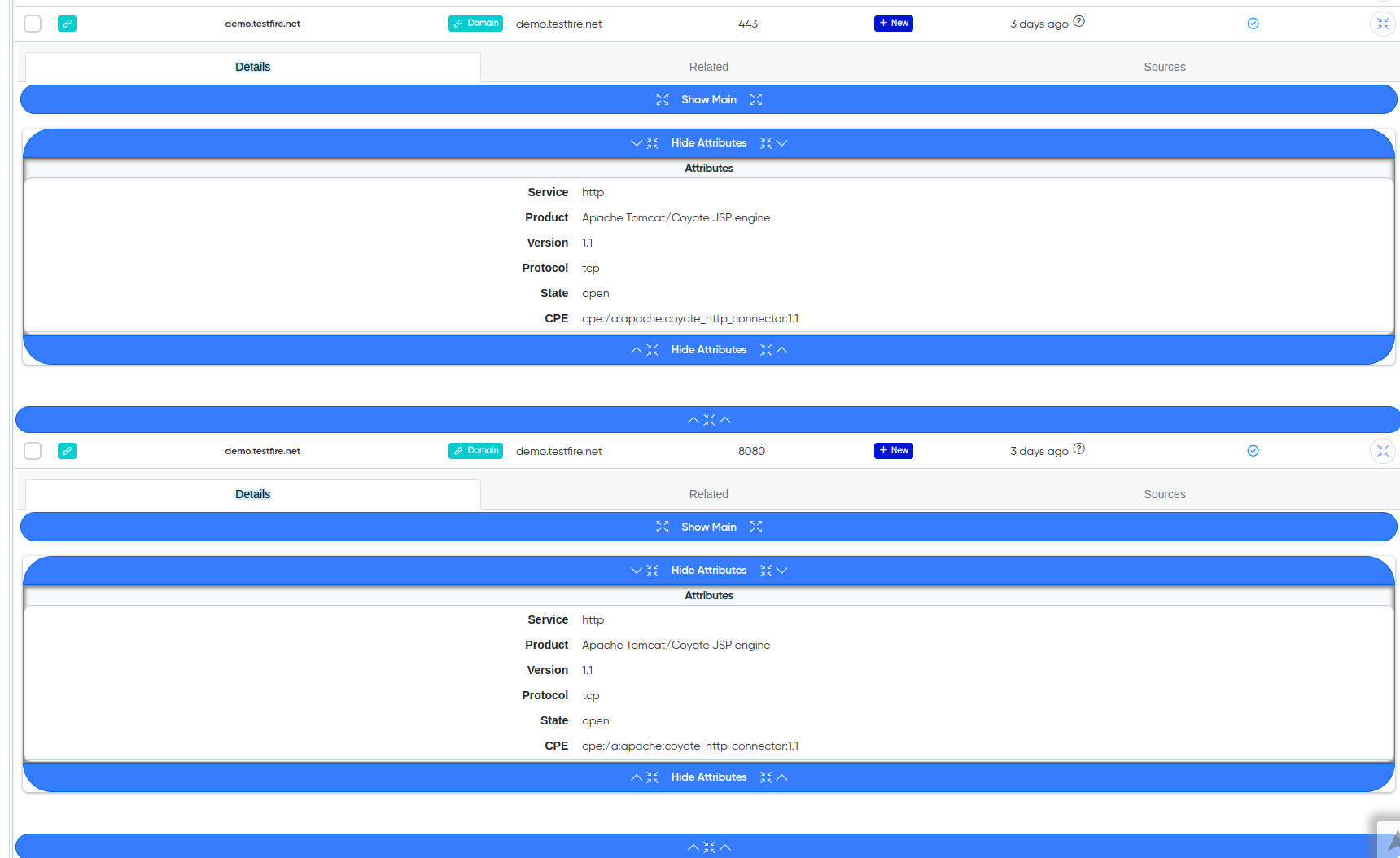
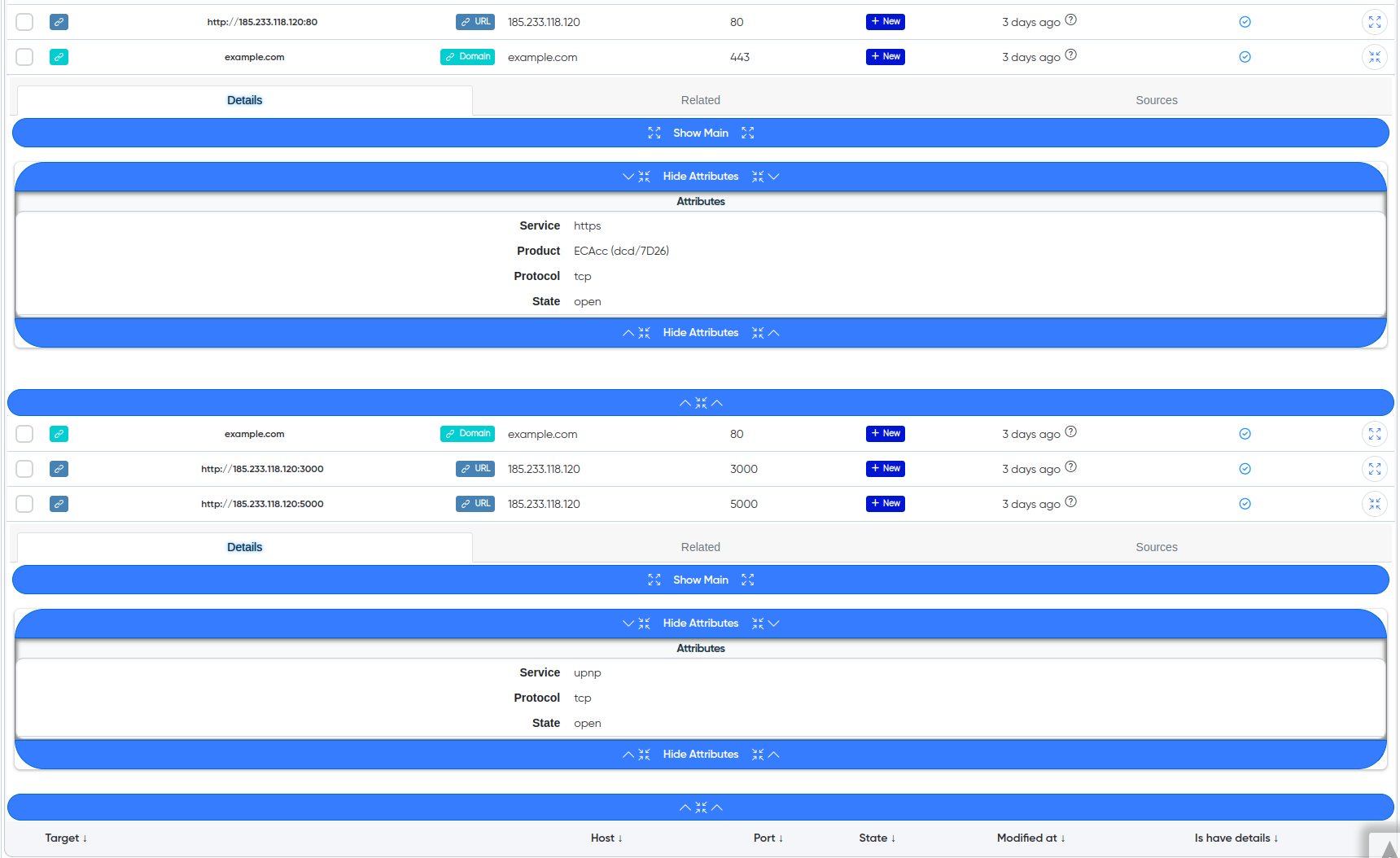
¶ Technologies
¶ Keywords
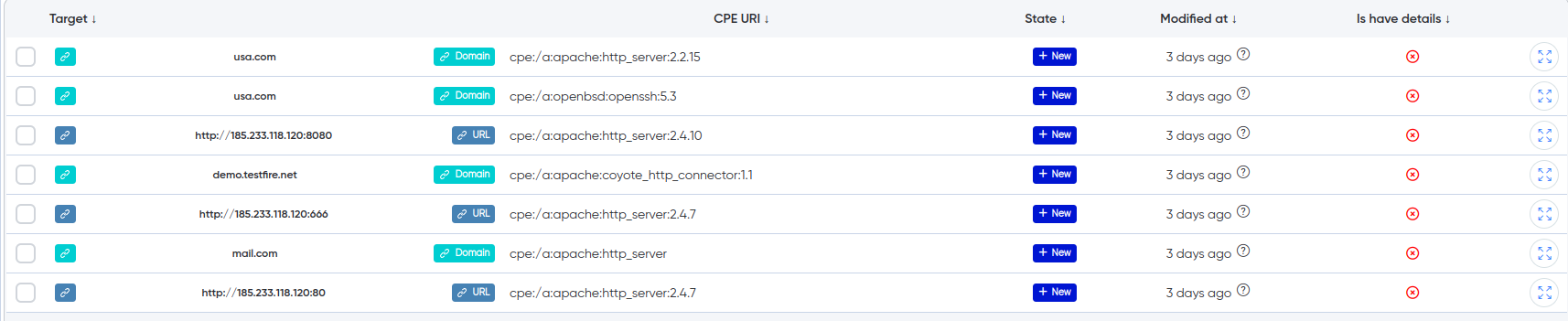
¶ CPE URIs
¶ Vulnerabilities