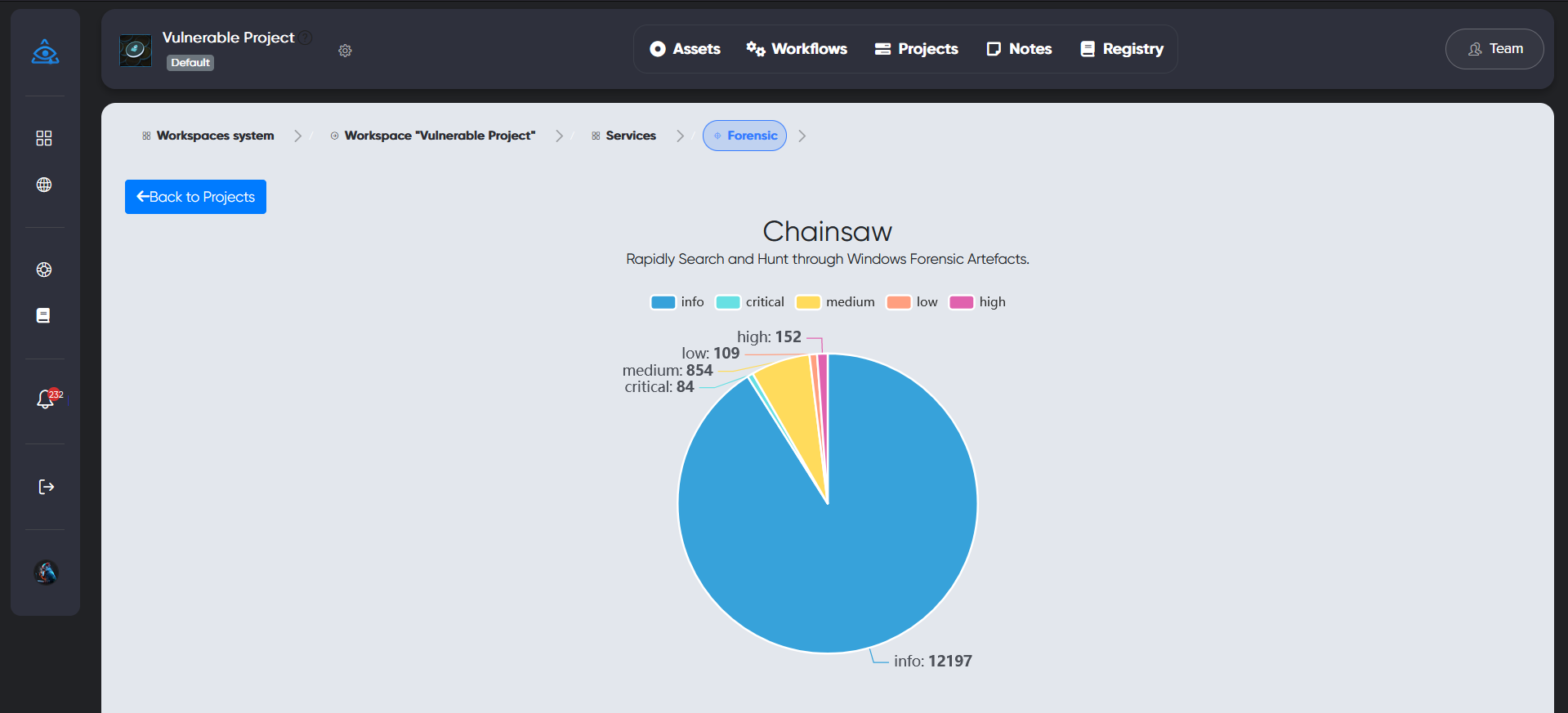
¶ Chainsaw
https://github.com/WithSecureLabs/chainsaw
¶ Overview
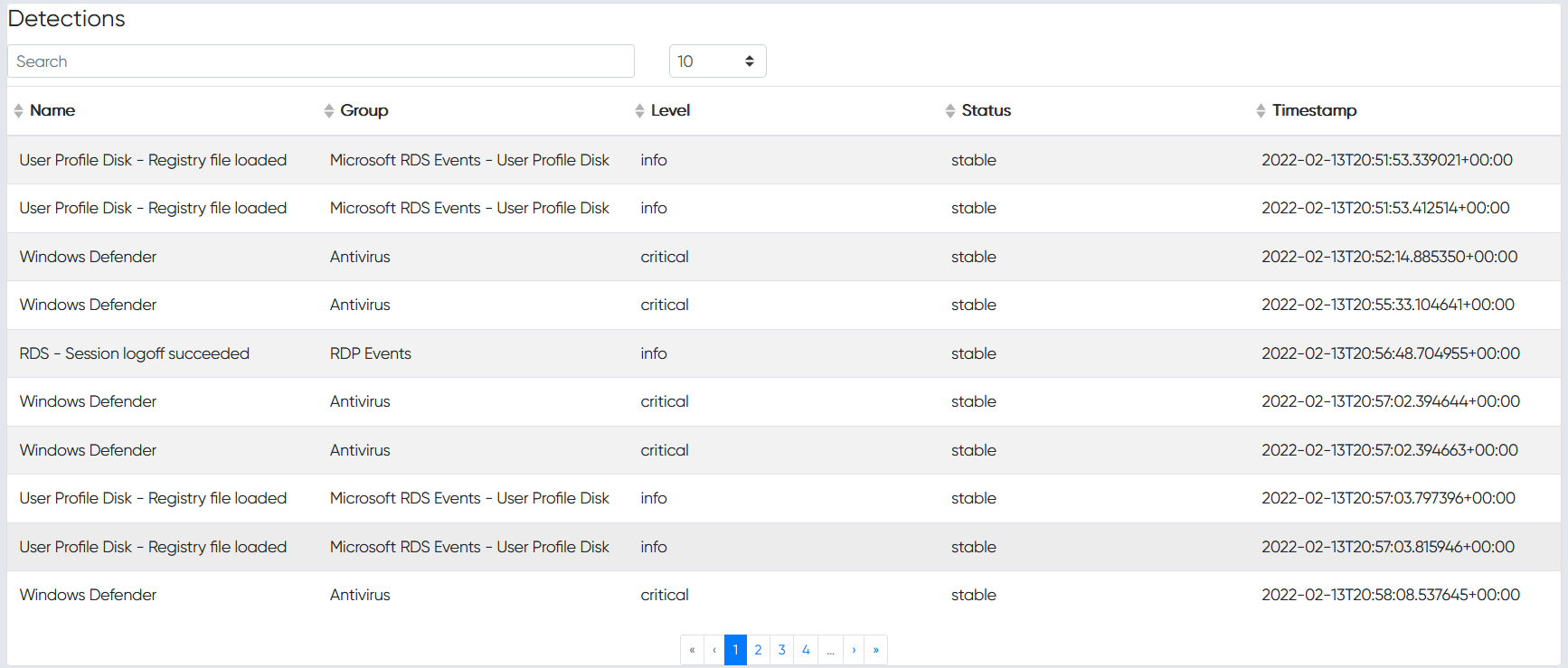
Chainsaw provides a powerful ‘first-response’ capability to quickly identify threats within Windows forensic artefacts such as Event Logs and the MFT file. Chainsaw offers a generic and fast method of searching through event logs for keywords, and by identifying threats using built-in support for Sigma detection rules, and via custom Chainsaw detection rules.
¶ Features
- Hunt for threats using Sigma detection rules and custom Chainsaw detection rules
- Search and extract forensic artefacts by string matching, and regex patterns
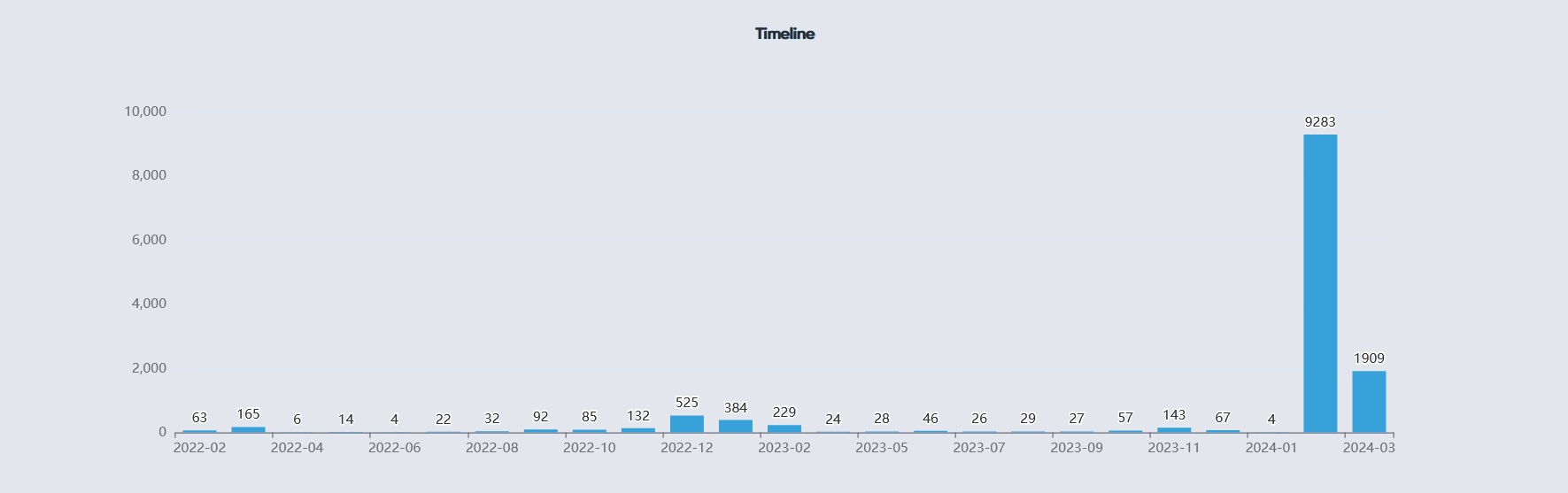
- Create execution timelines by analysing Shimcache artefacts and enriching them with Amcache data
- Analyse the SRUM database and provide insights about it
- Dump the raw content of forensic artefacts (MFT, registry hives, ESE databases)
- Lightning fast, written in rust, wrapping the EVTX parser library by @OBenamram
- Clean and lightweight execution and output formats without unnecessary bloat
- Document tagging (detection logic matching) provided by the TAU Engine Library
- Output results in a variety of formats, such as ASCII table format, CSV format, and JSON format
- Can be run on MacOS, Linux and Windows
¶ How to start?
You can find this here.