¶ 🛠 Infrastructure Security Scanning
Infrastructure as Code (IaC) security scanning is the process of analyzing code that defines and manages infrastructure resources like servers, networks, and storage — to detect vulnerabilities, misconfigurations, and security risks.
As IaC adoption grows via DevOps and cloud services, ensuring secure infrastructure configurations is critical.
¶ 🔍 What Is Scanned?
-
Security Best Practices
- Encryption, access controls, no hardcoded credentials
-
Vulnerability Detection
- Known CVEs, static analysis, insecure settings
-
Secrets Management
- Detects exposed API keys, passwords, tokens
-
Compliance Requirements
- Checks against standards like HIPAA, PCI DSS, ISO, GDPR
-
CI/CD Integration
- Embedded into pipelines for continuous monitoring
¶ 🚀 How It Works in CryEye
- Upload infrastructure code as an Asset
- Create an Audit Project
- Manually select and run security audits
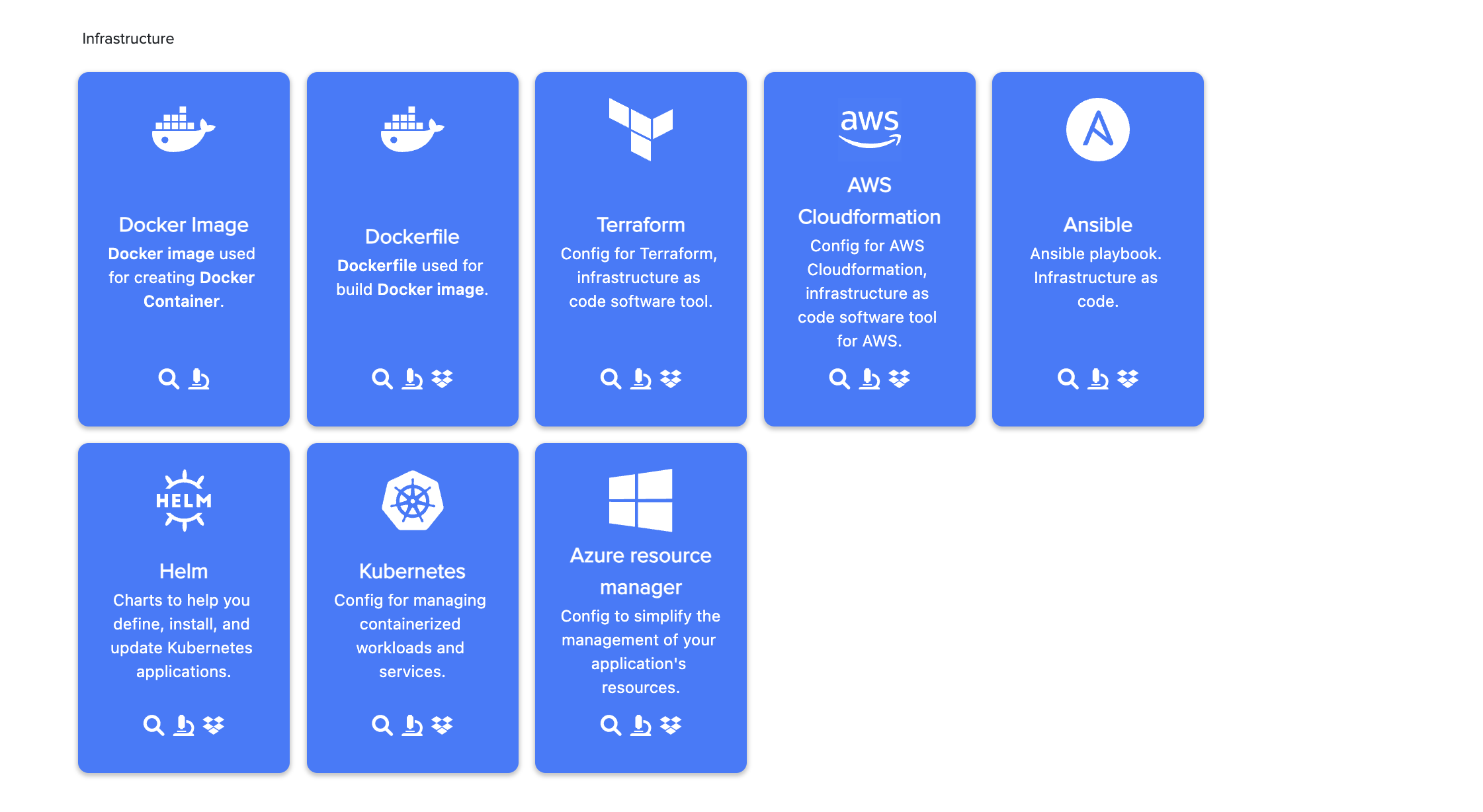
¶ 🧪 Supported IaC Types
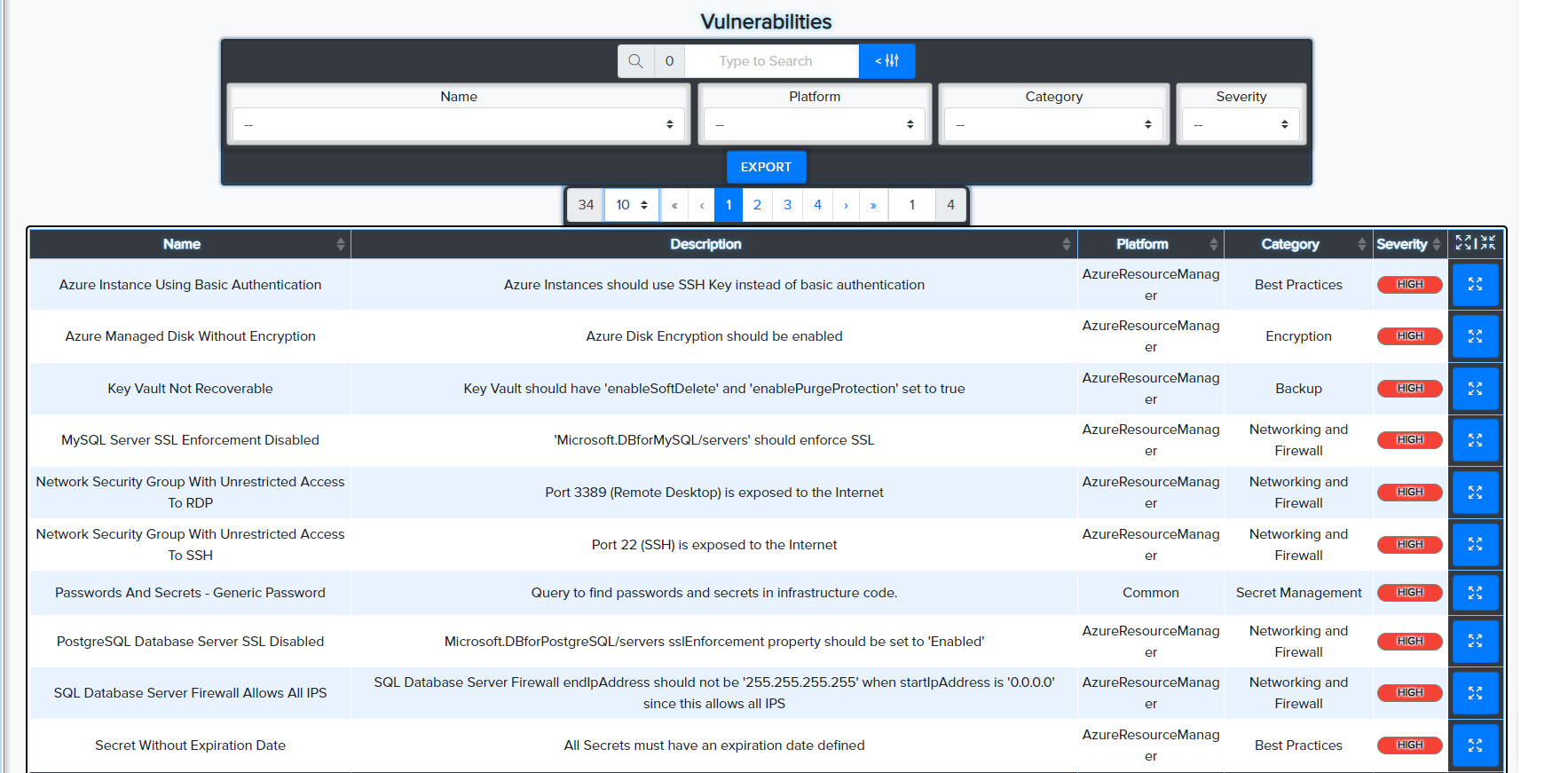
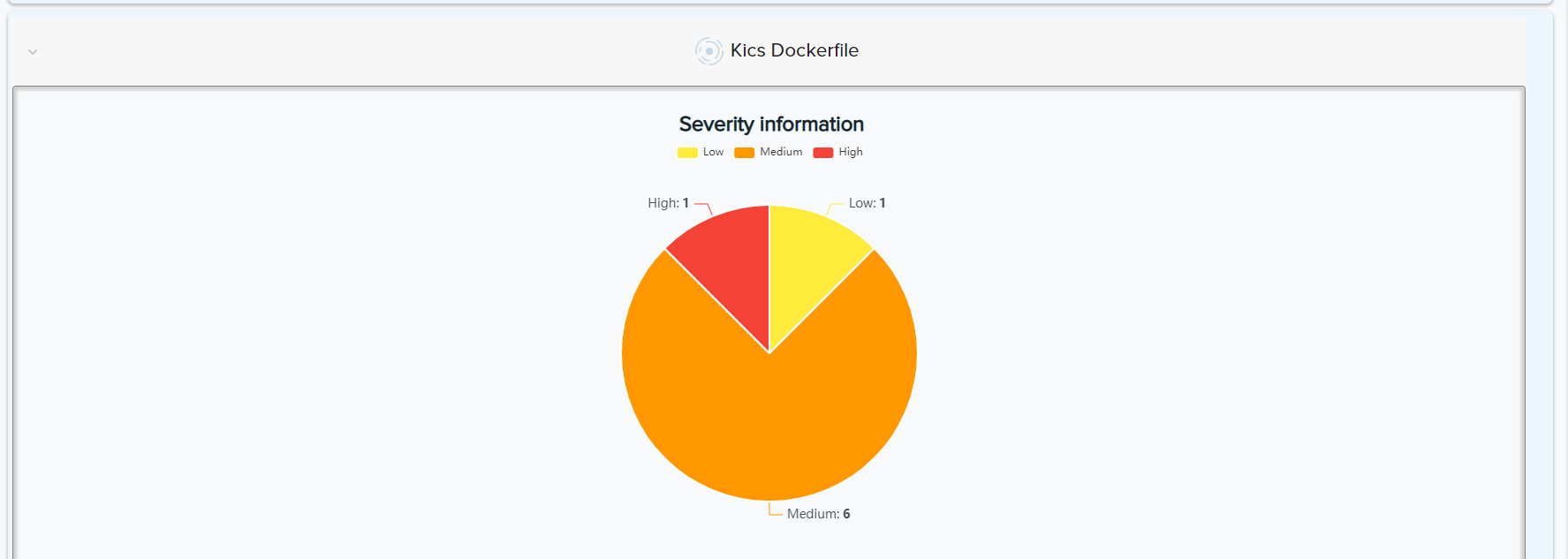
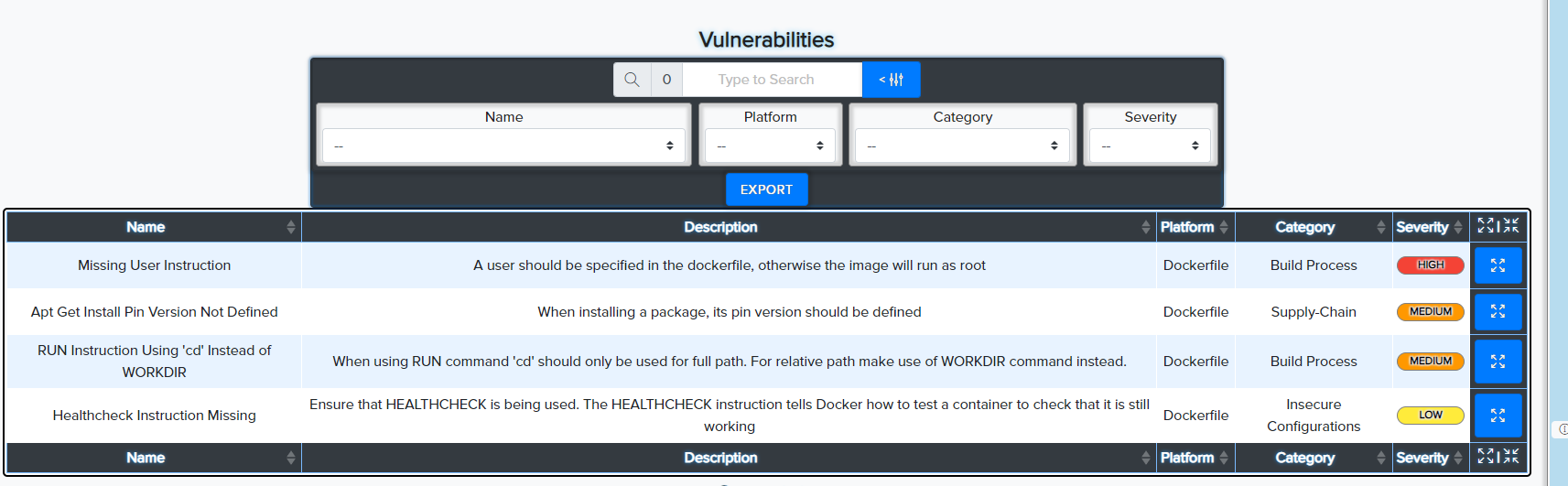
¶ 🐳 Docker Image & File Scanning
- Scans Dockerfiles and local images
- Detects insecure base images, bad permissions, unscanned packages
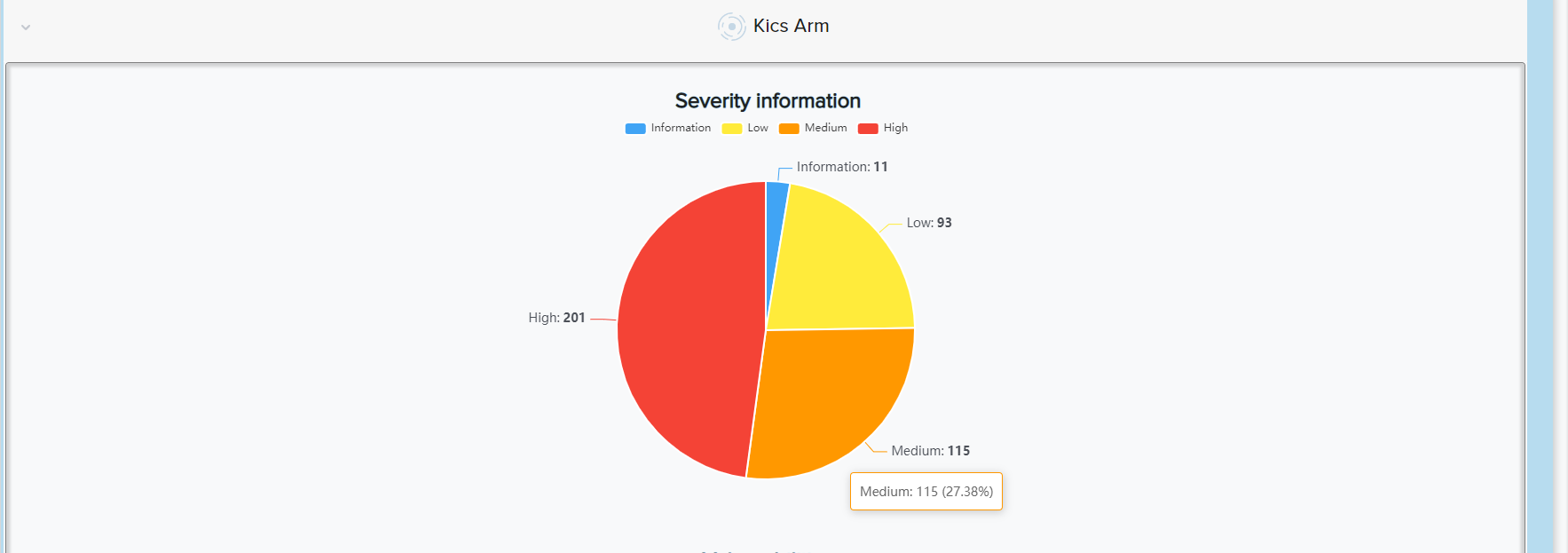
📸 Example:
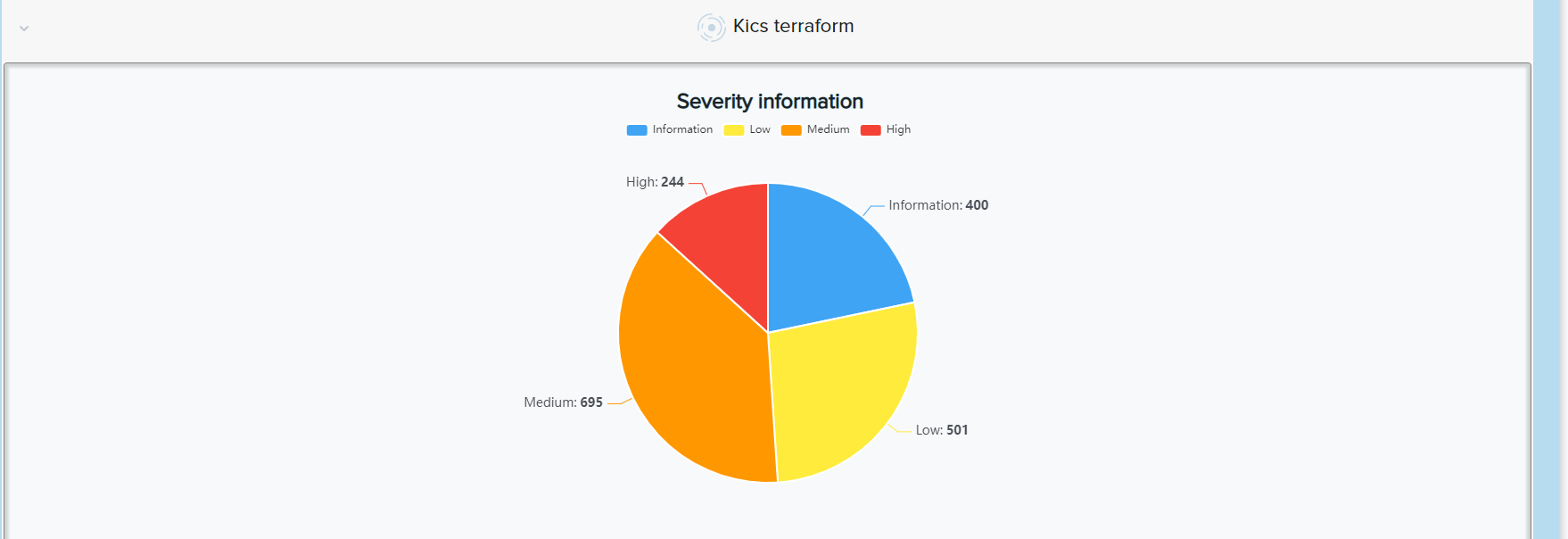
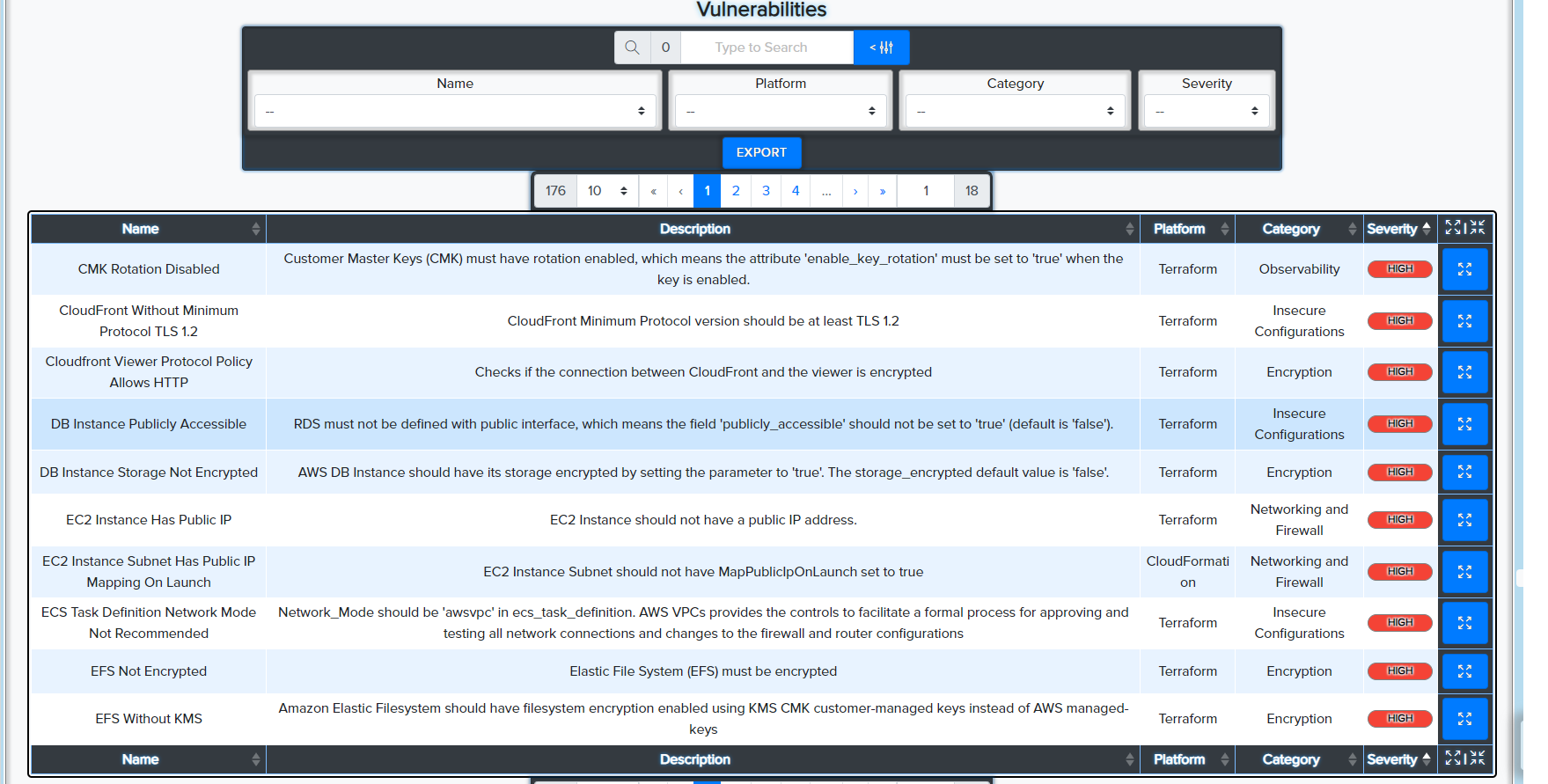
¶ 🌍 Terraform
- Analyzes
.tffiles for cloud resource misconfigurations - Supports AWS, Azure, GCP
📸 Example:
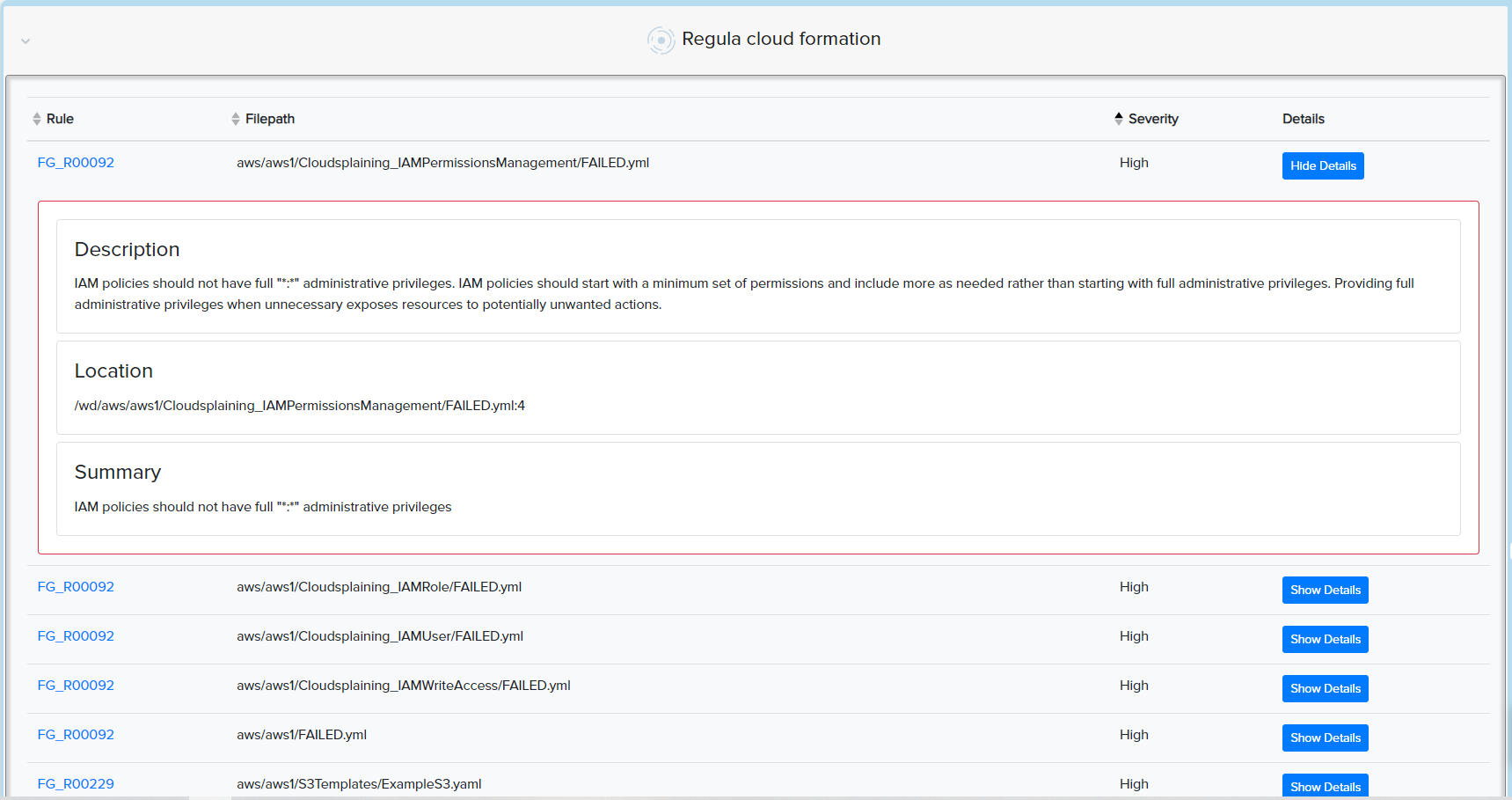
¶ ☁️ AWS CloudFormation
- Scans
.json/.yamltemplates - Detects IAM misconfigurations, open buckets, insecure protocols
📸 Example:
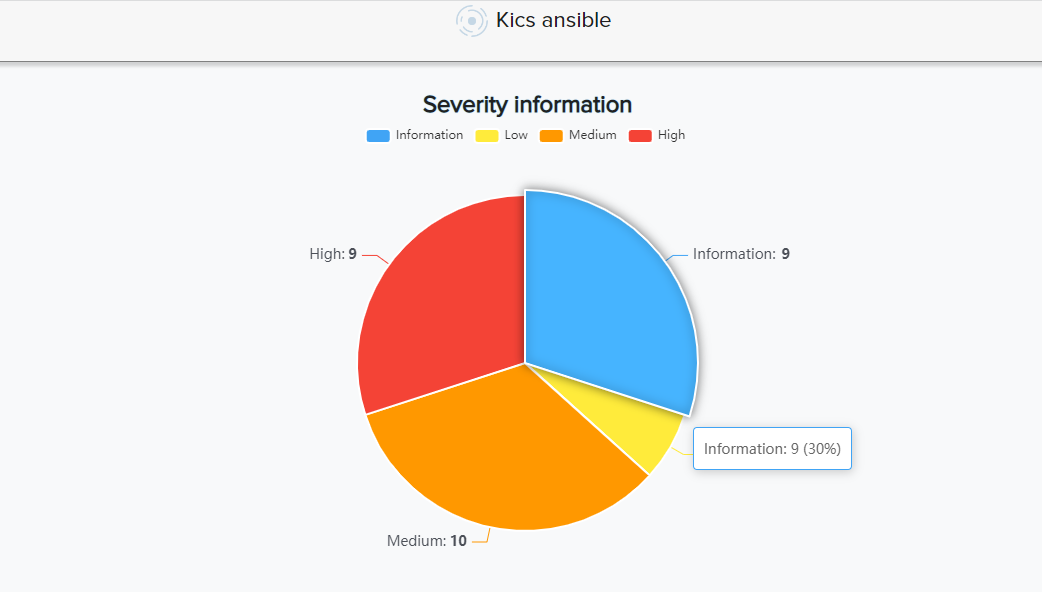
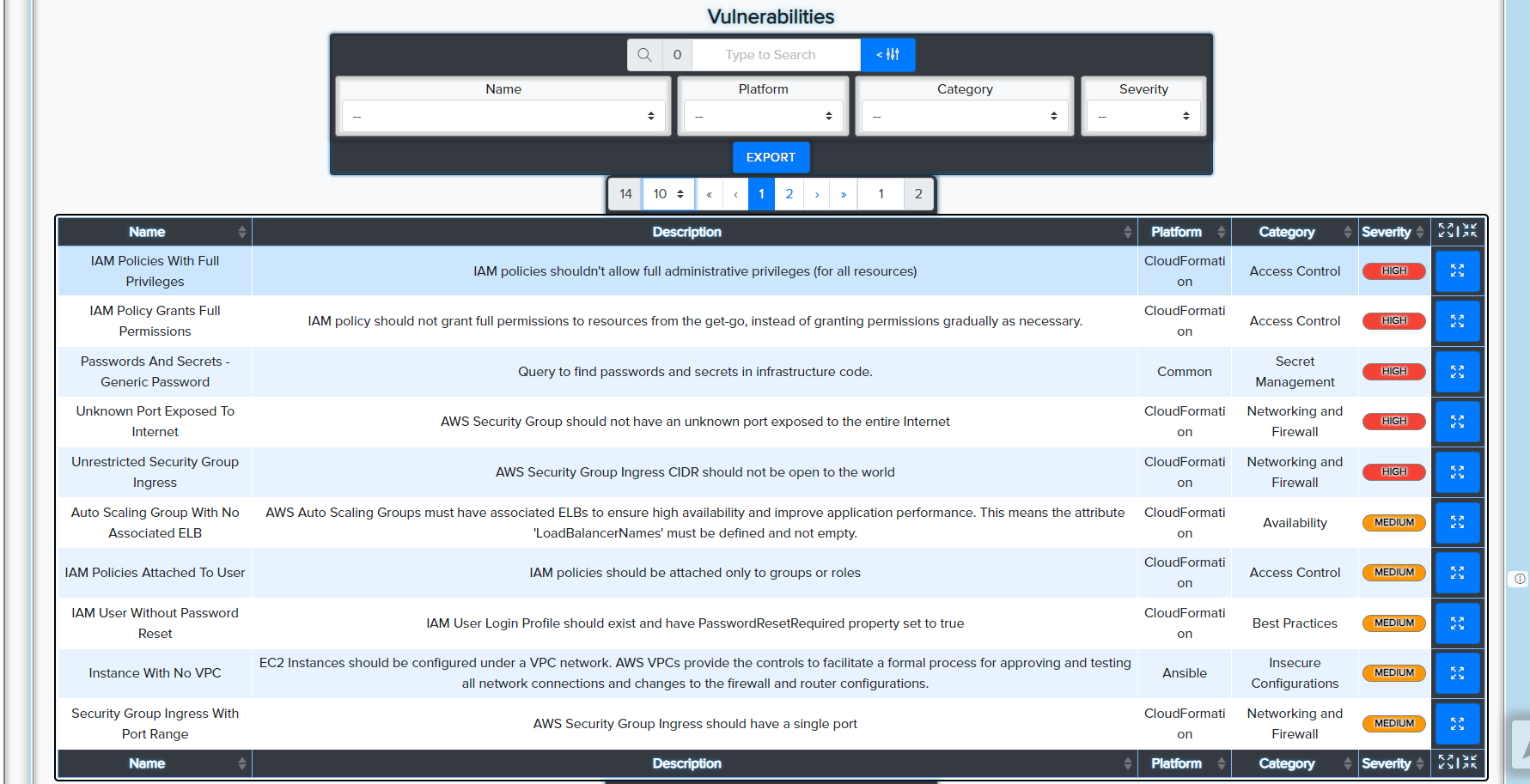
¶ ⚙️ Ansible
- Analyzes playbooks and config files
- Detects hardcoded credentials, unsafe modules, unencrypted secrets
📸 Example:
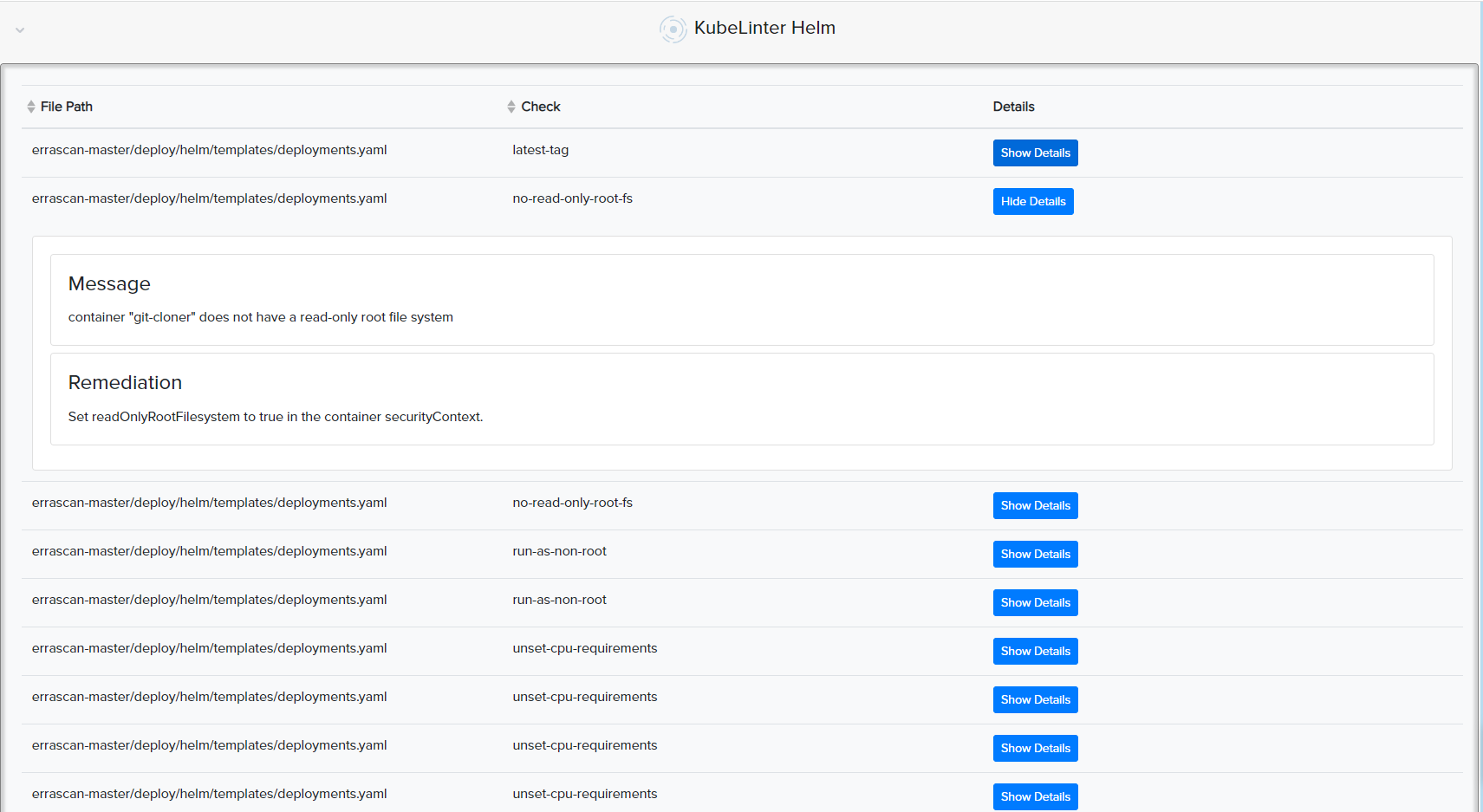
¶ 📦 Helm (Kubernetes)
- Scans Helm Charts for Kubernetes deployments
- Detects insecure defaults, privilege escalation, missing limits
📸 Example:
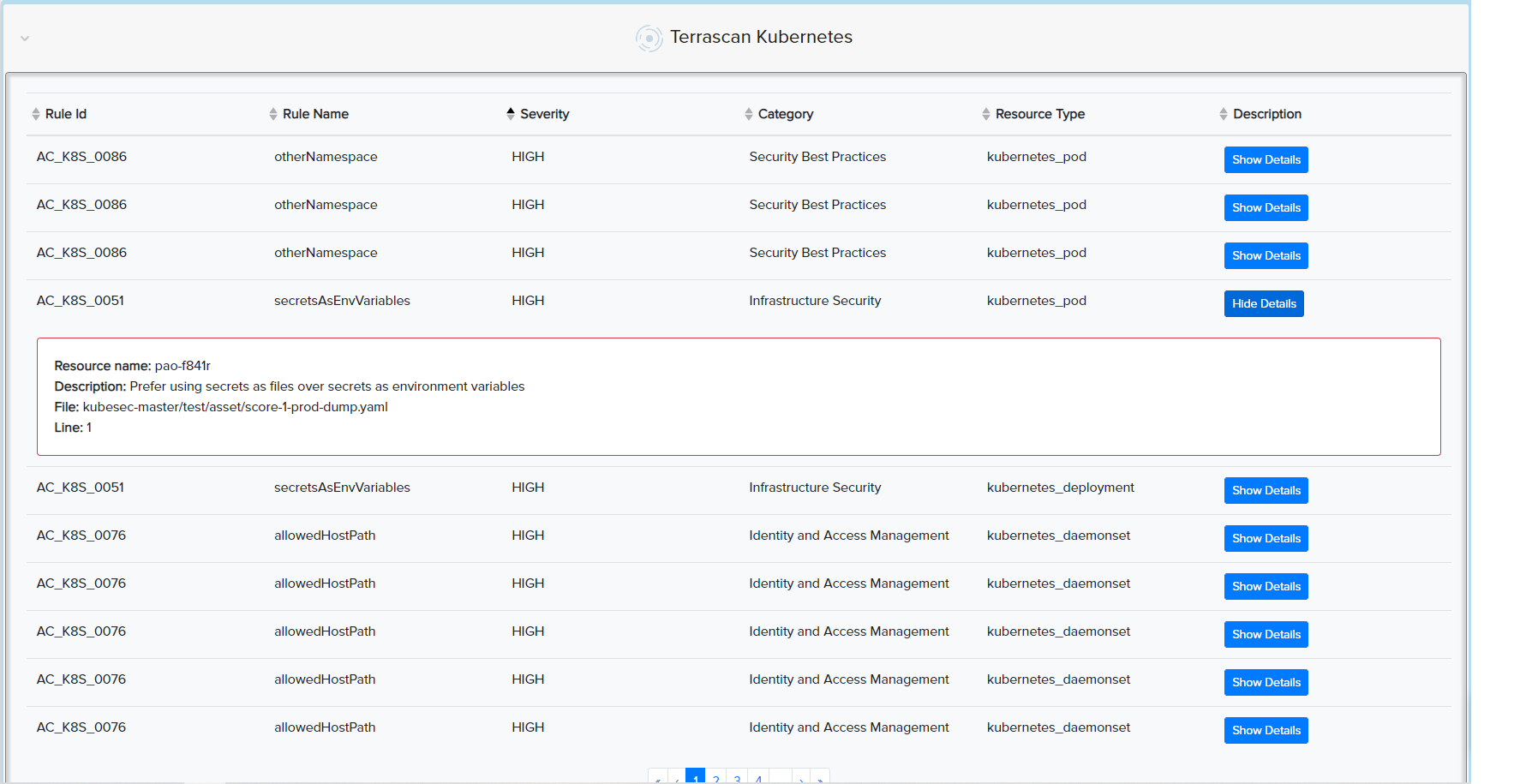
¶ ☸️ Kubernetes
- Analyzes K8s manifests (
.yaml) for best practices - Scans for insecure ports, capabilities, resource mismanagement
📸 Example:
¶ 🧱 Azure Resource Manager (ARM)
- Scans ARM templates for Azure services
- Validates RBAC roles, NSG rules, storage access policies
📸 Example: