¶ 📱 Mobile Security Scanning
¶ 🎥 Watch Video — Overview of features, modules, and use cases.
Mobile apps often handle personal data, sensitive information, and even remote control capabilities. They're widely used in IoT, FinTech, HealthTech, and beyond — making mobile security a top priority.
¶ 🚨 Why Mobile Apps Are a Prime Target
The more sensitive the data, the more valuable the target.
Common mobile app vulnerabilities:
- Weak server-side controls
- Insecure storage or communication
- Vulnerable third-party libraries
✅ Both backend and app-layer issues must be addressed to ensure full protection.
¶ ⚠️ Common Vulnerabilities in Mobile Applications
¶ 🔐 Server-Side Vulnerabilities, Injections, and IDOR
APIs and servers handle:
- Authentication
- User and financial data
- Backend logic
Top threats:
- SQL & Code Injections
- XSS
- IDOR attacks
- Misconfigurations
✅ Recommendations:
- Sanitize all input
- Use prepared statements
- Never trust client-side data
- Conduct regular black/grey/white box pentests
¶ 💾 Insecure Data Storage
Apps may store:
- Cookies, config files
- Credentials on SD card or internal memory
✅ Recommendations:
- Always encrypt sensitive data
- Use secure storage:
- iOS: Keychain
- Android: Keystore
- Minimize permissions
- Detect rooted/jailbroken devices
¶ 📡 Data Exchange Security & MITM Risks
Without proper encryption, attackers may intercept traffic using:
- ARP poisoning
- Packet sniffers
- Rogue Wi-Fi
✅ Recommendations:
- Enforce HTTPS (TLS)
- Pin certificates
- Avoid outdated TLS versions
¶ 📦 Third-Party Components
Many mobile apps depend on external libraries and SDKs.
Common issues:
- Vulnerable code
- Outdated dependencies
- Poorly maintained modules
✅ Recommendations:
- Audit third-party components regularly
- Follow secure coding standards
- Avoid untrusted packages
¶ 🛠️ Penetration Testing for Mobile Apps
Real-world simulations identify weaknesses in:
- Backend systems
- APIs
- Mobile app logic
¶ Example Server-Side Issues:
- Misconfigured servers
- Exposed services
- Access control flaws
¶ 📋 OWASP Top 10 – Web Vulnerabilities
- Injection
- Broken authentication
- Sensitive data exposure
- Broken access control
- XSS
- Security misconfig
- Insecure deserialization
- Vulnerable components
- Logging issues
¶ 📋 OWASP Top 10 – Mobile Vulnerabilities
- Improper platform usage
- Insecure storage & comms
- Broken authentication
- Weak cryptography
- Reverse engineering
- Code tampering
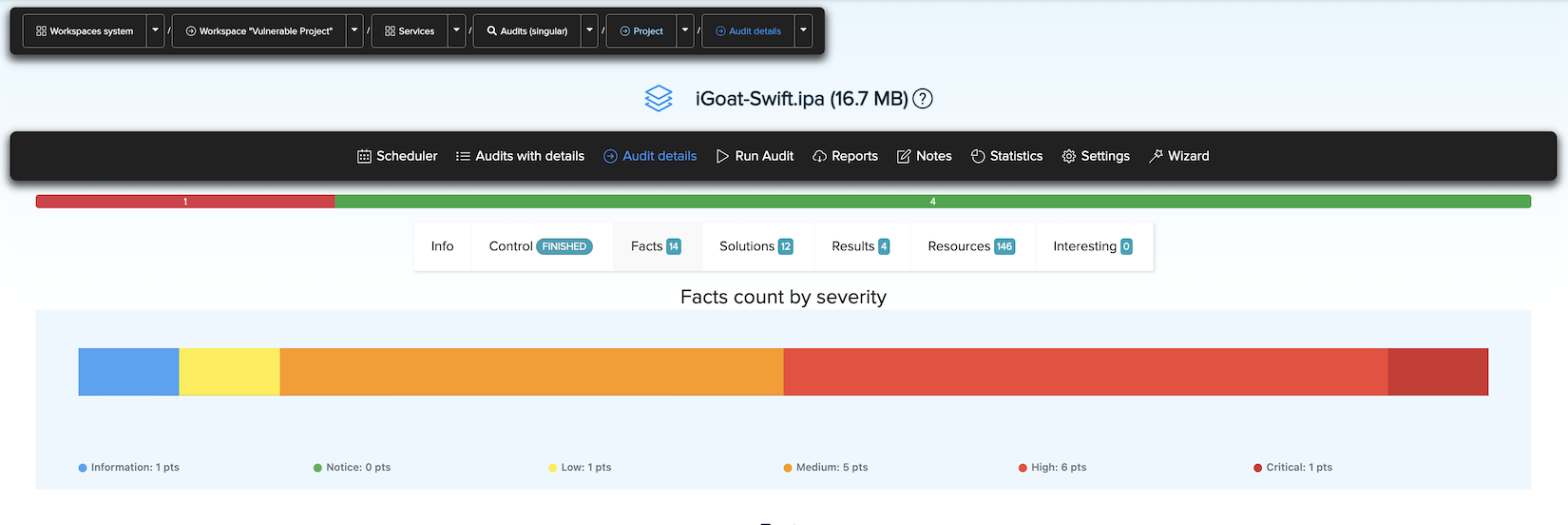
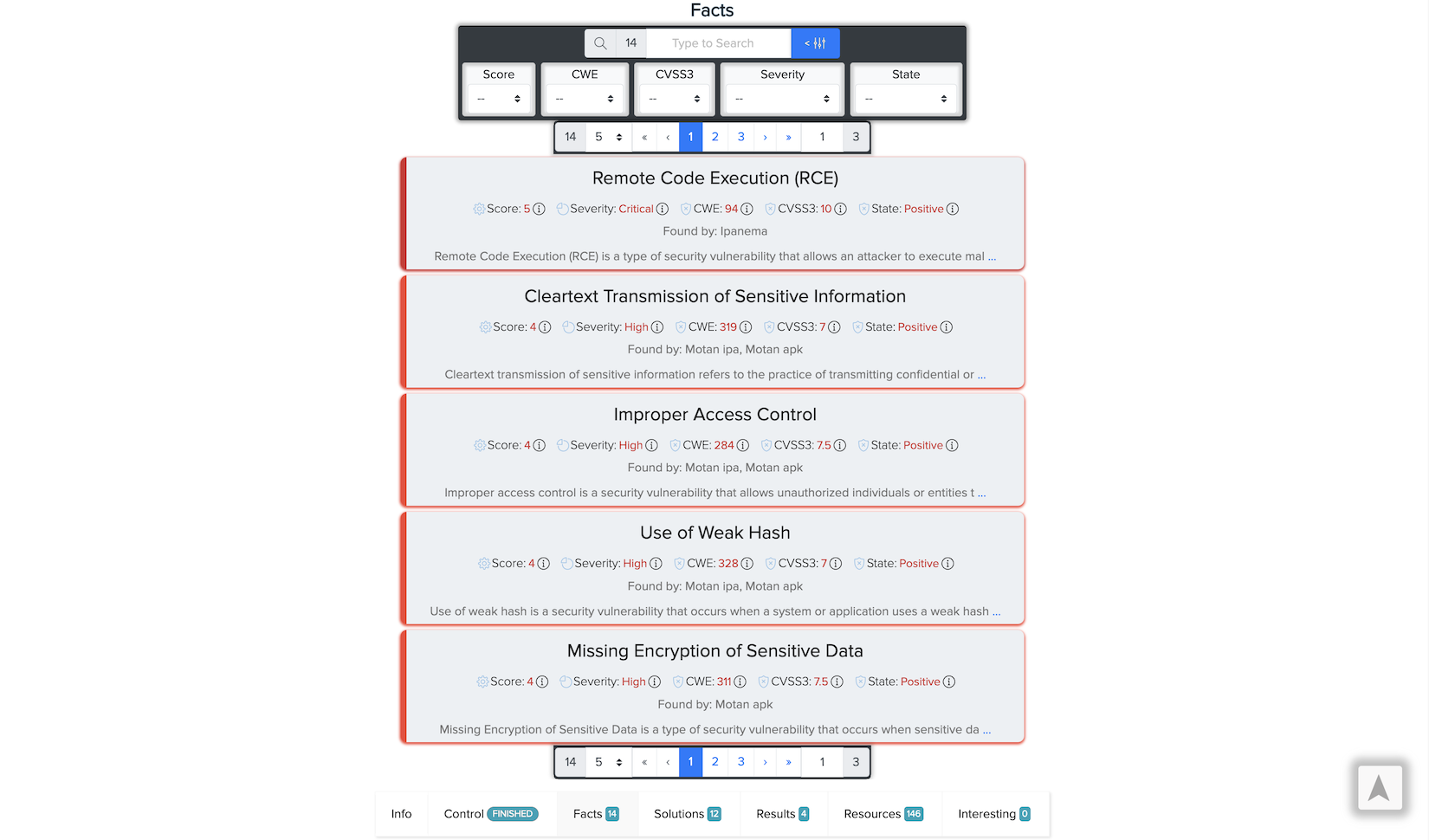
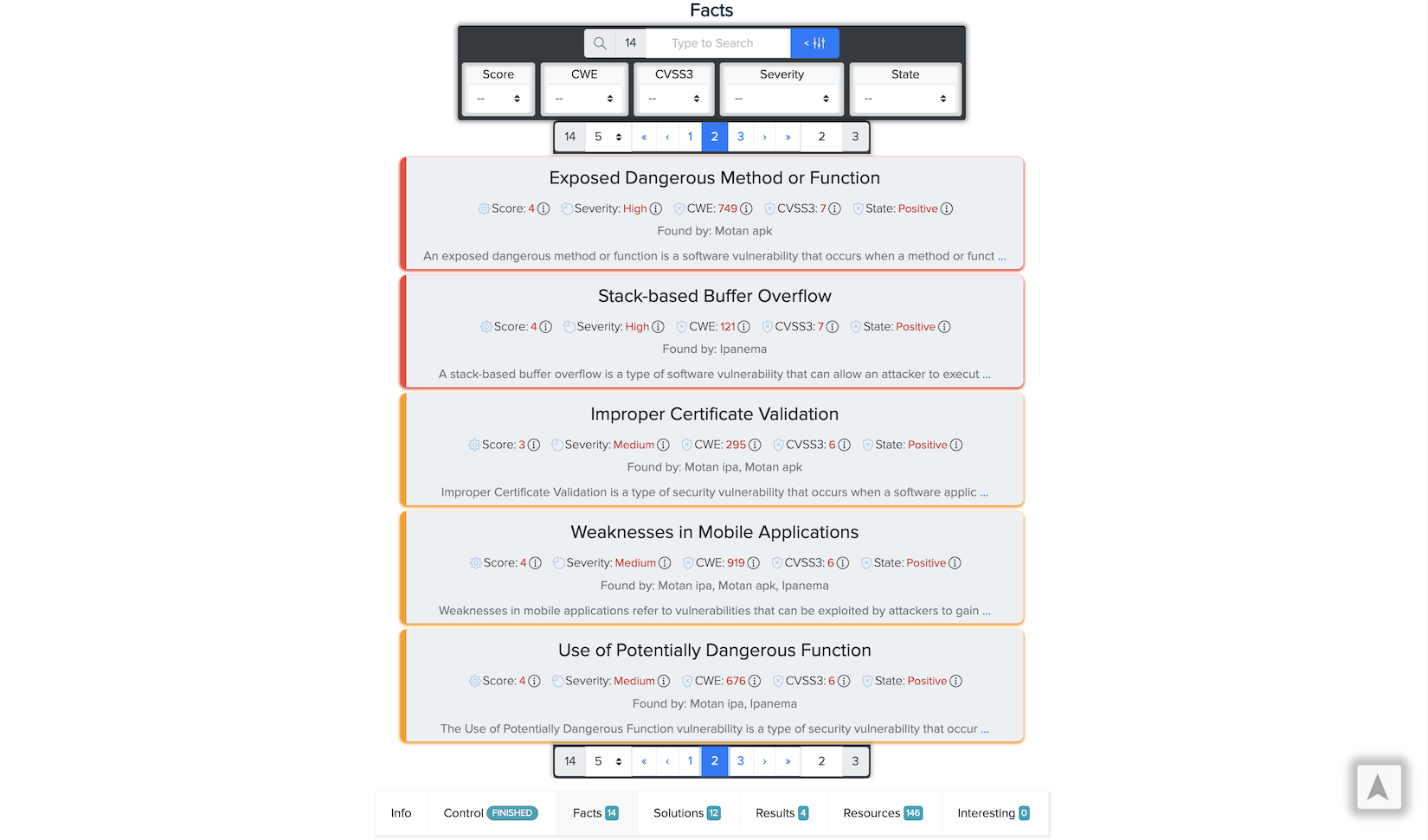
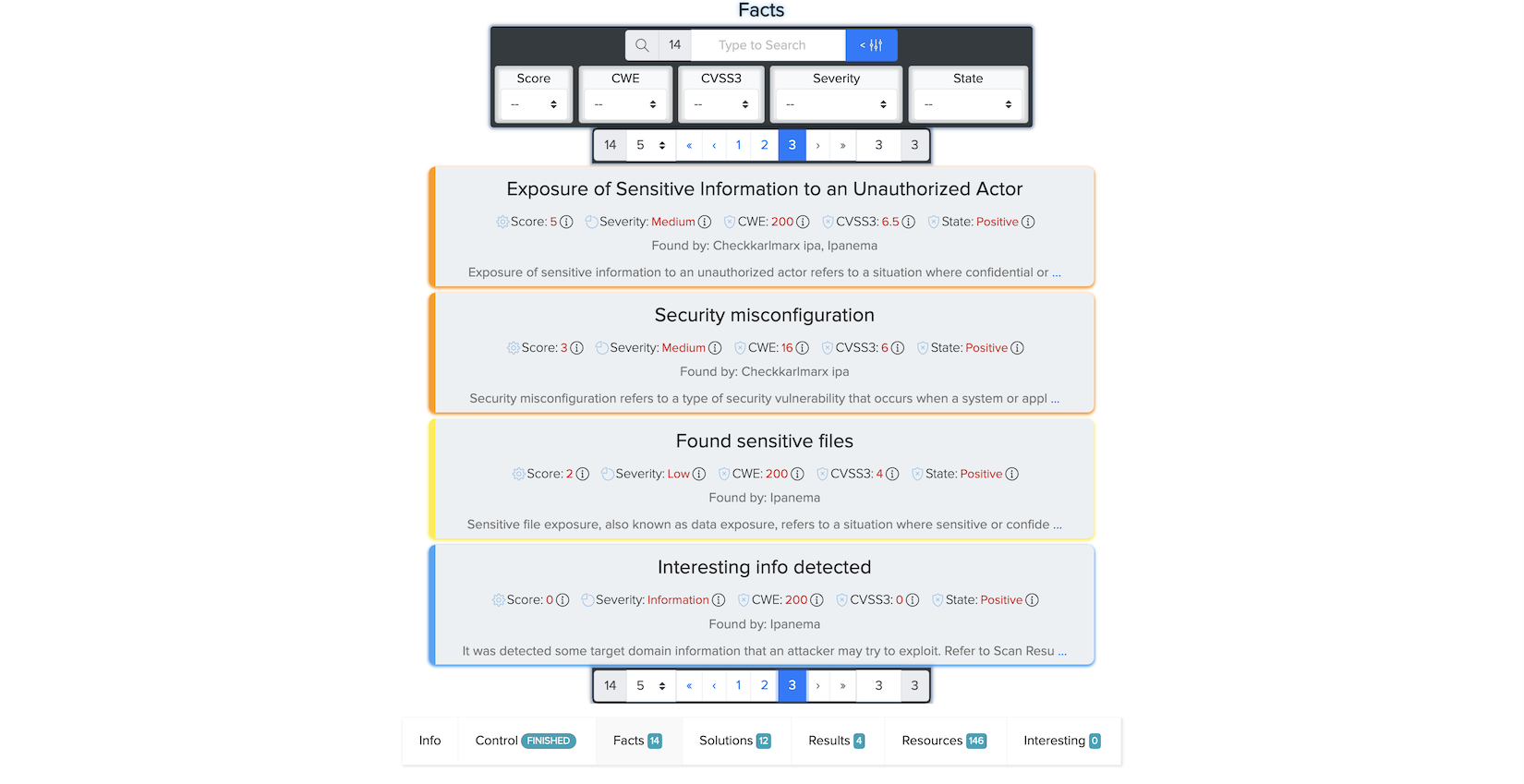
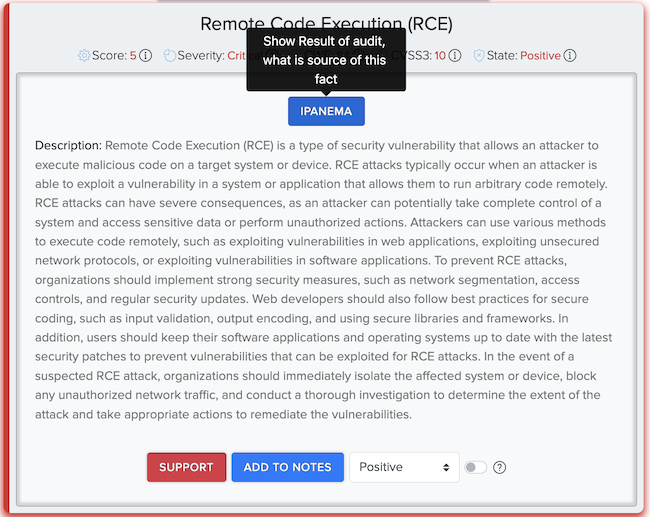
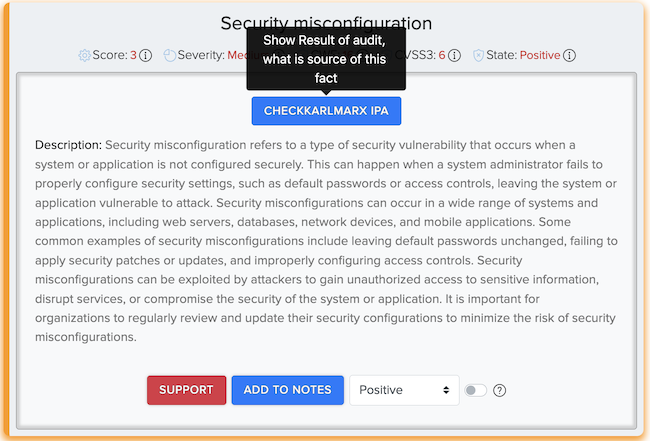
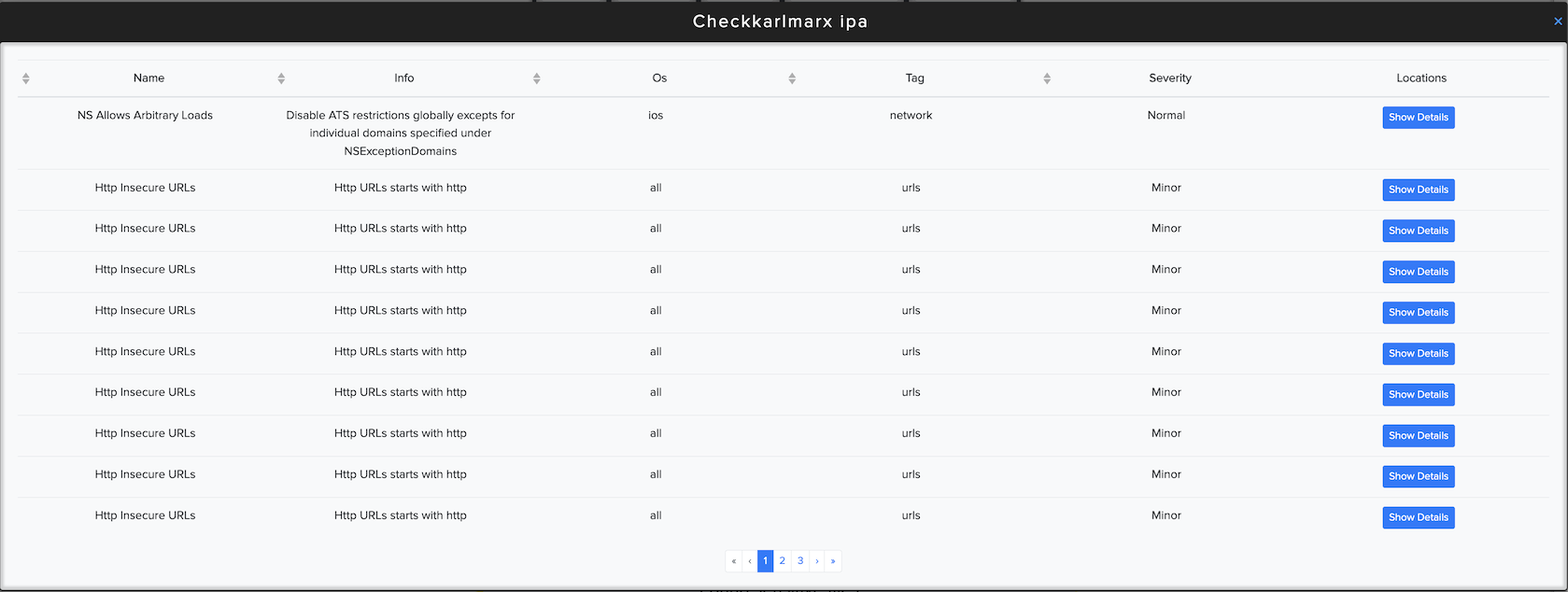
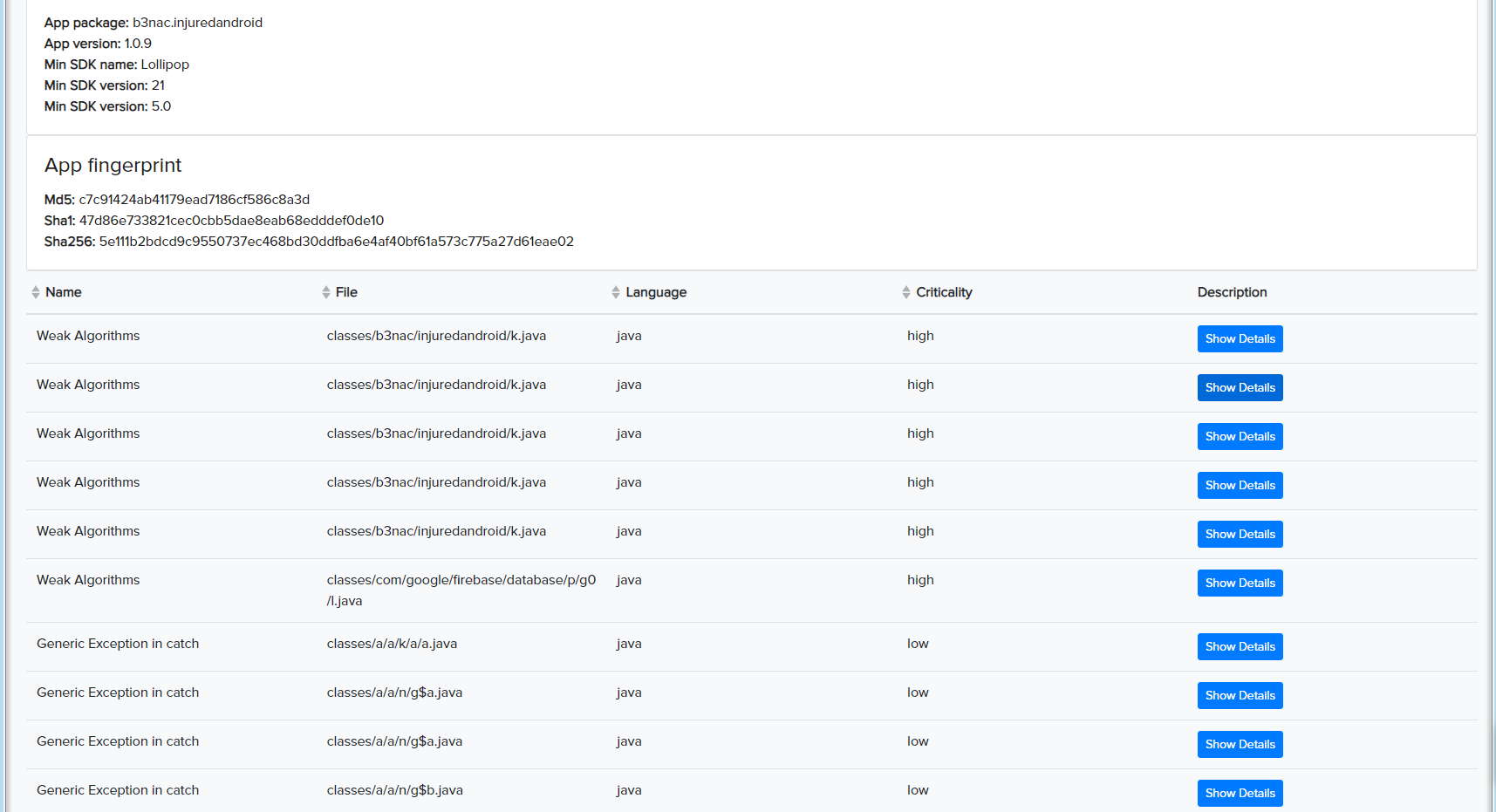
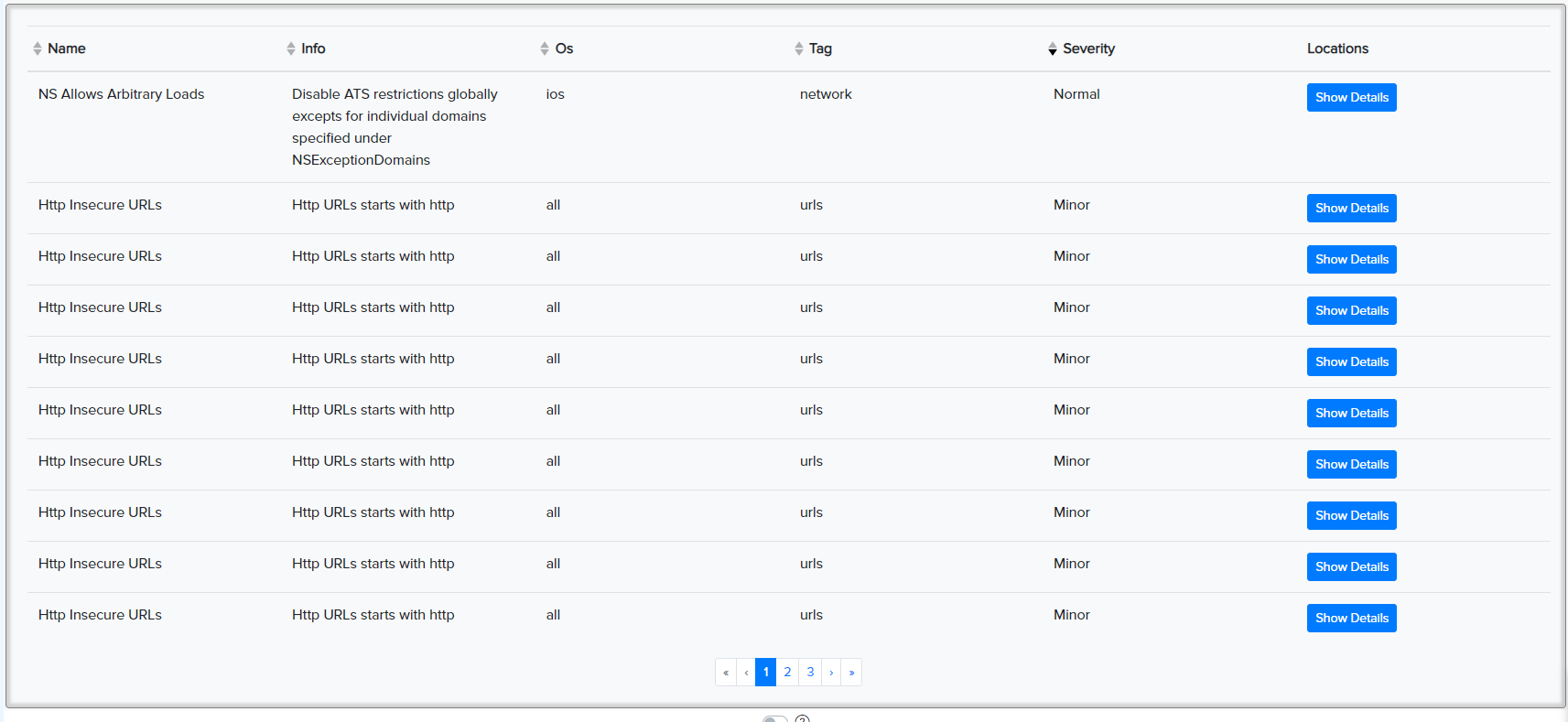
¶ ✅ Real Scan Example: Mobile App Facts
Vulnerabilities found in a CryEye mobile scan: