¶ Checkov
Checkov is a static code analysis tool for infrastructure-as-code.
It scans cloud infrastructure provisioned using Terraform, Terraform plan, Cloudformation, AWS SAM, Kubernetes, Helm charts,Kustomize, Dockerfile, Serverless, Bicep or ARM Templates and detects security and compliance misconfigurations using graph-based scanning.
Checkov also powers Bridgecrew, the developer-first platform that codifies and streamlines cloud security throughout the development lifecycle. Bridgecrew identifies, fixes, and prevents misconfigurations in cloud resources and infrastructure-as-code files.
¶ Features
- Over 1000 built-in policies cover security and compliance best practices for AWS, Azure and Google Cloud.
- Scans Terraform, Terraform Plan, CloudFormation, AWS SAM, Kubernetes, Dockerfile, Serverless framework, Bicep and ARM template files.
- Supports Context-awareness policies based on in-memory graph-based scanning.
- Supports Python format for attribute policies and YAML format for both attribute and composite policies.
- Detects AWS credentials in EC2 Userdata, Lambda environment variables and Terraform providers.
- Identifies secrets using regular expressions, keywords, and entropy based detection.
- Evaluates Terraform Provider settings to regulate the creation, management, and updates of IaaS, PaaS or SaaS managed through Terraform.
- Policies support evaluation of variables to their optional default value.
- Supports in-line suppression of accepted risks or false-positives to reduce recurring scan failures. Also supports global skip from using CLI.
- Output currently available as CLI, CycloneDX, JSON, JUnit XML, SARIF and github markdown and link to remediation guides.
¶ Findings Examples
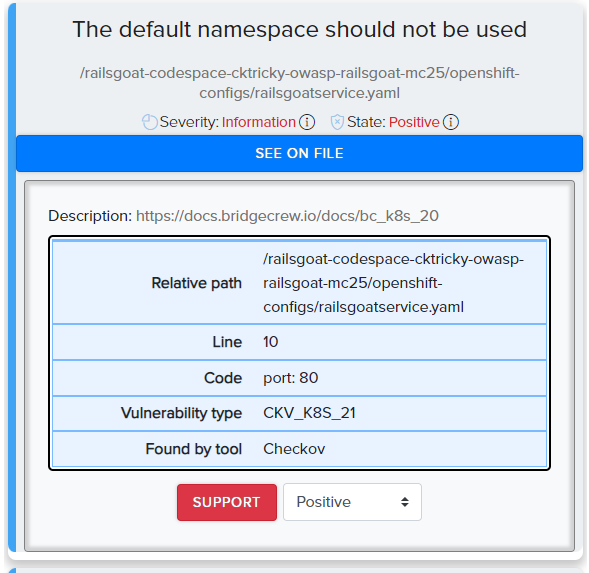
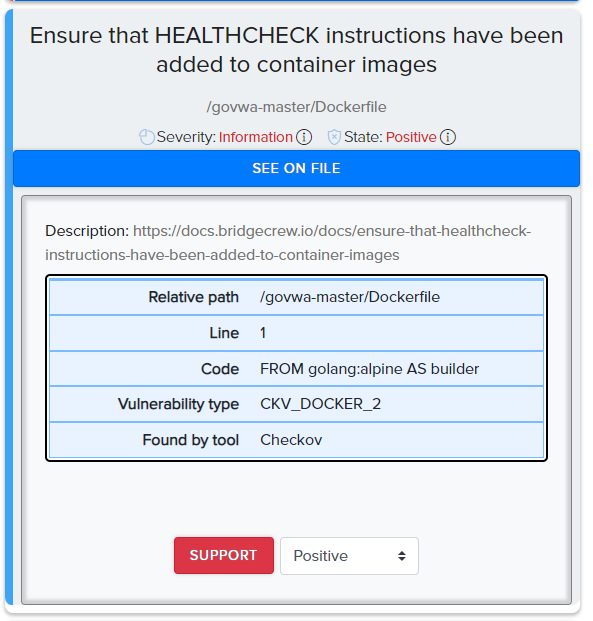
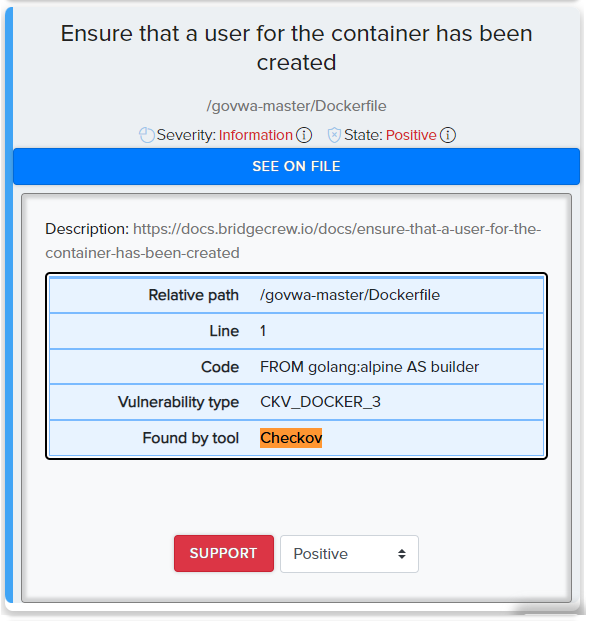
¶ Scan results in CLI
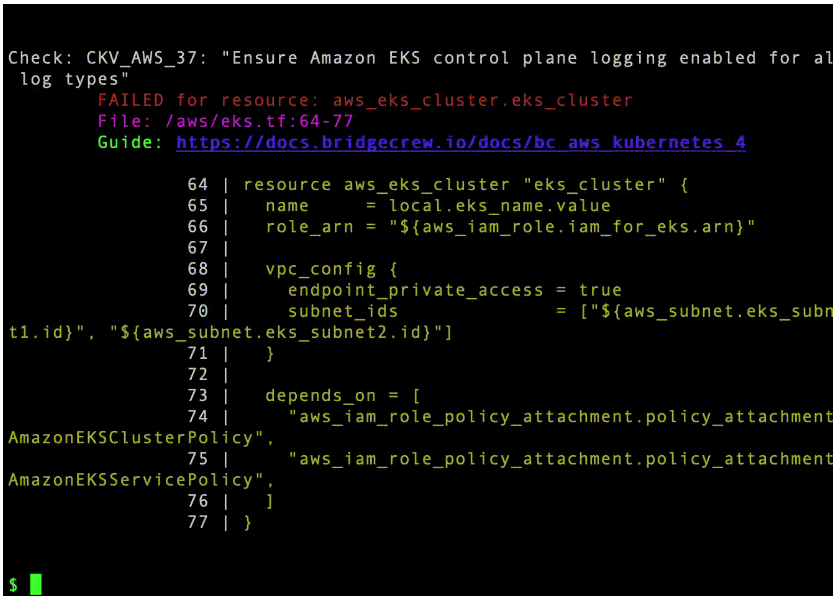
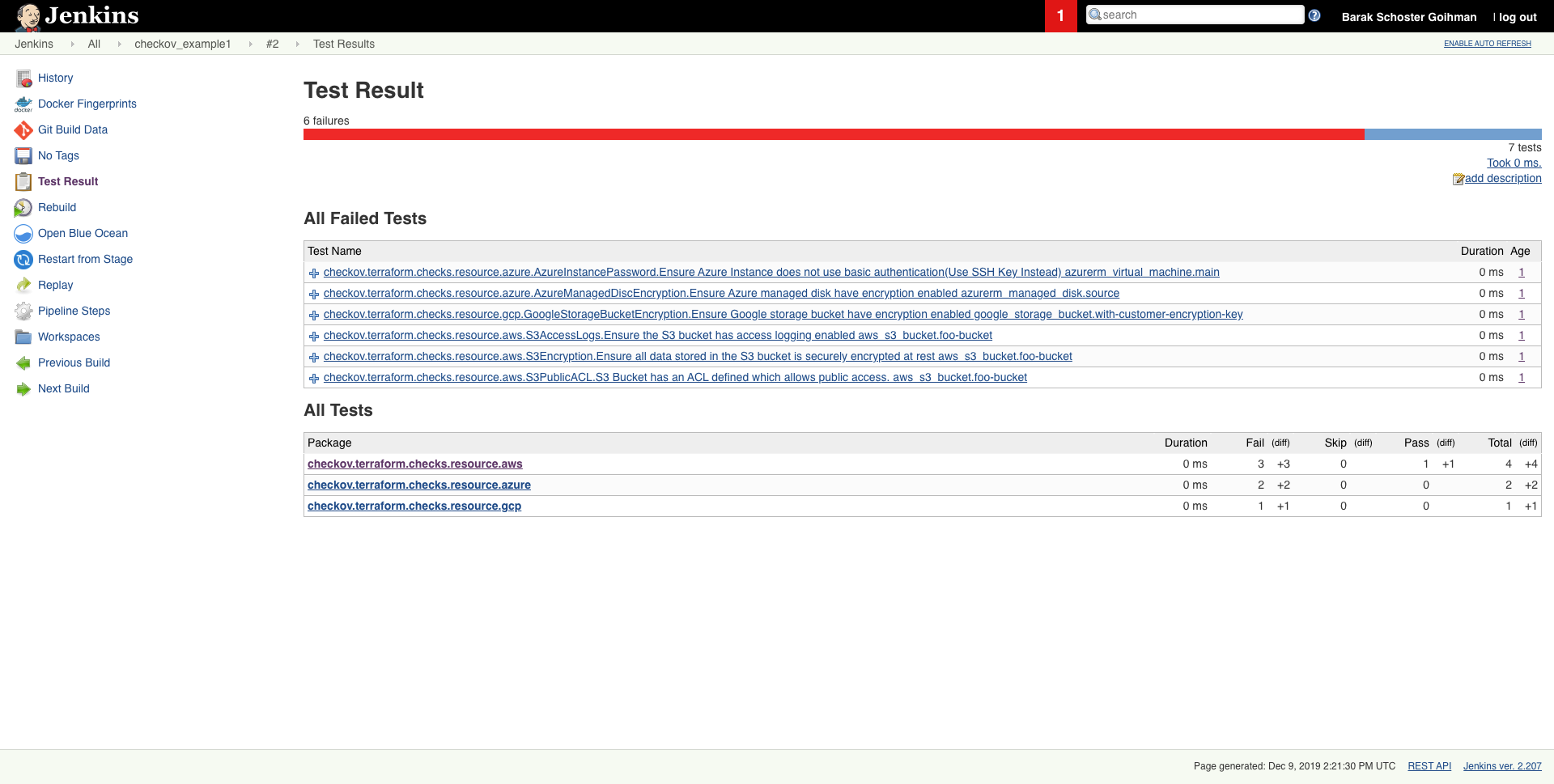
¶ Scheduled scan result in Jenkins
¶ Scan result sample (CLI)
Passed Checks: 1, Failed Checks: 1, Suppressed Checks: 0 Check: "Ensure all data stored in the S3 bucket is securely encrypted at rest" /main.tf: Passed for resource: aws_s3_bucket.template_bucket Check: "Ensure all data stored in the S3 bucket is securely encrypted at rest" /../regionStack/main.tf: Failed for resource: aws_s3_bucket.sls_deployment_bucket_name