¶ Hawkeye
https://github.com/hawkeyesec/scanner-cli
The Hawkeye scanner-cli is a project security, vulnerability and general risk highlighting tool. It is meant to be integrated into your pre-commit hooks and your pipelines.
The Hawkeye scanner-cli assumes that your directory structure is such that it keeps the toolchain's files on top level. Roughly, this is what it boils down to:
- Node.js projects have a package.json on top level
- Ruby projects will have a Gemfile on top level
- Python projects will have a requirements.txt on top level
- PHP projects will have a composer.lock on top level
- Java projects will have a build (gradle) or target (maven) folder, and include .java and .jar files
- Kotlin projects will have a build (gradle) or target (maven) folder, and include .kt and .jar files
- Scala projects will have a target (sbt with sbt-native-packager or sbt-assembly plugins) folder, and include .scala and .jar files. Check this repo for a running demo.
- Rust projects will have a Cargo.toml on top level
This is not exhaustive as sometimes tools require further files to exist. To understand how the modules decide whether they can handle a project, please check the How it works section and the modules folder.
¶ Findings Examples
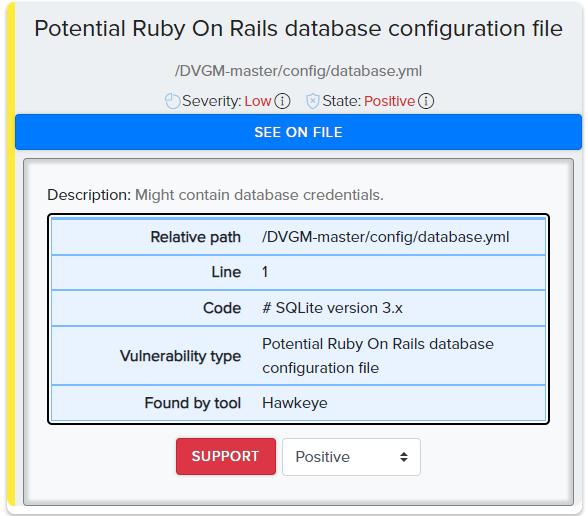
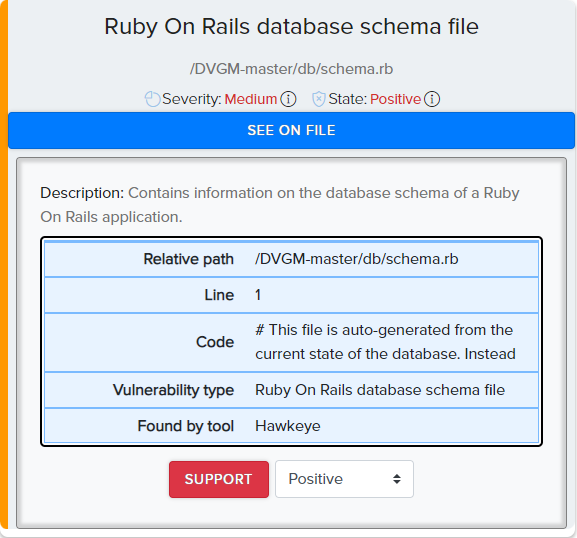
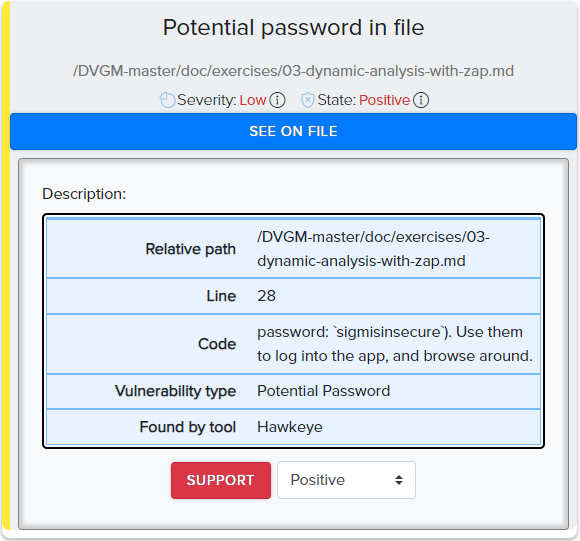
¶ Modules
Modules are basically little bits of code that either implement their own logic, or wrap a third party tool and standardise the output. They only run if the required criteria are met. For example: The npm outdated module would only run if a package.json is detected in the scan target - as a result, you don't need to tell Hawkeye what type of project you are scanning.
¶ Generic Modules
- files-ccnumber: Scans for suspicious file contents that are likely to contain credit card numbers
- files-contents: Scans for suspicious file contents that are likely to contain secrets
- files-entropy: Scans files for strings with high entropy that are likely to contain passwords. Entropy scanning is disabled by default because of the high number of false positives. It is useful to scan codebases every now and then for keys, in which case please run it please using the -m files-entropy switch.
- files-secrets: Scans for suspicious filenames that are likely to contain secrets
¶ Java / Kotlin / Scala
- java-find-secbugs: Finds common security issues in Java code with findsecbugs
- java-owasp: Scans Java projects for gradle/maven dependencies with known vulnerabilities with the OWASP dependency checker
¶ Node.js
- node-npmaudit: Checks node projects for dependencies with known vulnerabilities with npm audit
- node-npmoutdated: Checks node projects for outdated npm modules with npm outdated
- node-yarnaudit: Checks yarn projects for dependencies with known vulnerabilities with yarn audit
- node-yarnoutdated: Checks node projects for outdated yarn modules with yarn outdated
¶ PHP
- php-security-checker: Checks whether the composer.lock contains dependencies with known vulnerabilities using security-checker
¶ Python
- python-bandit: Scans for common security issues in Python code with bandit.
- python-piprot: Scans python dependencies for out of date packages with piprot
- python-safety: Checks python dependencies for known security vulnerabilities with the safety tool.
¶ Ruby
- ruby-brakeman: Statically analyzes Rails code for security issues with Brakeman.
- ruby-bundler-scan: Scan for Ruby gems with known vulnerabilities using bundler
¶ Rust
- rust-cargoaudit: Checks whether the Cargo.lock contains dependencies with known vulnerabilities using cargo audit