¶ Darknet Monitoring
¶ 🎥 Watch Video — Overview of features, modules, and use cases
¶ 🛡️ Description
Darknet Monitoring helps collect and analyze data from various darknet text feeds.
The darknet is a hidden part of the internet (e.g., Tor network) not indexed by traditional search engines. It is often used for anonymous communication, forums, marketplaces, and potentially illegal activity.
What does Darknet Monitoring track?
- Forums & Marketplaces – Discussions, illicit goods/services
- Threat Intelligence – Cyberattacks, exploits, malware
- Data Leaks – Stolen credentials, private info
- Illegal Activities – Drugs, human trafficking, counterfeits
- Insider Info – Leaks involving companies or government
- Cybersecurity Research – TTPs (tactics, techniques, procedures)
Use cases:
- Real-time threat intelligence
- Early warning of breaches
- Cybercrime investigations
- Data leak discovery and response
- Risk mitigation
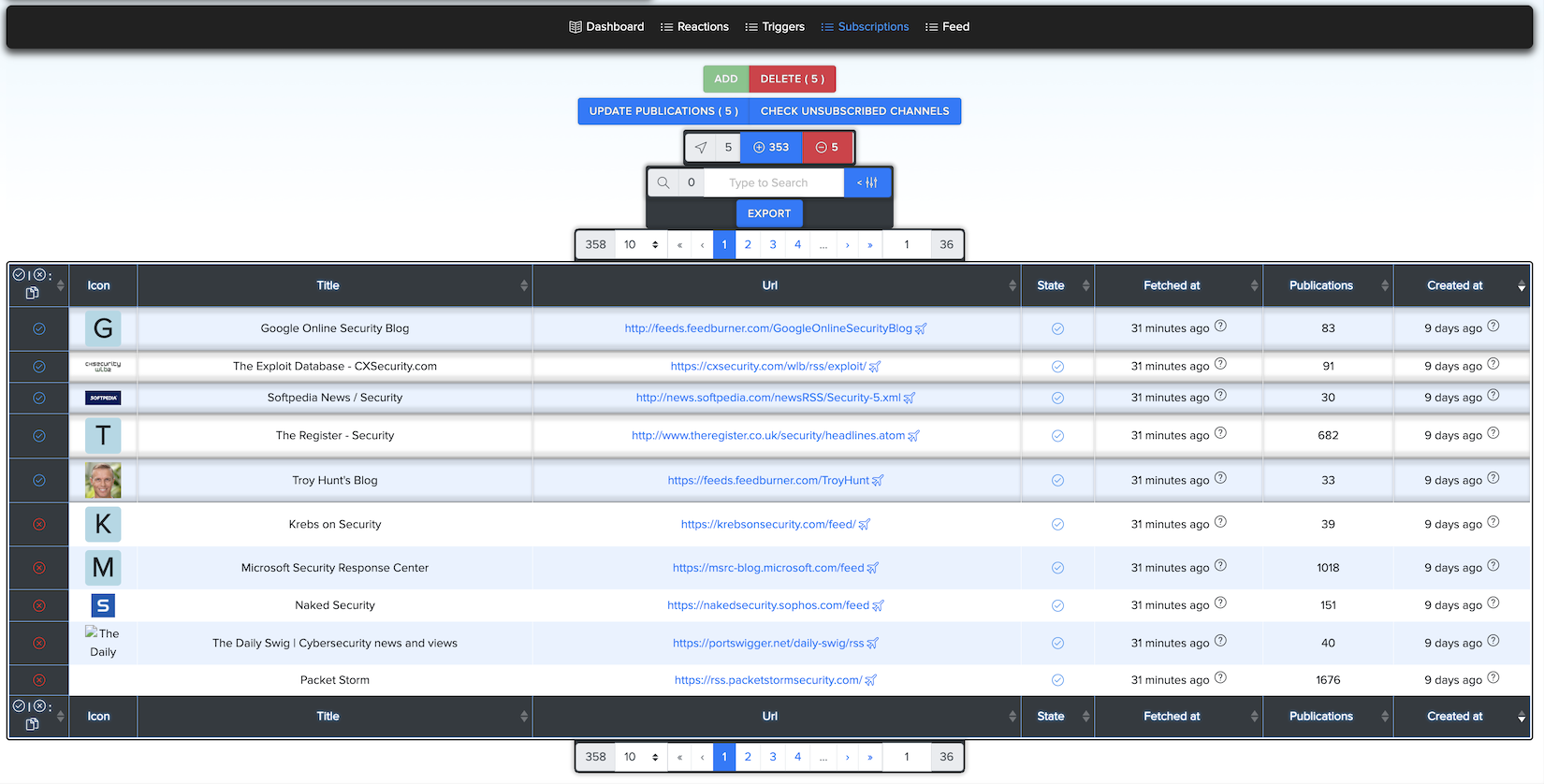
¶ 📡 Subscriptions and Channels
To start using Darknet Monitoring, you must subscribe to text feed channels.
¶ 🔘 Predefined Channels
You can subscribe to existing channels from the system list.
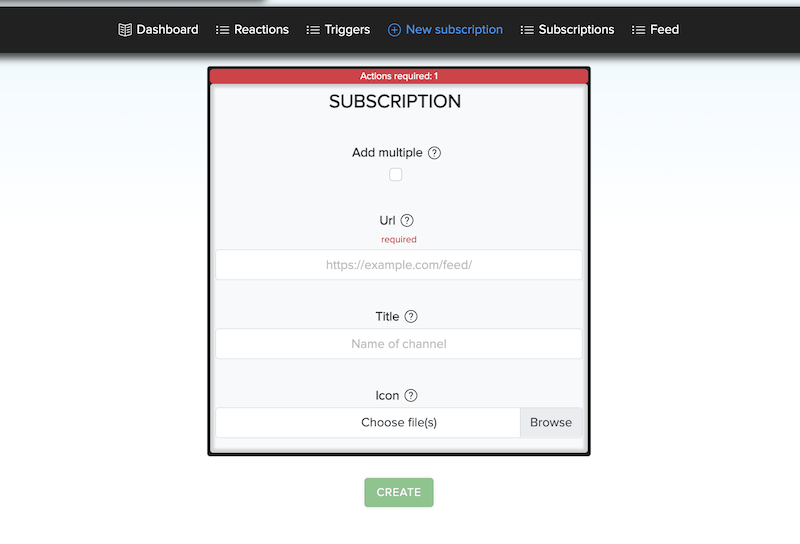
¶ ➕ Add Custom Channels
You can create your own subscriptions with a custom name and icon.
You can also bulk-add multiple feeds at once:
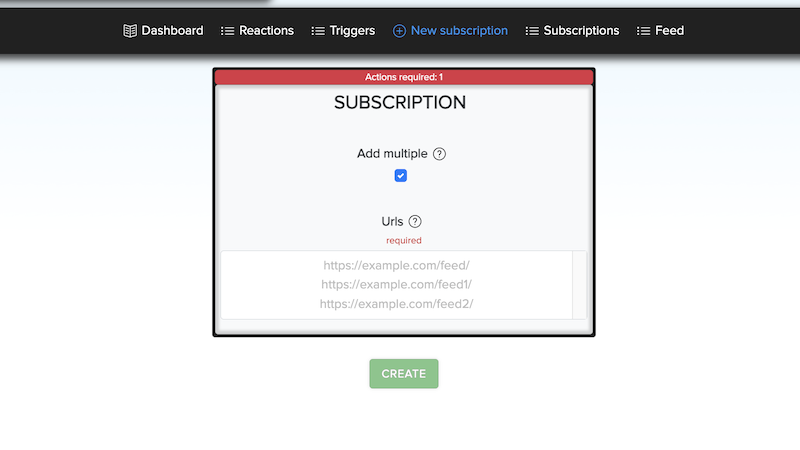
ℹ️ Duplicate feeds are automatically filtered out.
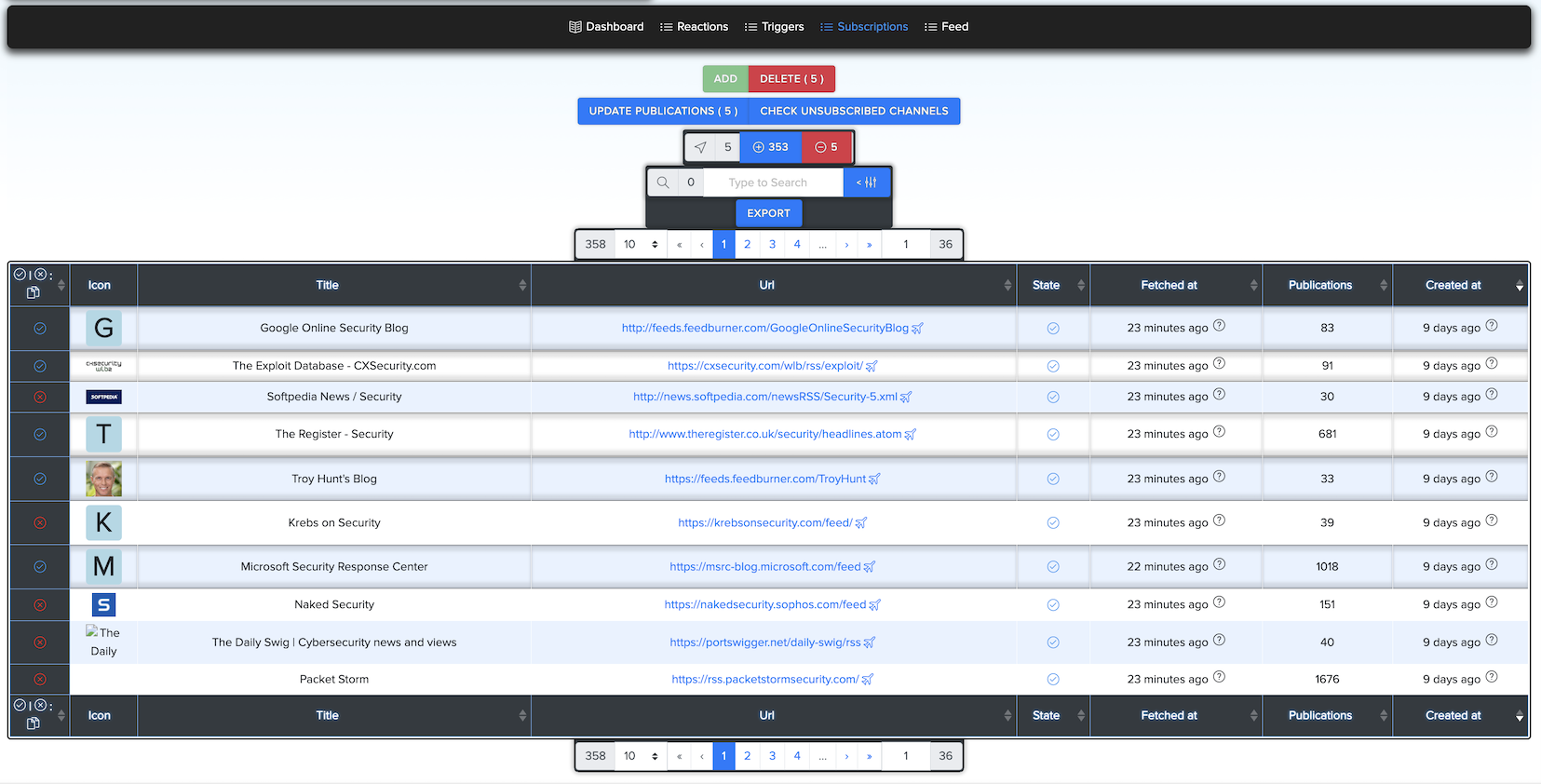
¶ 🕓 Feed History
CryEye stores the history of all publications — even if the source deletes them.
- If a channel already exists in the system, you get access to its historical data.
- This ensures no publication is lost after removal.
¶ 🔄 Feed Updates
- New posts are fetched regularly.
- You can also manually refresh subscriptions if needed.
¶ 📰 Feed View
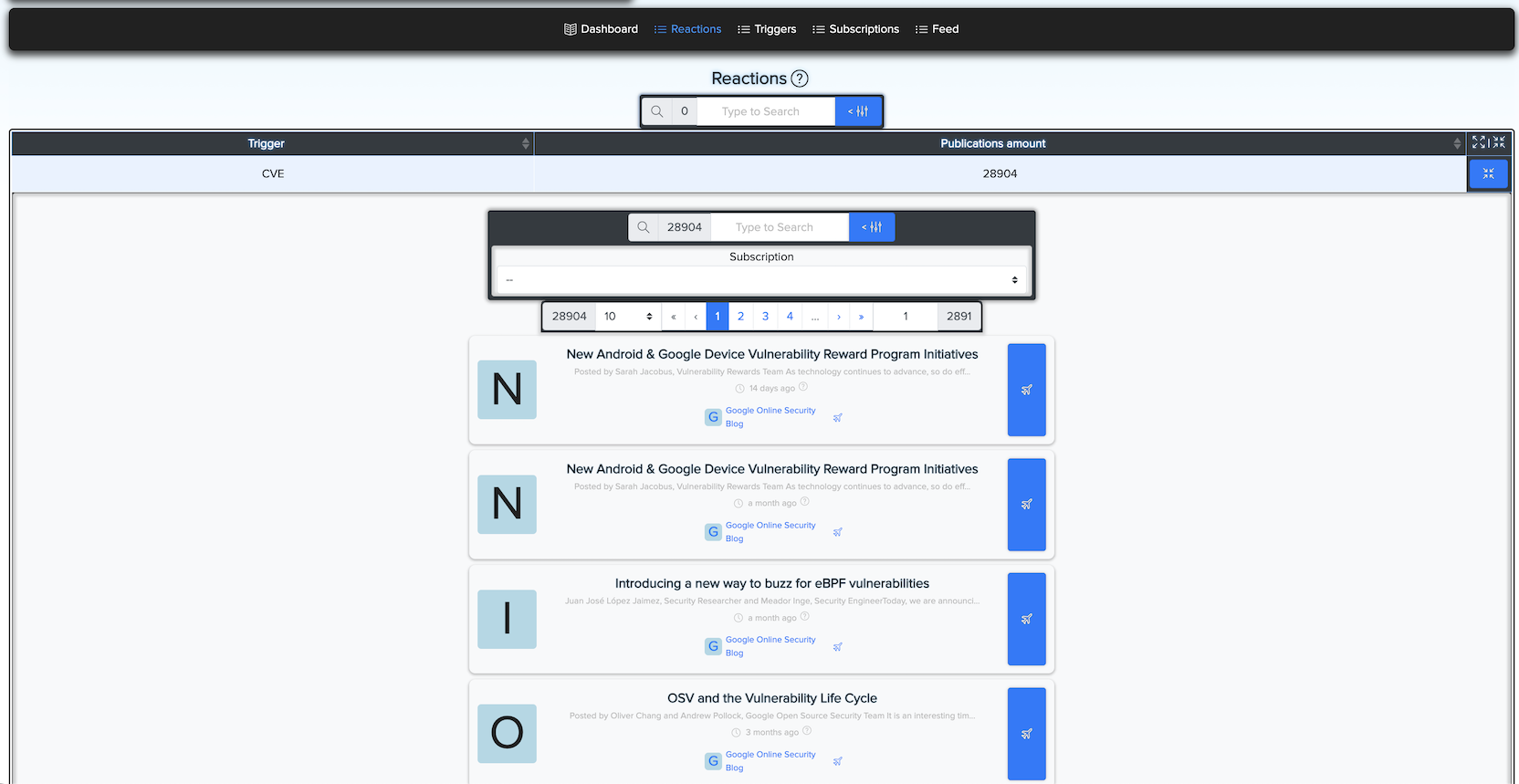
View recent posts from subscribed feeds. Each post includes a link to the original darknet source.
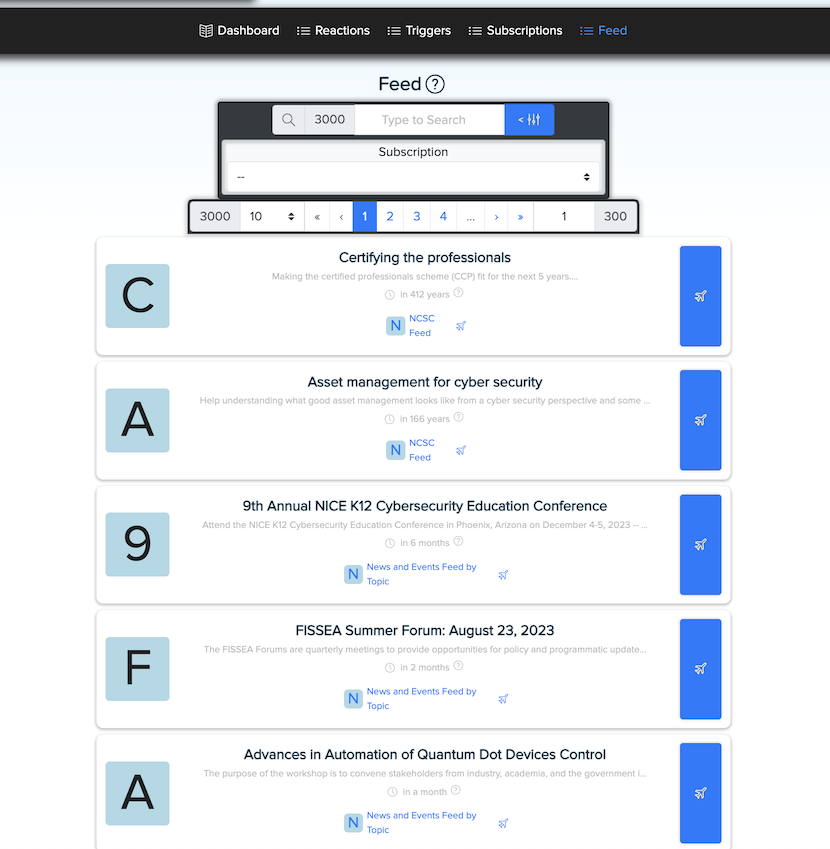
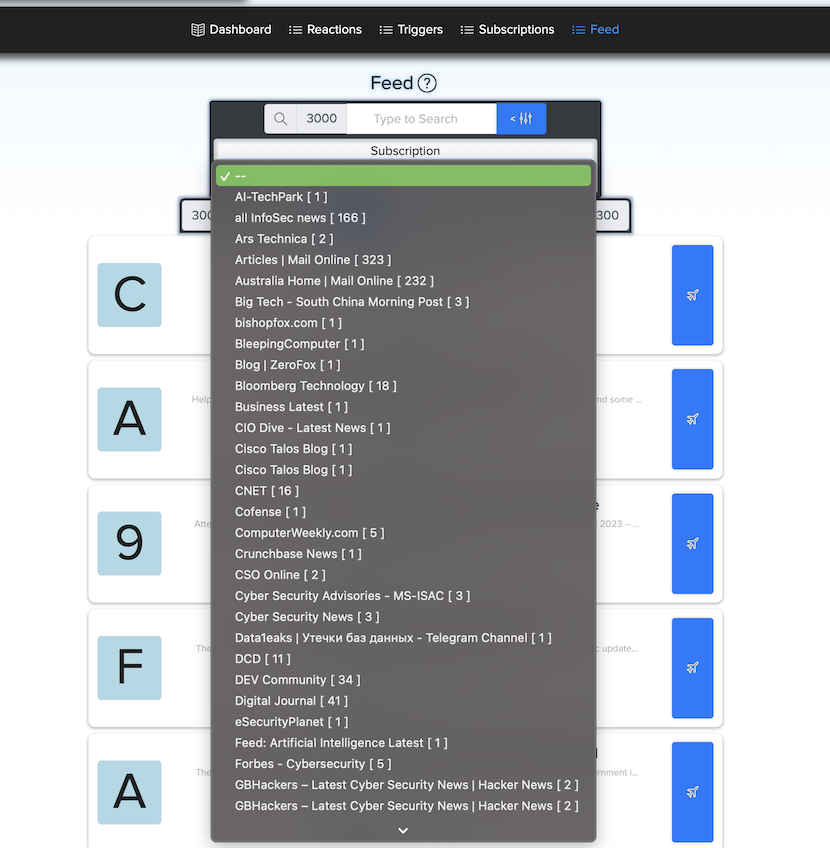
You can filter posts by subscription:
¶ 🎯 Triggers and Reactions
You can track specific keywords or patterns appearing in darknet publications.
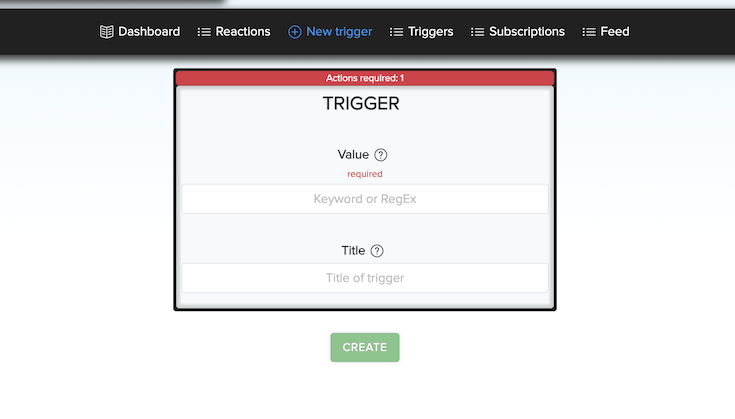
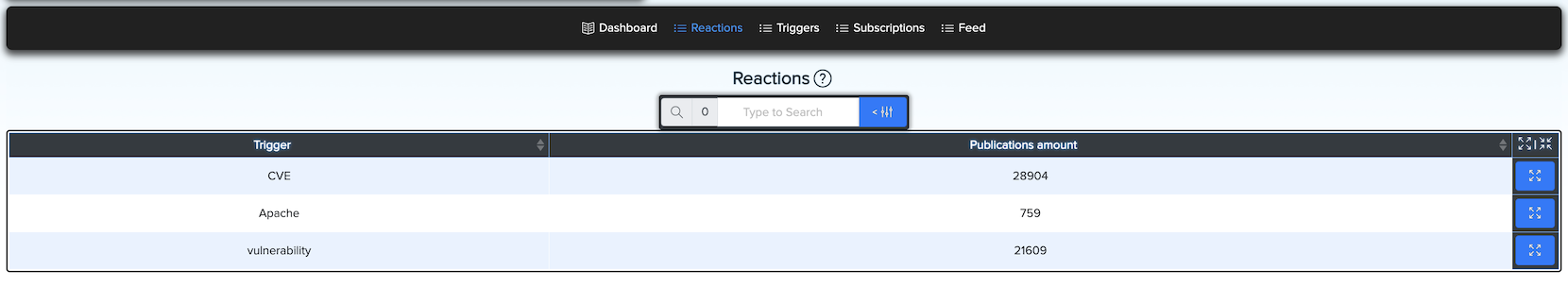
¶ 🔔 Triggers
Triggers can be:
- Keywords
- Regular expressions (regex, lowercase)
- Each trigger can have a descriptive title for clarity
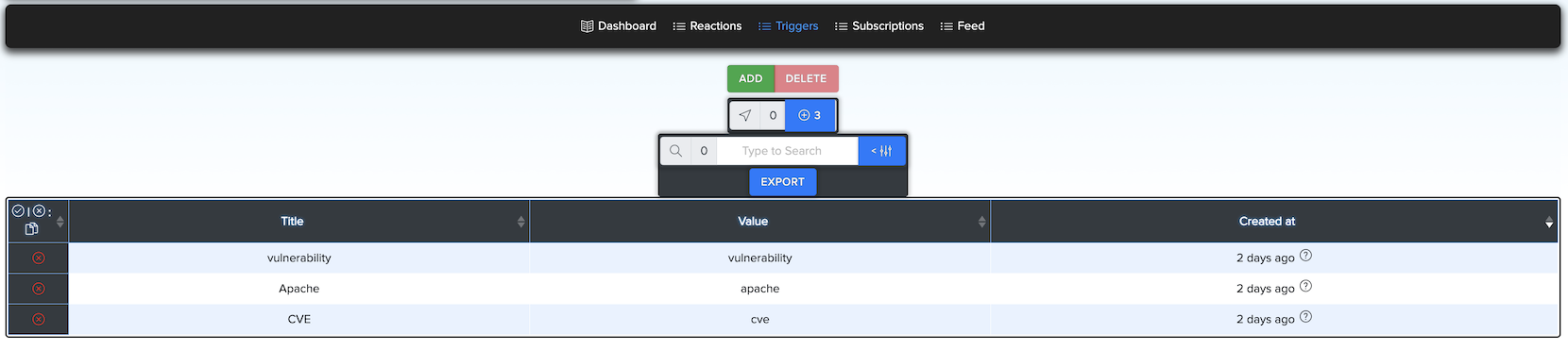
¶ ⚡ Reactions
Reactions are posts that match one or more triggers.
¶ 🧠 How Matching Works
CryEye searches for trigger matches in:
- The content of each publication
- All text is analyzed in lowercase
- Regex and keywords are applied to all available metadata
¶ 🧭 Quick Start
- Subscribe to one or more darknet channels
- Review the feed and history
- Create custom triggers (keywords or regex)
- Monitor reactions and receive alerts on important matches