¶ ADRecon
https://github.com/sense-of-security/ADRecon
¶ ADRecon: Active Directory Recon
ADRecon is a tool which extracts and combines various artefacts (as highlighted below) out of an AD environment. The information can be presented in a specially formatted Microsoft Excel report that includes summary views with metrics to facilitate analysis and provide a holistic picture of the current state of the target AD environment.
The tool is useful to various classes of security professionals like auditors, DFIR, students, administrators, etc. It can also be an invaluable post-exploitation tool for a penetration tester.
It can be run from any workstation that is connected to the environment, even hosts that are not domain members. Furthermore, the tool can be executed in the context of a non-privileged (i.e. standard domain user) account. Fine Grained Password Policy, LAPS and BitLocker may require Privileged user accounts. The tool will use Microsoft Remote Server Administration Tools (RSAT) if available, otherwise it will communicate with the Domain Controller using LDAP.
The following information is gathered by the tool:
- Forest
- Domain
- Trusts
- Sites
- Subnets
- Default and Fine Grained Password Policy (if implemented)
- Domain Controllers, SMB versions, whether SMB Signing is supported and FSMO roles
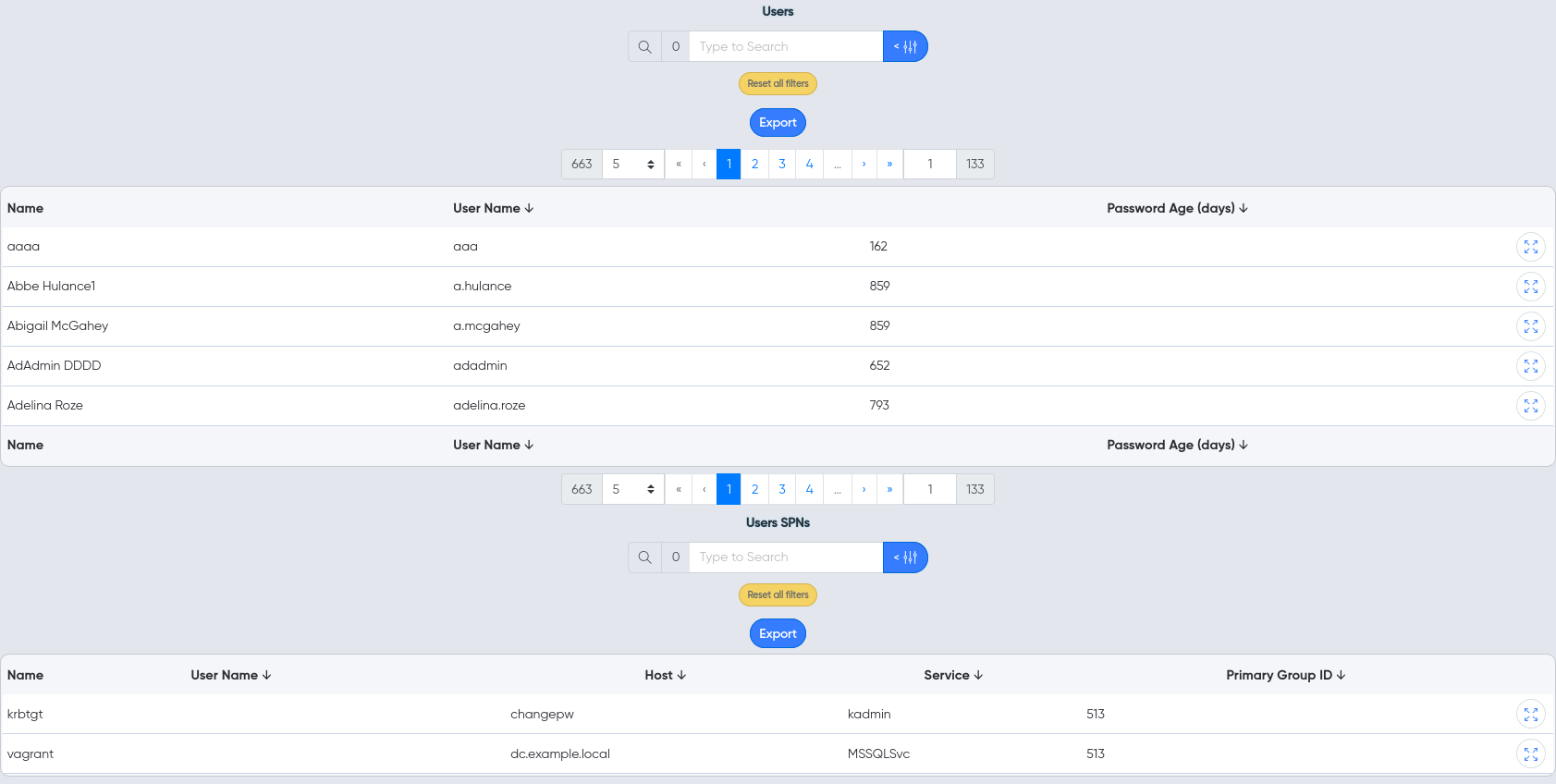
- Users and their attributes
- Service Principal Names (SPNs)
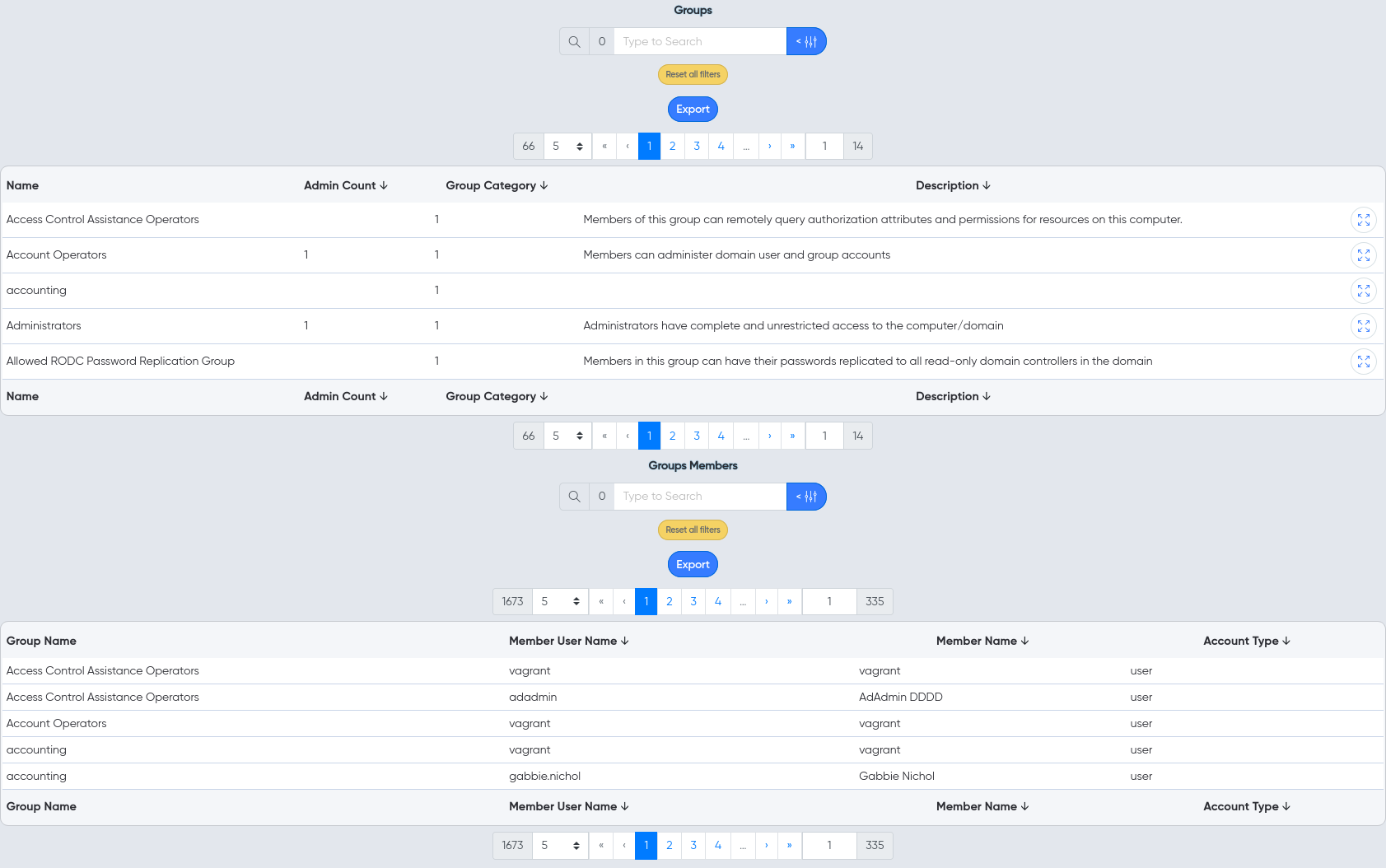
- Groups and memberships
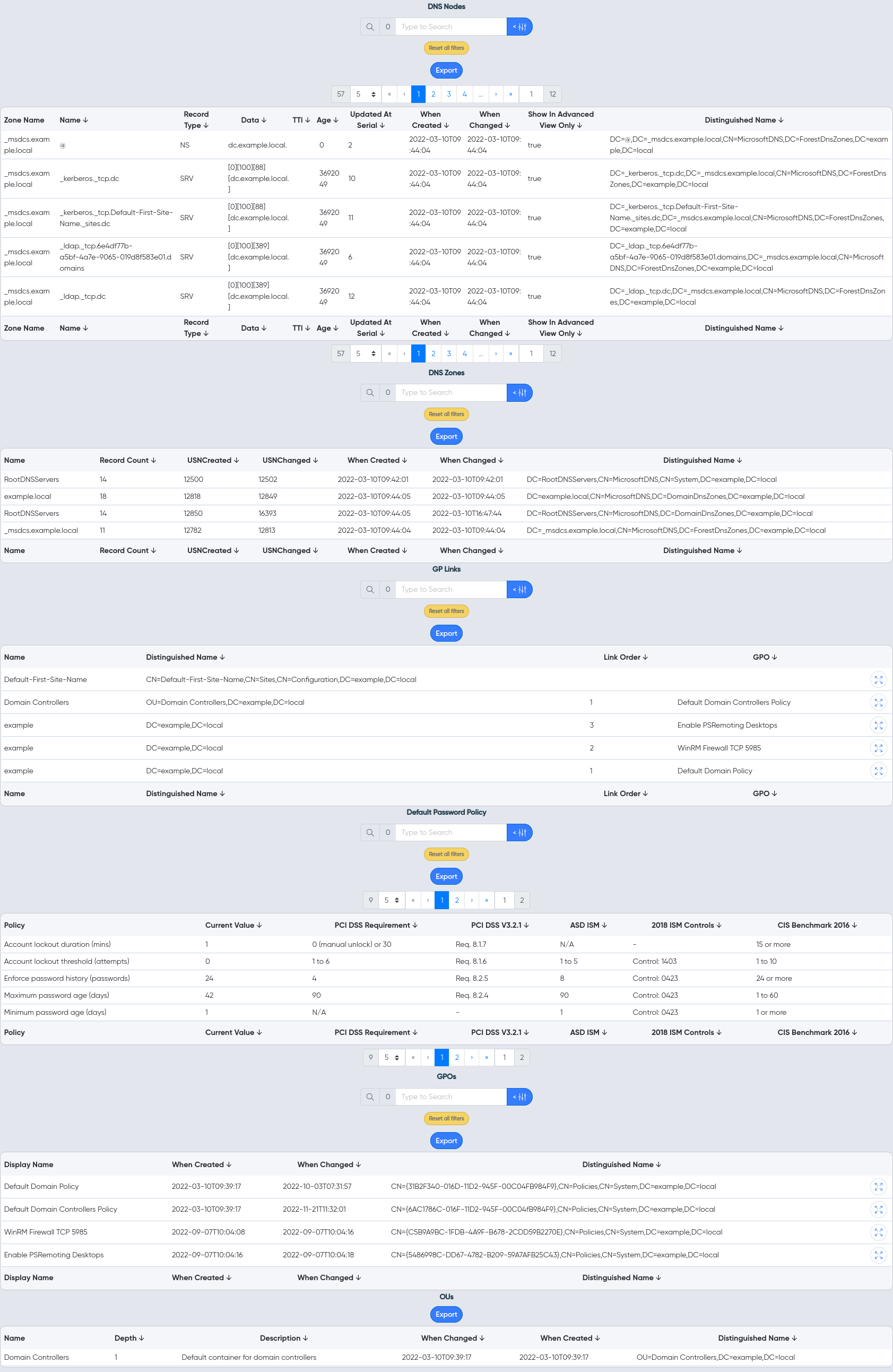
- Organizational Units (OUs)
- GroupPolicy objects and gPLink details
- DNS Zones and Records
- Printers
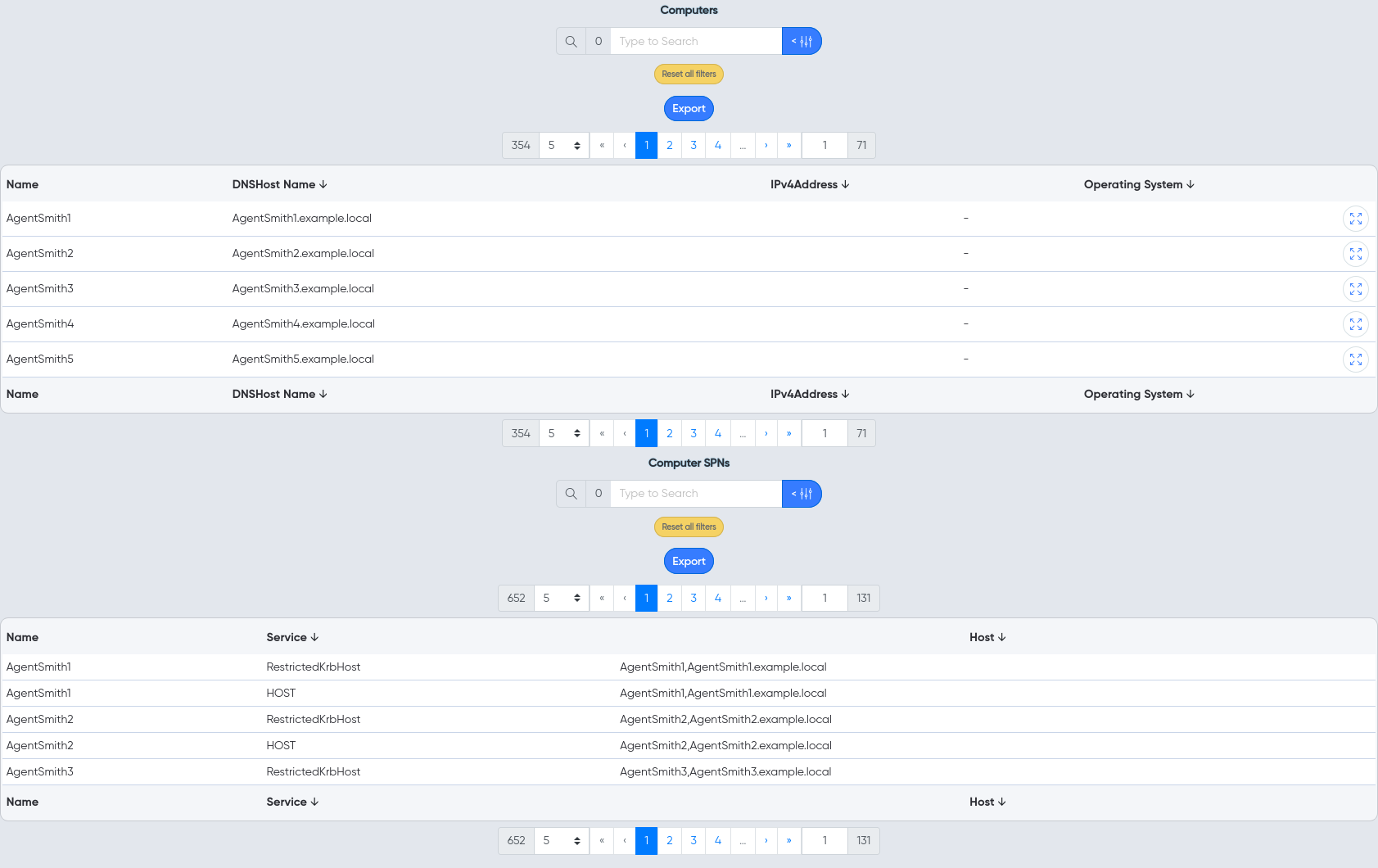
- Computers and their attributes
- PasswordAttributes (Experimental)
- LAPS passwords (if implemented)
- BitLocker Recovery Keys (if implemented)
- ACLs (DACLs and SACLs) for the Domain, OUs, Root Containers, GPO, Users, Computers and Groups objects
- GPOReport (requires RSAT)
- Kerberoast (not included in the default collection method)
- Domain accounts used for service accounts (requires privileged account and not included in the default collection method)
¶ Usage
PS C:\> .\ADRecon.ps1
¶ LICENSE
ADRecon is licensed under the GNU Affero General Public License v3.0.
ADRecon is a tool which gathers information about the Active Directory and generates a report which can provide a holistic picture of the current state of the target AD environment.
Copyright (C) Sense of Security
This program is free software: you can redistribute it and/or modify it under the terms of the GNU Affero General Public License as published by the Free Software Foundation, either version 3 of the License, or (at your option) any later version.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU Affero General Public License for more details.
You should have received a copy of the GNU Affero General Public License along with this program. If not, see http://www.gnu.org/licenses/.
This program borrows and uses code from many sources. All attempts are made to credit the original author. If you find that your code is used without proper credit, please shoot an insult to @prashant3535, Thanks.
¶ Screenshots of results
¶ Users
¶ Computers
¶ Groups
¶ Other
¶ Host
¶ How to start?
You can find this here.