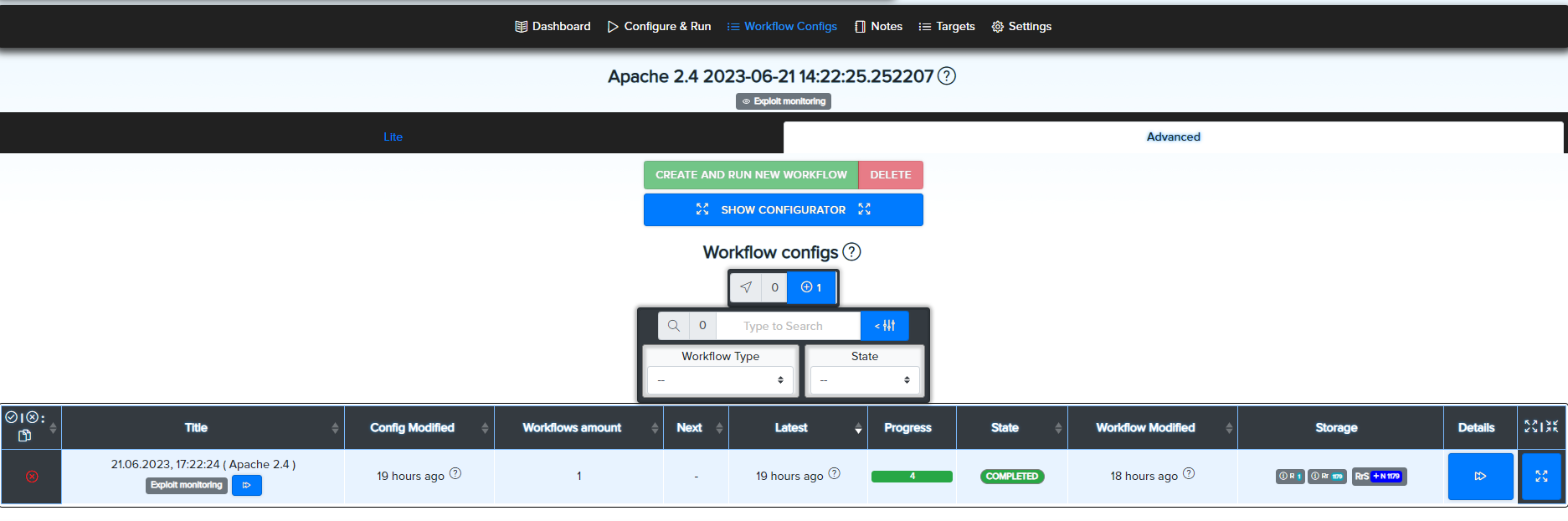
¶ Exploit Monitoring
¶ 🎥 Watch Video — Overview of Exploit Monitor
¶ Description
CQR Exploit Monitoring is an automated system that collects information about technologies and services used on a target website and searches for associated vulnerabilities, exploits, and related news.
While large vulnerability databases exist, they are typically designed for manual analysis. CryEye’s Exploit Monitoring filters, correlates, and analyzes findings automatically — a feature rarely available in existing tools.
¶ How It Works
The process includes 4 automated steps:
- Detect technologies and services used on the target
- Search global databases for exploits and vulnerabilities
- Search relevant news and PoCs
- Analyze, filter, and enrich results using machine learning
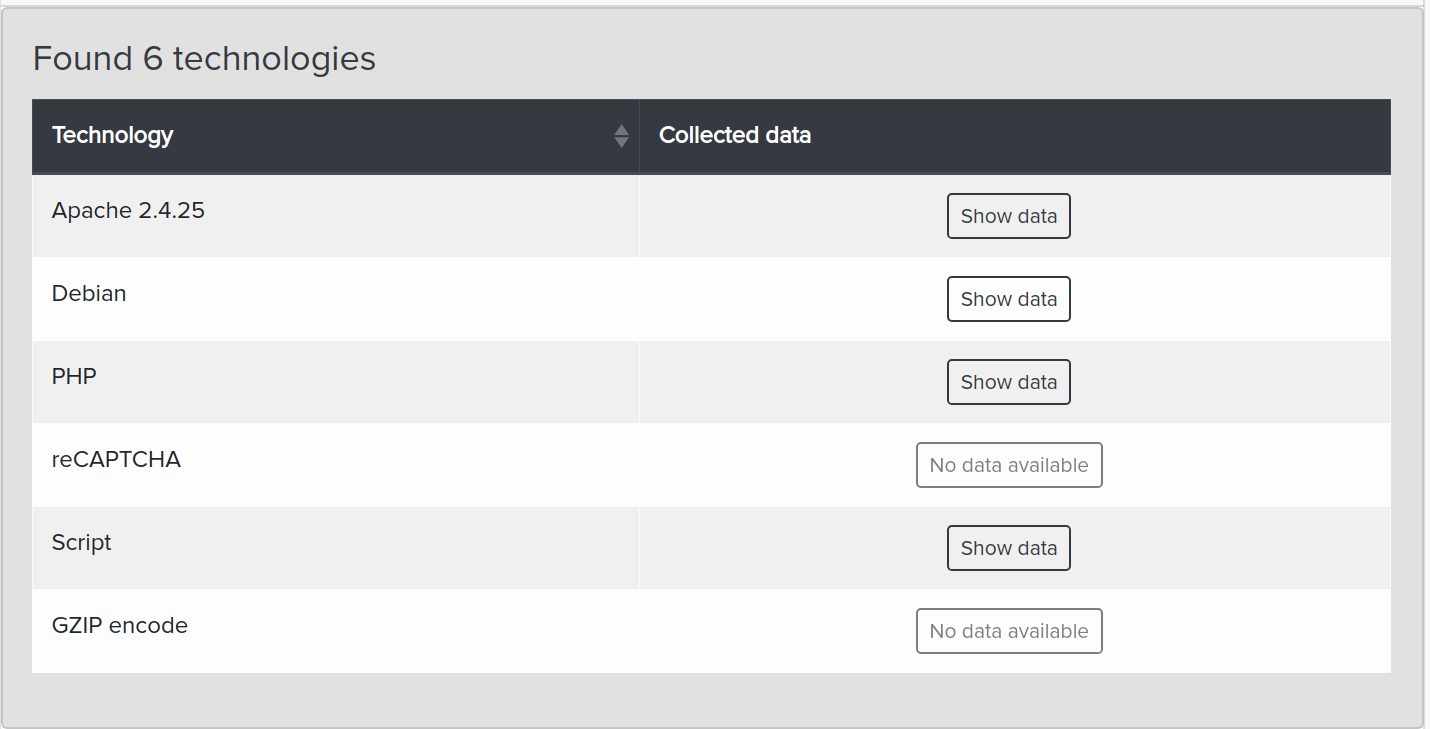
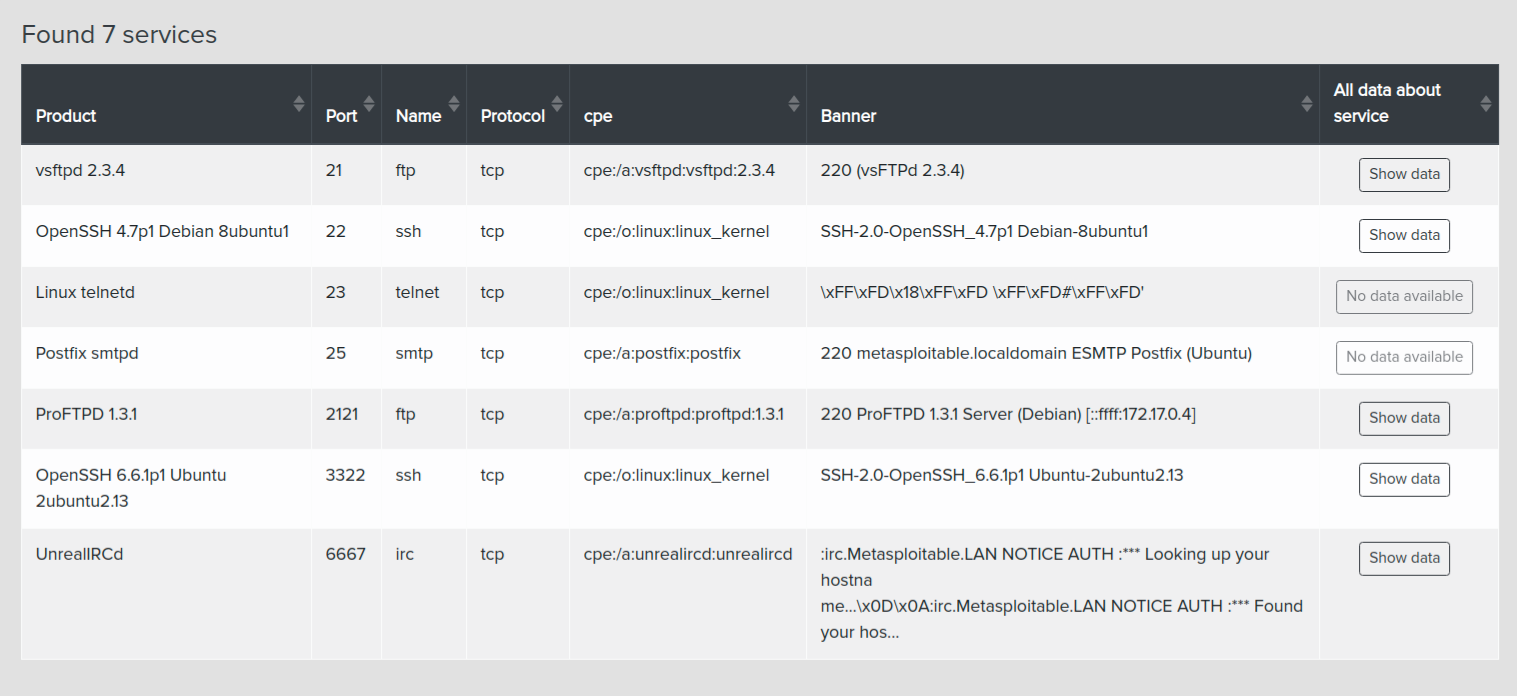
¶ Technologies & Services Gathering
Technologies are identified using WebAnalyzer and Wappalyzer.
Services are detected via CLI tools like nmap, netcat, and curl.
- Technologies: name + version
- Services: product, port, protocol, CPE, and banner
Example:
¶ Exploit Search
Vulnerabilities and exploits are retrieved from:
The system determines relevance by matching version ranges and analyzing exploit headers using custom algorithms.
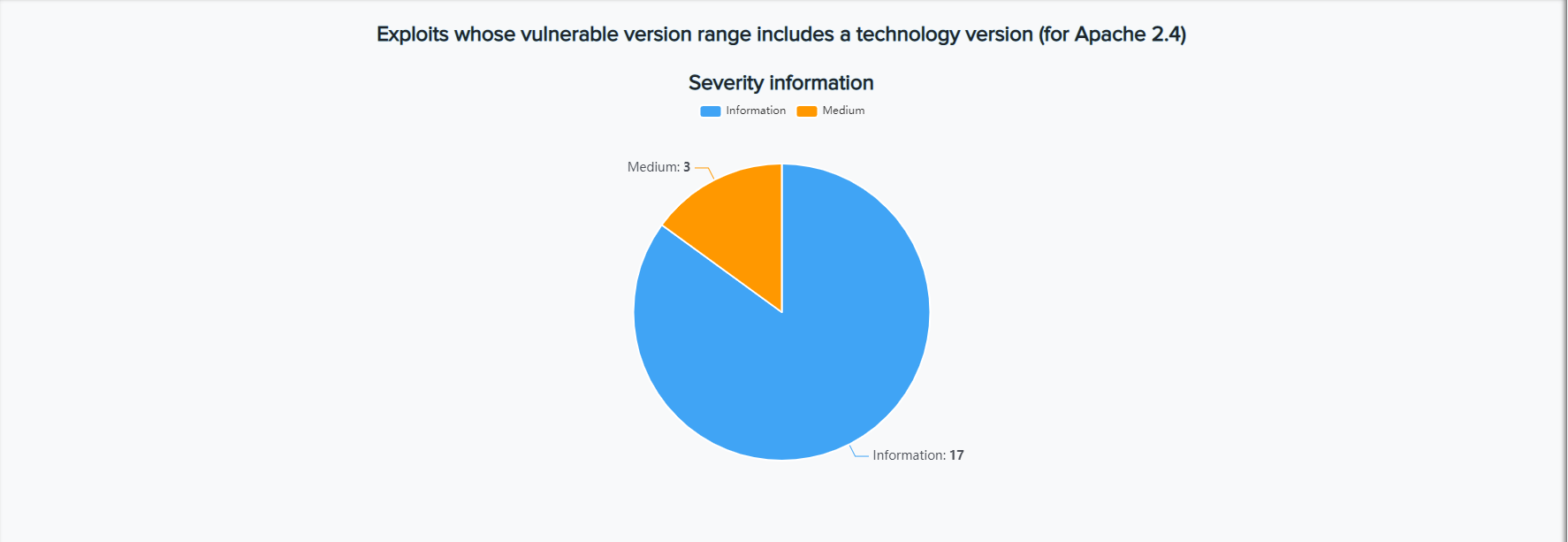
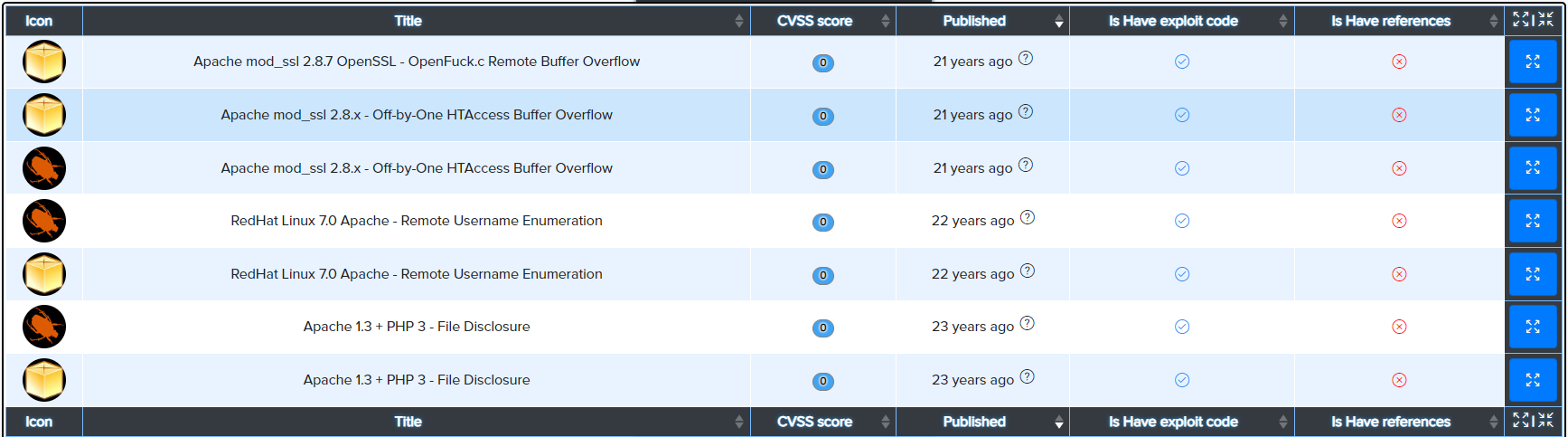
¶ Example: Exact Version Matches
For Apache 2.4:
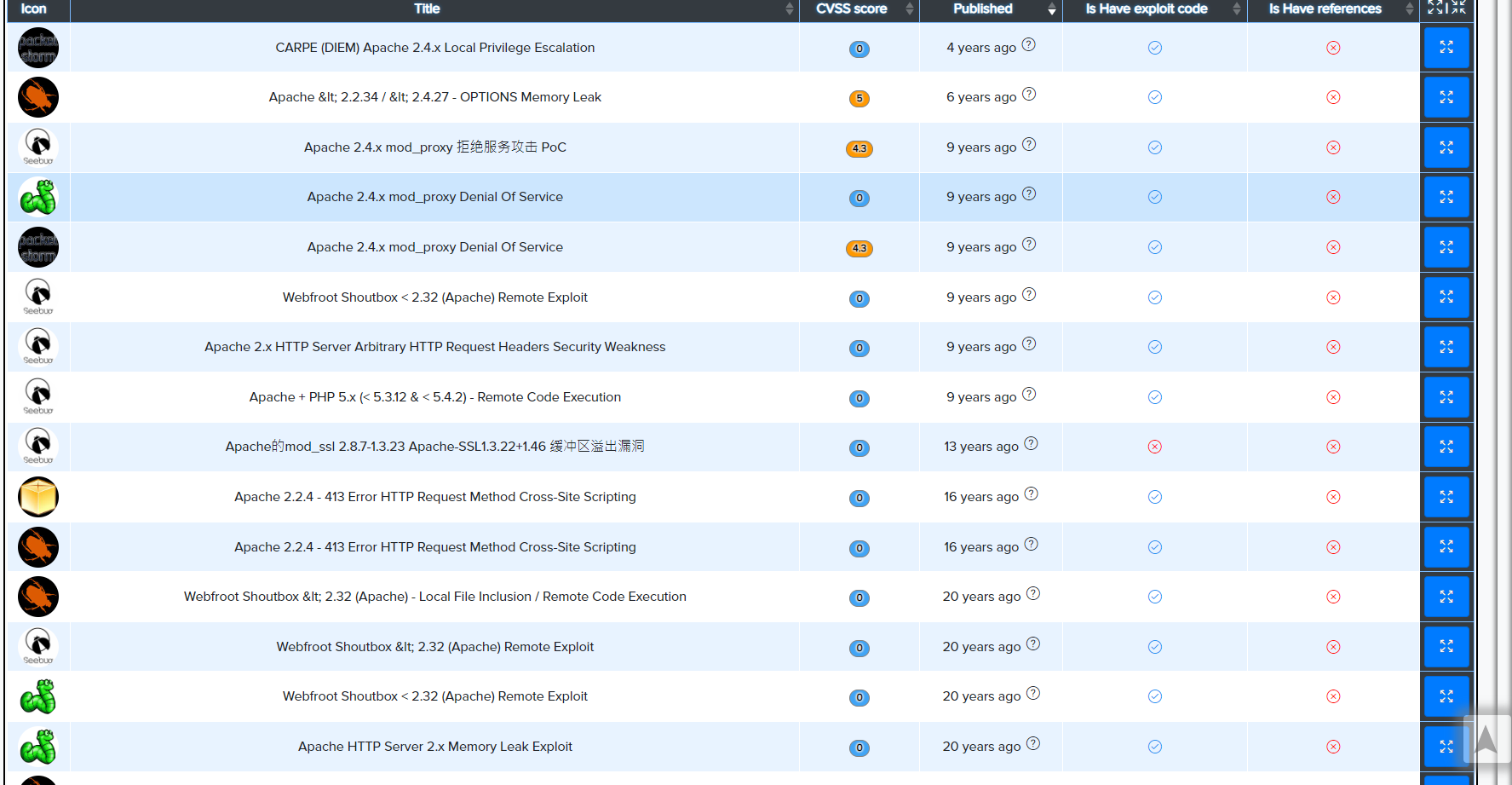
¶ Example: Version Range Matching
-
No version range:
-
Higher than target version:
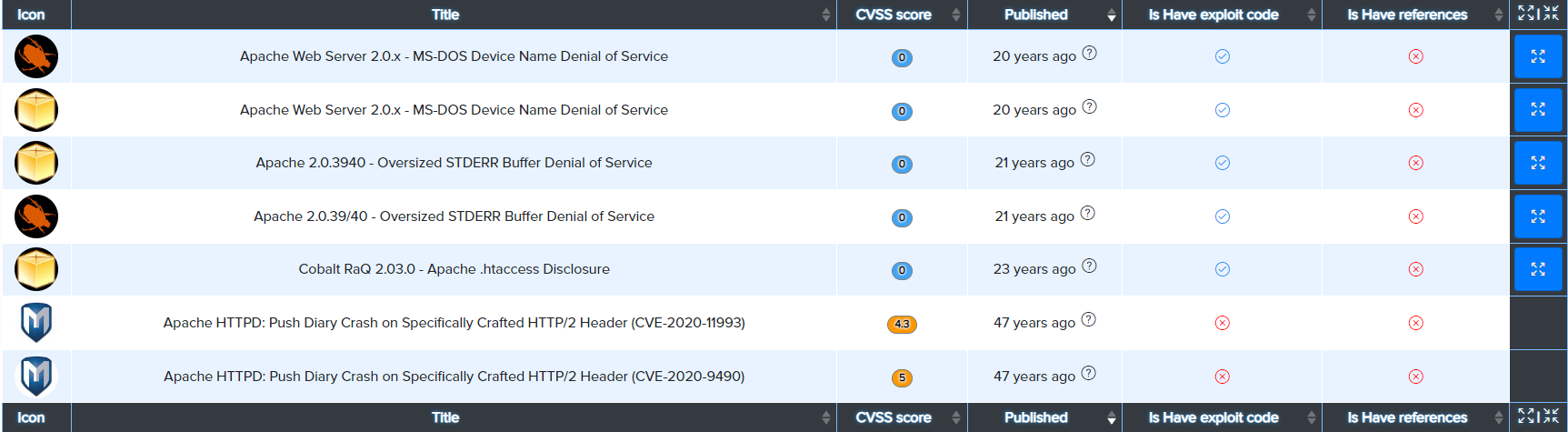
-
Lower than target version:
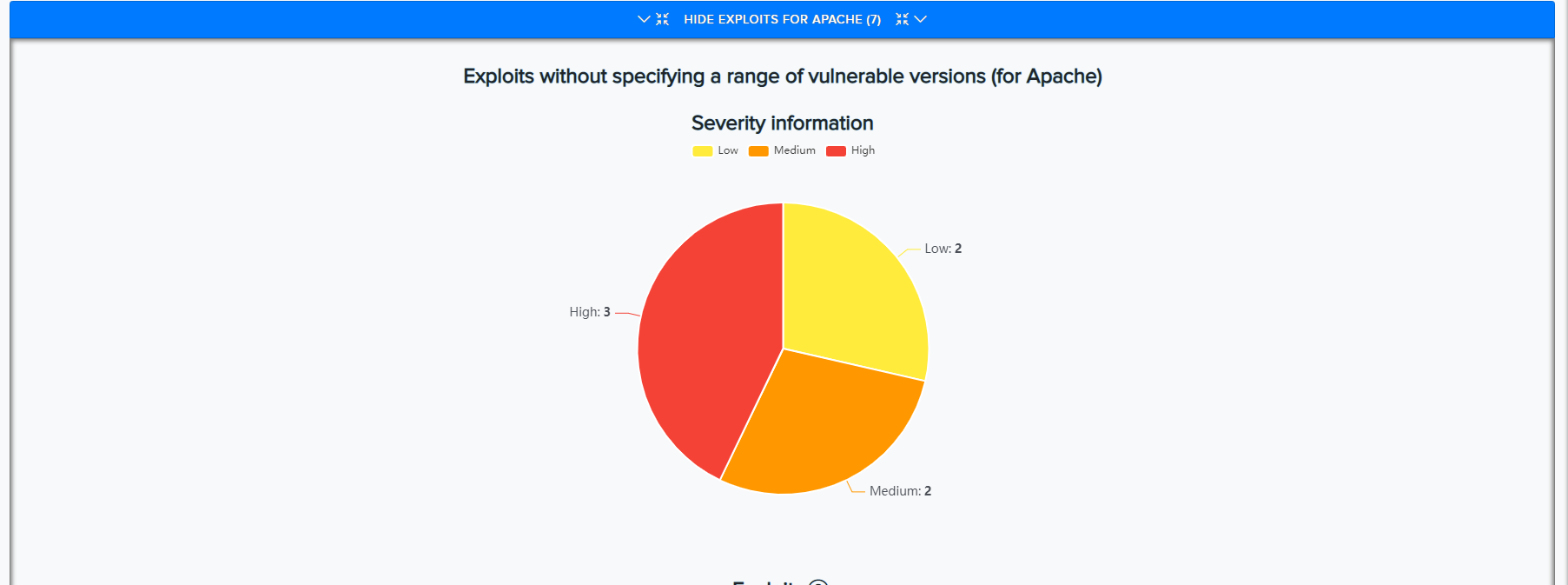
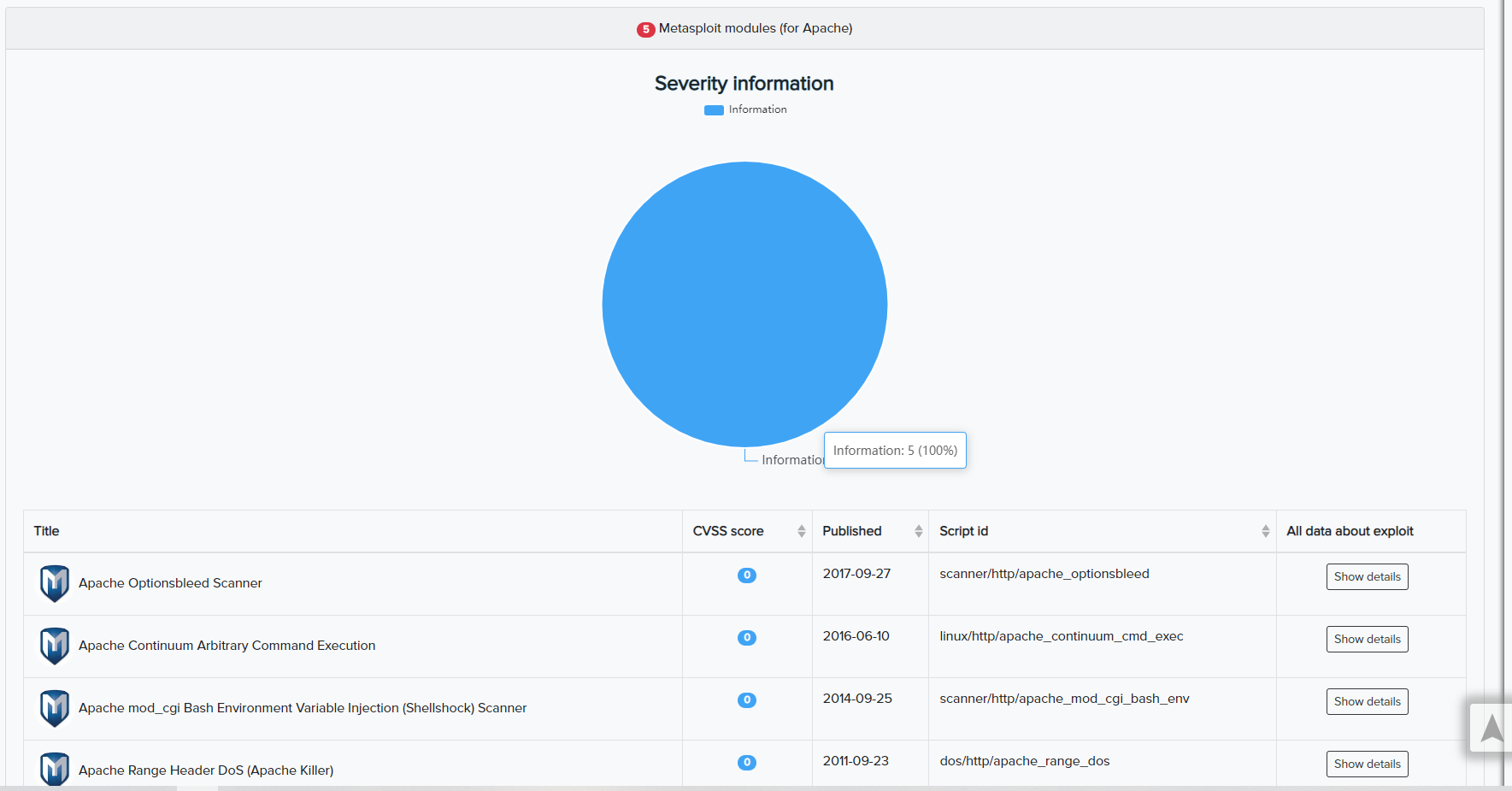
¶ Additional Data & Visualization
-
Metasploit Modules:
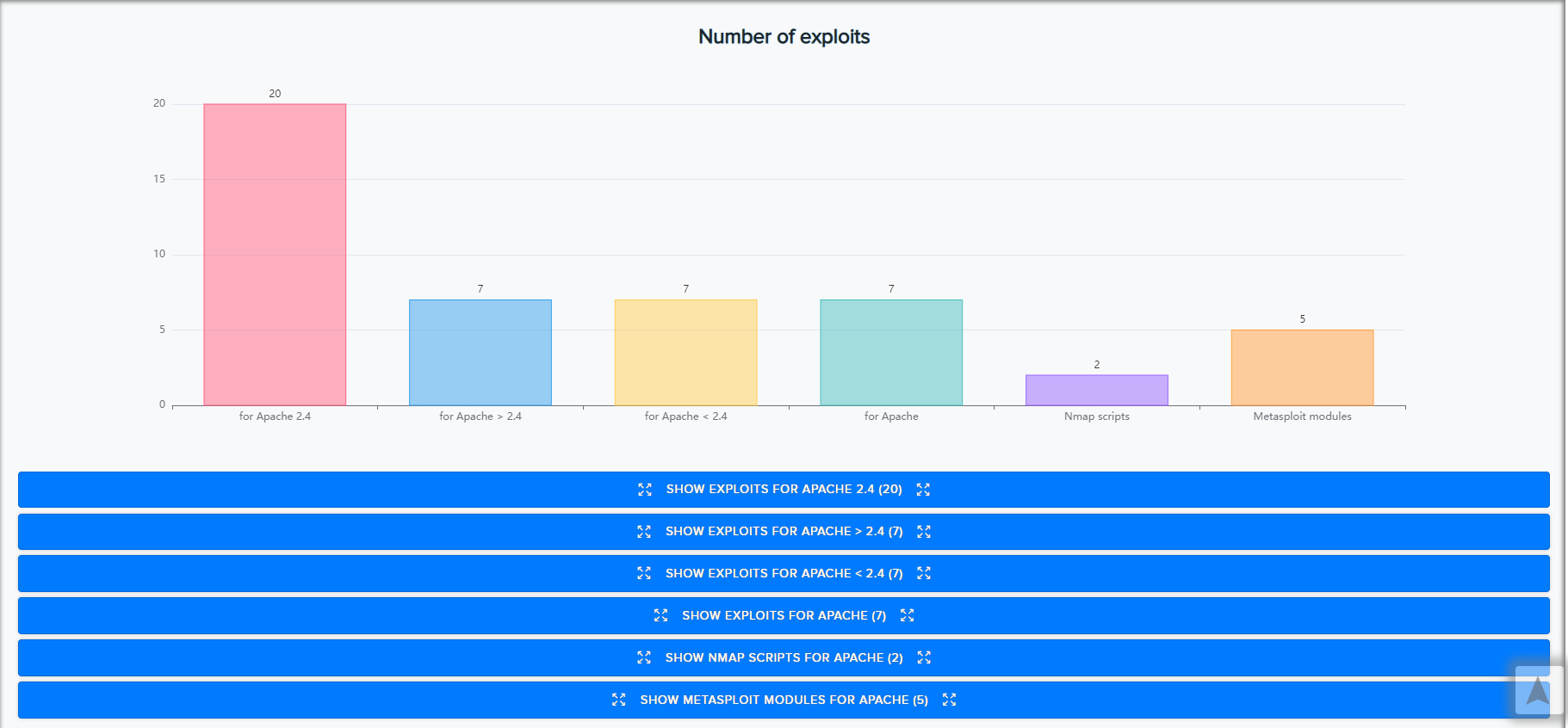
-
Exploit Histogram:
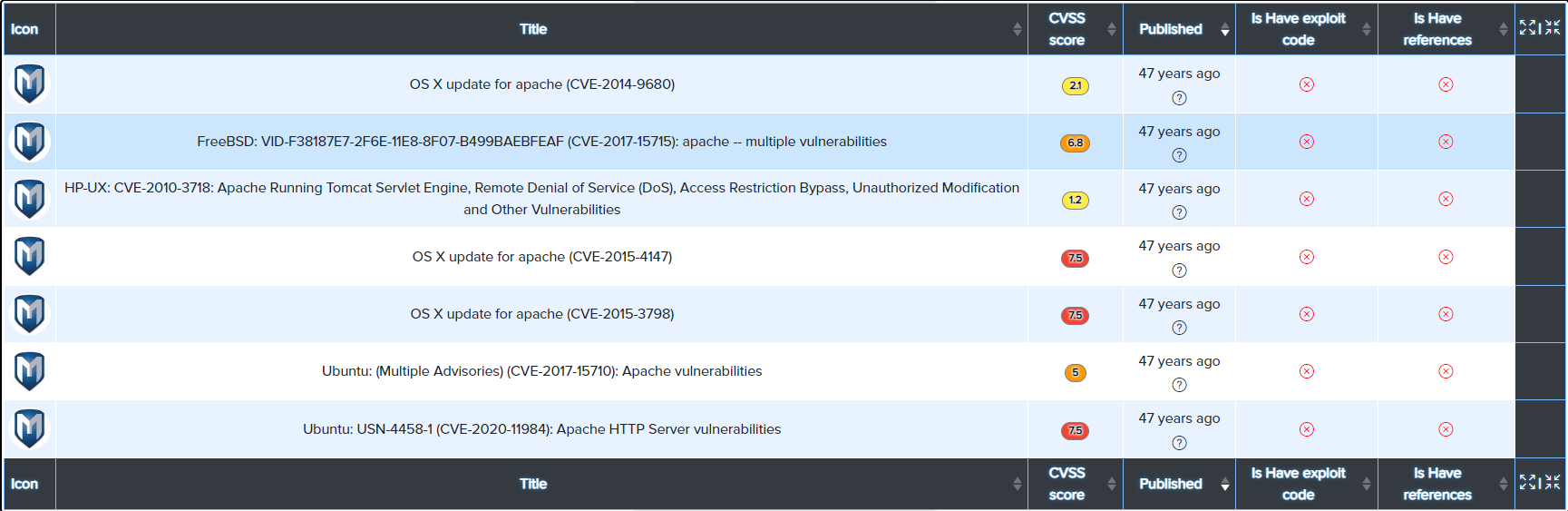
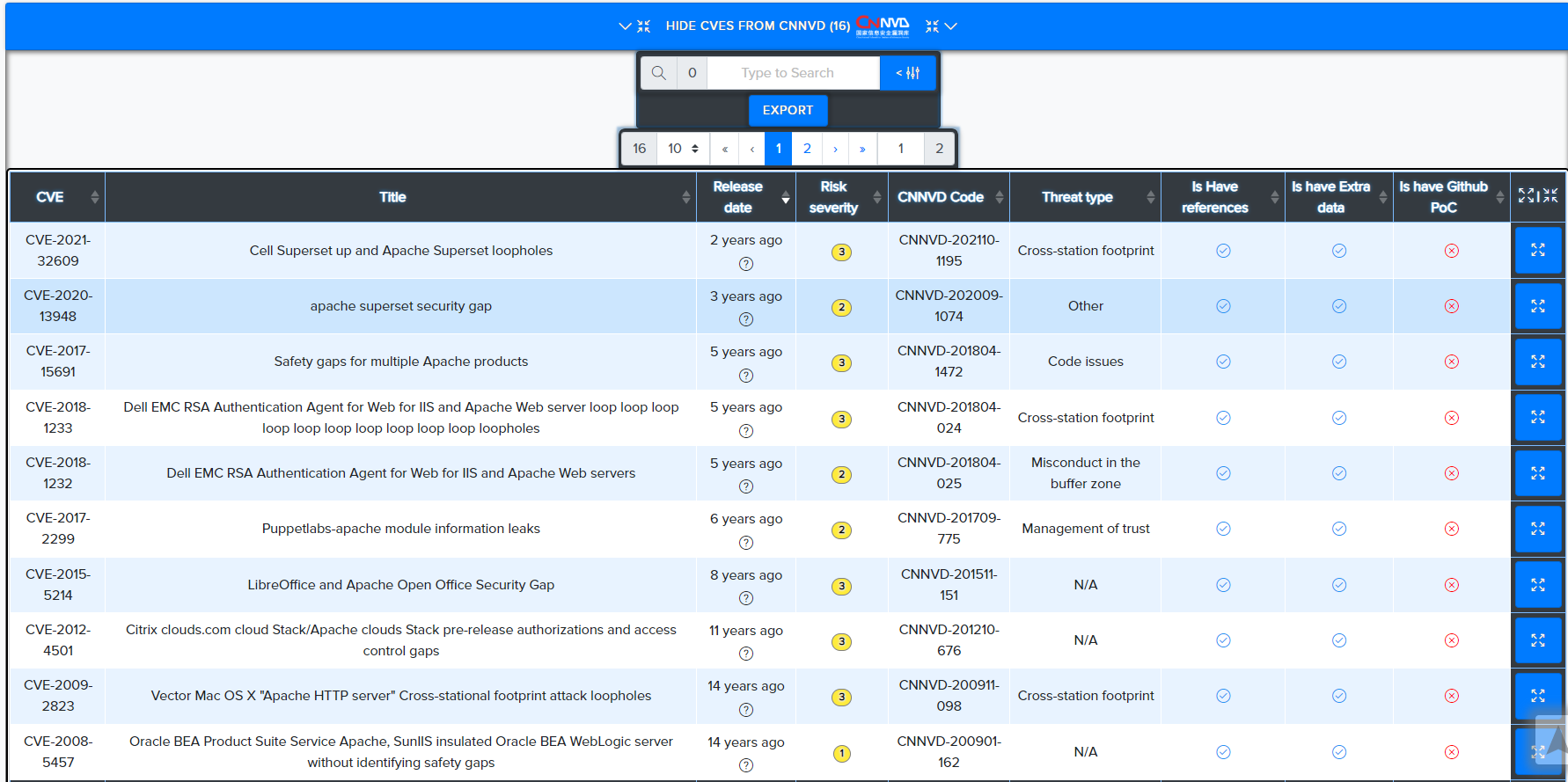
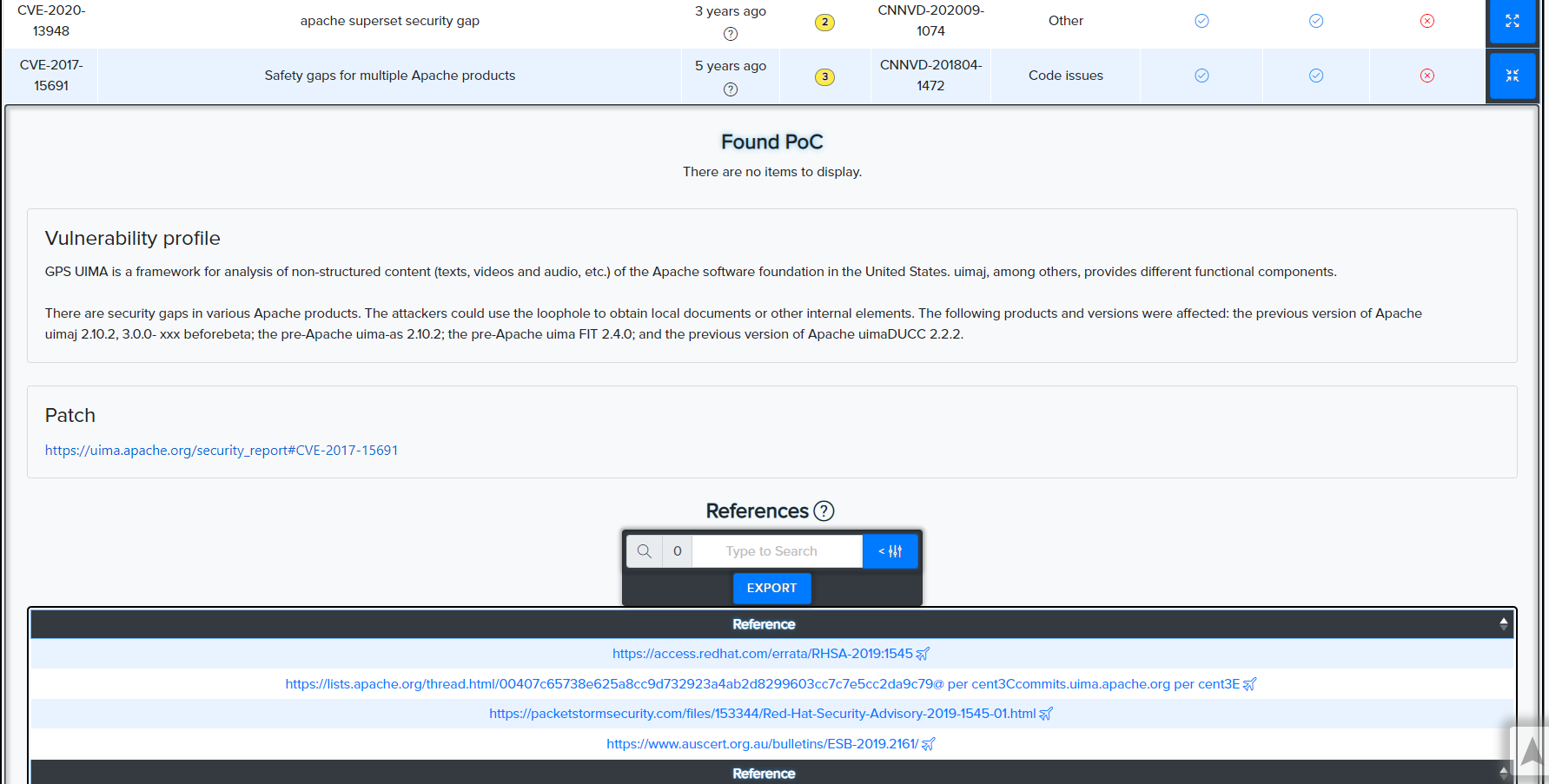
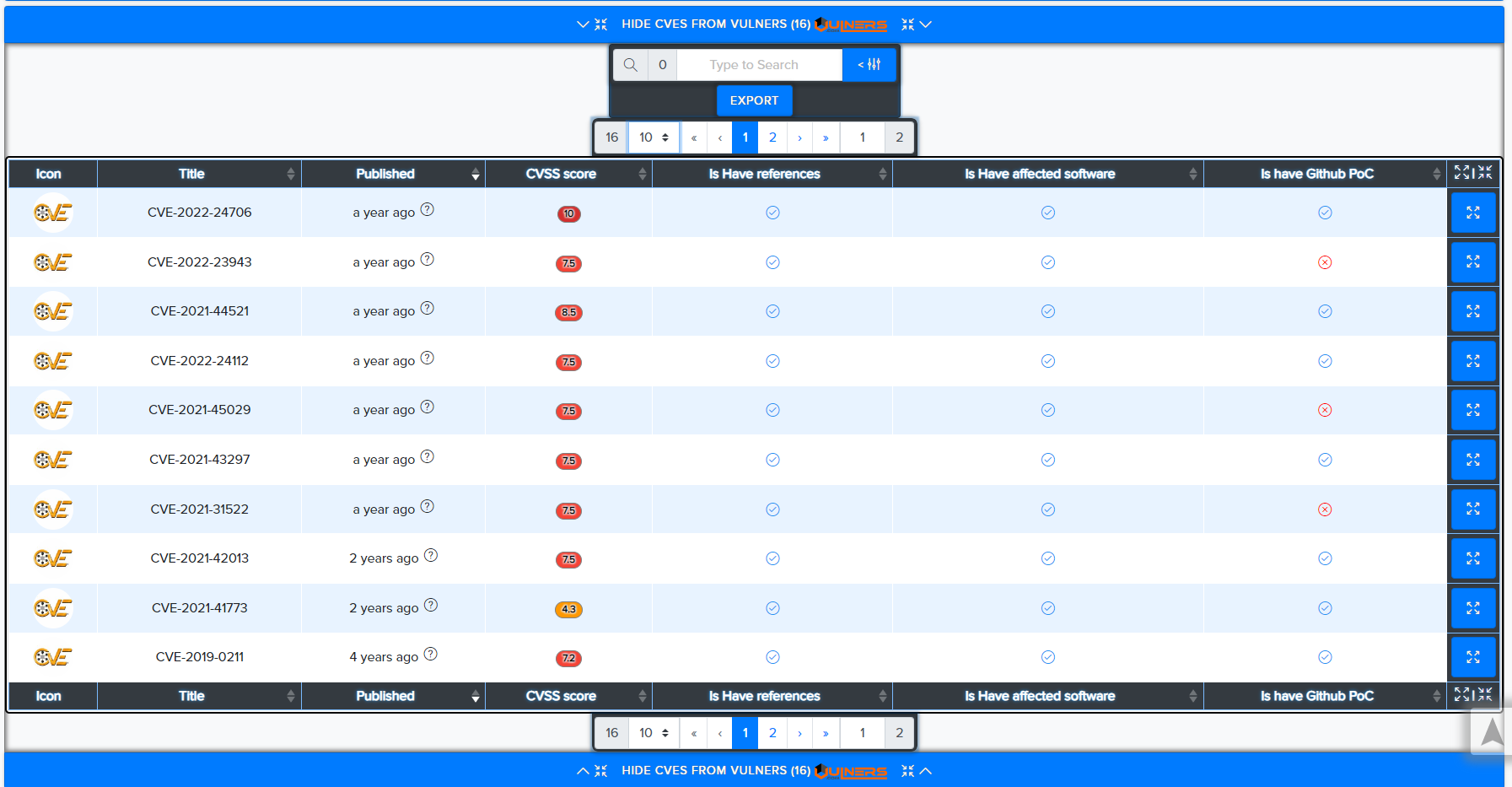
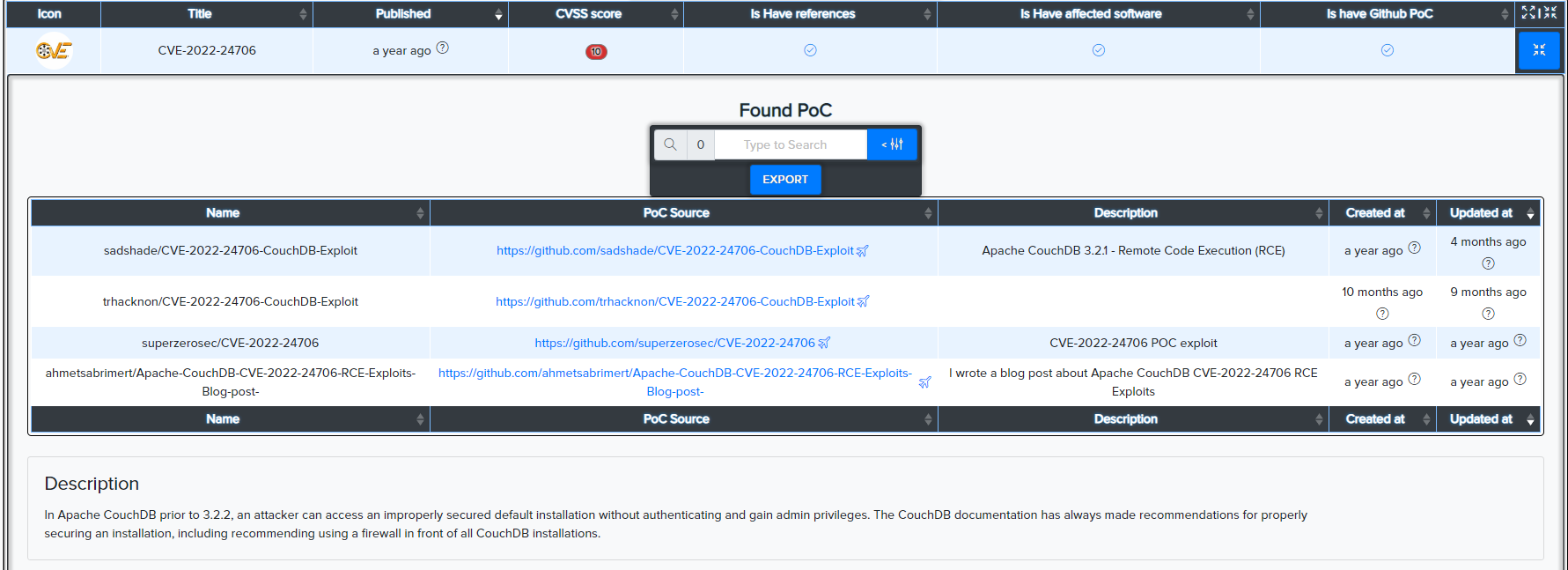
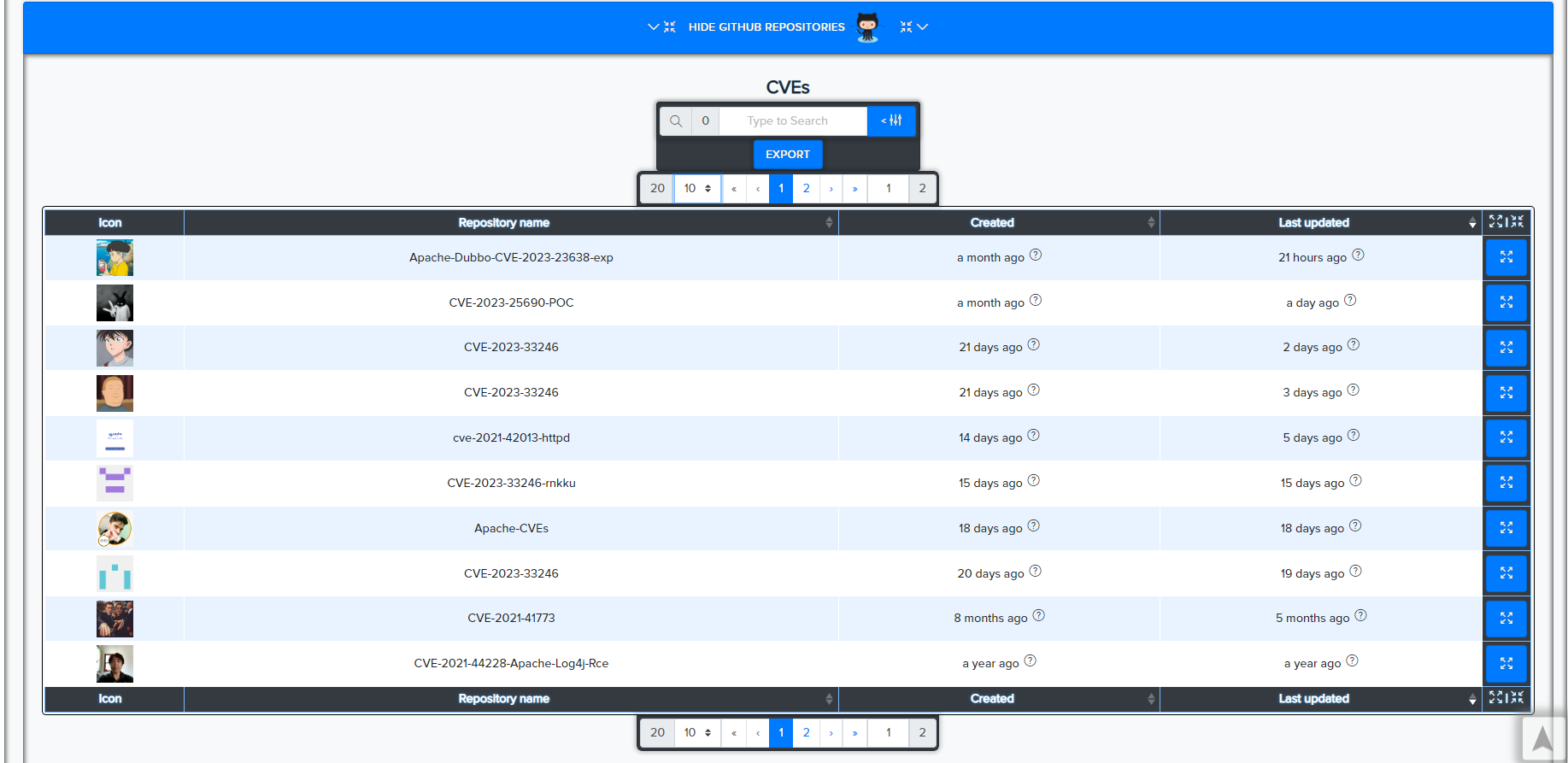
¶ CVE Search
CVE data is sourced from:
CVEs are matched against technologies and services using version-aware logic.
Visualizations:
-
CVE Histogram:
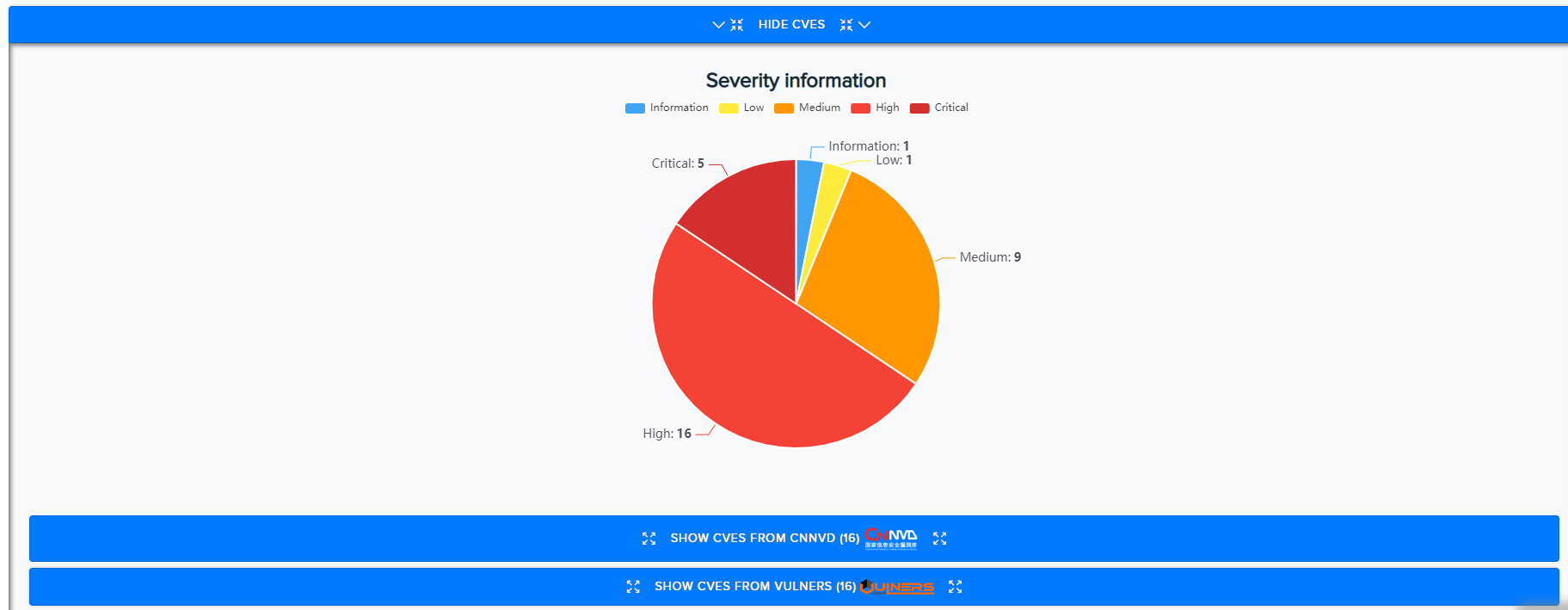
-
CNNVD CVEs:
-
Vulners CVEs:
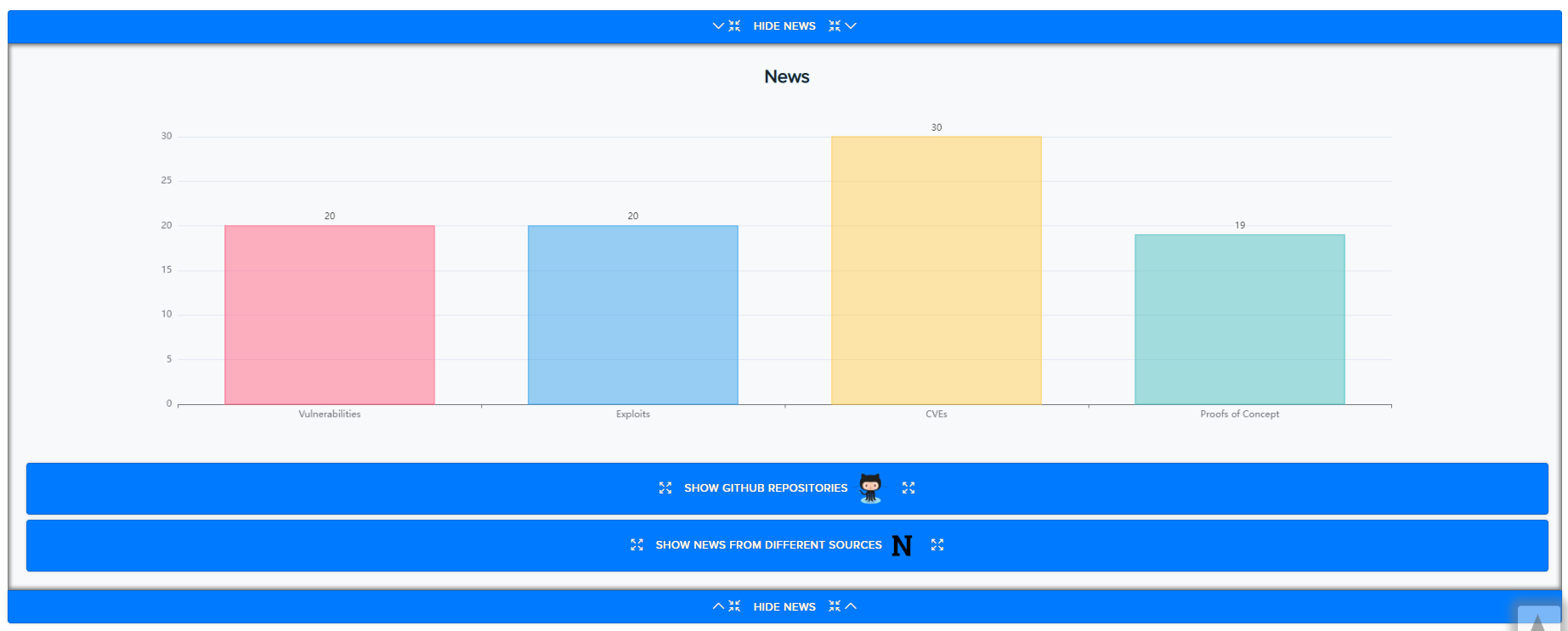
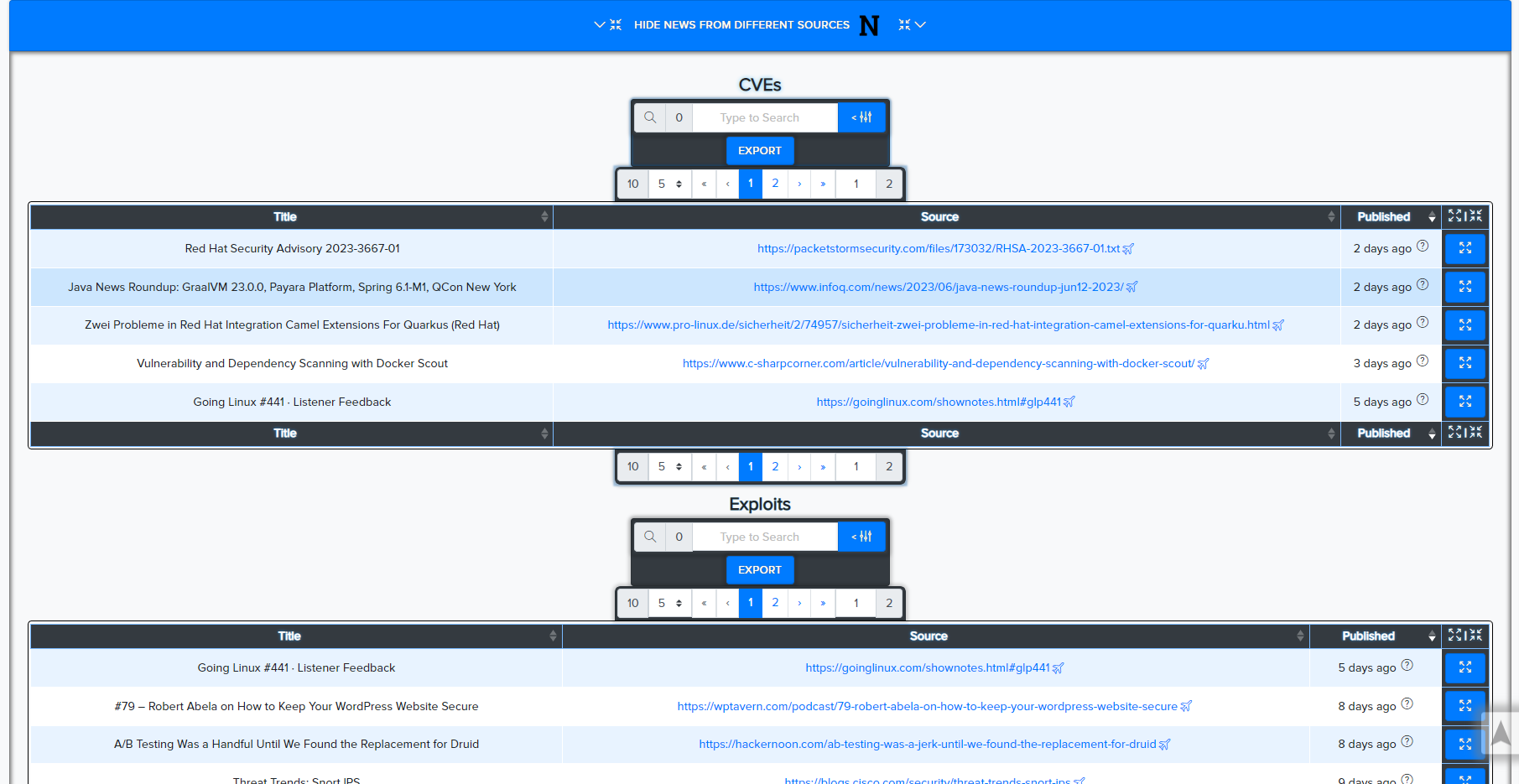
¶ News Monitoring
CryEye also tracks news, GitHub repositories, and PoCs related to technology vulnerabilities, helping users stay ahead of active exploitation.
- News API + GitHub keyword matching
- Finds CVEs, PoCs, zero-days before public exploit release
Examples:
-
News feed:
-
GitHub repos:
-
News from multiple sources:
¶ How to Start Exploit Monitoring
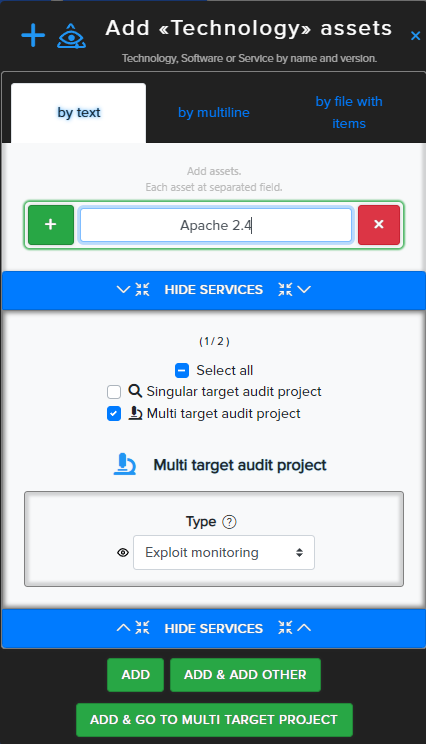
-
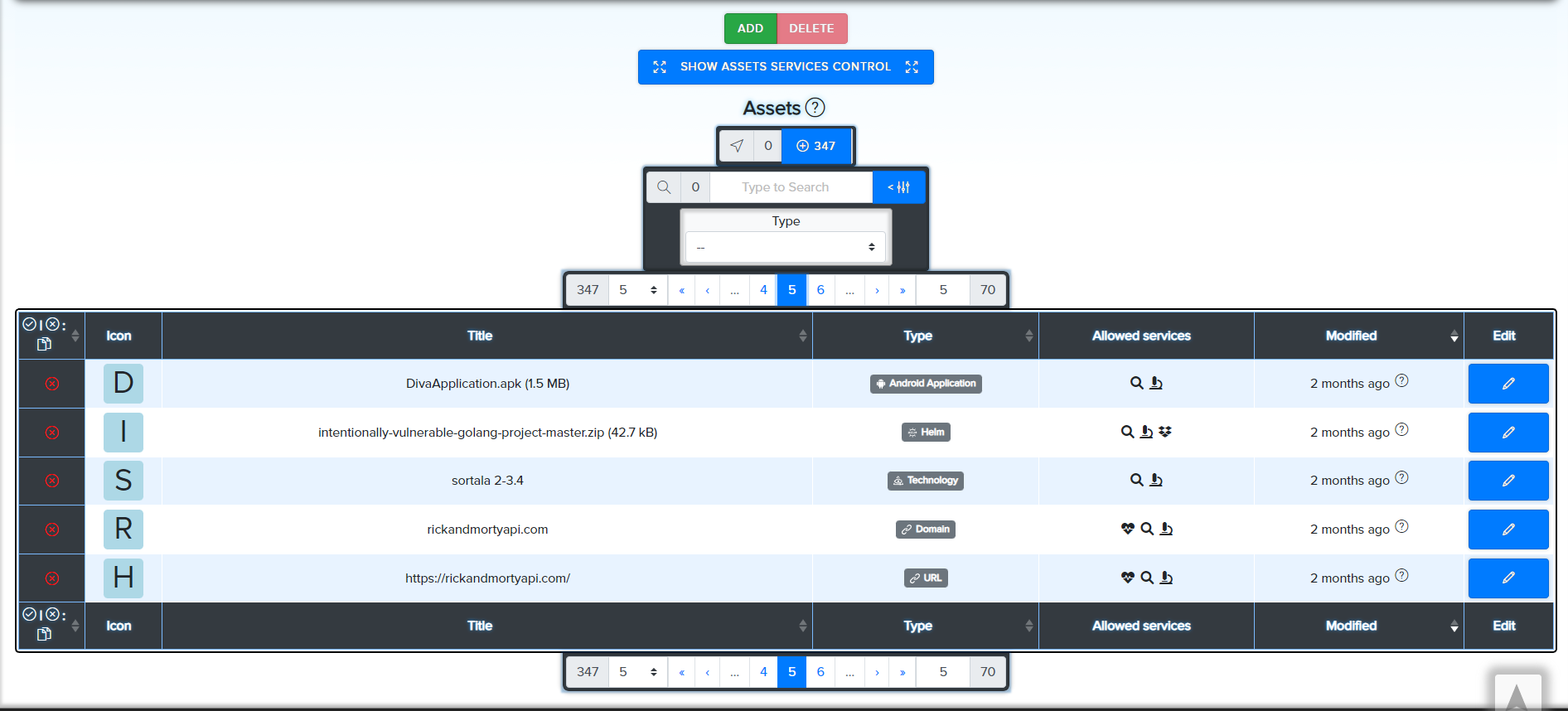
Add an Asset of type Technology
→ Go to Assets
-
Create a Simple Audit Project of type Exploit Monitoring
→ Projects Dashboard
-
Open the project/workflow, create and run the scan
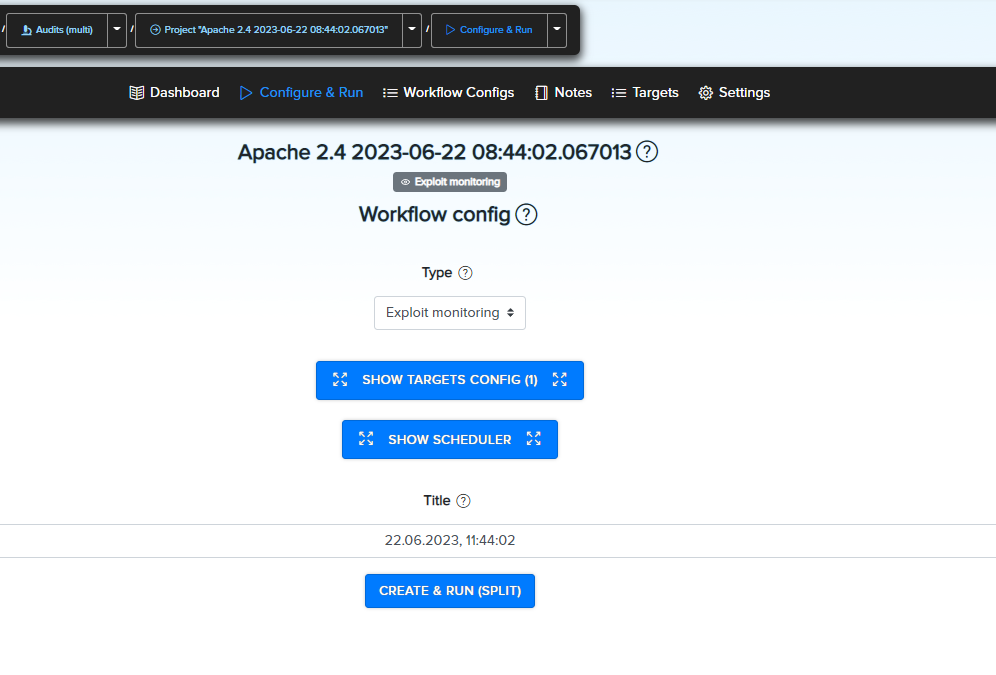
-
View results inside workflow