¶ Assets
¶ Video — Briefly about features, modules, and use cases.
In CryEye, users can add various assets to their workspaces. These assets can be:
Scanned by the audit system to detect vulnerabilities, misconfigurations, and data leaks.
Monitored for Uptime to track availability.
Included in audit projects (single/multi-target or whitebox to analyze source code for development-stage risks.
¶ Assets types
Assets in CryEye are categorized as follows:
-
Web- For scanning web resources to detect vulnerabilities or data leaks. -
Infrastructure- For analyzing infrastructure files for vulnerabilities and misconfigurations. -
Mobile- For inspecting mobile app files to uncover security flaws, misconfigurations, or incorrect permissions. -
Source Code Analysis- For scanning GitHub repositories and source code to detect vulnerabilities, hardcoded secrets, emails, usernames, and passwords. -
Binary Analysis- For analyzing binary code to understand behavior and uncover potential security risks. -
Recon- For scanning personal data (emails, usernames, phone numbers) for exposure or leaks. -
Network Forensics- For analyzing network traffic to investigate incidents, detect intrusions, and collect legal evidence. -
Names, Titles or Identifications- For OSINT and identity-related reconnaissance. -
Other- For assets that do not fit into any specific category.
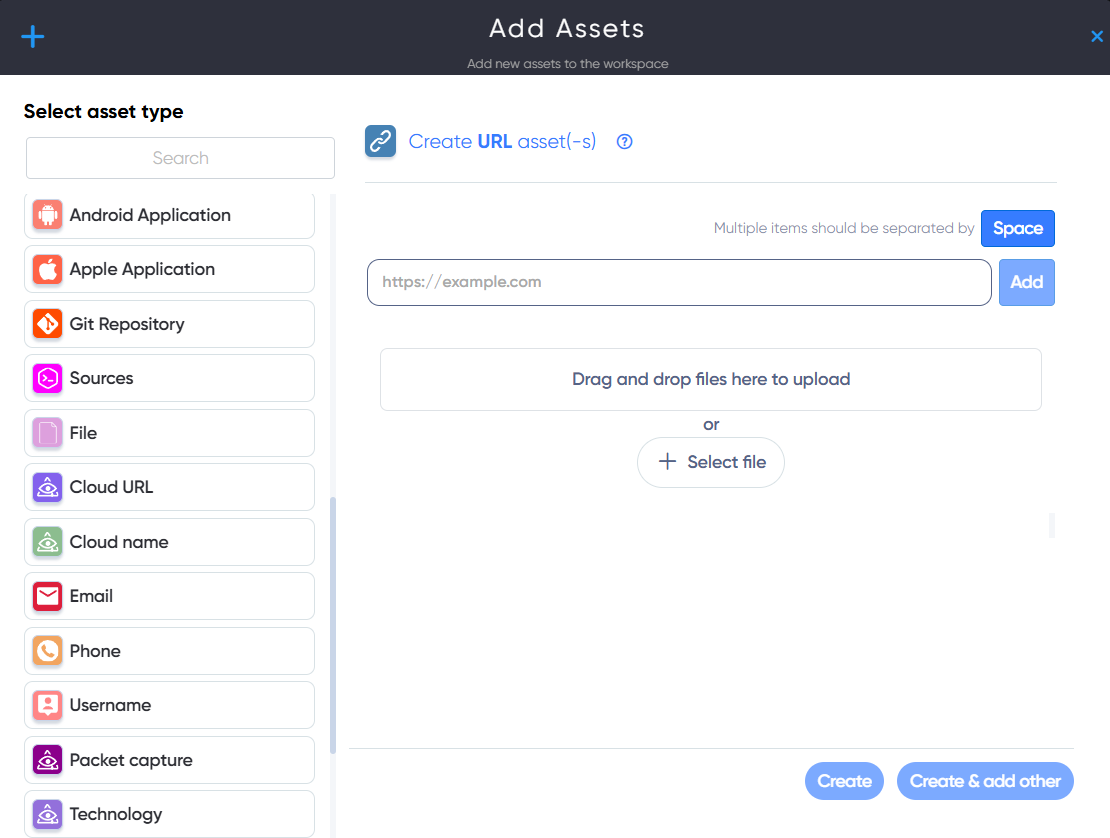
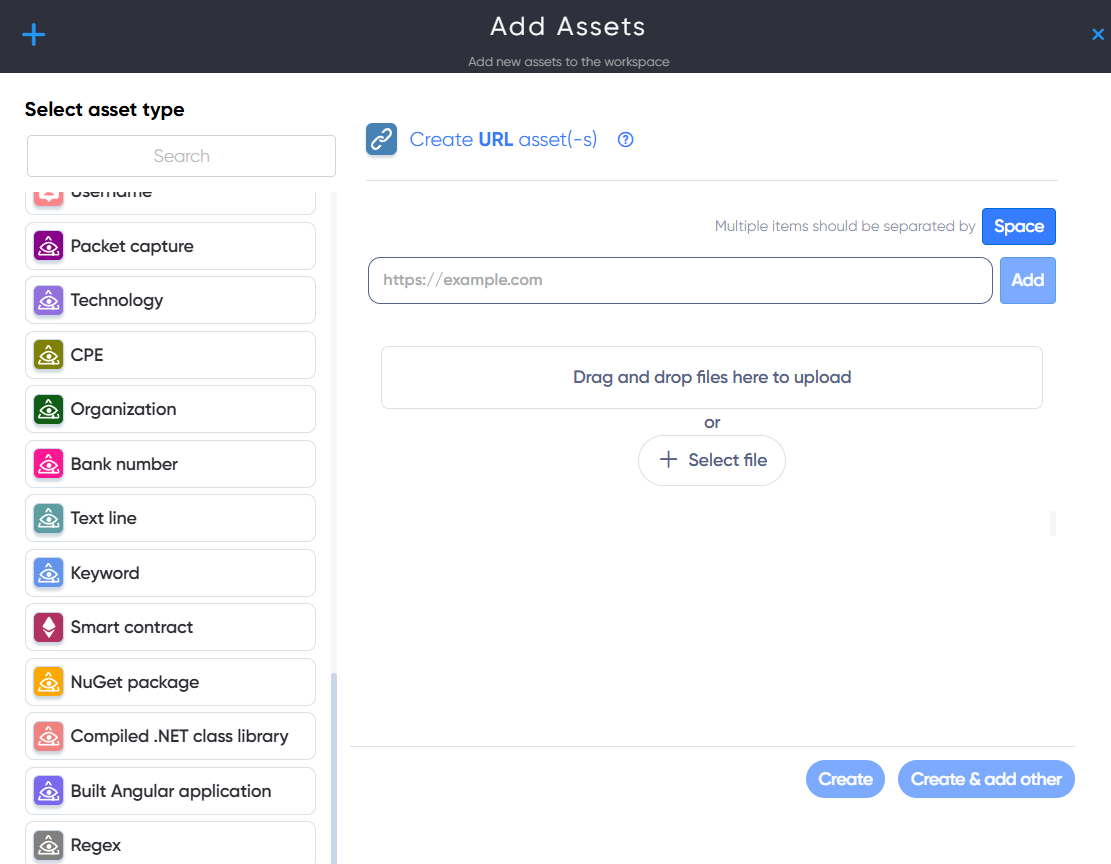

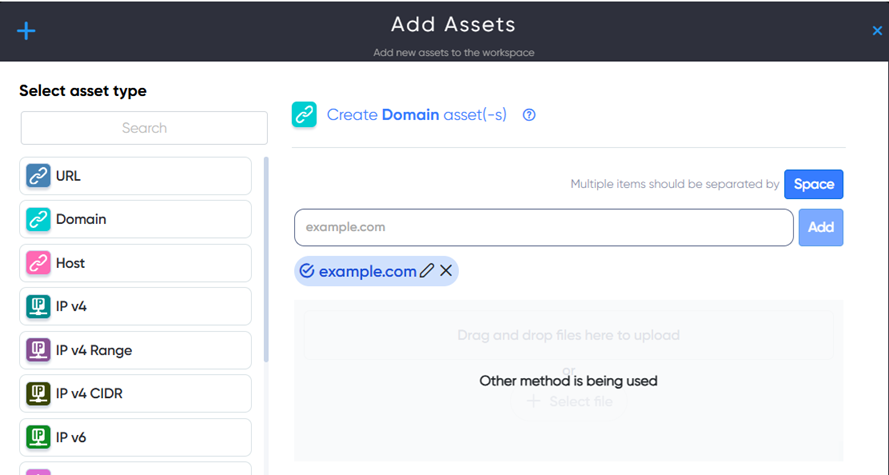
¶ How to add asset
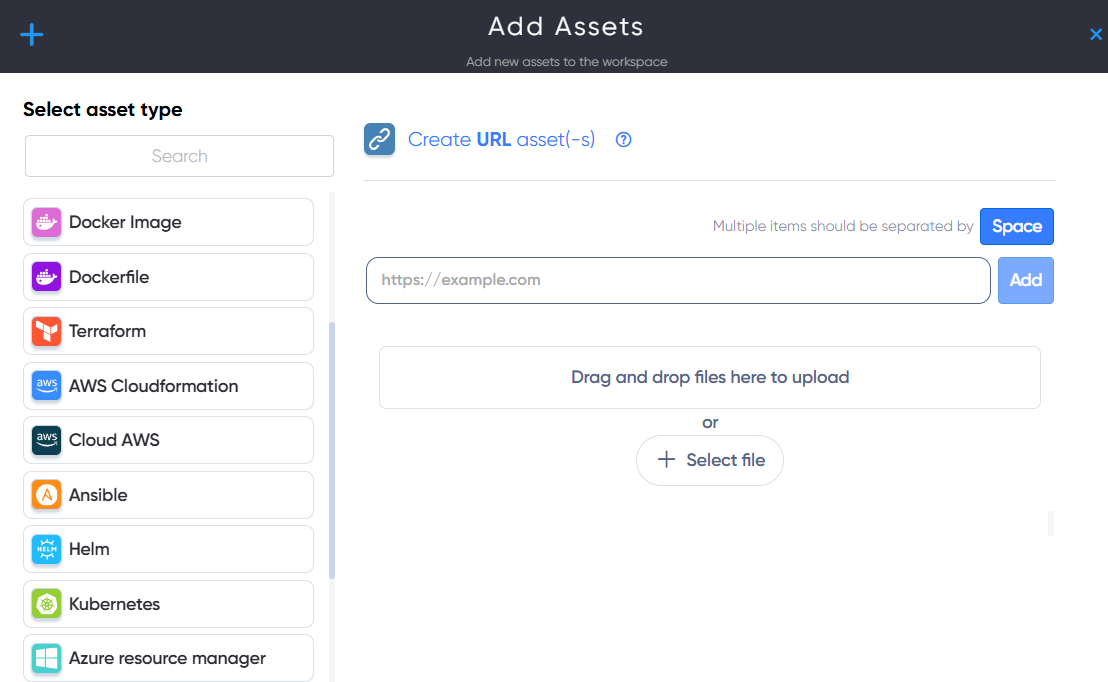
In the Asset Dashboard, click the Add Assets button. Then select the icon for the asset type you want to add and fill in the required details.
You can:
- Enter a single target
- Add multiple targets
- Or upload a file with a list of targets
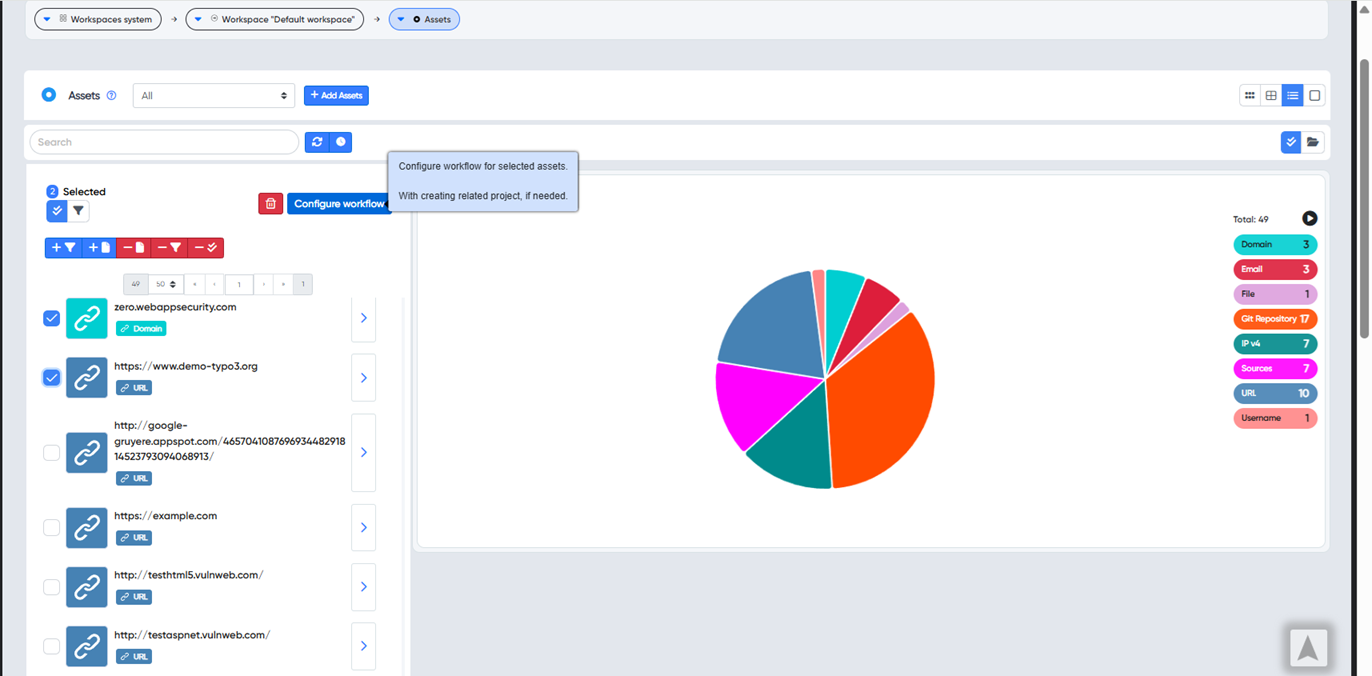
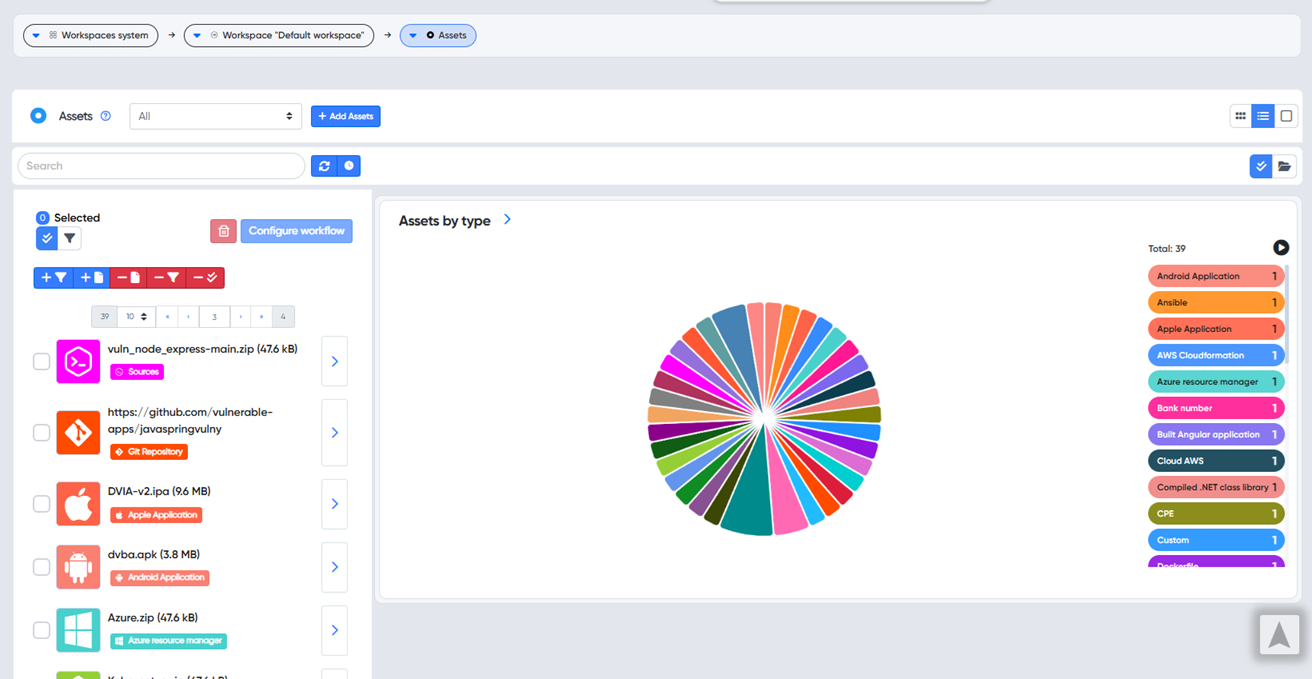
¶ Assets dashboard
Alternatively, users can create different projects later from the Asset Dashboard using the Configure workflow.
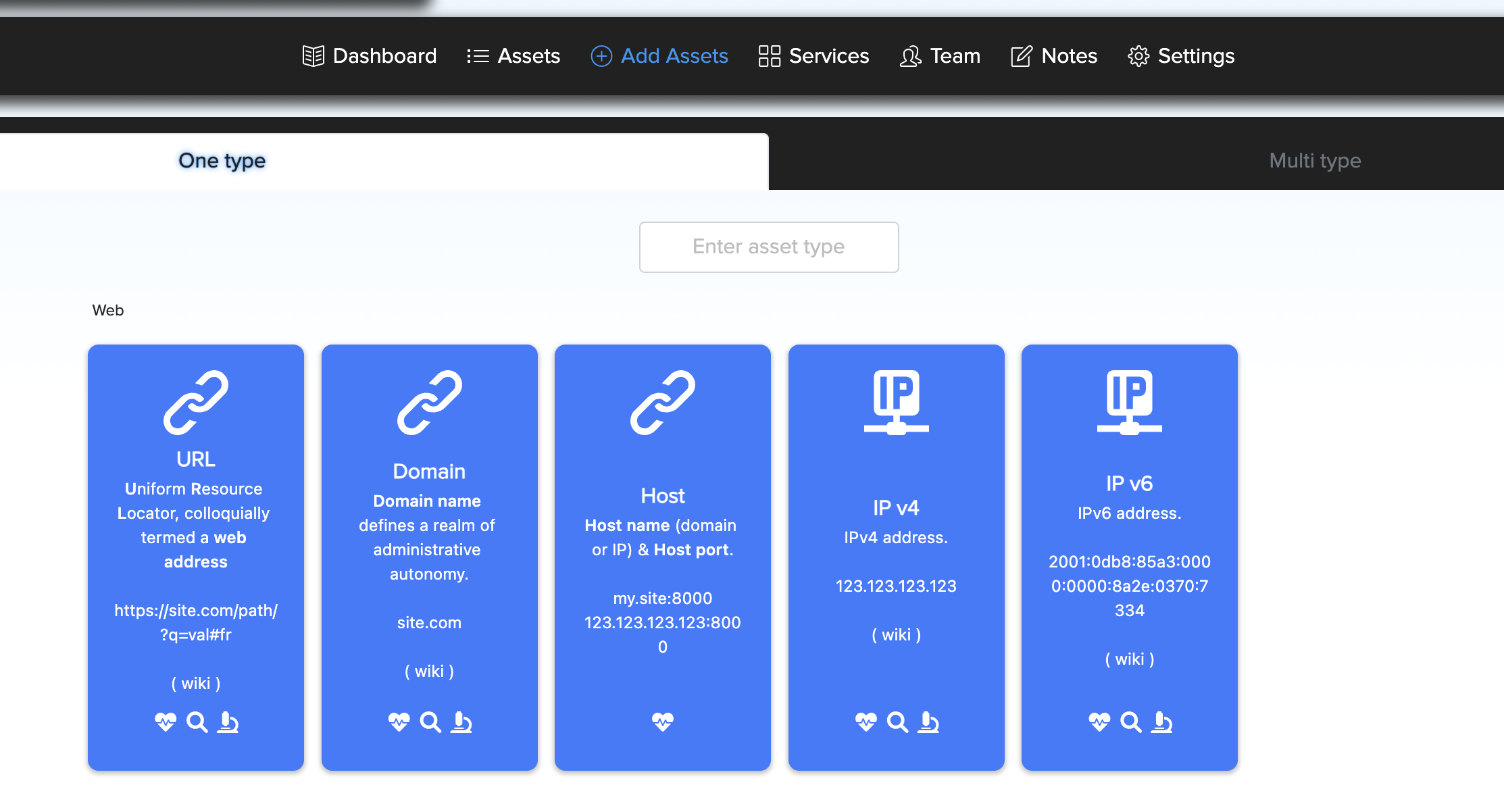
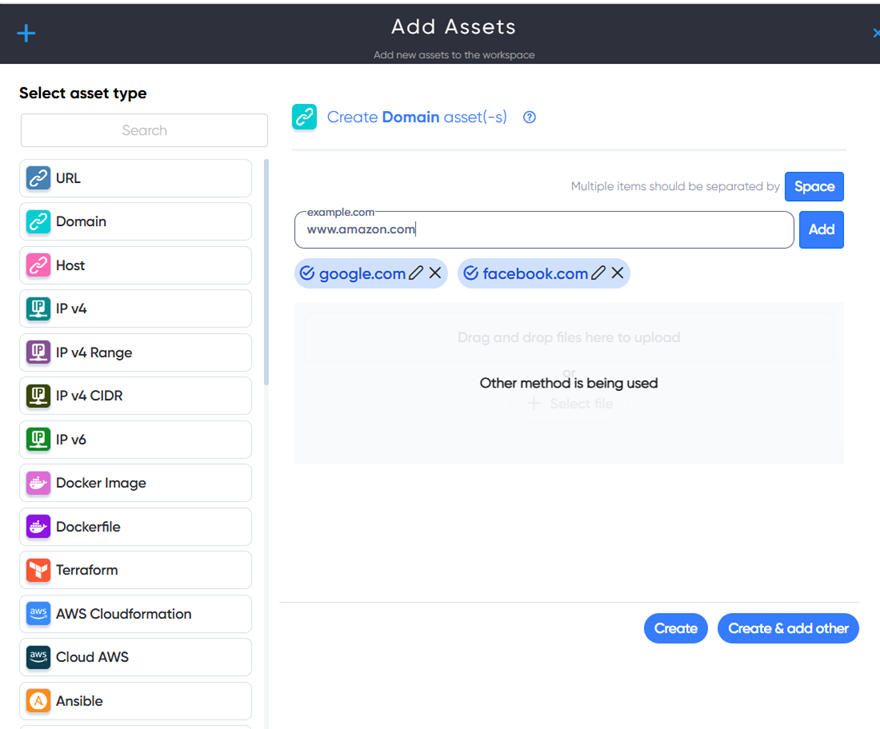
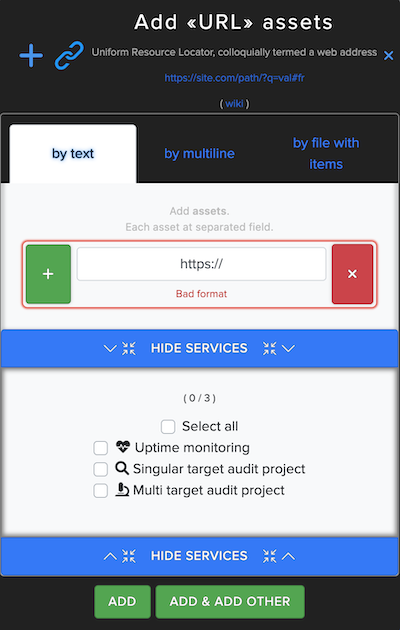
¶ URL Asset
In URL Asset users can enter and scan website URL. For example: https://example.com
¶ Domain Asset
In Domain Asset users can enter and scan website Domain name. For example: example.com
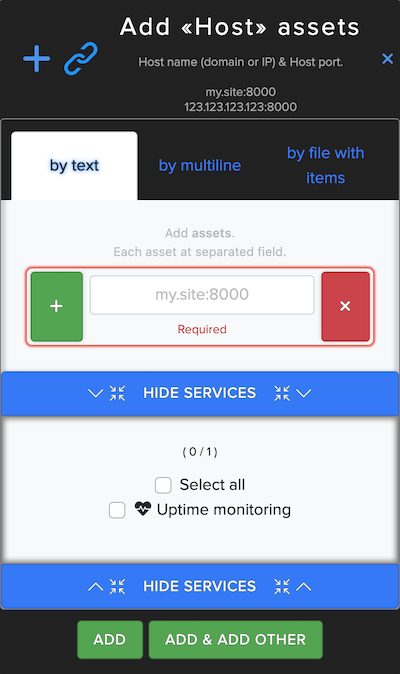
¶ Host Asset
In Host Asset users can enter and scan website Host name (domain or IP) & Host port. For example: example.com:8000 or 192.168.0.1:8000
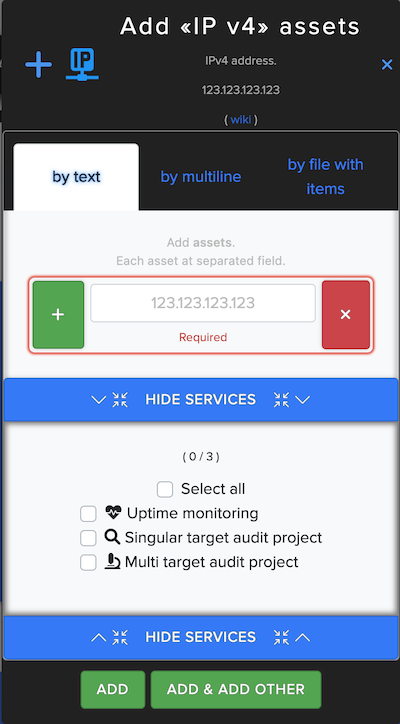
¶ IPv4 Asset
In IPv4 Asset users can enter and scan website IPv4 address. For example: 192.168.0.1
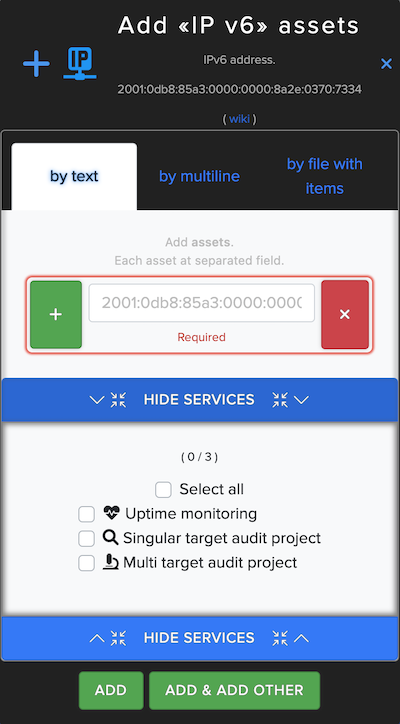
¶ IPv6 Asset
In IPv6 Asset users can enter and scan website IPv6 address. For example: 2001:0db8:85a3:0000:0000:8a2e:0370:7334
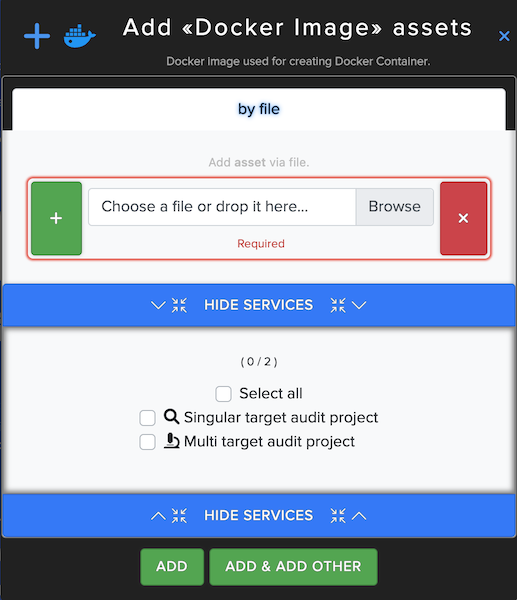
¶ Docker Image Asset
In Docker Image Asset users can upload txt file with Docker image name scan Docker image, used for creating Docker Container. For example: docker-compose.yml
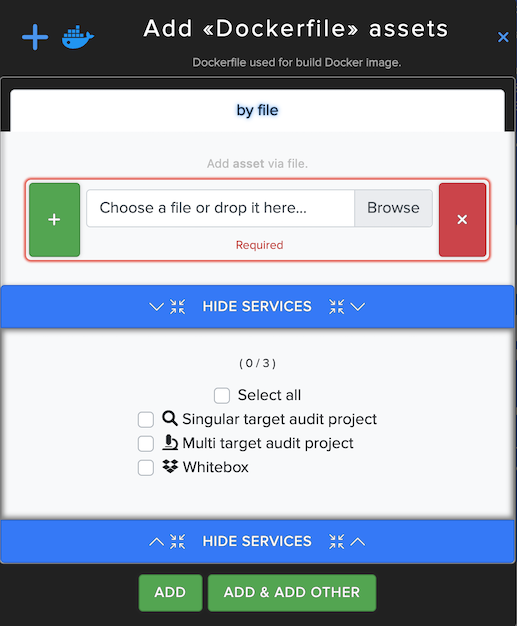
¶ Docker File Asset
In Docker File Asset users can Upload and scan Docker File, Dockerfile used for build Docker image. For example: https://github.com/docker-library/tomcat/blob/9cad4b1a880782d3504d7c8723fccc667965cf29/8.5/jdk8/temurin-focal/Dockerfile
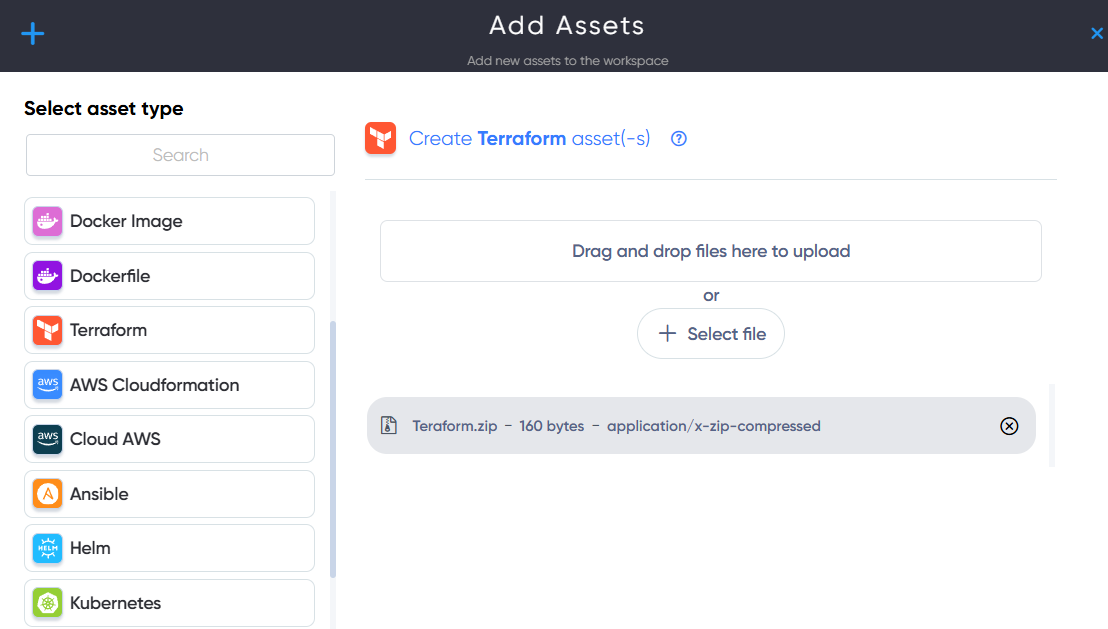
¶ Teraform Asset
In Teraform Asset users can upload and scan Infrastructure files for Terraform vulnerabilities and misconfigurations. For example: Teraform.zip
¶ AWS Cloudformation Asset
In AWS Cloudformation Asset users can upload and scan Infrastructure files for AWS Cloudformation vulnerabilities and misconfigurations. For example: AWS.zip
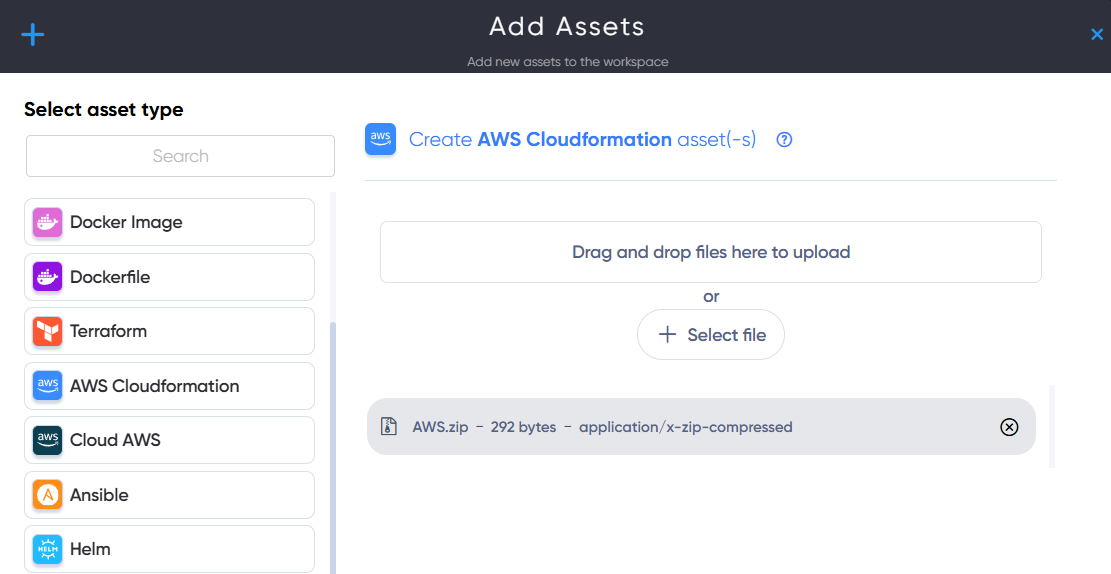
¶ Ansible Asset
In Ansible Asset users can upload and scan Infrastructure files for AWS Cloudformation vulnerabilities and misconfigurations. For example: Ansible.zip
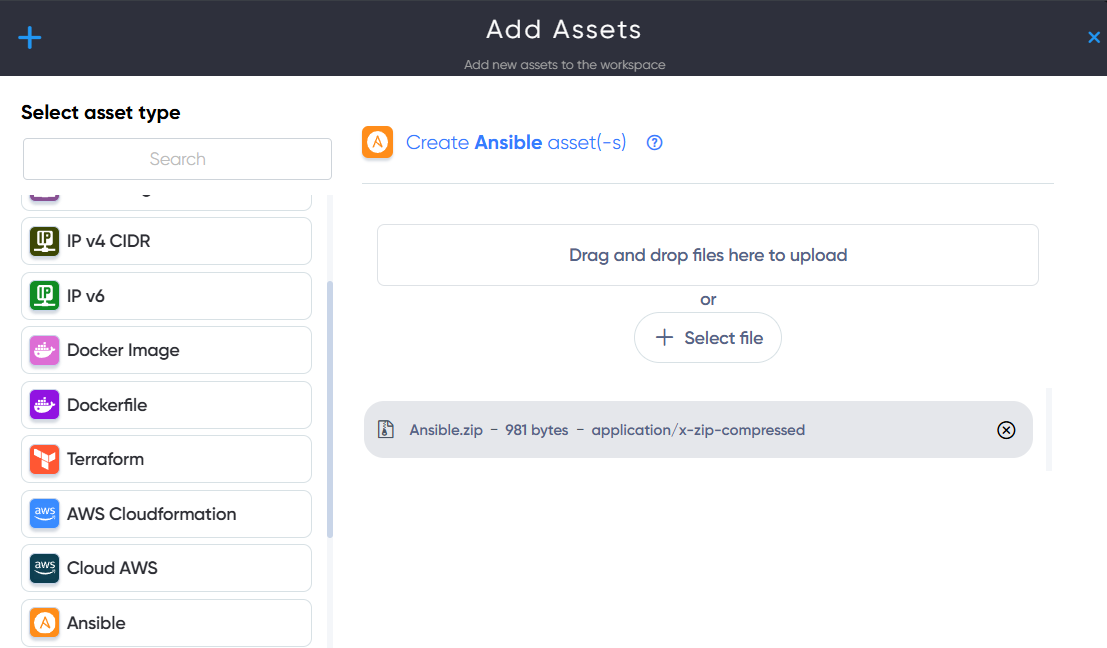
¶ Helm Asset
In Helm Asset users can upload and scan Infrastructure files for Helm vulnerabilities and misconfigurations. For example: Helm.zip
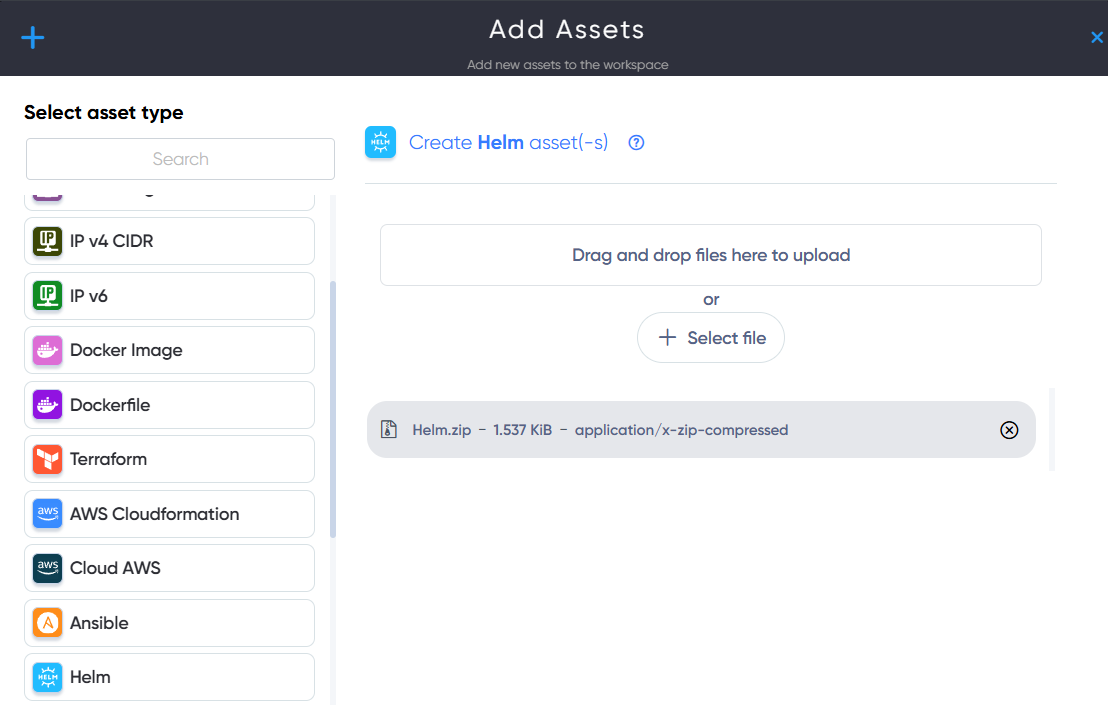
¶ Kubernetes Asset
In Kubernetes Asset users can upload and scan Infrastructure files for Kubernetes vulnerabilities and misconfigurations. For example: Kubernetes.zip
¶ Azure resource manager Asset
In Azure resource manager Asset users can upload and scan Infrastructure files for Azure vulnerabilities and misconfigurations. For example: ARM.zip
¶ Android Application Asset
In Android Application Asset users can upload and scan Android APK files for Mobile vulnerabilities, misconfigurations and wrong permissions. For example: Application.apk
¶ Apple Application Asset
In Apple Application Asset users can upload and scan Apple IPA files for Mobile vulnerabilities, misconfigurations and wrong permissions. For example: Application.ipa
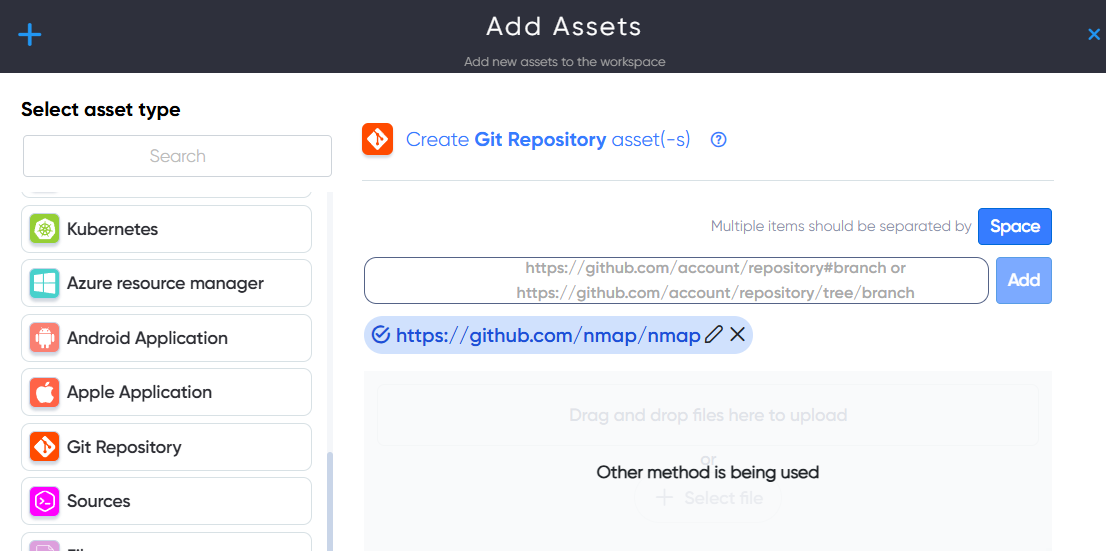
¶ Git Repository Asset
In Git Repository asset users can add GitHub repositories for scan to find vulnerabilities, hardcoded misconfigurations, emails, usernames, passwords. For example: https://github.com/nmap/nmap
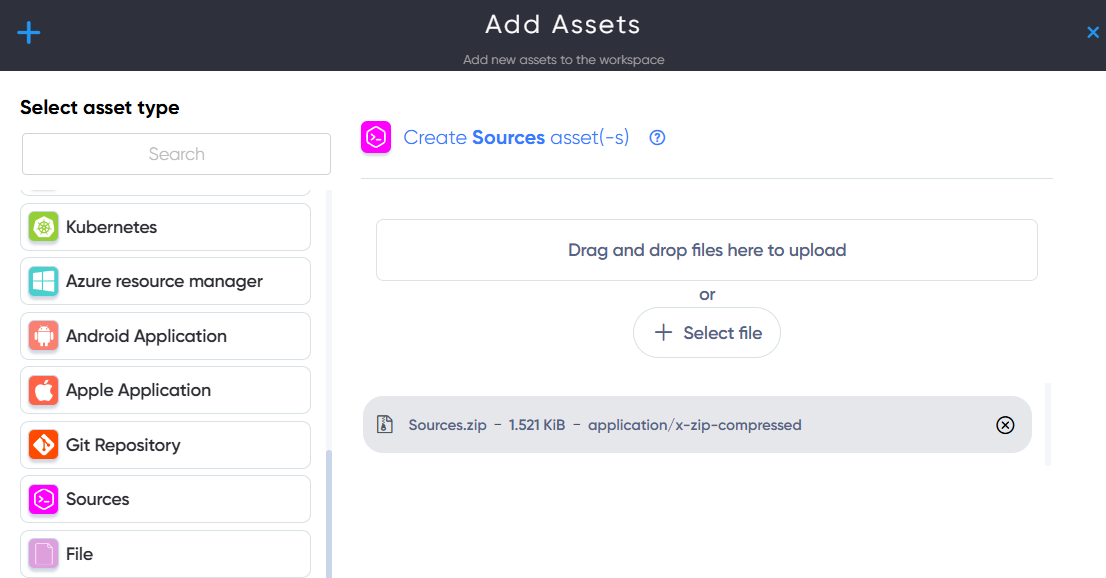
¶ Sources Asset
In Sources asset users can add source code archive with application source code. for scan to find vulnerabilities, hardcoded misconfigurations, emails, usernames, passwords.
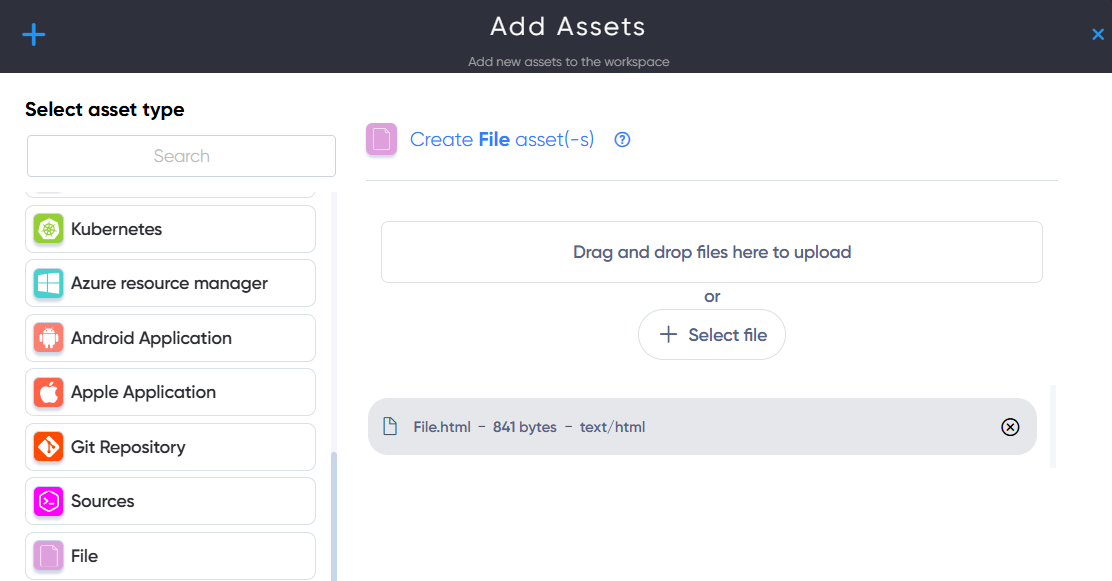
¶ File Asset
In File asset users can add any file for analyzing and understanding the behavior and vulnerabilities of binary code to identify and mitigate potential security risks.
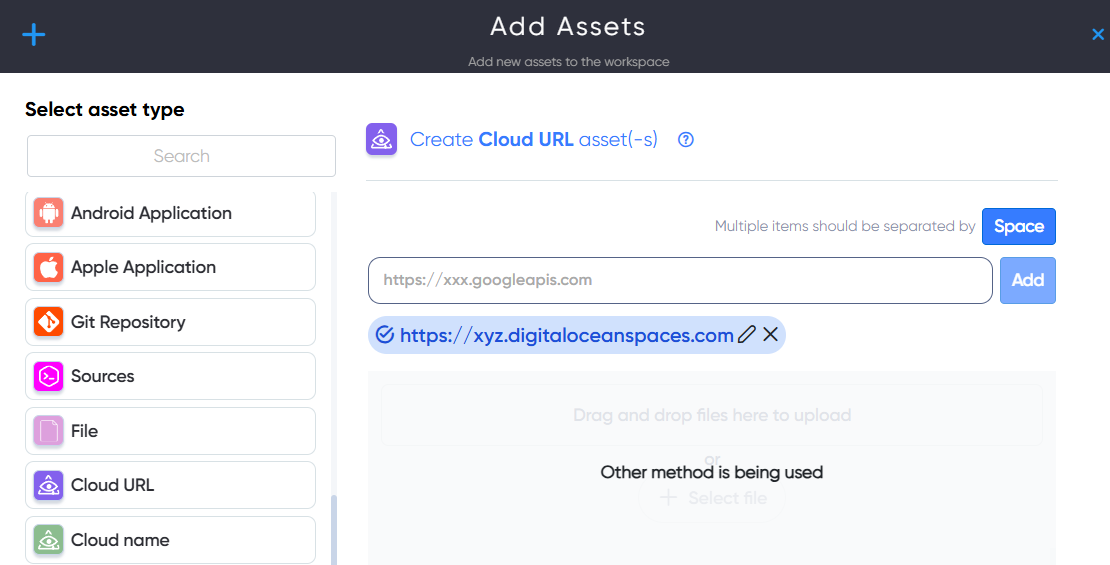
¶ Cloud URL Asset
The Cloud URL asset allows users to provide a URL for a cloud asset located with a cloud provider. For example: https://xxx.digitaloceanspaces.com
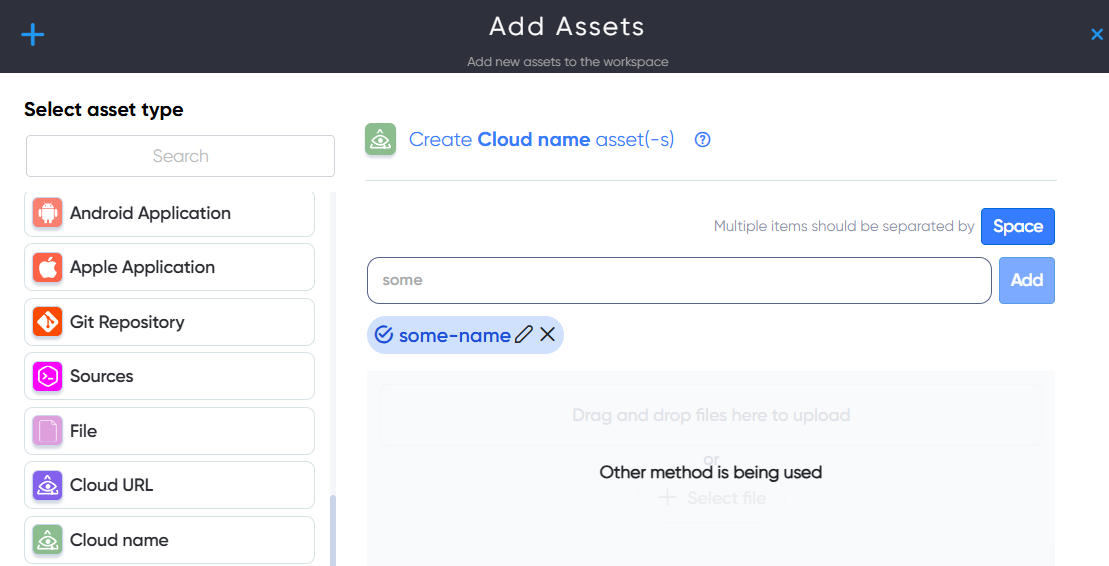
¶ Cloud Name Asset
The Cloud Name asset allows users to provide a name for a cloud asset located with a cloud provider. For example: somename or some-name
¶ Email Asset
In Email asset users can enter and scan electronic mail address for information leaks and breaches. For example: [email protected]
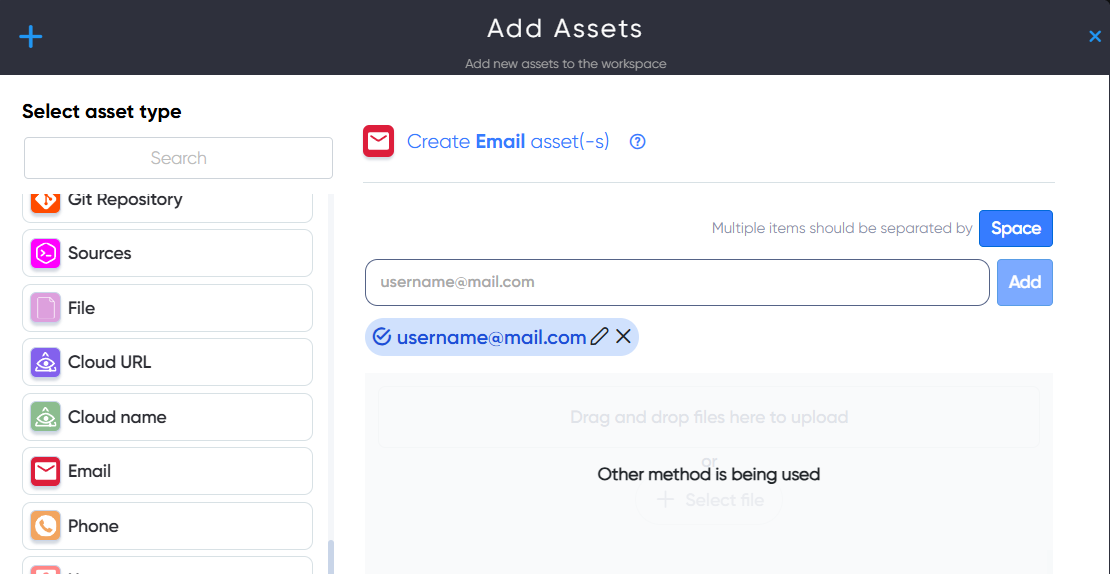
¶ Phone Asset
In Phone asset users can enter and scan phone numbers for information leaks. For example: +1234567890
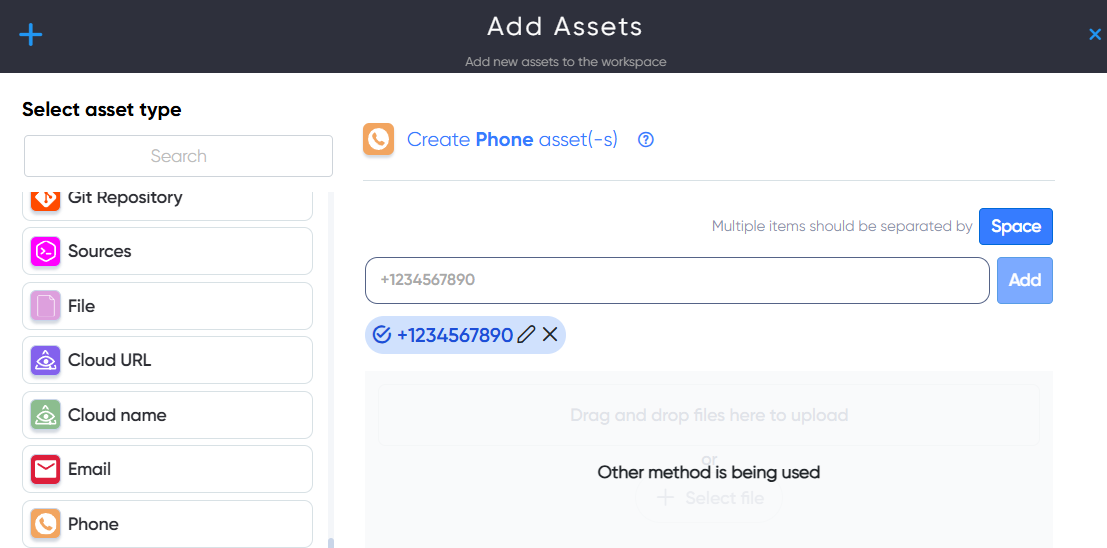
¶ Username Asset
In Username asset users can enter and scan Usernames for information leaks and breaches. For example: username_123
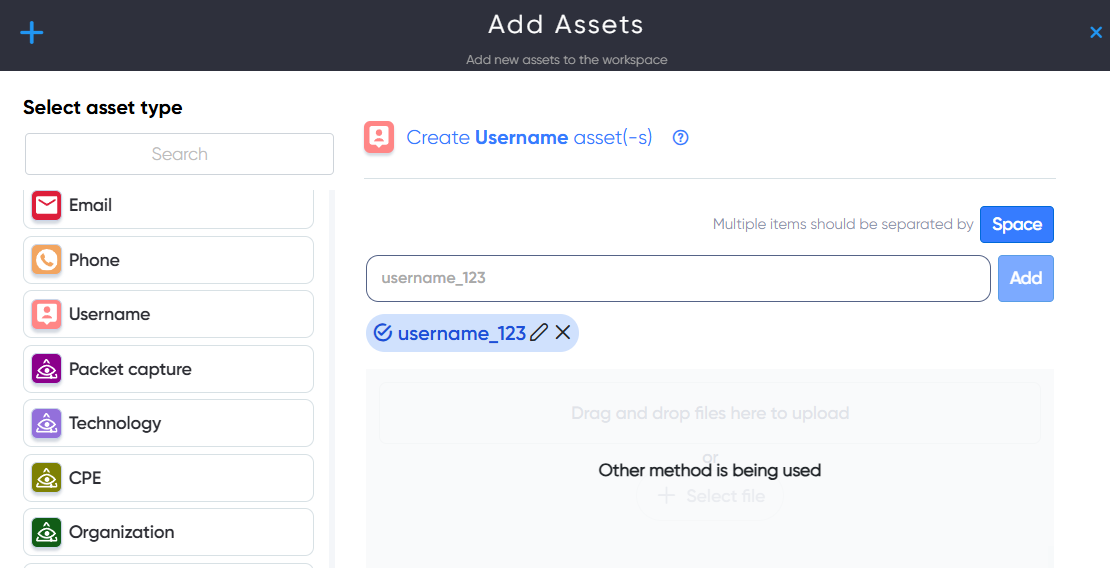
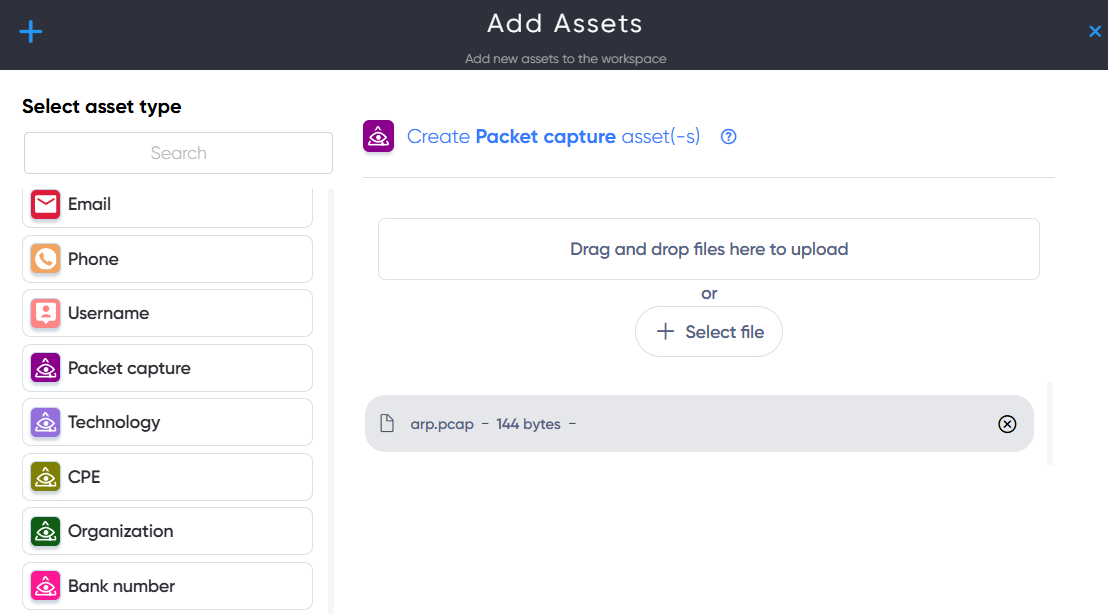
¶ Packet Capture Asset
In Packet Capture asset users can upload Packet capture file with extentions .pcap, .cap, .dmp for analysis, and interpretation of network traffic data.
¶ Technology Asset
In Technology asset users can add technology for scaning to find a vulnerabilities, exploits, PoCs. For example: Django 3.0
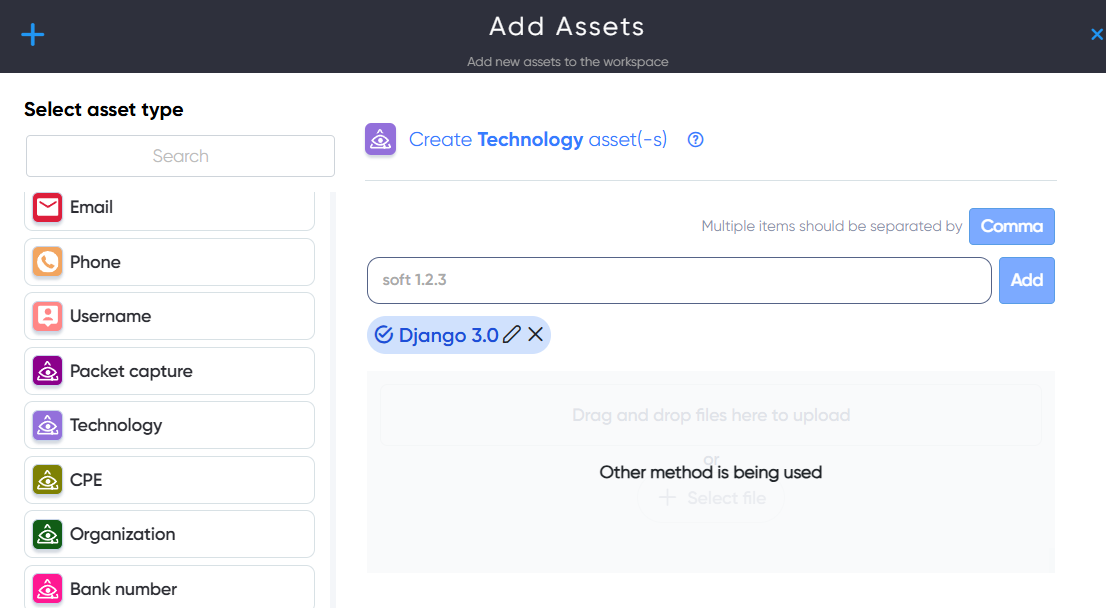
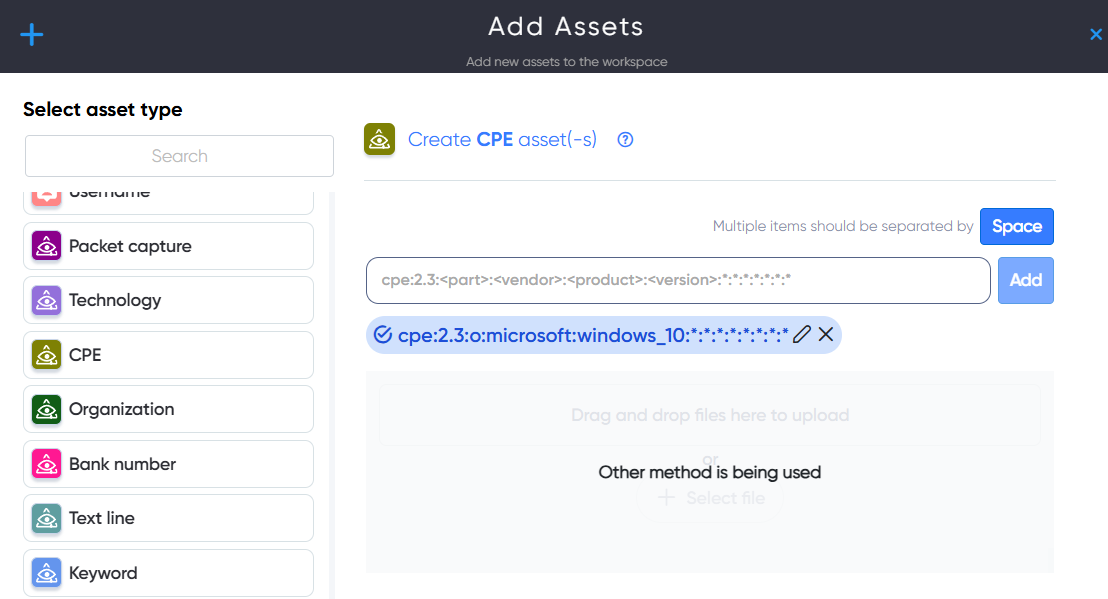
¶ CPE Asset
In CPE asset users can add technology in CPE 2.3 format for scaning to find a vulnerabilities, exploits, PoCs.
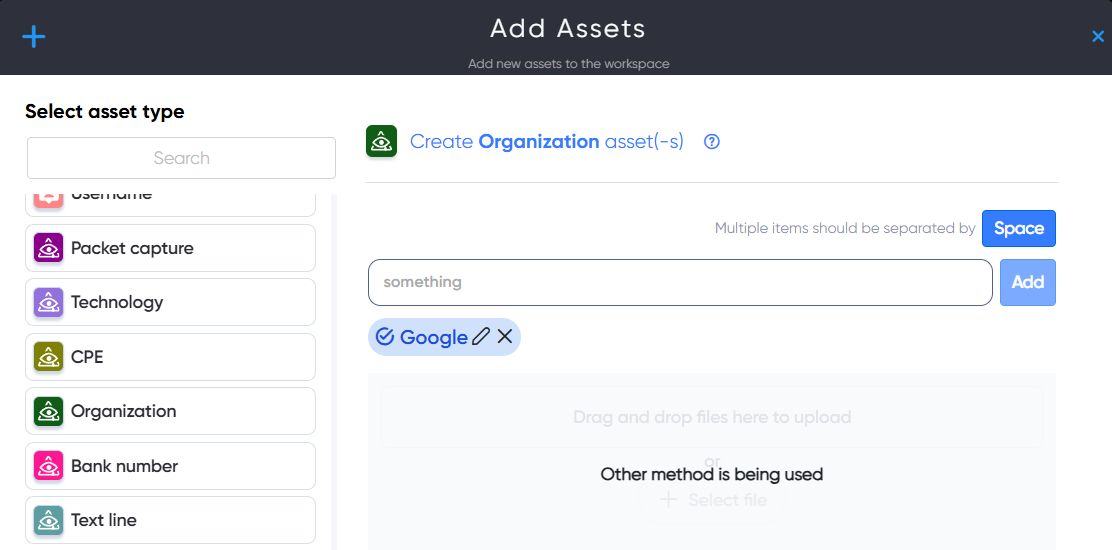
¶ Organization Asset
In Organization asset users can add name of organization, company or groupe for information gathering, OSINT. For example: Google
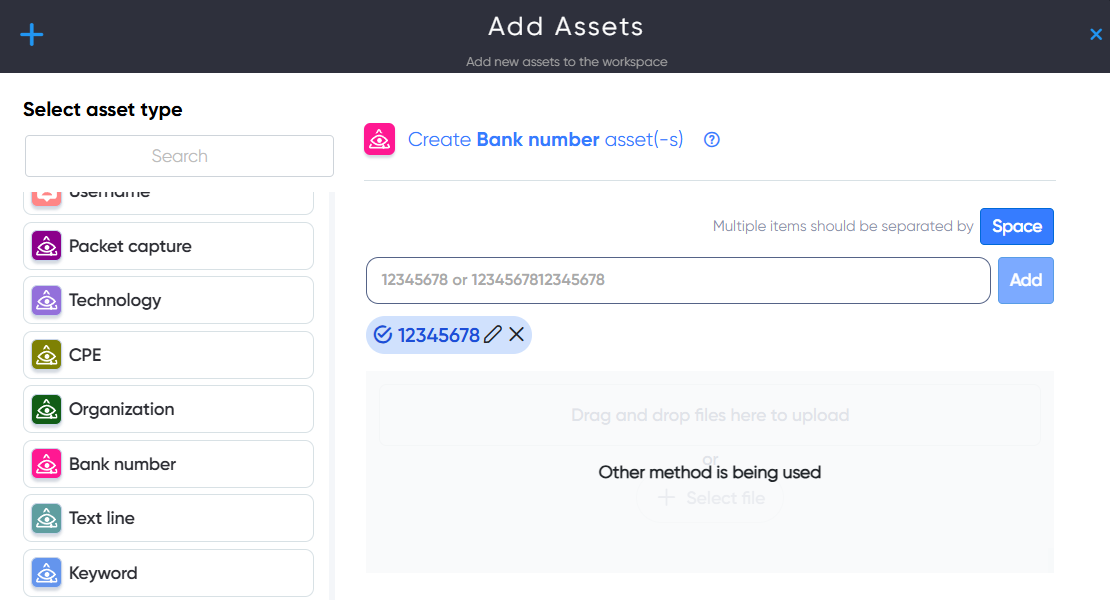
¶ Bank number Asset
In Bank number asset users can add IBAN or credit card number for check leaked information.
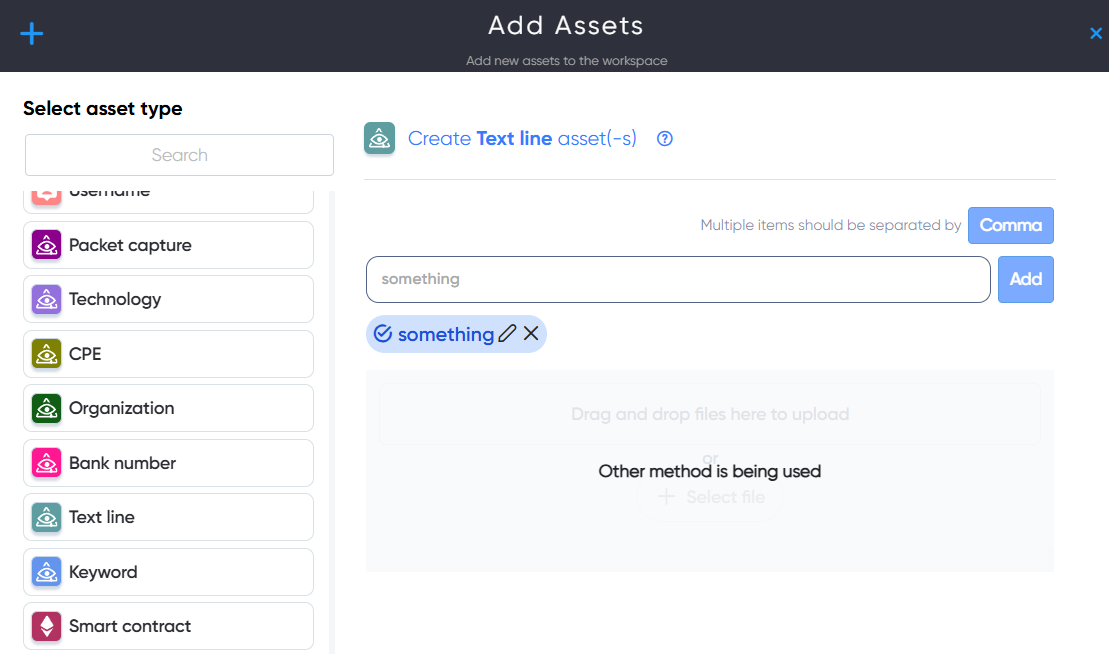
¶ Textline Asset
The Text Line asset is for general use, allowing users to input a text string or a single word for various purposes.
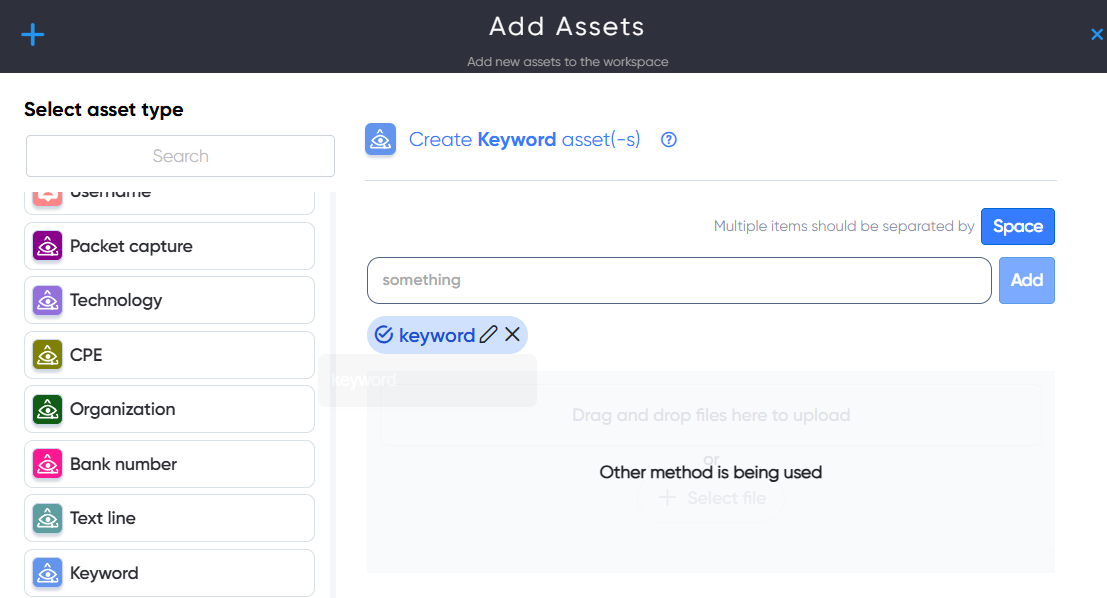
¶ Keyword Asset
In Keyword asset user can add a keyword to search for similar domain names and url addresses and check them for phishing.
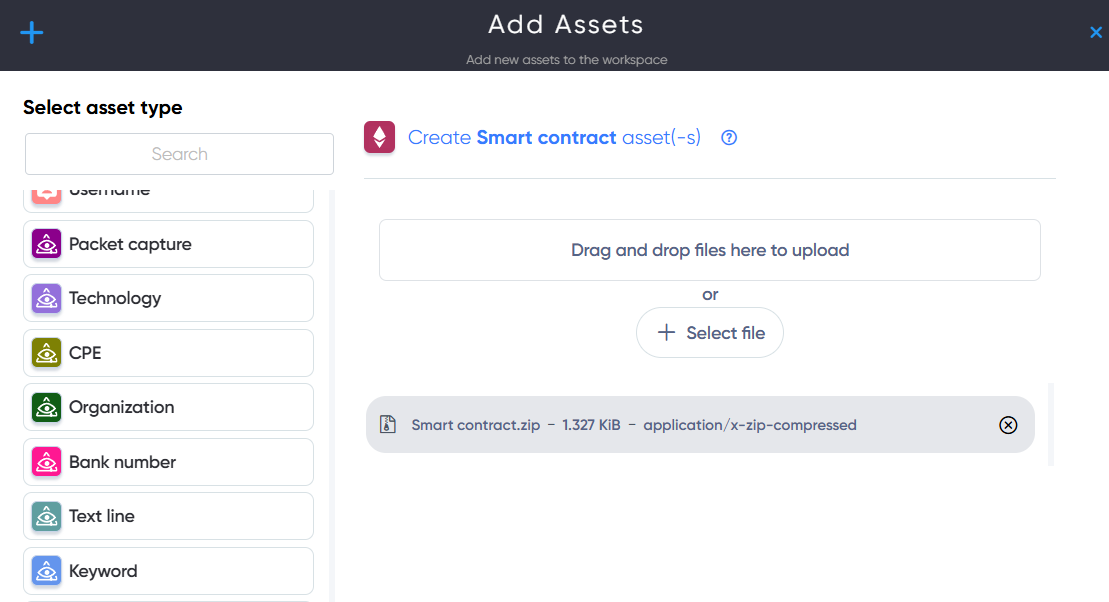
¶ Smart contract Asset
In Smart contract asset users can Upload and scan Self-executing smart contract files for different blockchains.
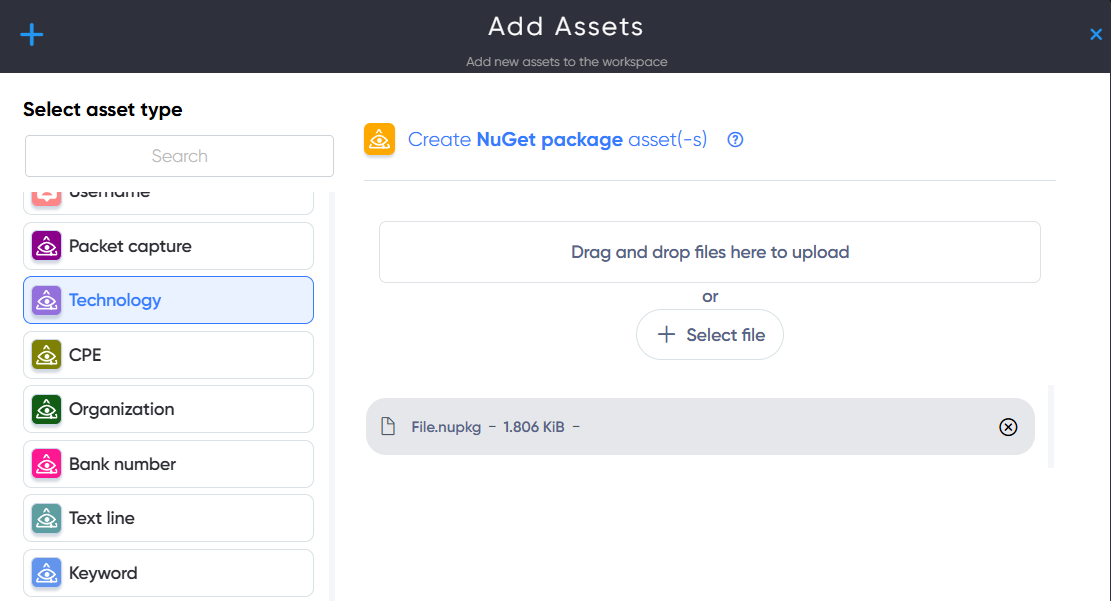
¶ NuGet Package Asset
In NuGet Package asset users can add archive file with some NuGet packegas for vulnerability scan.
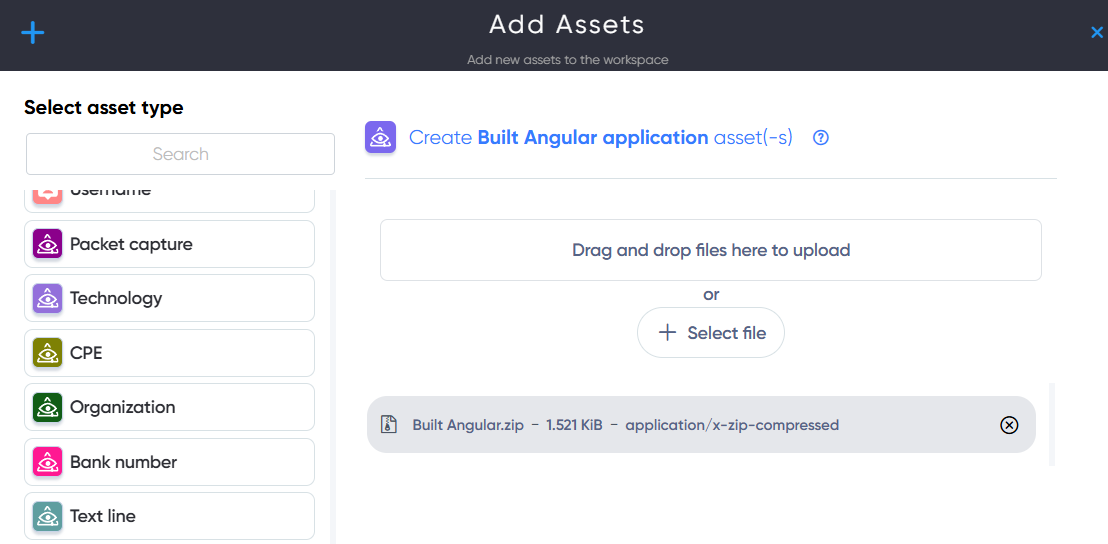
¶ Built Angular Application Asset
In the Built Angular Application asset, users can add a Zip archive with a built Angular application (JavaScript files) for vulnerability scanning.
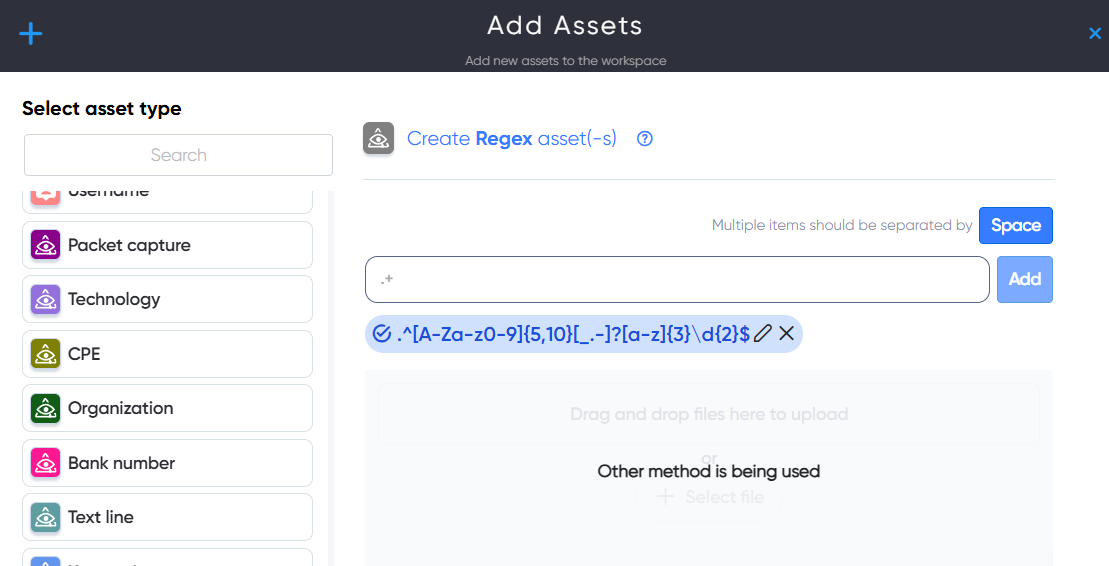
¶ Regex Asset
In Regex asset users can add regular expression for darknet monitoring triggers.
¶ Custom Asset
In Custom asset users can enter or upload anything else that is not listed here.