¶ Audits System Singular
¶ Video — Briefly about features, modules, and use cases.
In Audits (Singular) users can create projects to work with one target. This means that you can create many projects, but you can only run scans on one target per project.
For example you create Singular Url project and you can run Web audits on url, but if you need to run same Web audits to IPv4 target you need to create new Singular project with IPv4 asset.
¶ Singular target project creation
Users can directly create singular targets project from Add assets page.
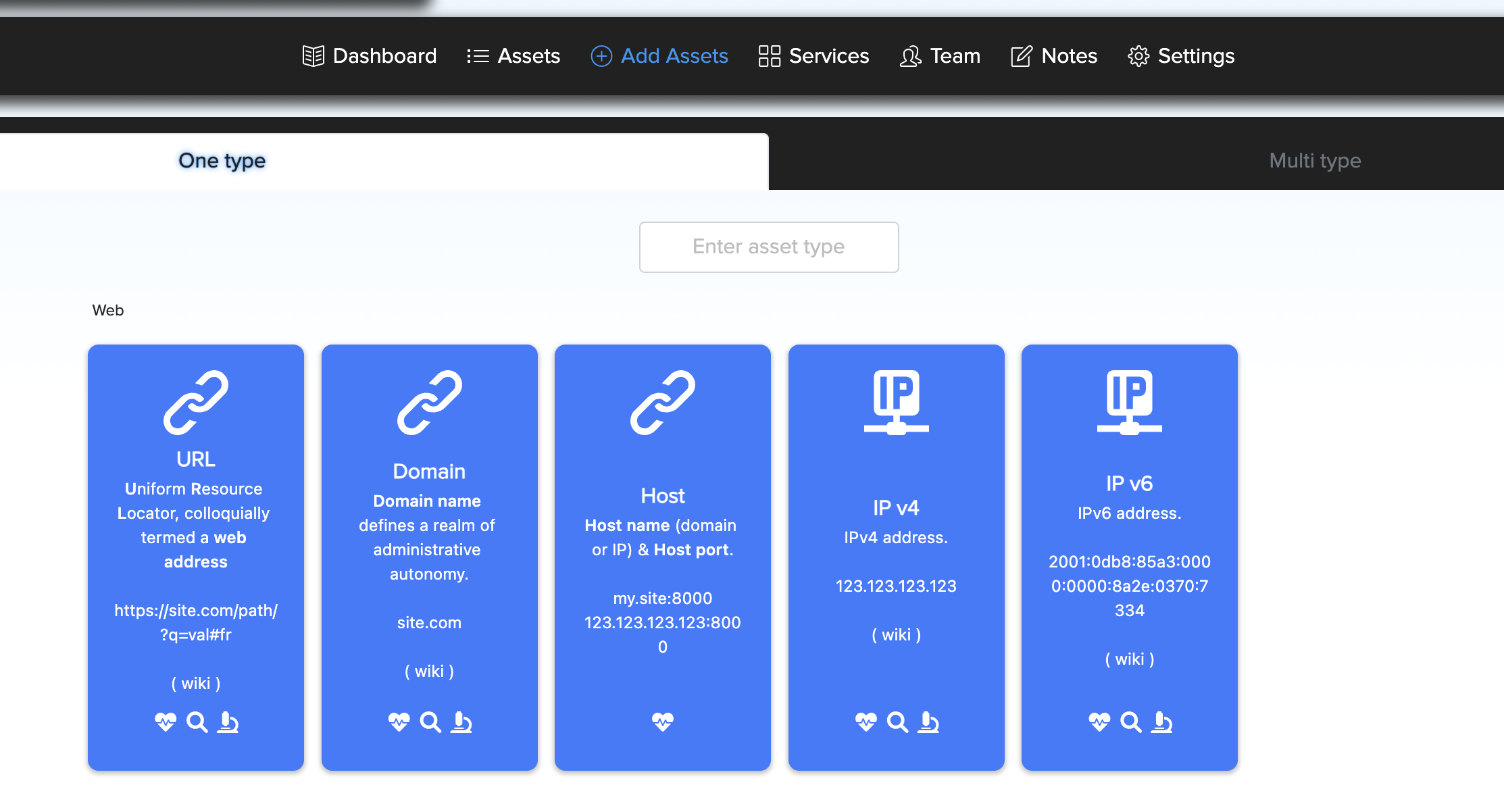
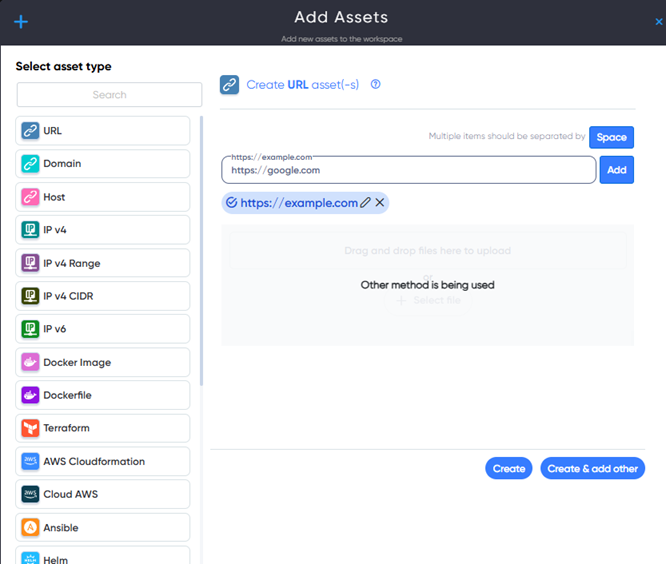
For example, You can click on Url asset icon and enter url target and go to singular target project.
Or Users can create singular target project later from assets dashboard.
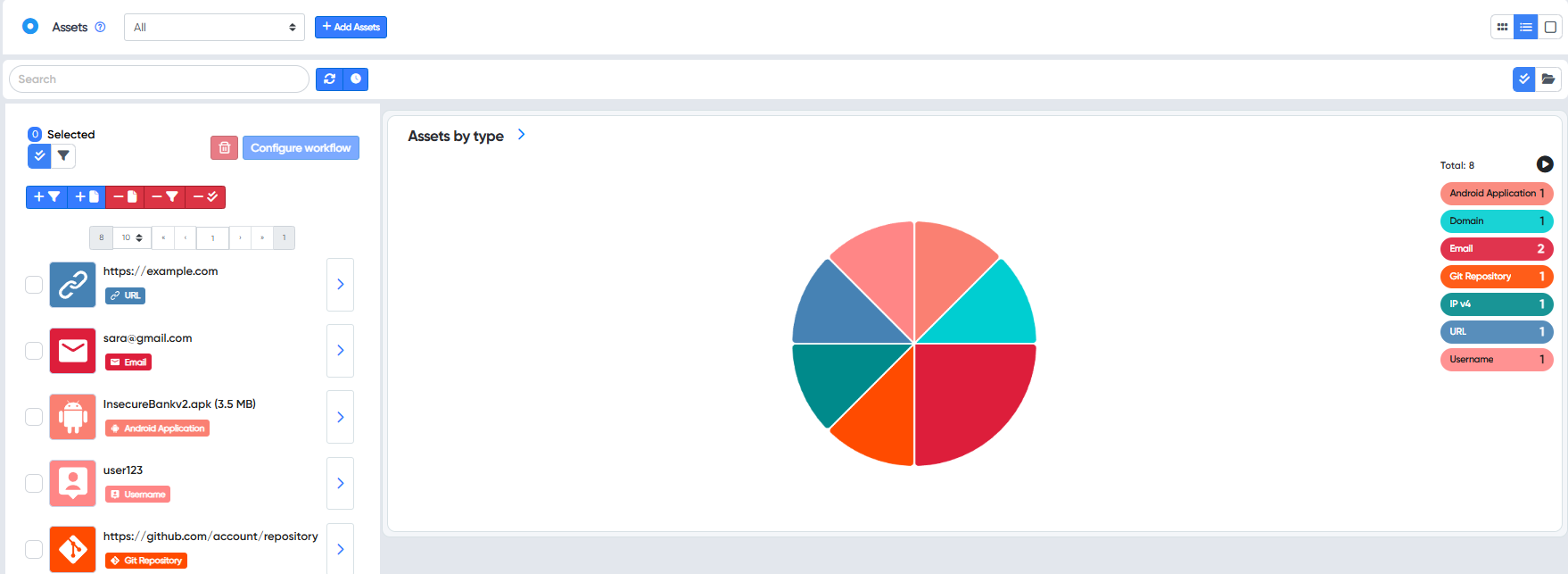
Then you can go directly to project or open created project from singular target projects list.
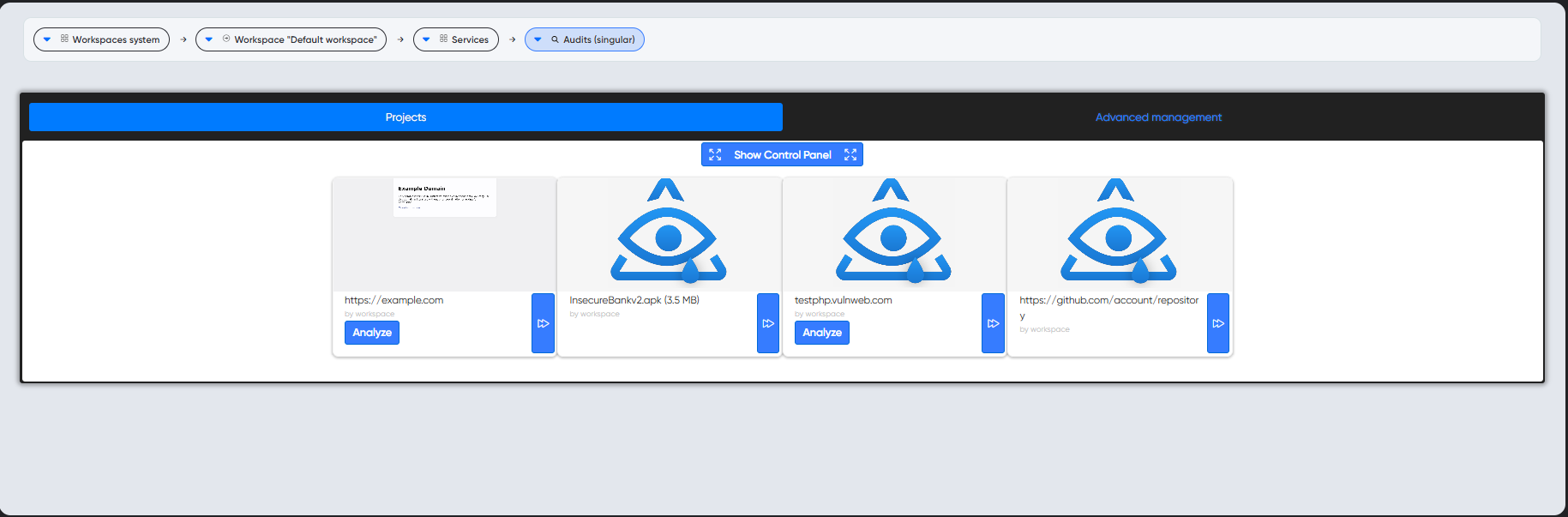
¶ Project running
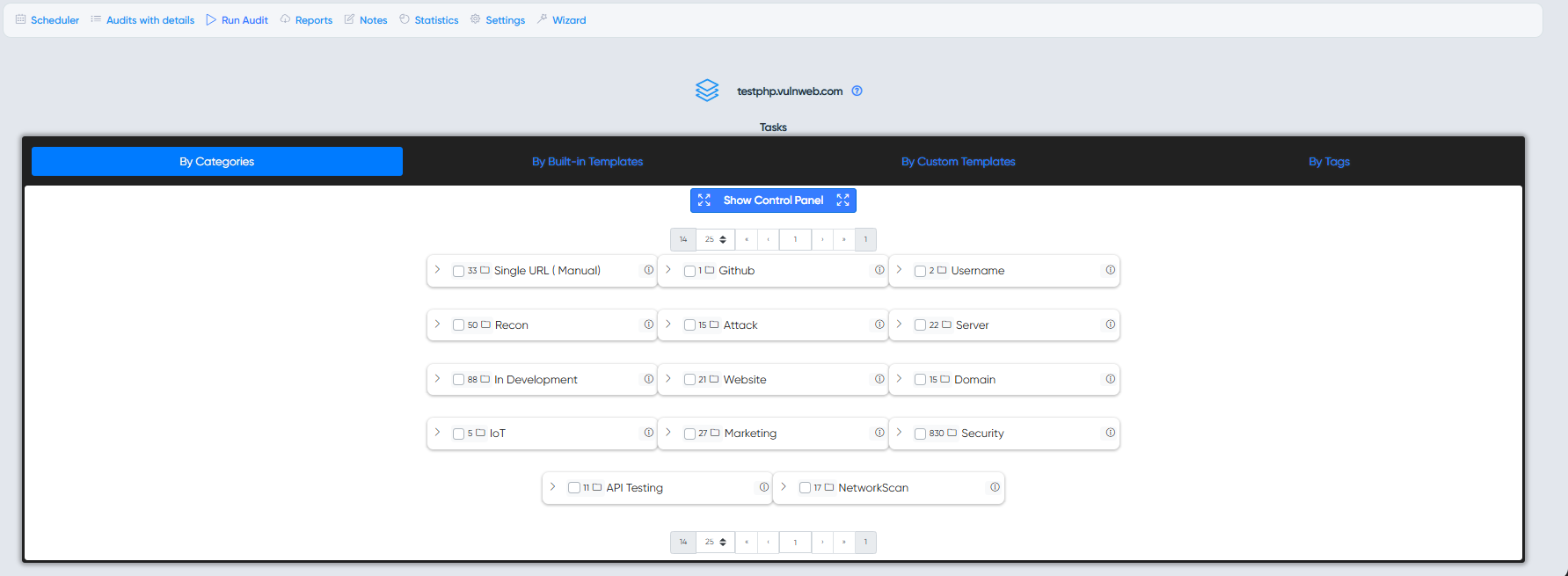
After opening project you can choose and run audits from Run Audit page.
Users can select audits sorted by standard categories.
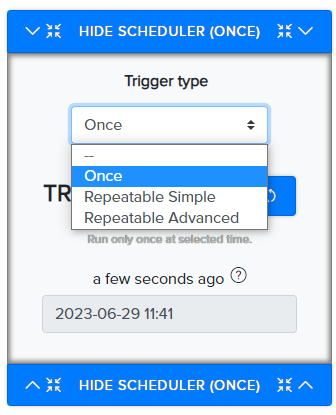
Also you can schedule a scan and choose the exact start time of the scan, or you can set up a rescan in simple and advanced variants.
¶ Templates
Templates are handy sets of different audits with similar functions that are aimed at finding the same results to confirm problems. Build In Templates contain sets of audits specially selected by the project developers for auditorium users.
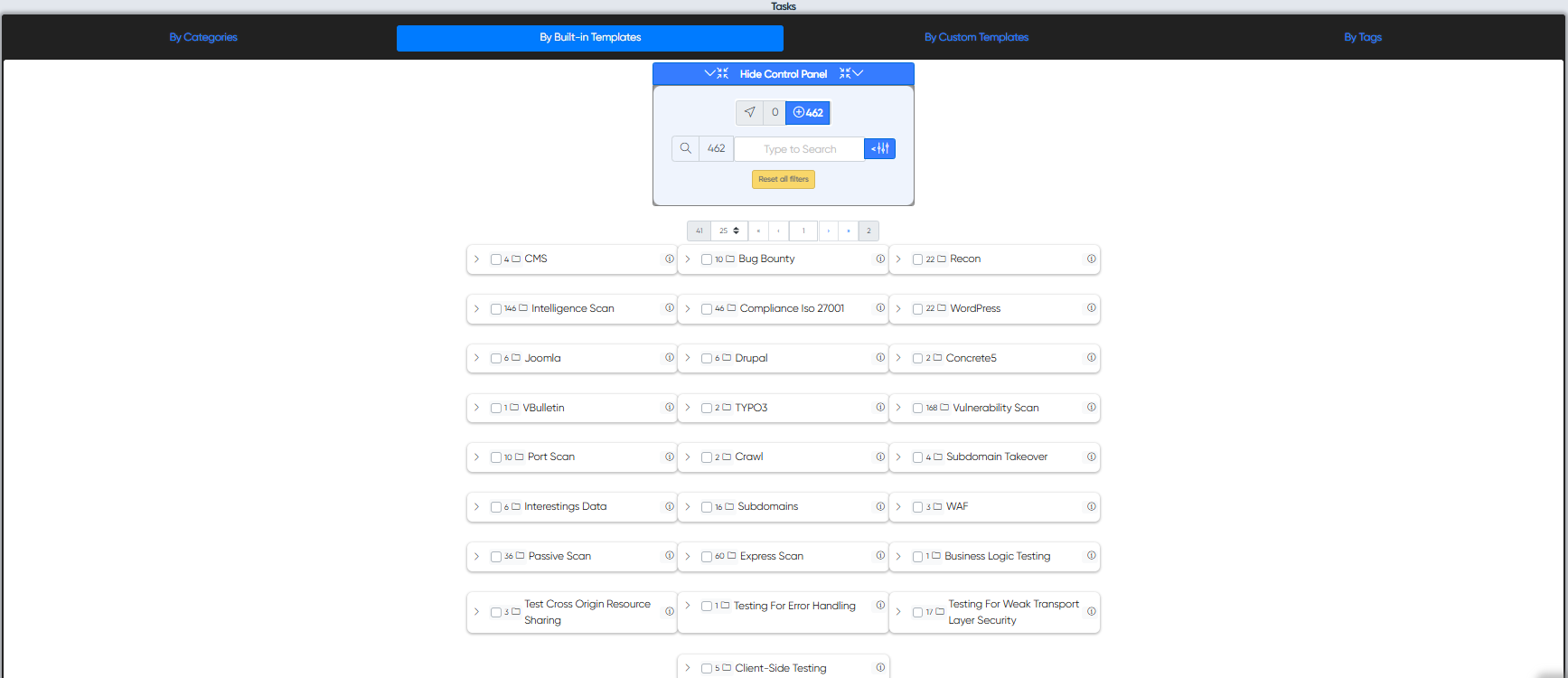
Custom Templates can be created by users themselves for specific purposes, creators can modify and delete their templates at will.
¶ Tag system
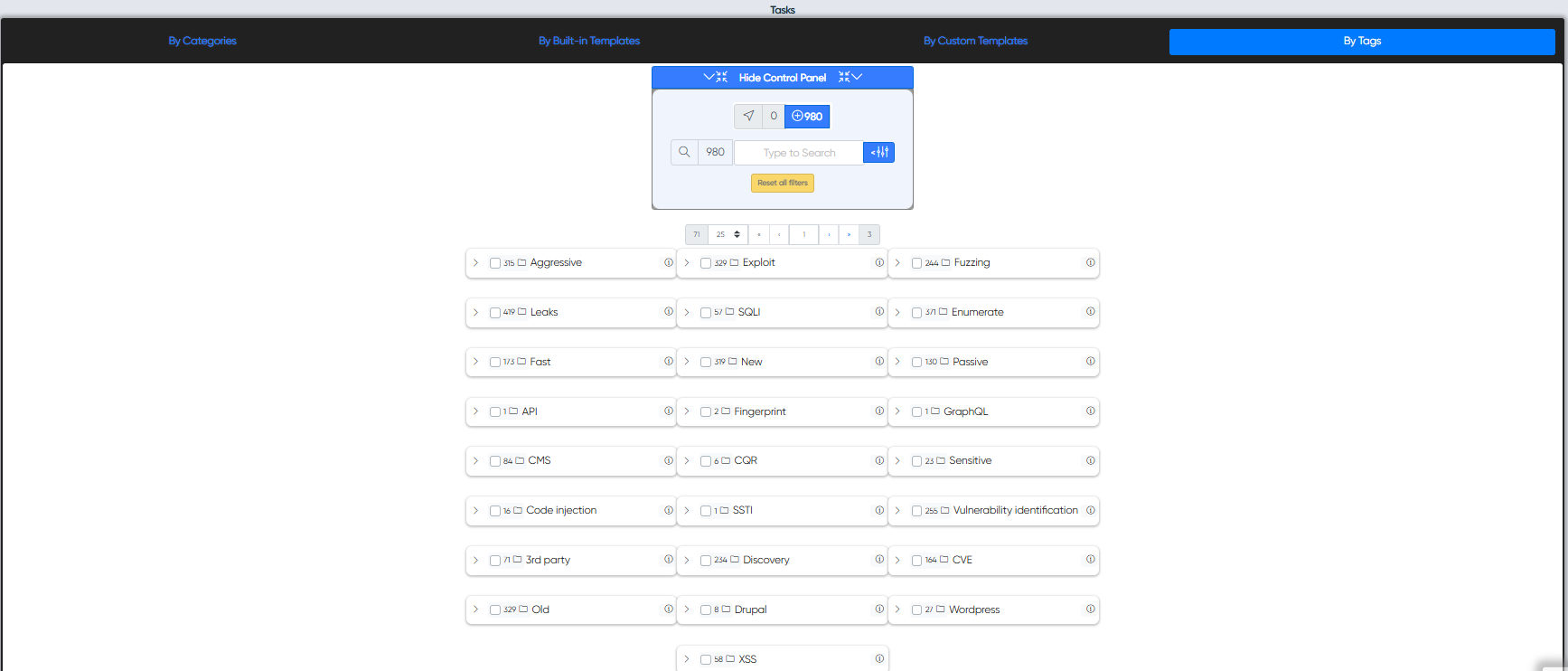
Also Users can find neddend audits by using Tag system. The tag system is a very convenient tool, the user selects the desired tags, and the system sorts the audits that relate to them, for example, select the xss tag and the system will show audits to search for XSS vulnerabilities.
Smart Tag System will help you quickly find needed audits and suggest a proper list of tools to include into your project.
¶ CryAI Wizard
If the presented sorting methods do not suit you, you can always use CryAI Wizard function
CryAI Wizard - a special feature designed to help users select the audits that are appropriate for their systems. The CryAI Wizard system analyzes technologies and services on the website, verifies against the database and offers audits for scanning that match the criteria and technologies found on the website.

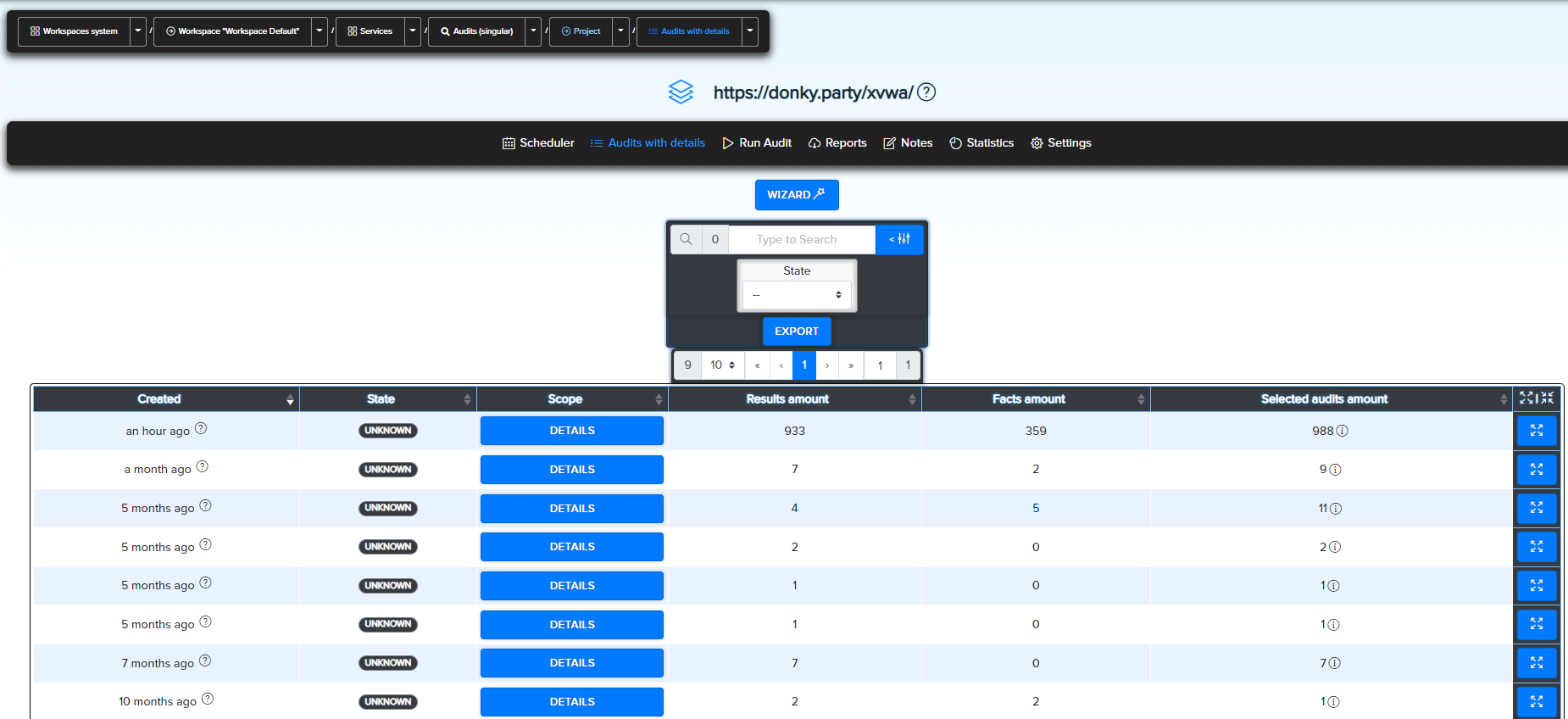
¶ Scan results
Users can see their Scans results on Audits with details.
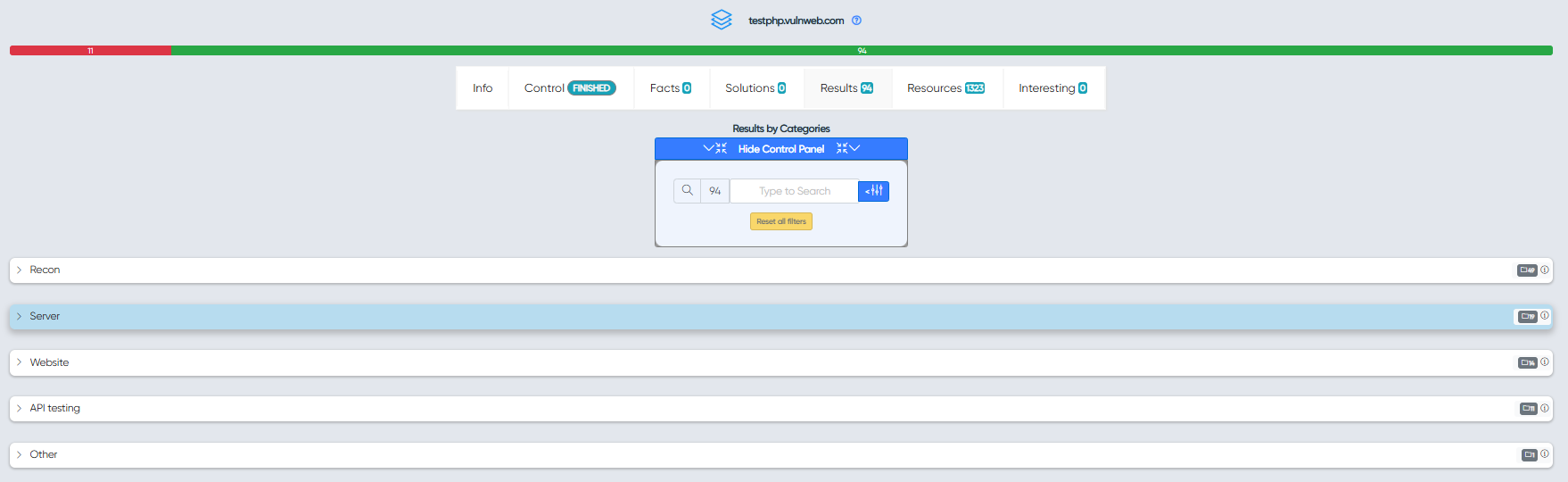
¶ Audits Results
Here are the scan results of all audits in this scan workflow.
¶ Facts
Facts are valuable information extracted from scan results, depending on the data found, facts have different characteristics such as severity, css3 score and CWE number.

Same as with Audit results, Users can sort and open a fact and see a description of what information or vulnerability was discovered, provide its number and classification in vulnerability databases, an overall threat score, and more.
¶ Solutions
Solutions are similar to Fact, but the give you advice on fixing founded vulnerabilities.
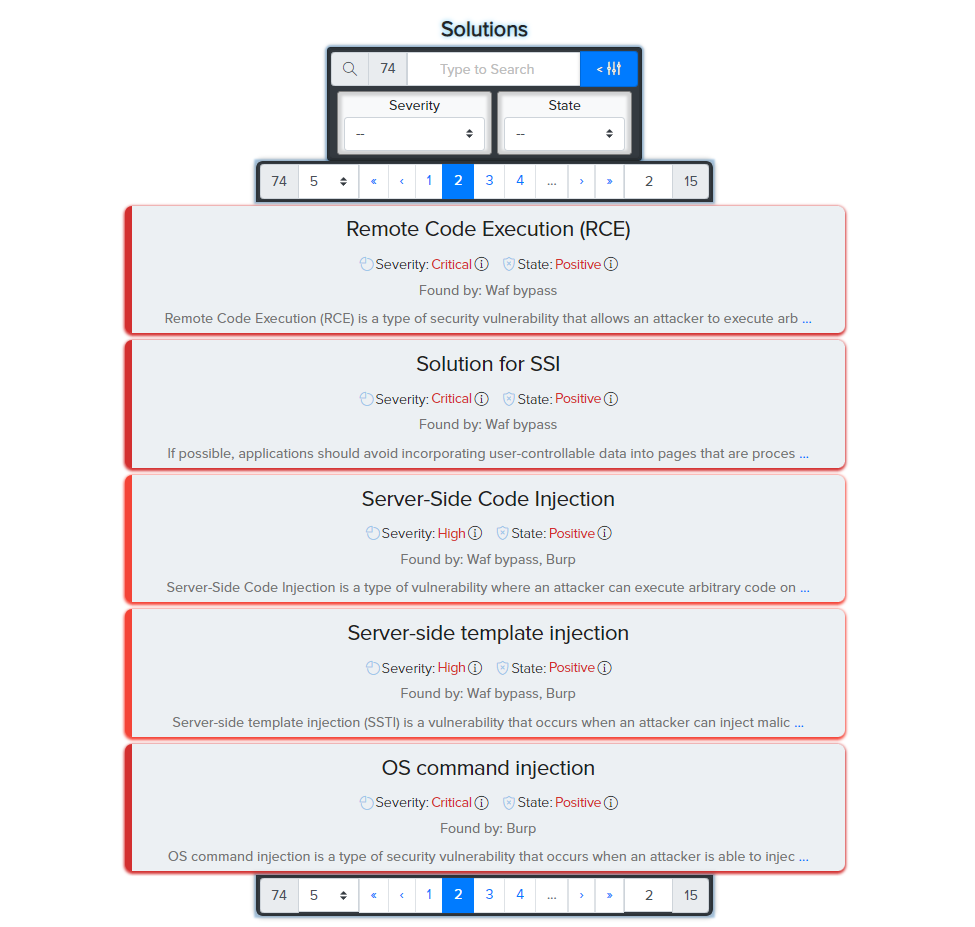
As with the facts, users can sort and open the solution to see recommendations for fixing the discovered vulnerability.
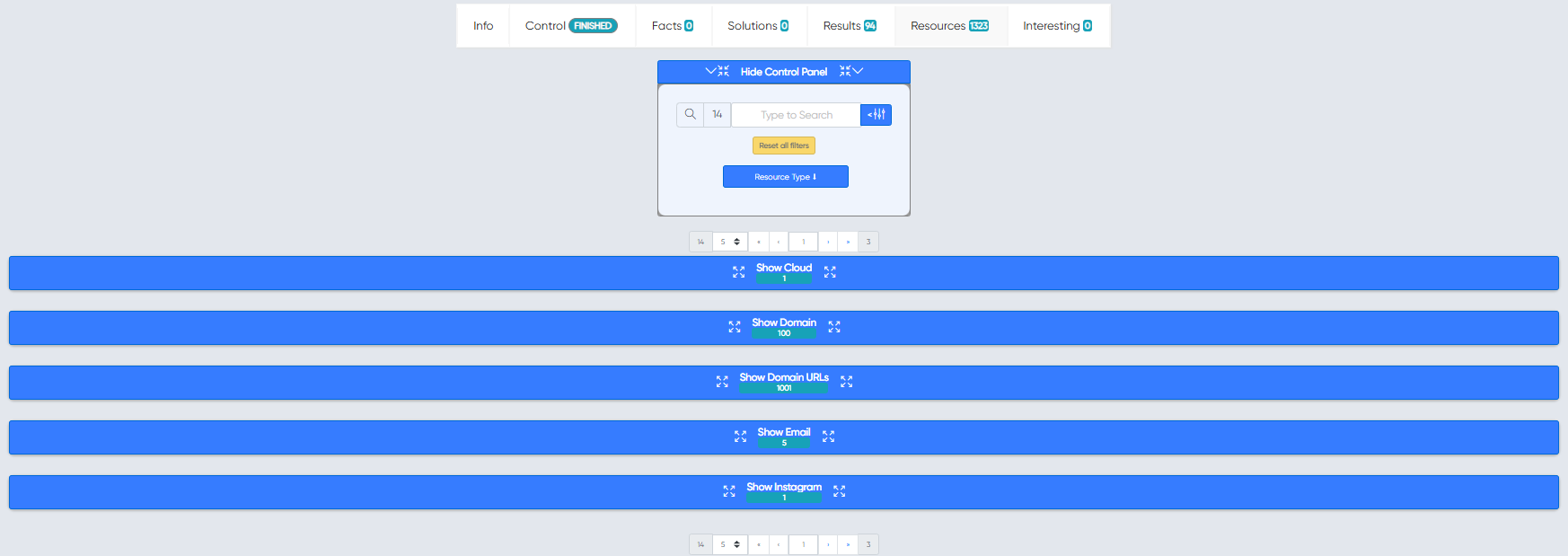
¶ Resources
Resource extraction systems extract information about the target's web resources from results.
Multiple results are parsed and recognized as resources after being analyzed based on its type: URL, Domain, Subdomain, Email, CVE, IPv4, IPv6 and more others.
¶ Additional fuctions
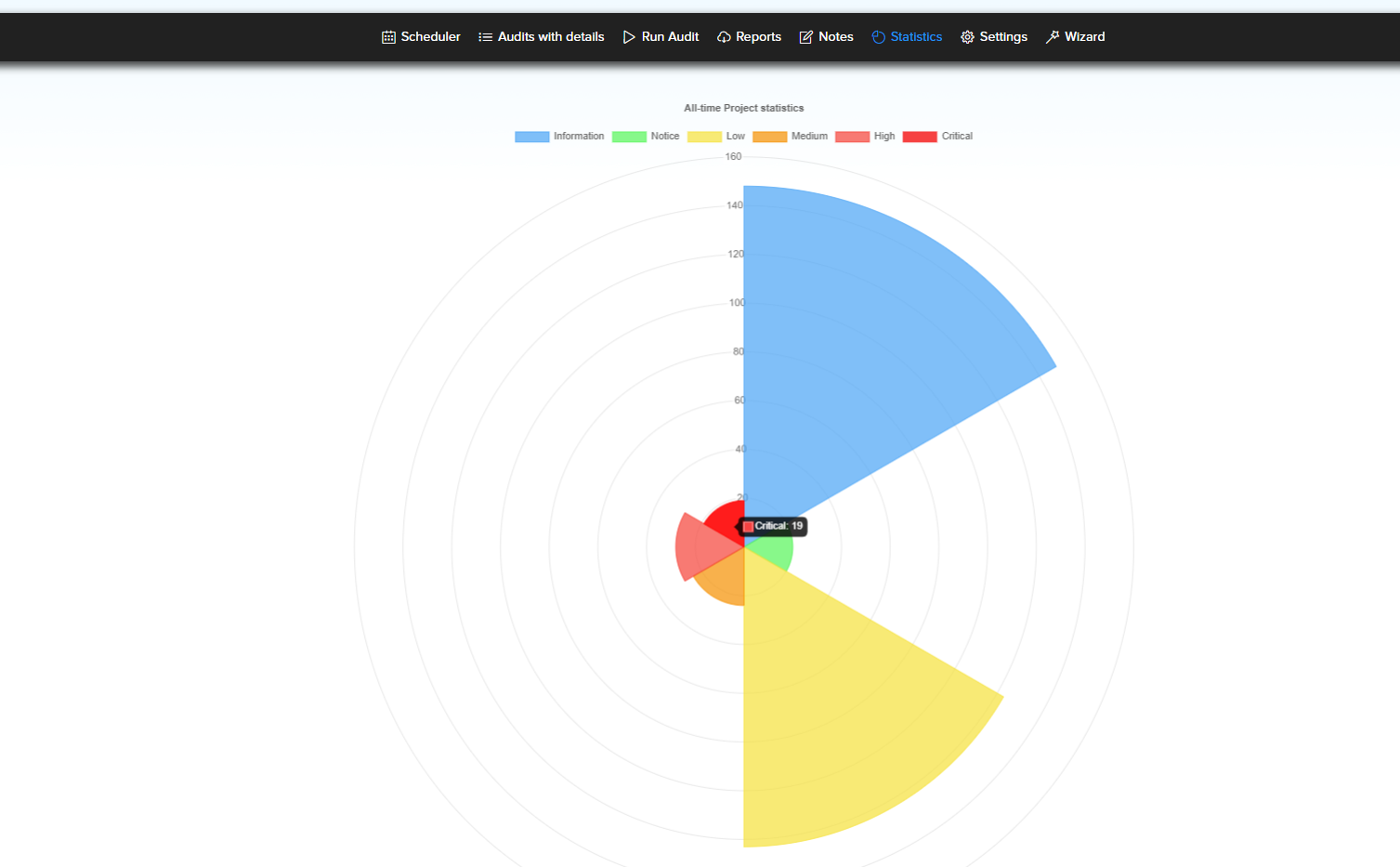
In addition to the results in the project Statistics, users can view graphs of finded facts.
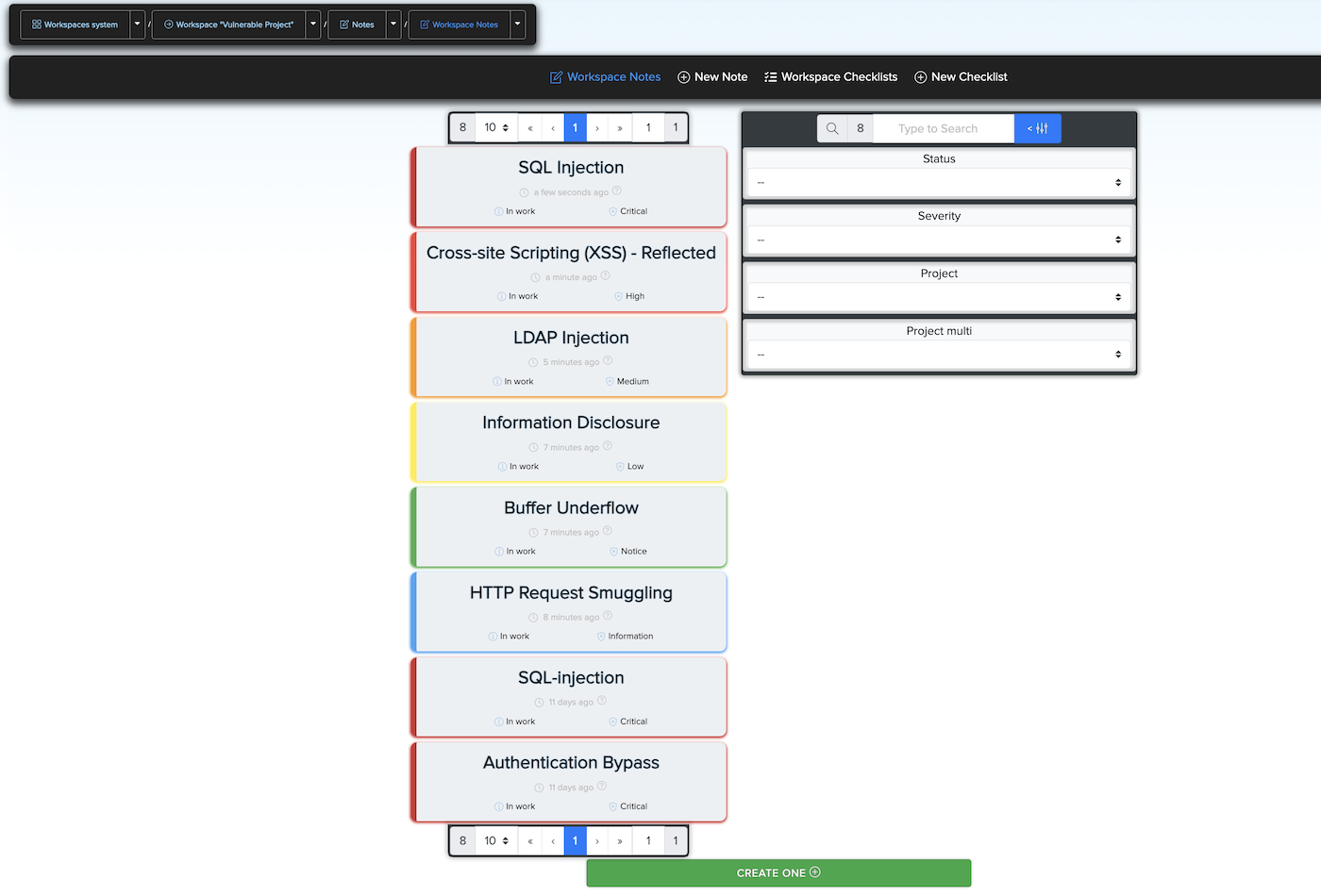
Users Notes where you can create notes and checklists in them however you like.
¶ Report System
The Report System helps users to generate lightweight reports with QR codes and access technical details via any smart device.
We created a report generator that generates customizable reports from the facts, results, and resources extracted during a vulnerability assessment. It has a QR code to access the HTML-based results right in your browser easily - it means you are not missing anything in your report. Generate your custom report, and you are good to go.
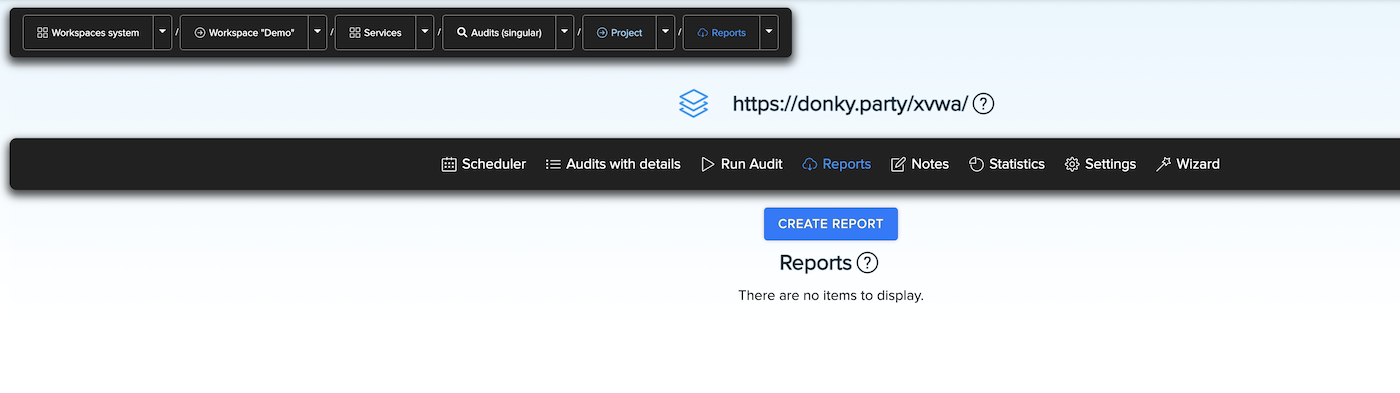
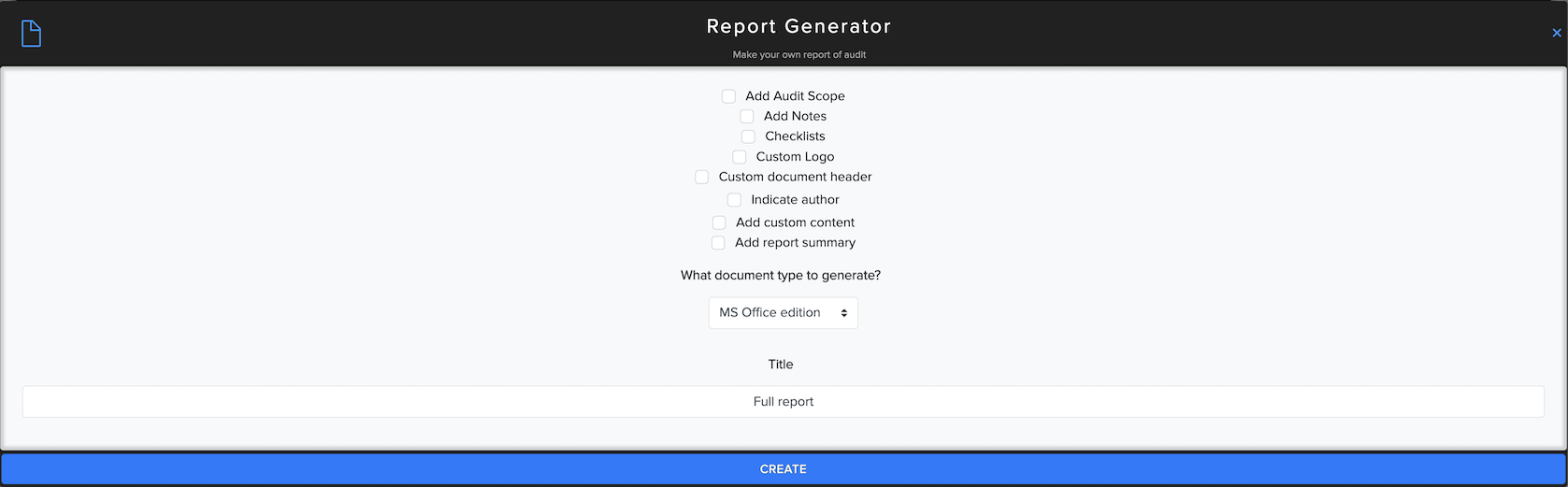
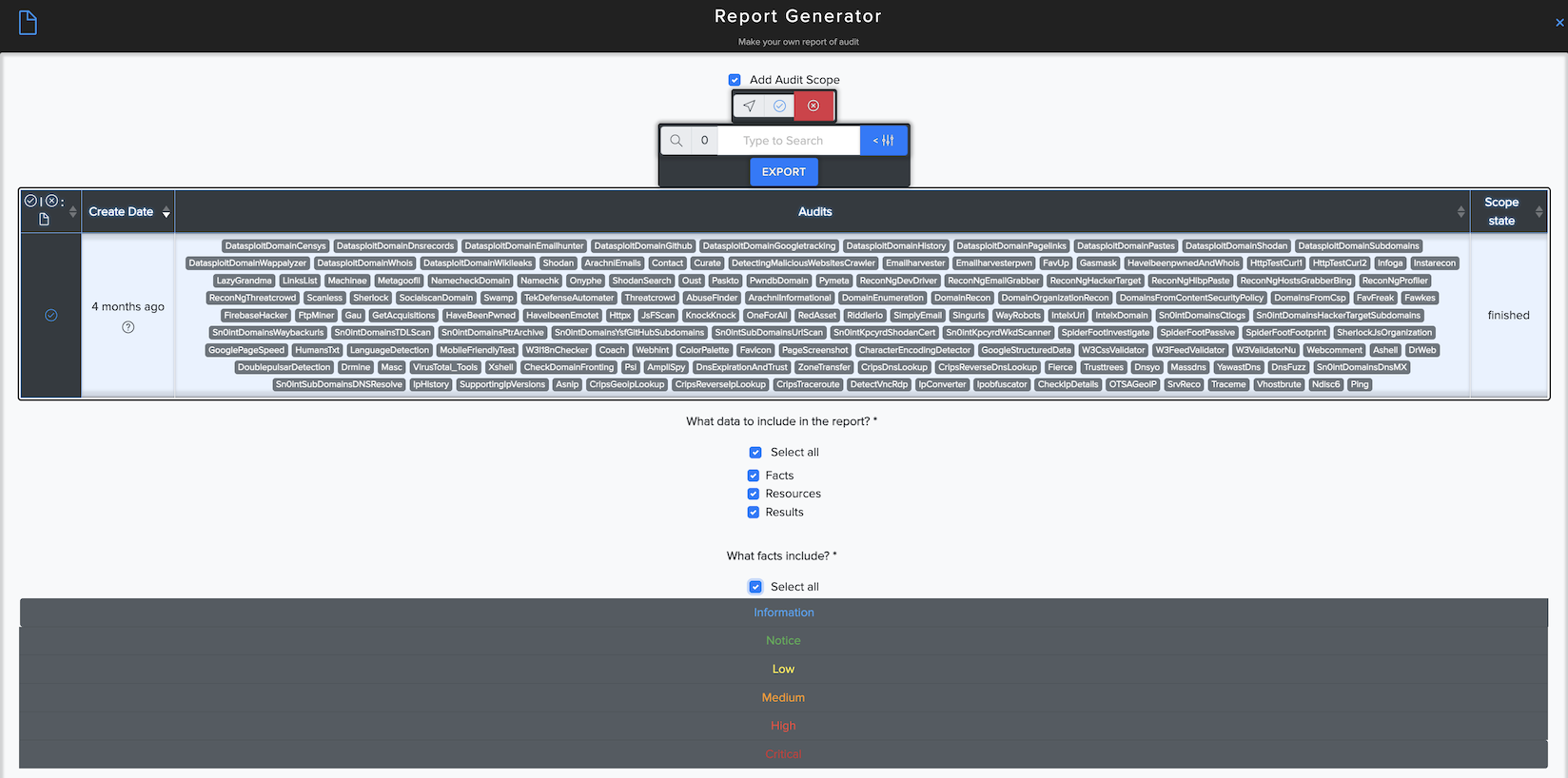
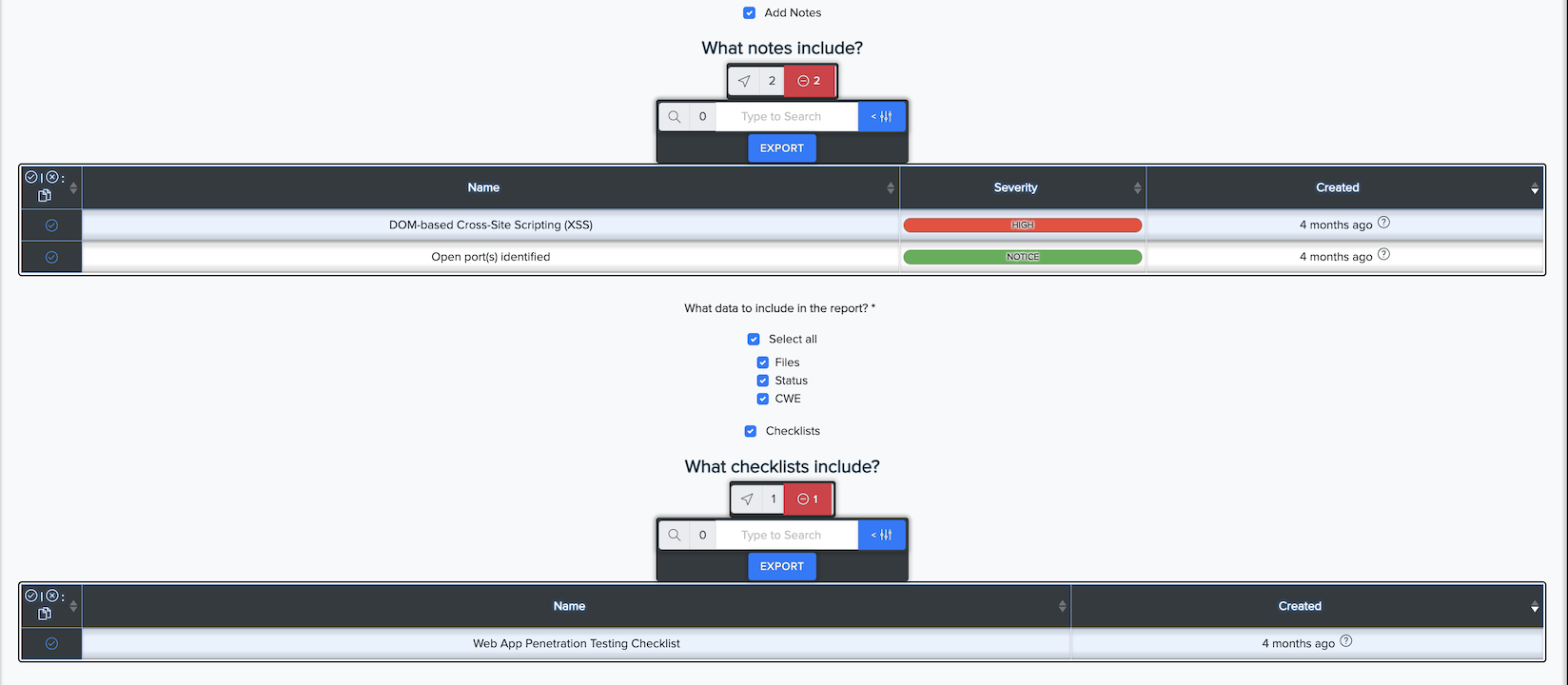
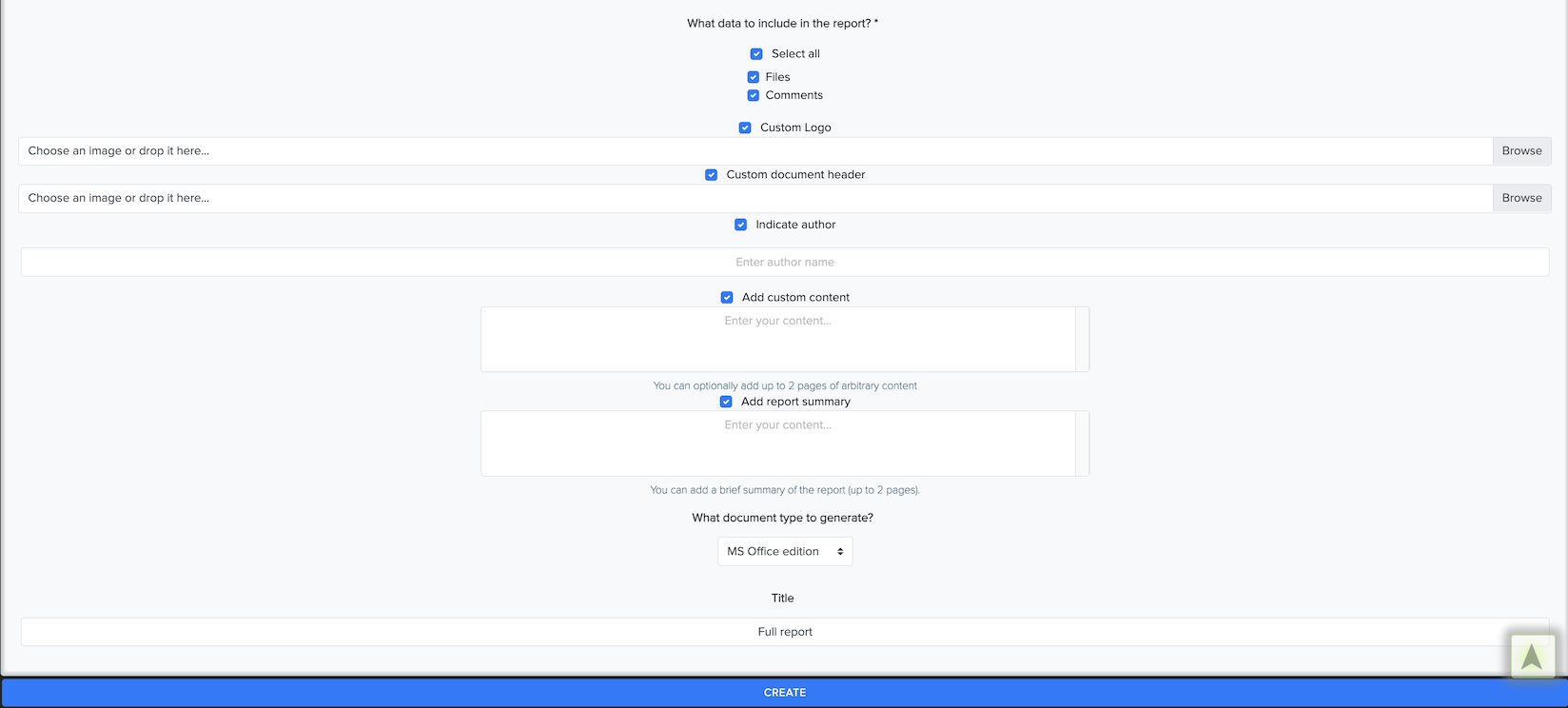
You can see and download a report with results.
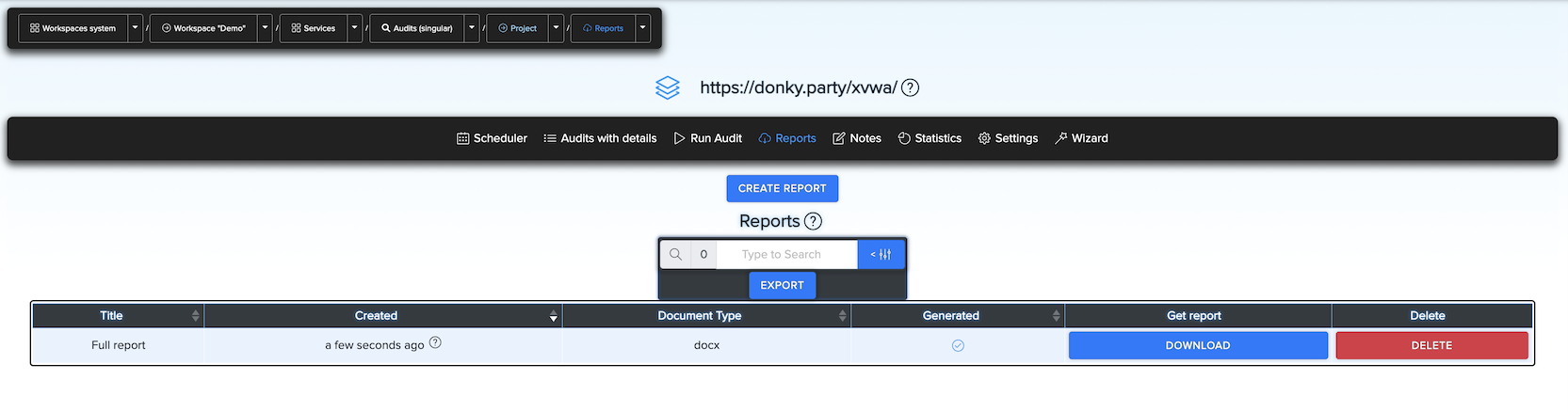
Example of report document.