¶ 🛡️ Audits System
¶ ❓ What is Audits system?
In CryEye, we’ve integrated many open-source and licensed security tools called audits. Users can manually run audit checks on their Assets.
¶ 🔍 CryEye Audits
Audits cover multiple domains:
¶ 🌐 Web Audits
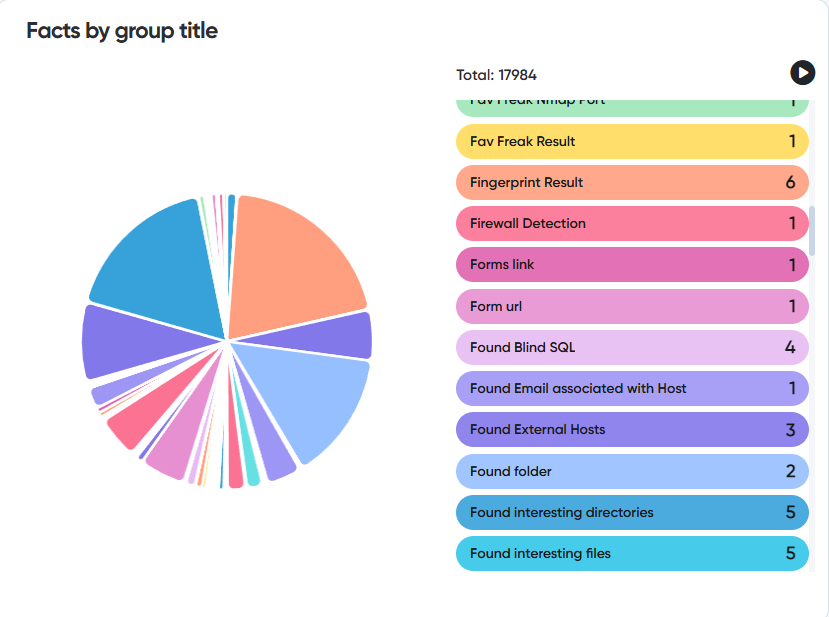
You can scan web resources for:
- Security vulnerabilities
- Malware
- Weak credentials (bruteforce)
- User and file enumeration
- Security exploits
- Server configuration leaks
- Subdomains & phishing domains
- UX/Design recommendations
📷 Example:
¶ 🏗️ Infrastructure Audits
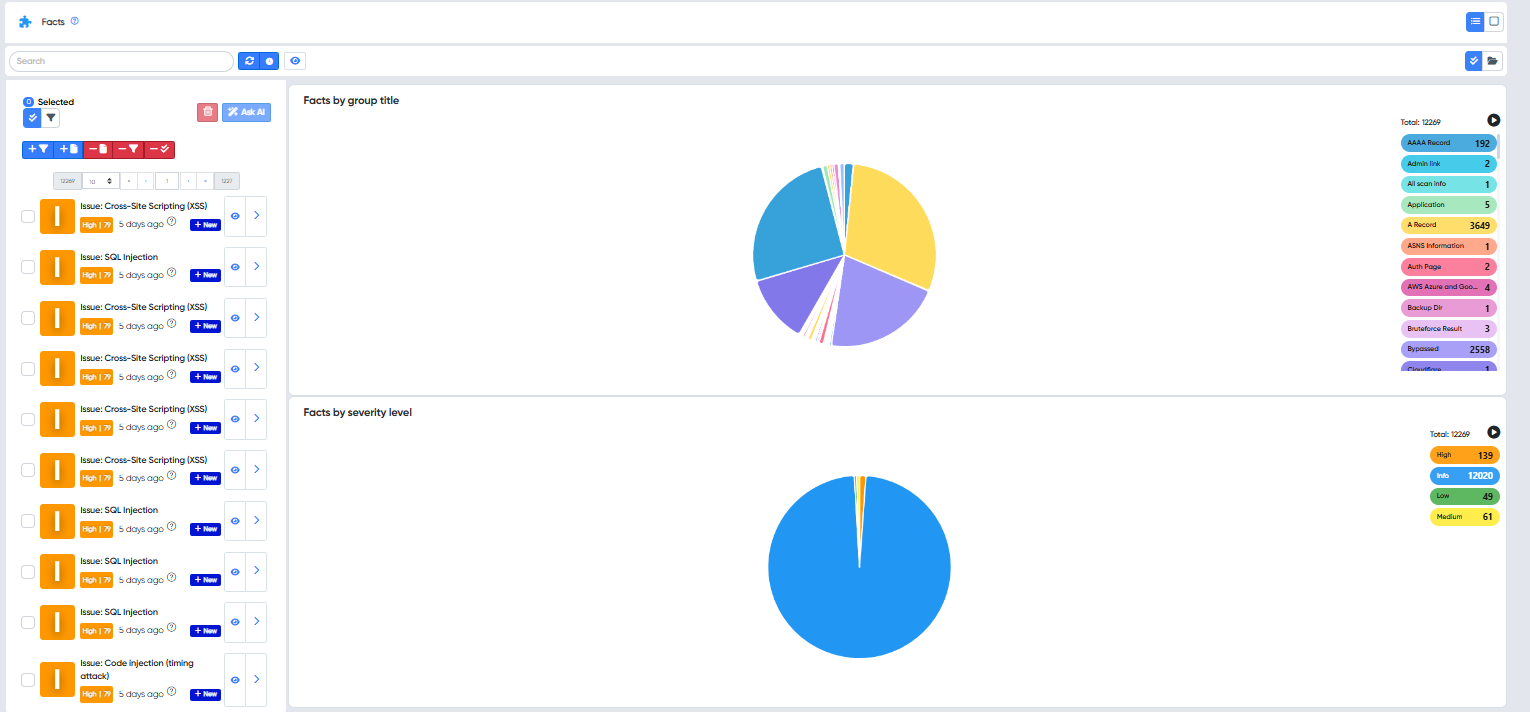
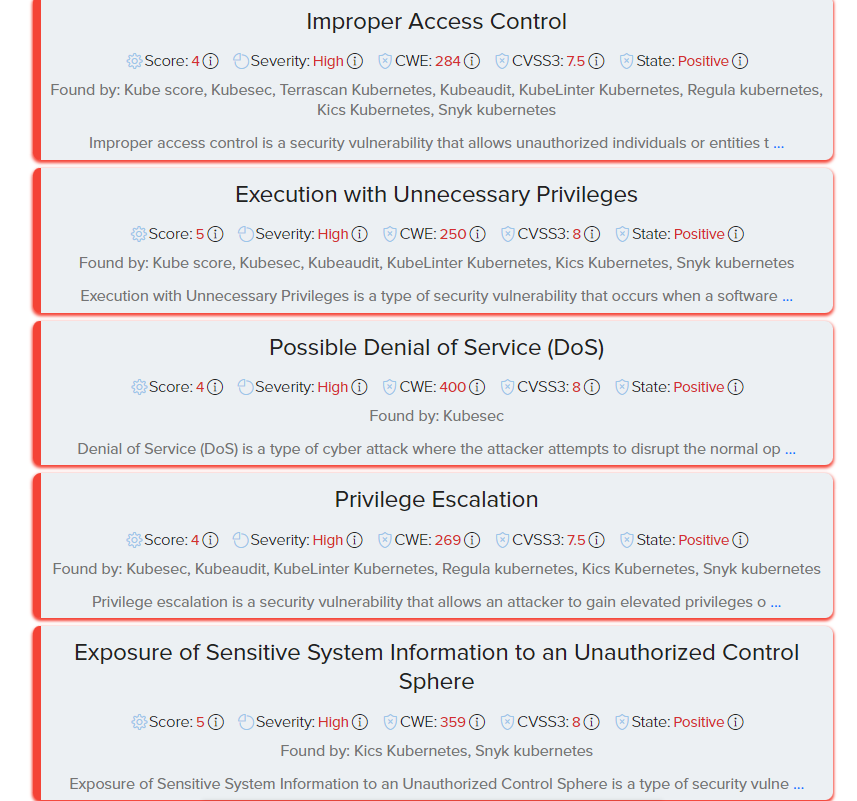
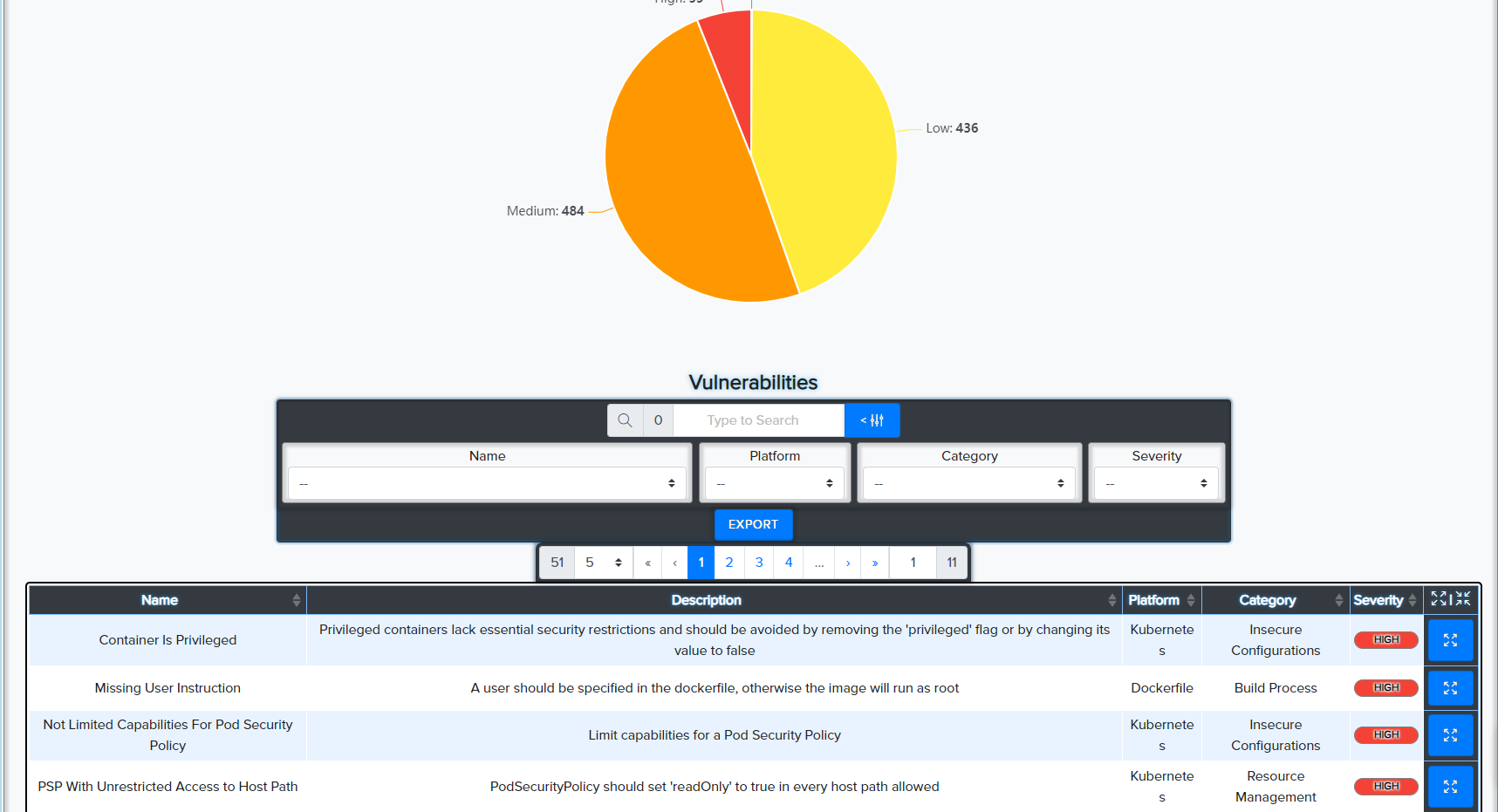
Upload and scan infrastructure files for vulnerabilities and misconfigurations.
Supported types:
- Docker Images & Dockerfiles
- Terraform
- AWS CloudFormation
- Ansible
- Helm
- Kubernetes
- Azure Resource Manager (ARM)
📷 Example:
¶ 📱 Mobile Audits
Scan mobile application files for security flaws.
Supported file types:
- APK (Android)
- IPA (iOS)
📷 Example:
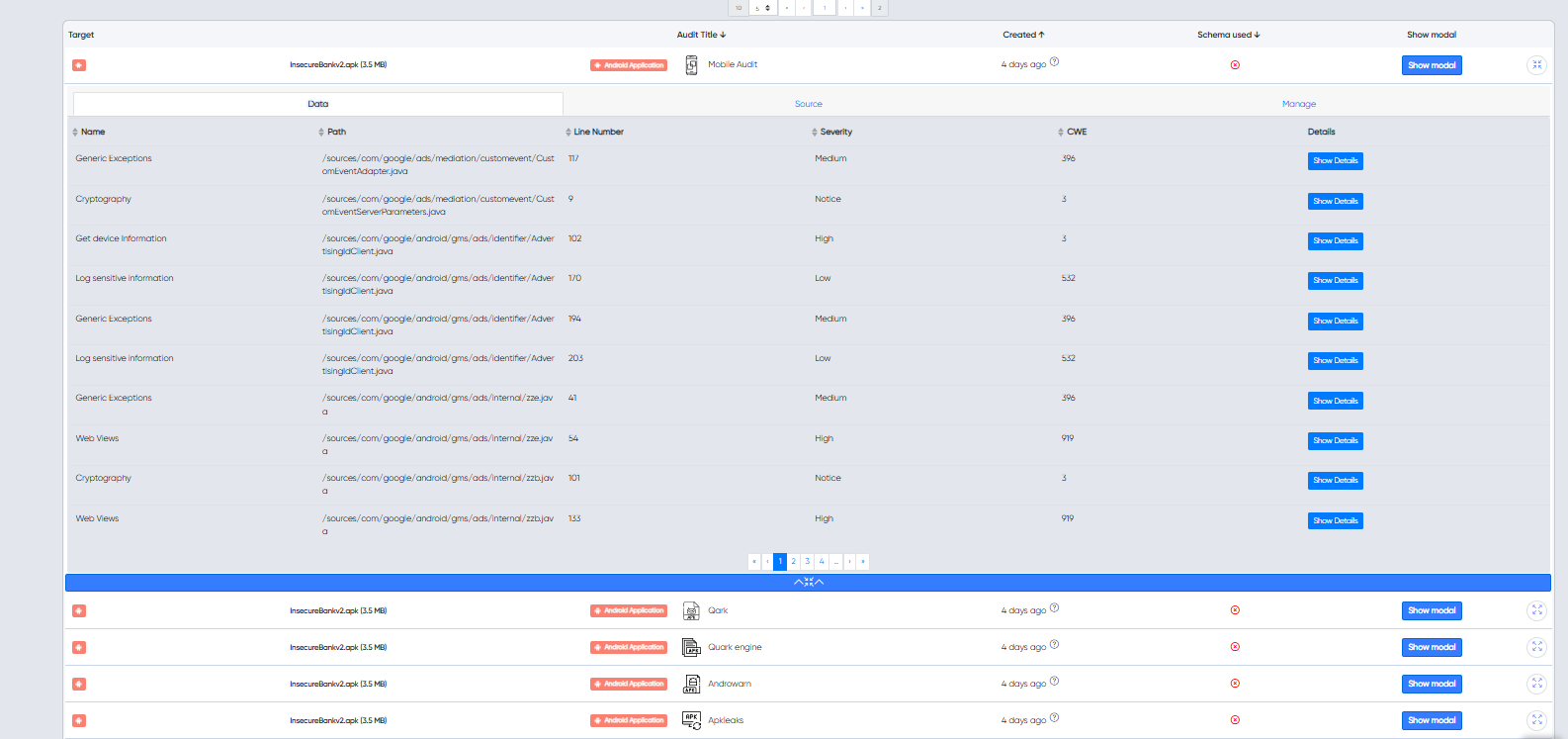
¶ 👨💻 Whitebox Audits
Scan source code or GitHub repositories for code vulnerabilities.
Supported languages:
📷 Example:
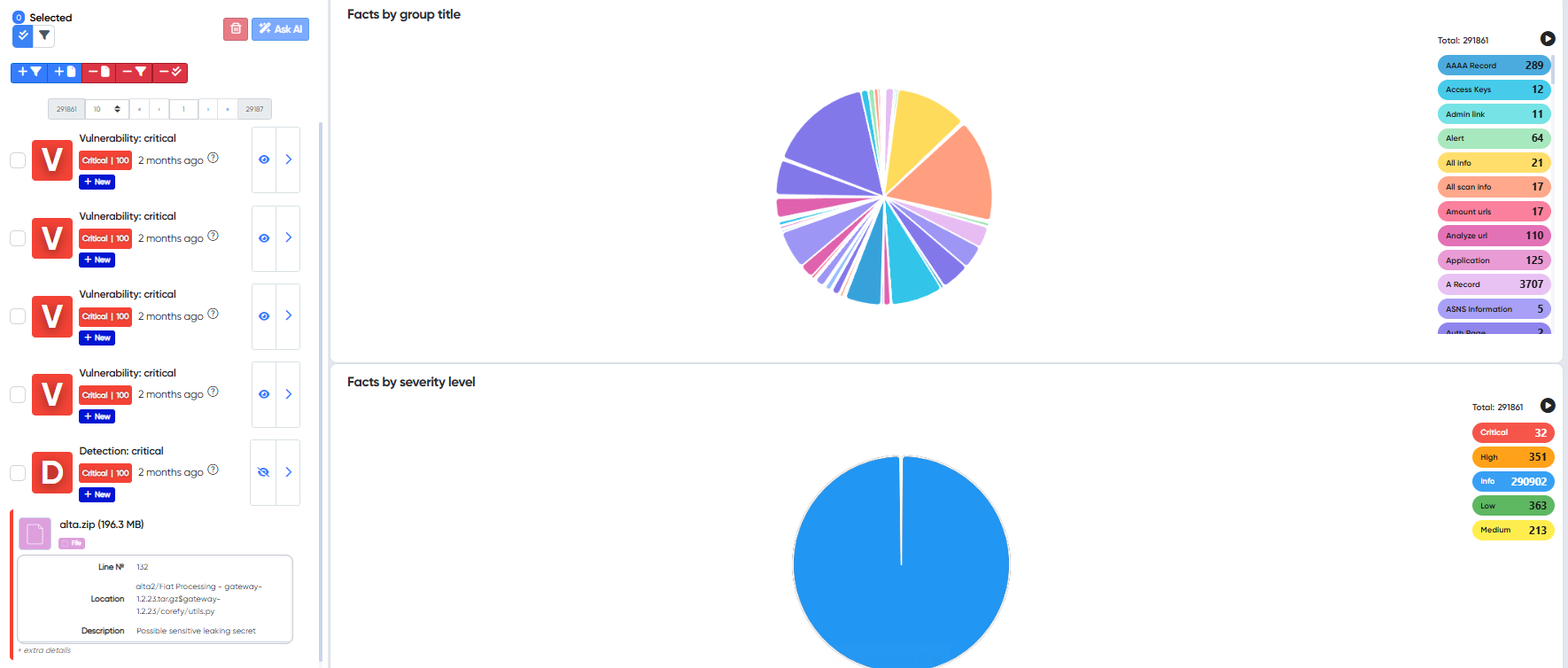
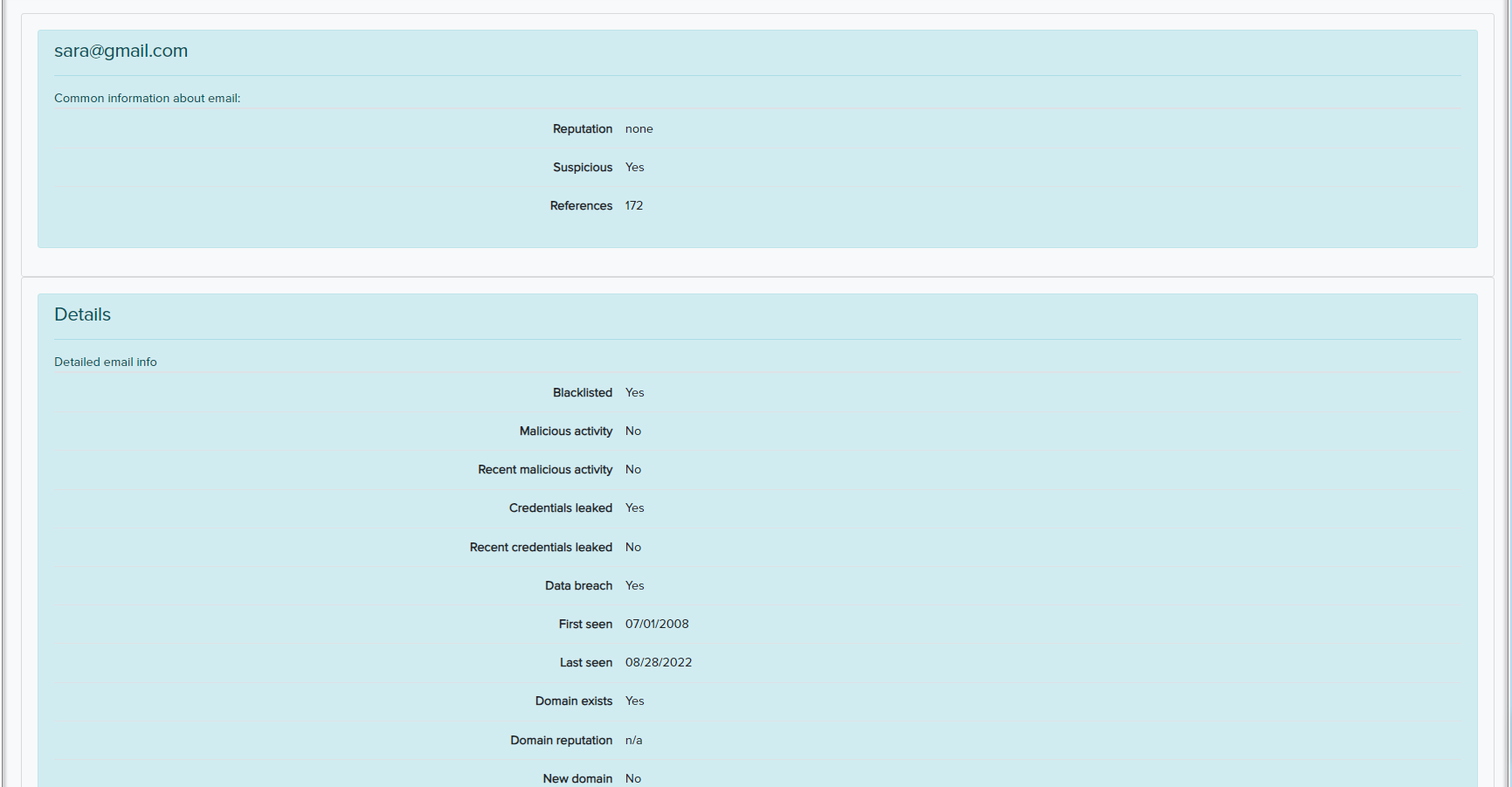
¶ 🌍 Recon Audits
Scan the internet for leaked personal/organizational data:
- Usernames
- Emails
- Phone numbers
- Organization info
- Bank card numbers
📷 Example:
¶ 🧠 Smart Contract Audits
Audits for blockchain-based smart contracts (e.g., Ethereum) to detect vulnerabilities.
¶ 🧩 Audit Modes: Singular & Multi
CryEye splits audit modes into:

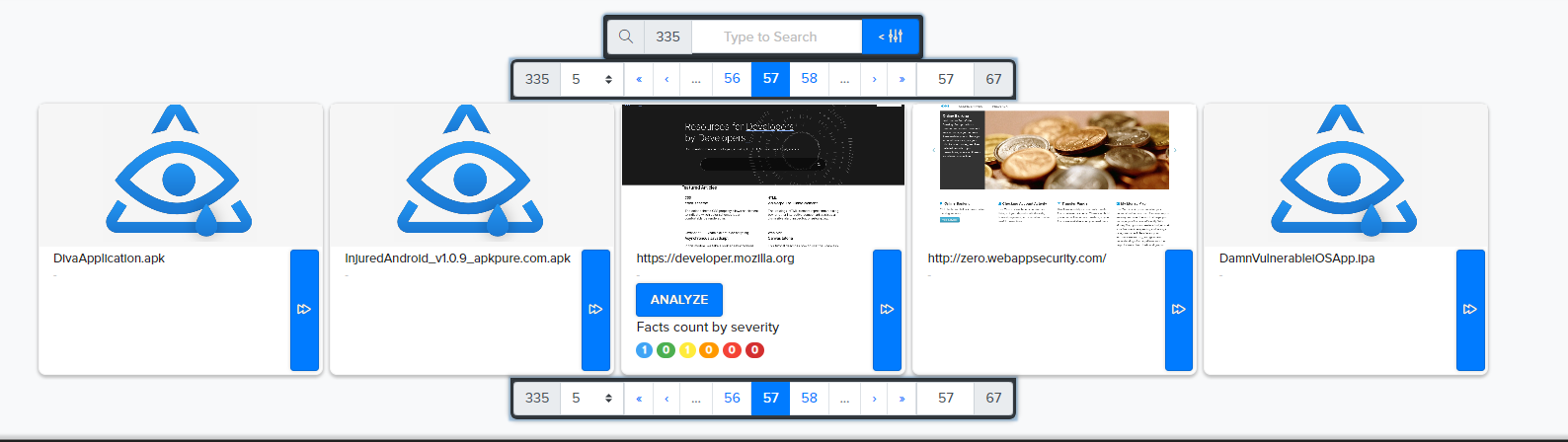
¶ 🔹 Singular Audits
Work with one target per project.
- Each target (URL, IP, APK...) needs a separate project.
- Focused scans with isolated results.
📷 Example:
¶ 🔸 Simple Audits (Multi)
Work with multiple targets in a single project.
- Add URLs, IPs, APKs, source code, usernames, emails, etc.
- CryEye automatically matches audits to supported targets.
📷 Example: