¶ What is Cryeye?

This is Wiki about Cryeye project
¶ video tutorial
¶ All-in-one Cyber security platform
Cryeye is a cloud-based continuous deep audit and security monitoring solution with a variety of integrated tools that provides an all-in-one SaaS cybersecurity platform.
Automate vulnerability detection across servers, websites, mobile applications, source code, and cloud solutions.
¶ Unlimited security options Features
Automate vulnerability detection across servers, websites, mobile applications, source code, and cloud solutions.
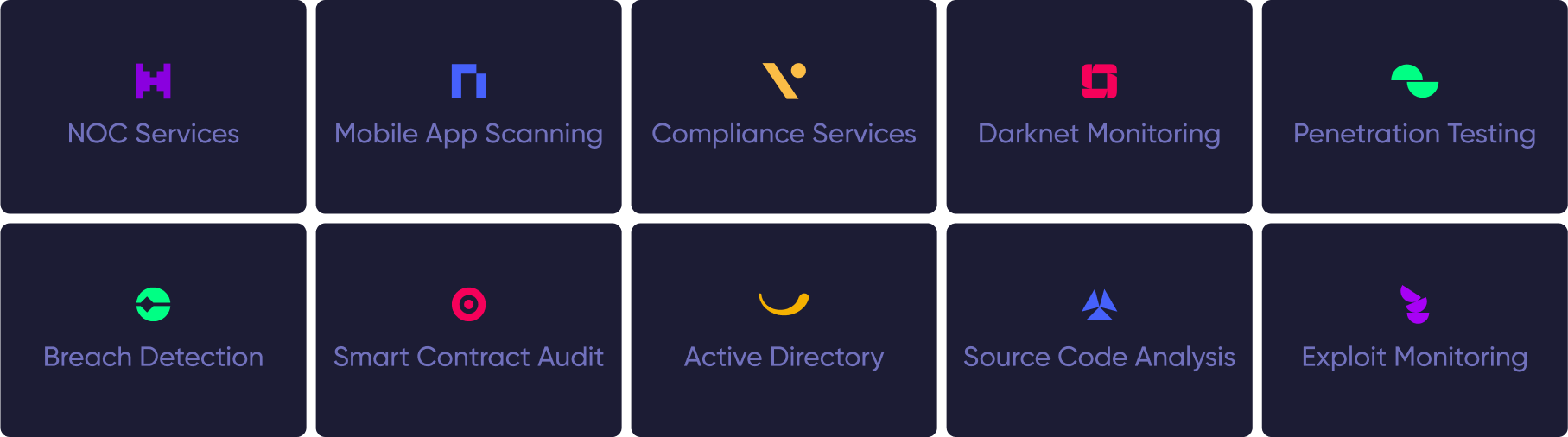
- NOC Services
- Mobile App Scanning
- Compliance Services
- Darknet Monitoring
- Penetration Testing
- Breach Detection
- Smart Contract Audit
- Active Directory
- Source Code Analysis
- Exploit Monitoring
- Infrastructure scanning
¶ Cryeye Interface

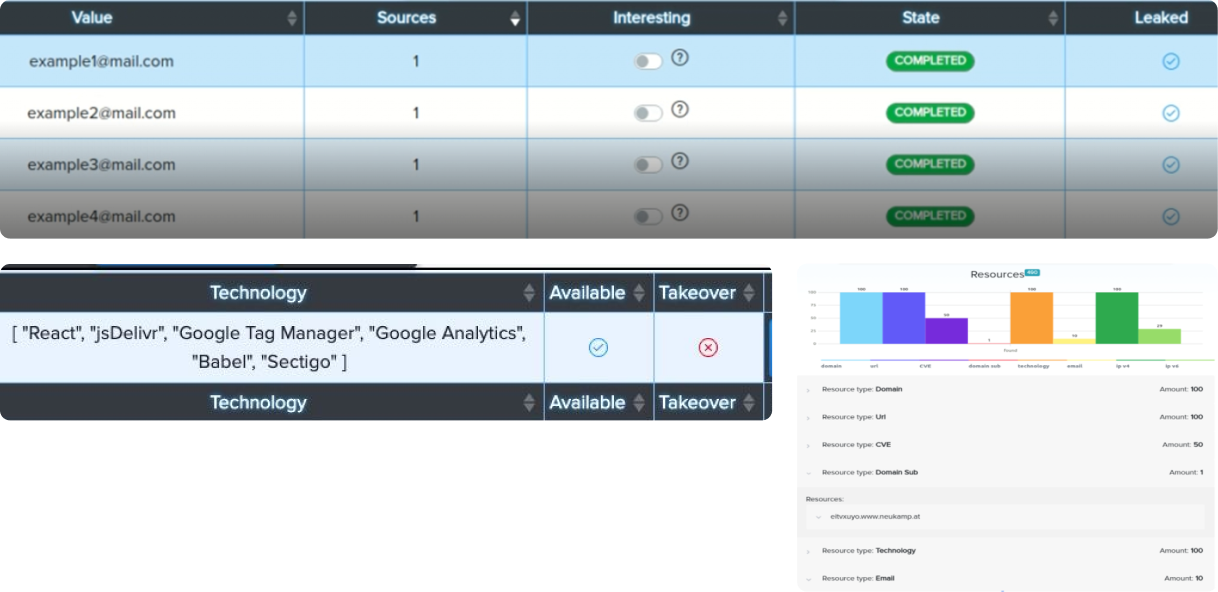
¶ Resource system
Resource extraction systems extract information about the target's web resources from the bulk of the results, they can be used for subsequent attacks.
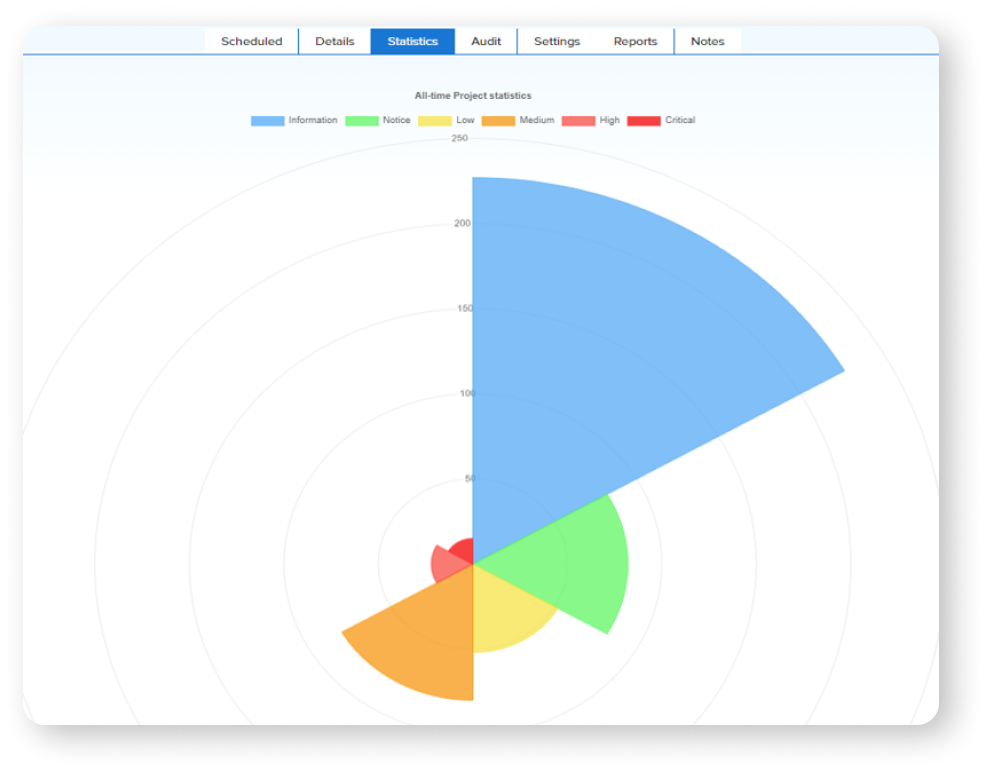
¶ Project statistics visualization
View statistics of found vulnerabilities
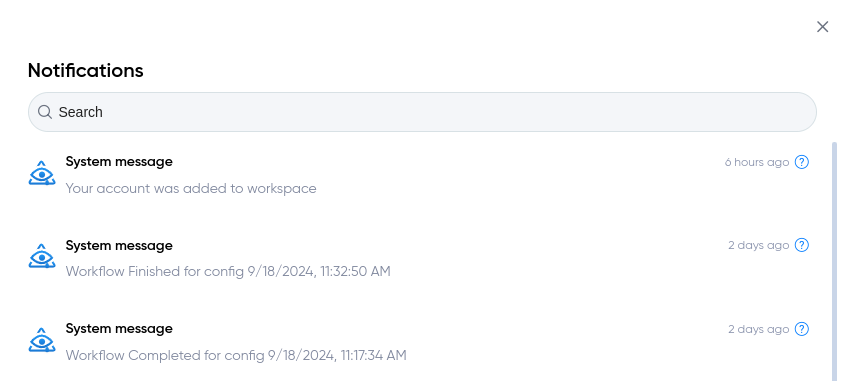
¶ Notification system
Notification system can send notifications on Email and inside Cryeye on your dashboard.
- Get instant notifications about your activity.
- Set up the notification system as you like.
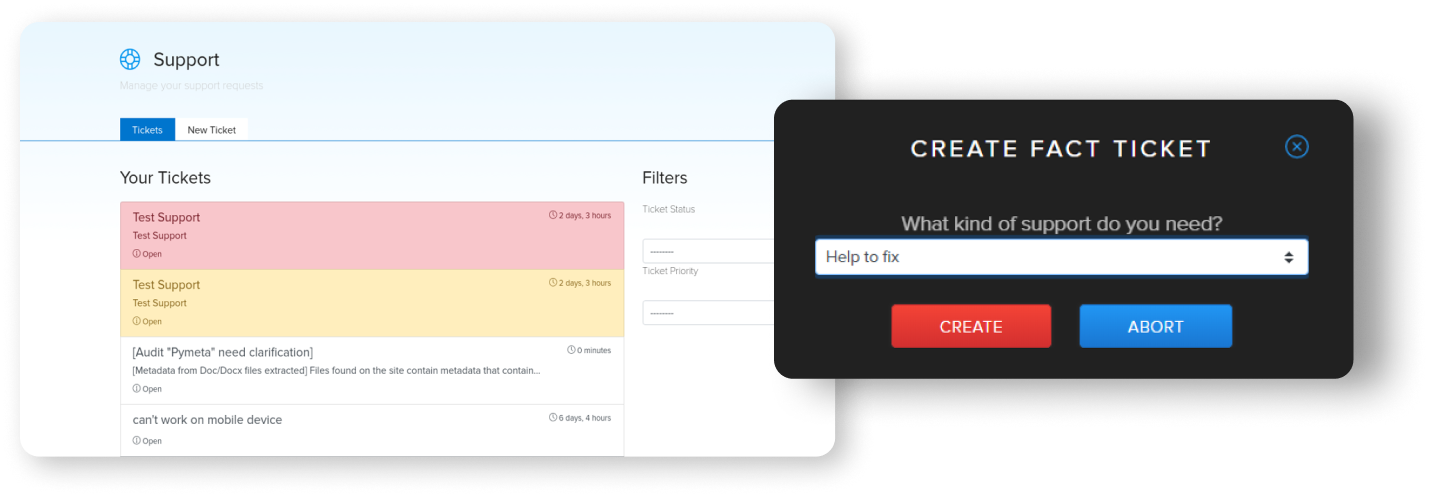
¶ Support
There users can request Support from cryeye developers by creating "Support tickets". Support tickets can be created from findings such as vulnerabilities facts finded by audits service or by whitebox service.
- Track the status of your technical support request in real-time.
- Request support in one click.
- Our technical support team will contact.
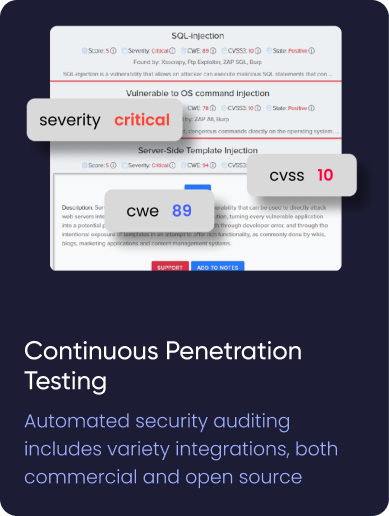
¶ Manual Pentesting Tools (MPT)
A complete cloud-based solution for manual testing.
Check the vulnerabilities found or perform other actions necessary for a full cycle of vulnerability assessments or penetration testing cycle.
Tools like Metasploit, Nmap, commix, SQL map, zap and others can be run from our cloud. You can add your own MTP.

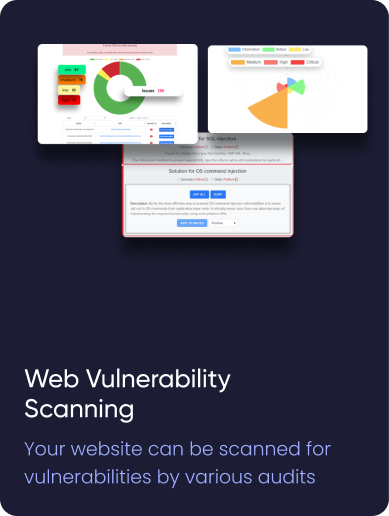
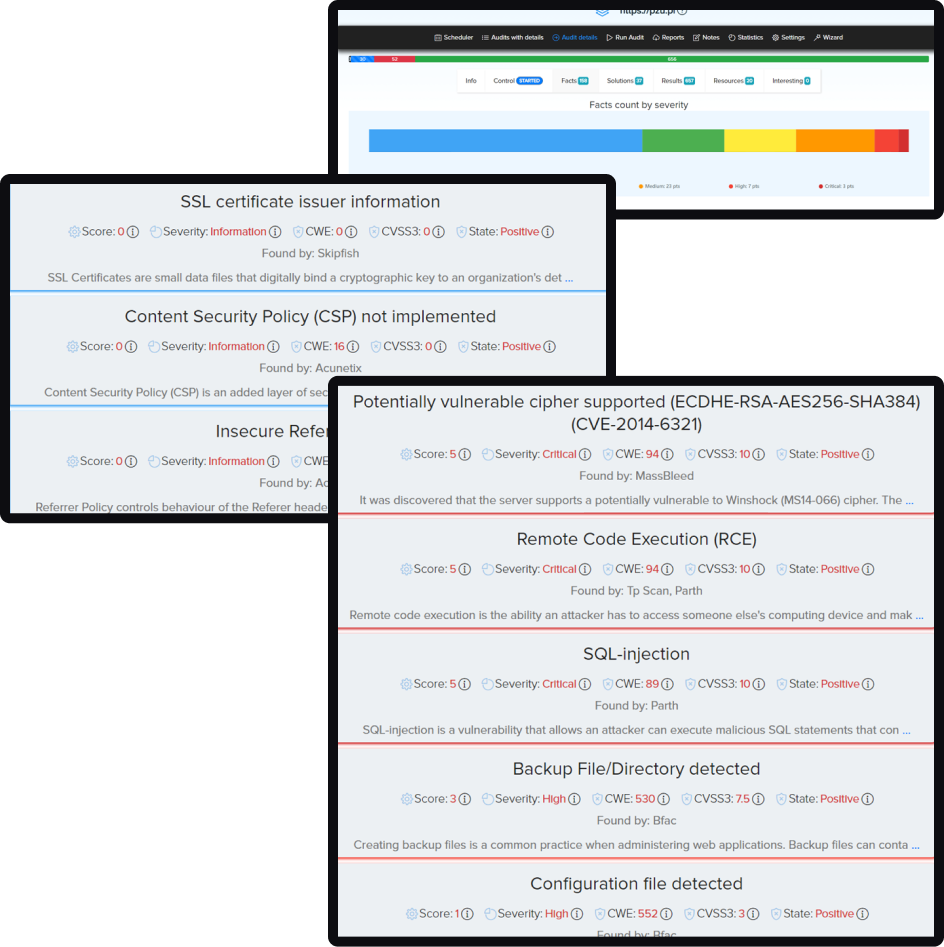
¶ Security audits
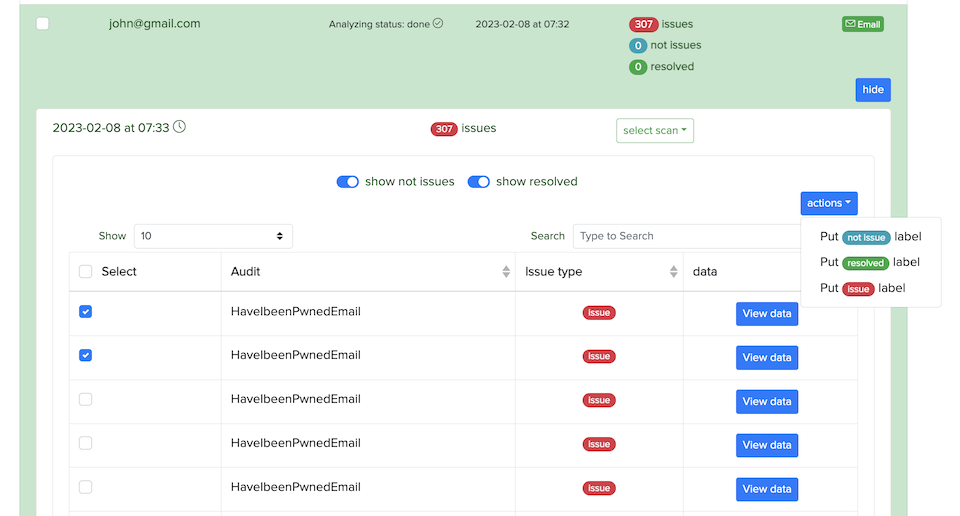
In Cryeye, we have many integrated open source and licensed security software that we call audits. In the audit system, our users can manually run audit checks on their Assets. Show possible vulnerabilities in your web application by sorting them from critical to informational. Audits allow you to select each attack vector and type of scan, showing a description of the vulnerability, its severity, CVSS assessment and remedies. Also, you can sort the results by many different parameters.
Integrated commercial Blackbox tools:

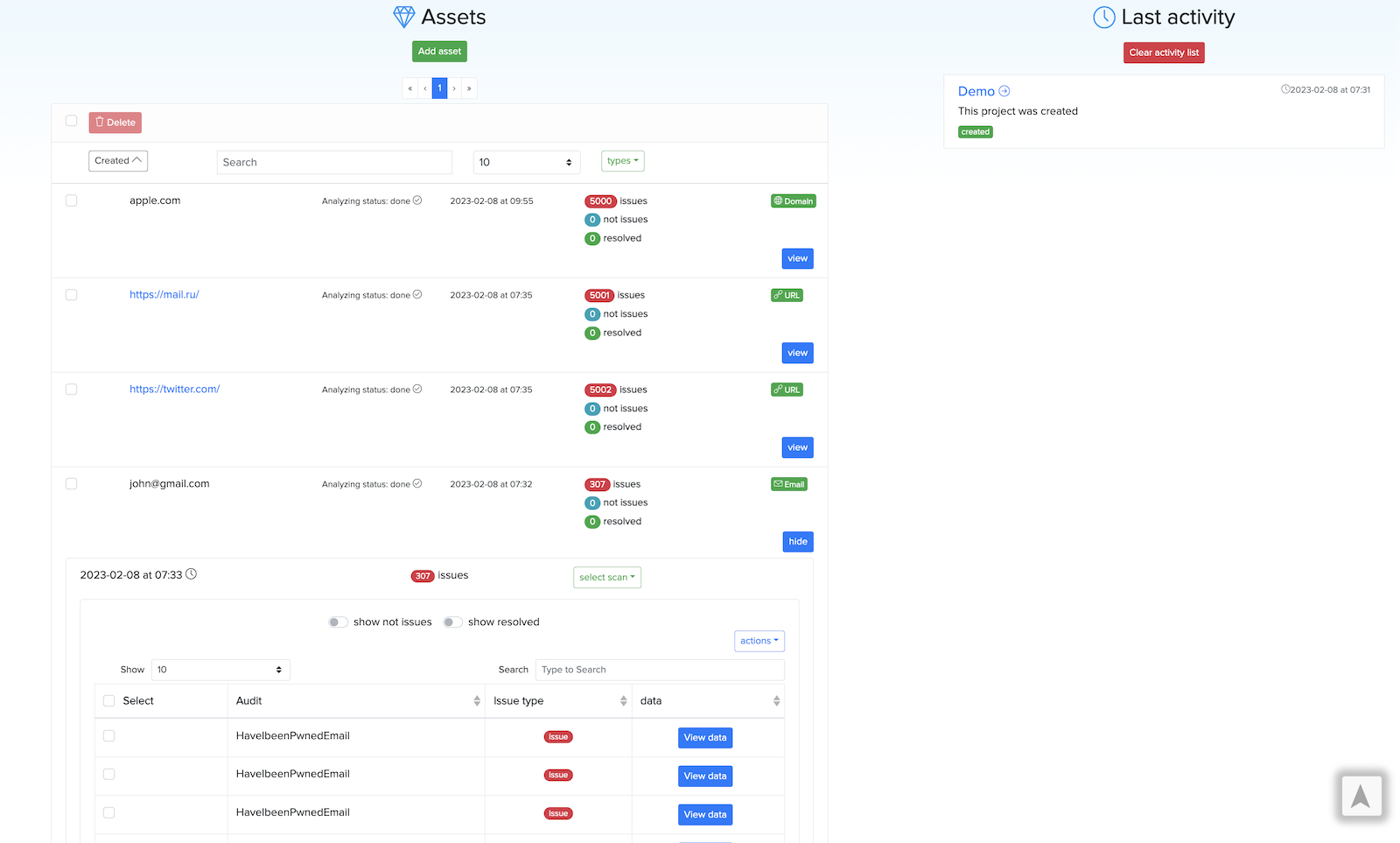
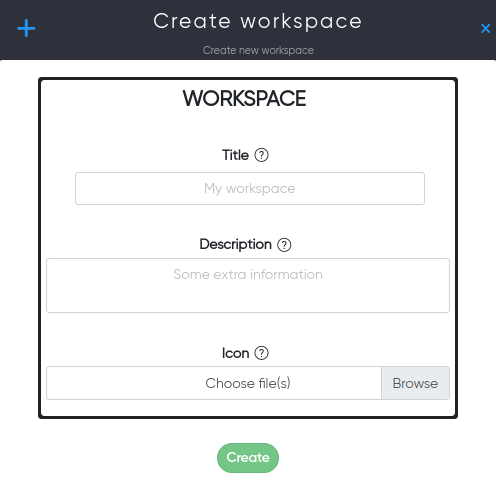
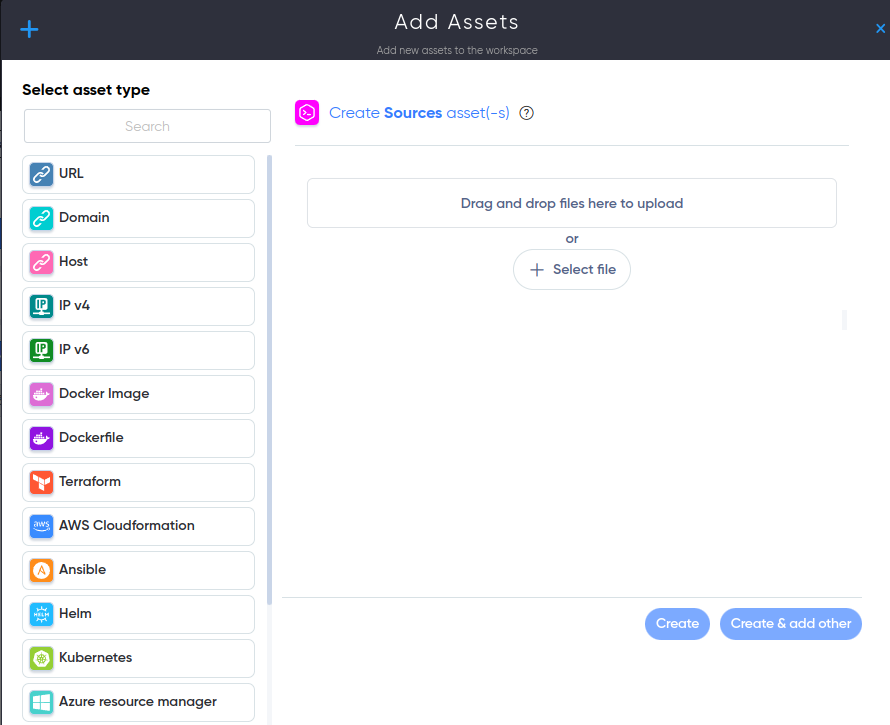
¶ Assets and Workspace
In Workspaces users work with Cryeye project. Inside workspace you can add Assets to use Cryeye services.
For example:
- Site addresses.
- E-mail addresses of employees.
- Configuration files for infrastructure.
- Mobile application files.
- etc;
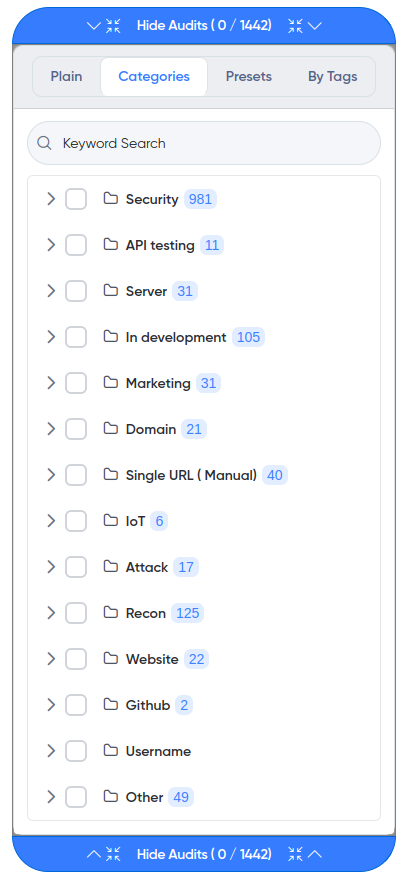
¶ Example of an Audit list
Constant updating of audits.
- More than 1500 audits.
An example of audits for URLs:
¶ Massive assets scanning
Multi targets audit system allows you to add an unlimited number of assets and run automatic scanning on them in one click. You can add several IPs, domains, source code archives, mobile applications at once.
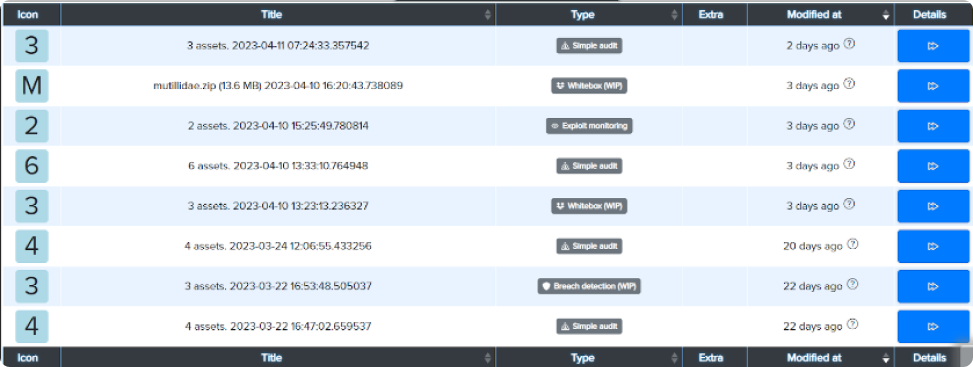
An example of adding several archives with source code at once:
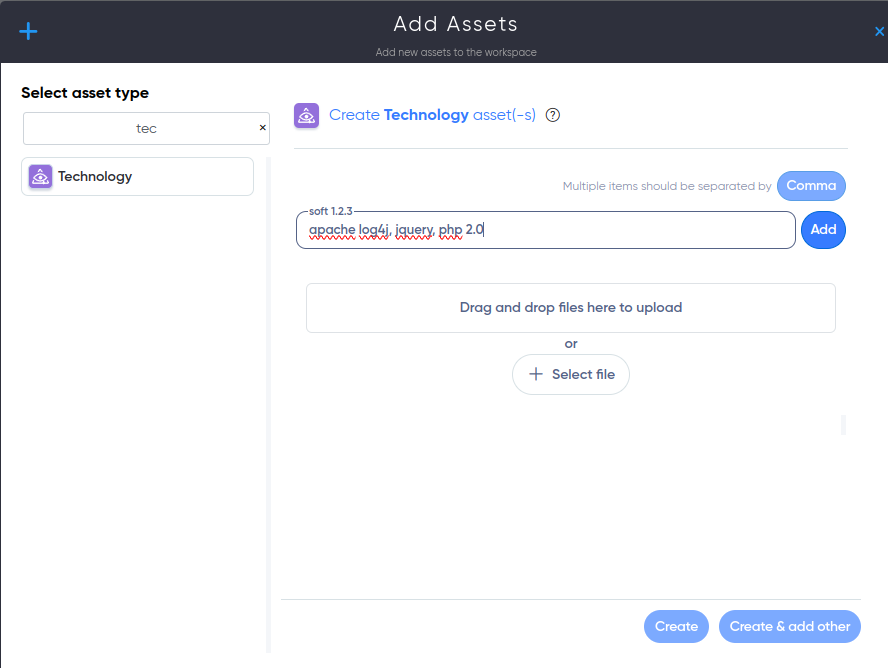
Example of adding a list of technologies for Exploit Monitoring:
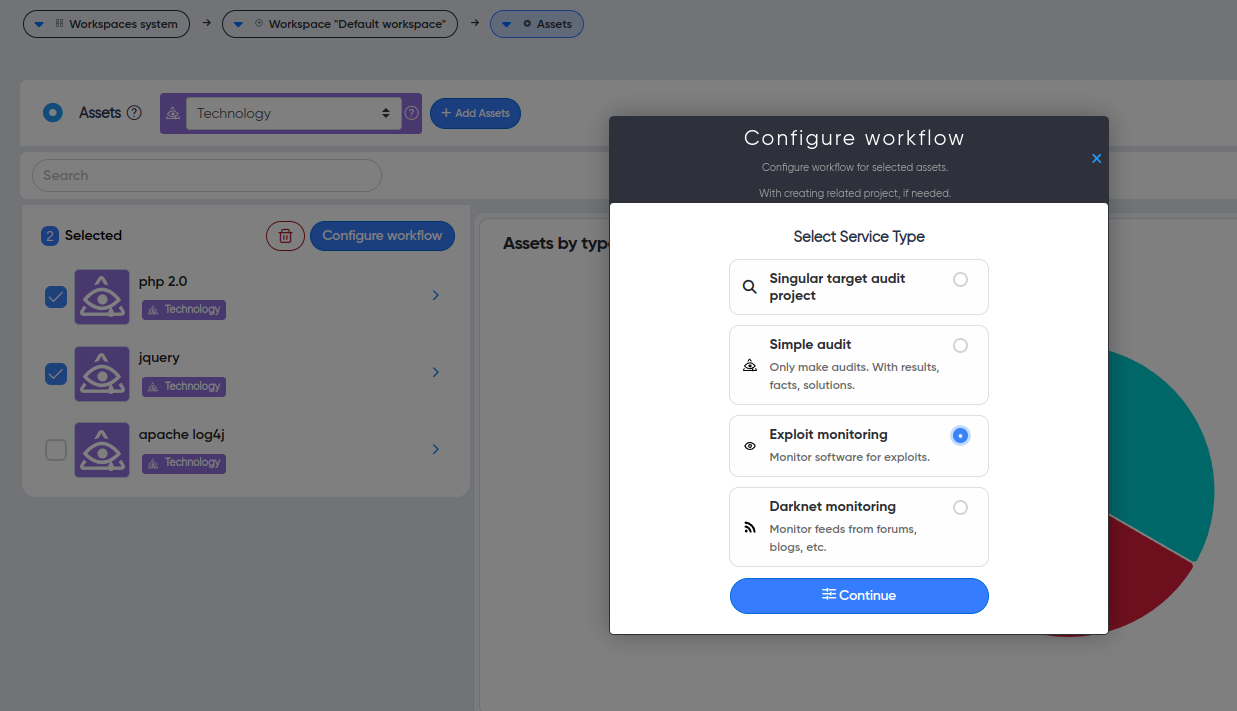
To add technologies for Exploit Monitoring, select the required assets, click 'Configure Workflow,' and a modal window will appear. From there, choose the service 'Exploit Monitoring' and click 'Continue.'
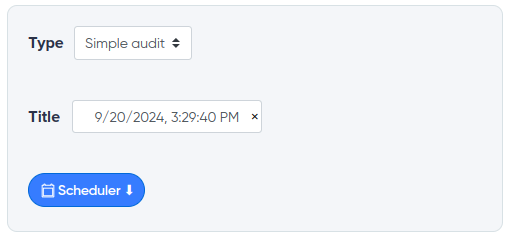
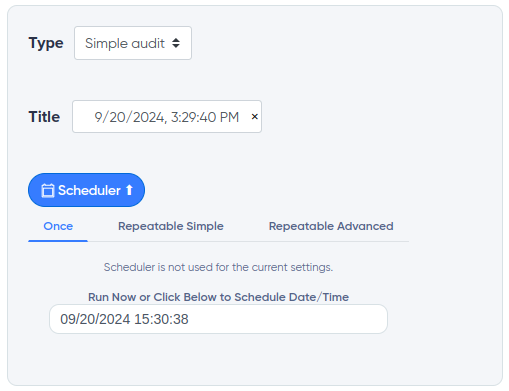
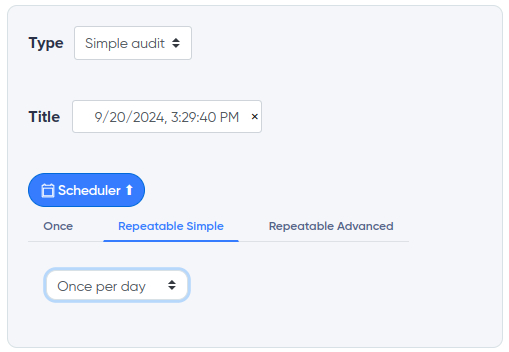
¶ Planner
Allows you to configure the automatic launch of the necessary audits in the desired period of time or schedule automatic scanning. For example, the scheduler will allow you to control the automatic search for new exploits and CVEs for your technology.
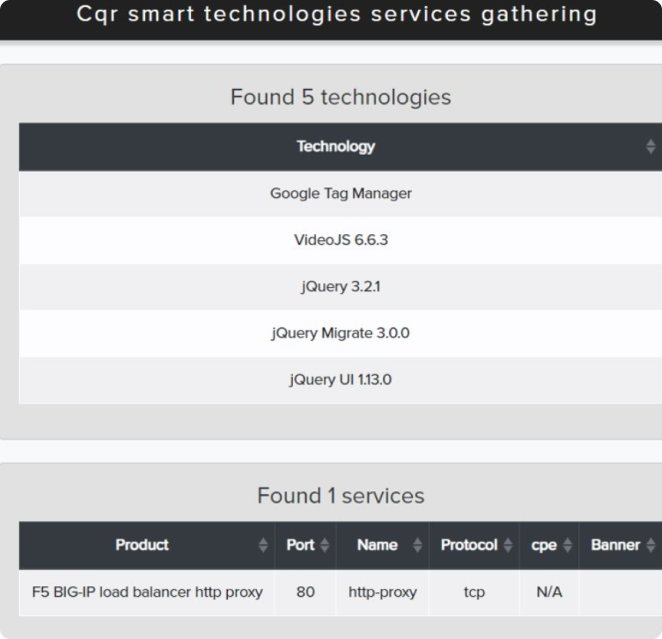
¶ Detection technology with Cryeye
Technology detected on the project and added F5 Firewall (BIG IP) for assets, and exploit monitoring and Darknet/CVE monitoring started.
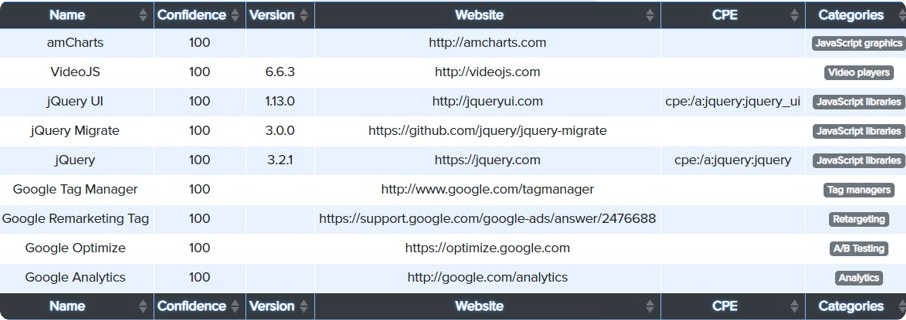
Discovered technology
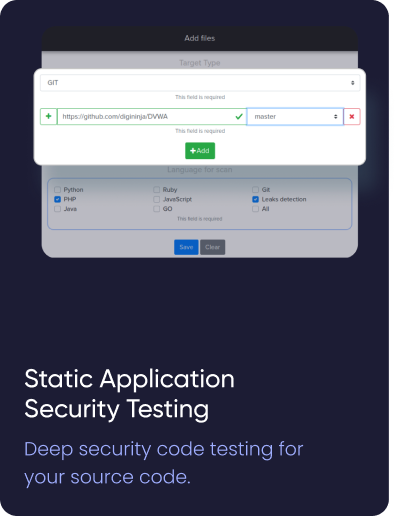
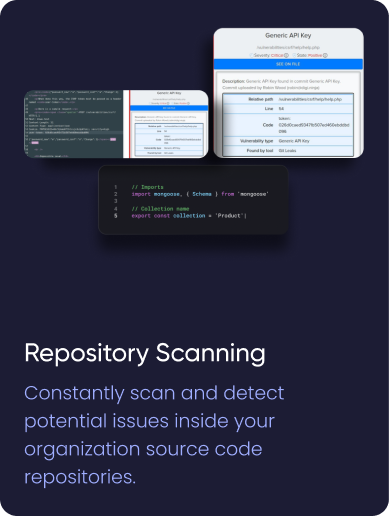
¶ Whitebox/Source code review
Source Code Analysis will help you monitor the security of your products at all stages of software development.
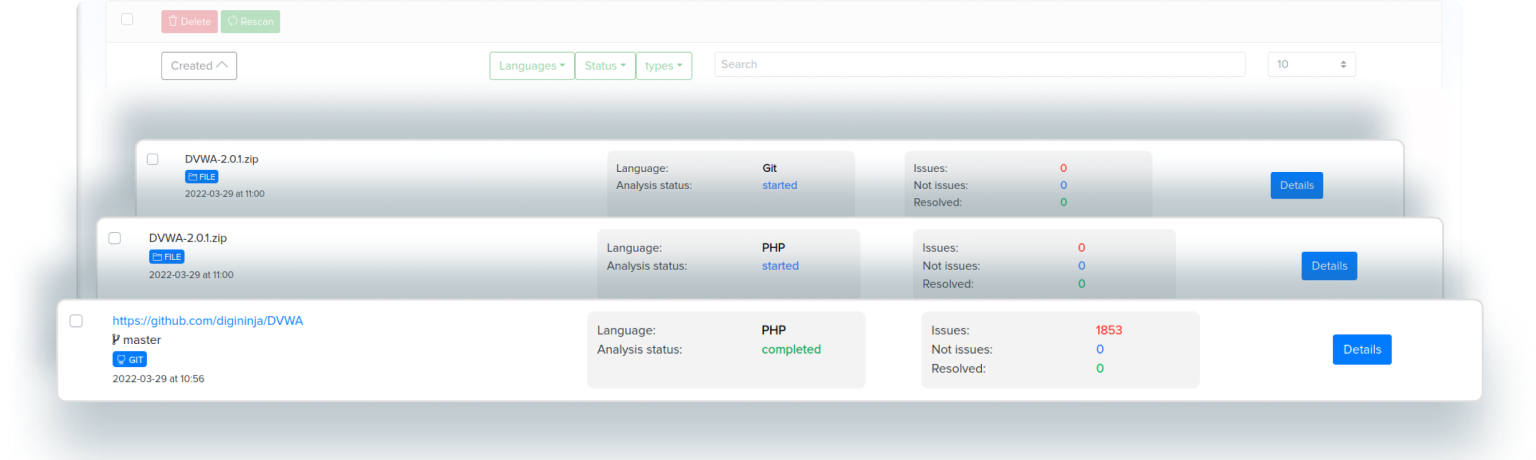
Our scanner can scan zip files and git repositories from Github.com
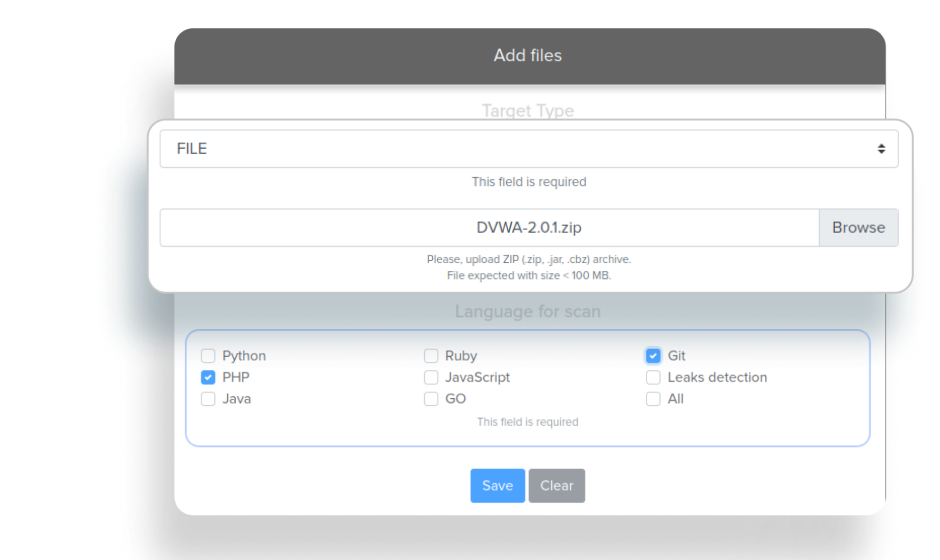
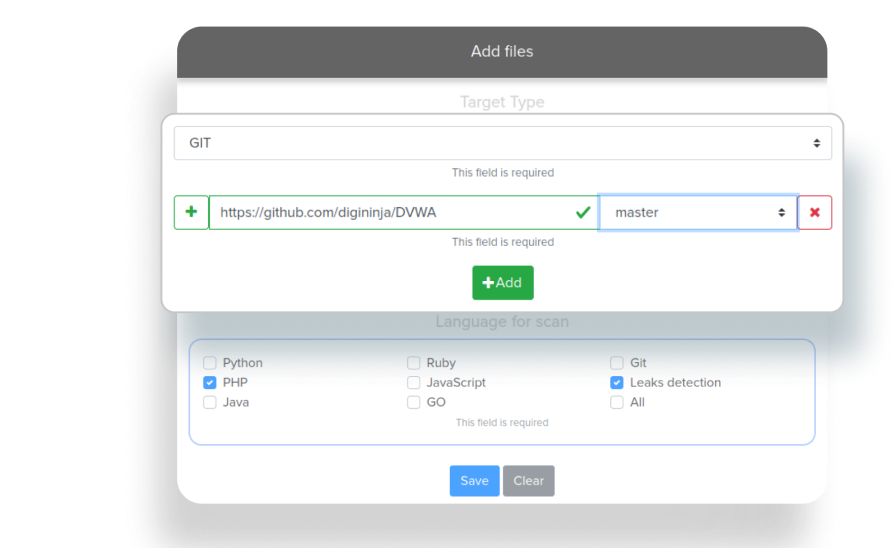
Our team tried to find the source code but didn't find it in github/gitlab/bitbucket.
However, we have uploaded vulnerable code so that you can verify it.
Please remember to sort by severity.
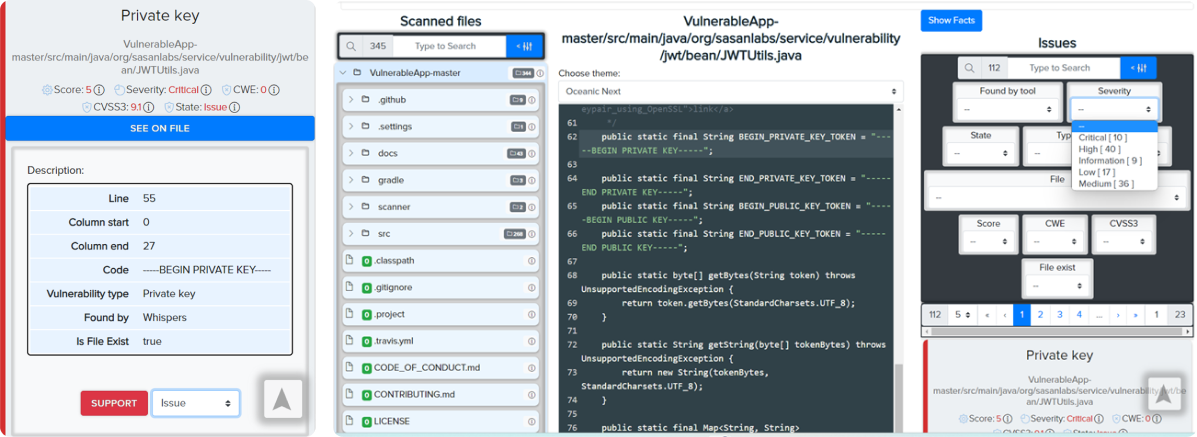
You can easily download your source code and get real-time scan results.

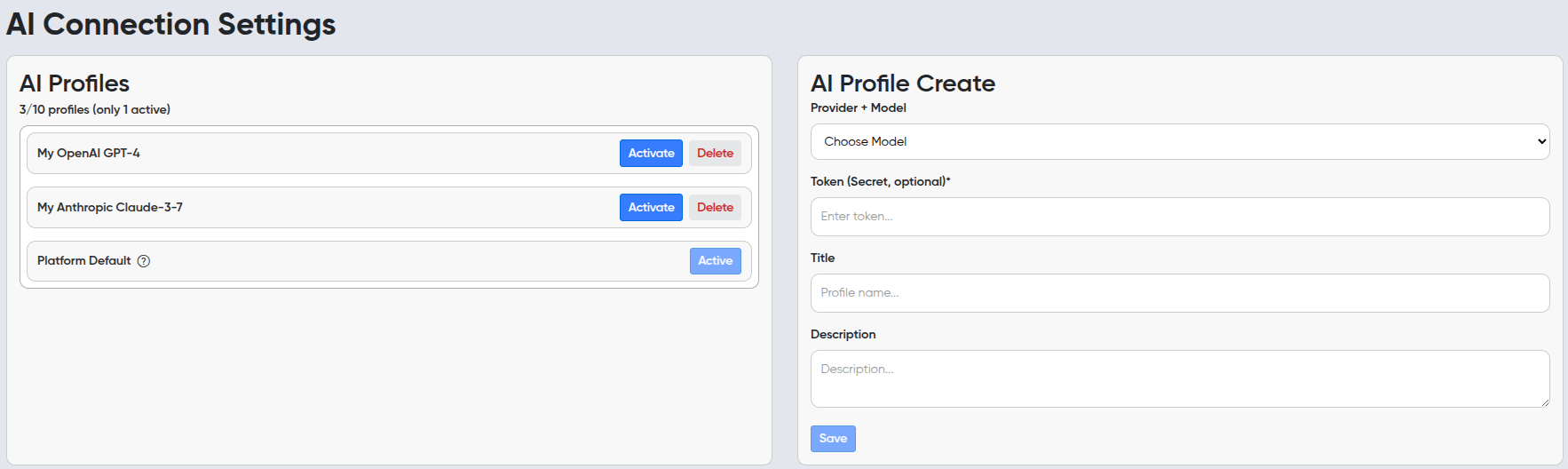
¶ AI Profiles
AI Profiles allow you to add multiple profiles with different AI models and providers, giving you the flexibility to choose which one to use for each task.
You can also use our default model — specifically fine-tuned for our platform, completely free!
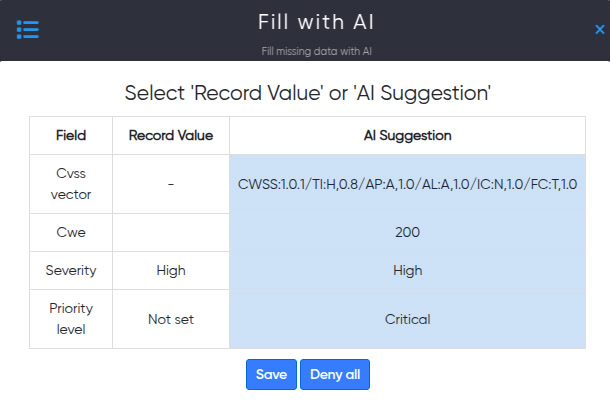
¶ Fill With AI
Fill With AI is a feature for working with Registry Records that enables users to quickly add or update existing data with the assistance of AI.
The feature provides an intuitive way to compare and selectively apply AI-suggested improvements.
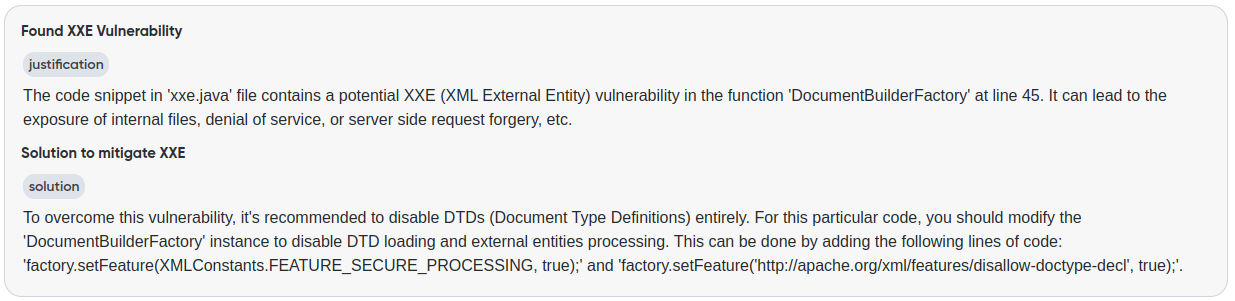
¶ Ask AI
Ask AI is a powerful feature that provides users with additional, AI-generated insights on audit findings. It offers key information such as explanations, suggested solutions, and validation of data accuracy, helping users quickly understand issues and take action to resolve them.
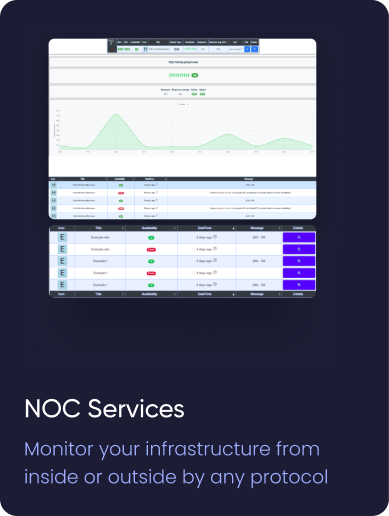
¶ NOC Services
NOC Services
We regularly check the condition of the assets. Let's call it a heartbeat.
With uptime monitoring, you can monitor assets availability.
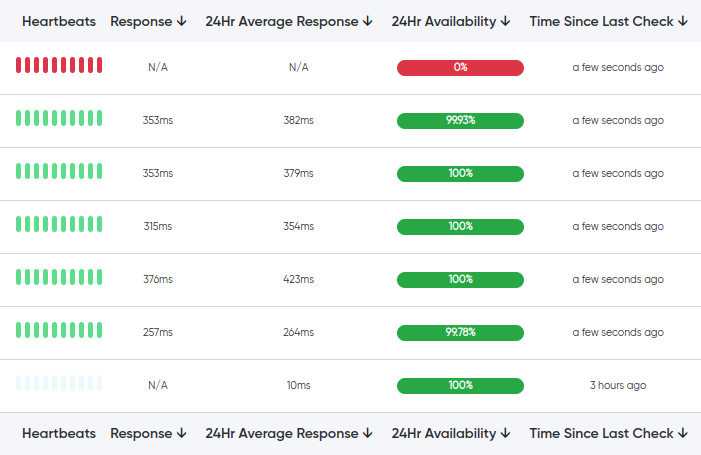
Uptime monitoring allows you to continuously monitor the availability of your assets.

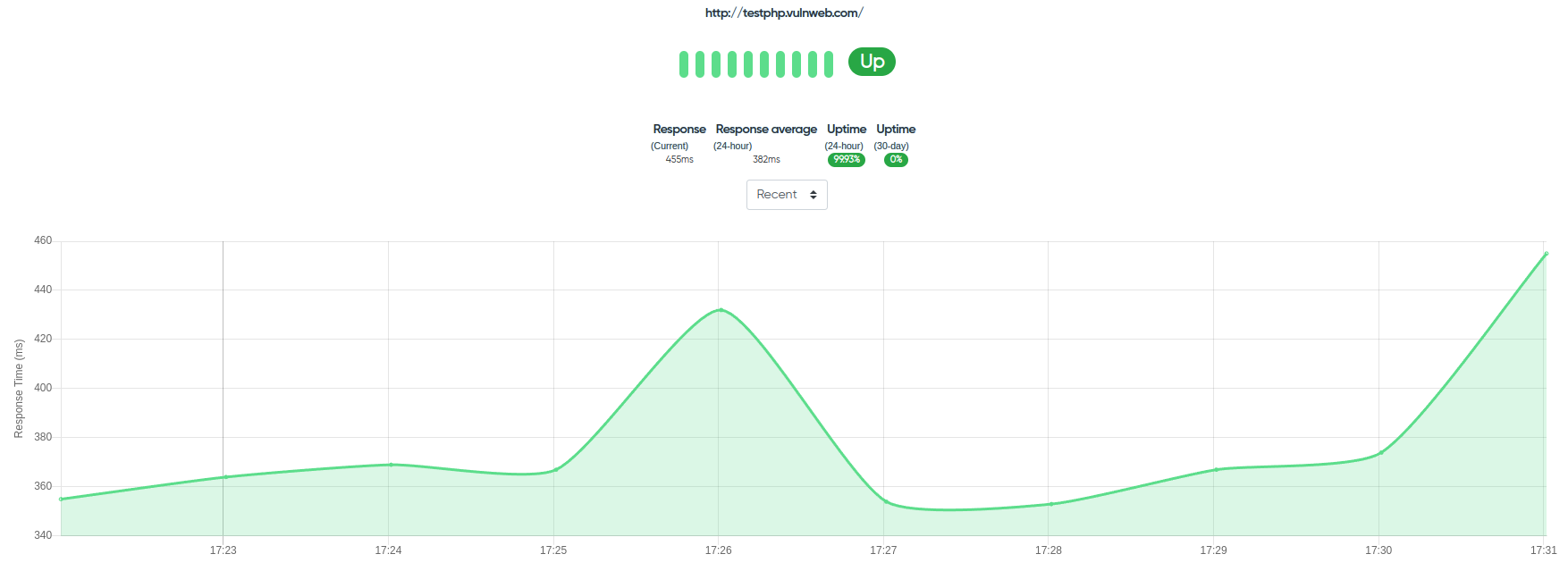
¶ Exploit Monitoring
Exploit Monitoring is a system designed to collect technologies and services on the site and search for their vulnerabilities. This tool allows you to carry out this process at an automated level. Its relevance is confirmed by the lack of the availability of this kind of instrument in the world. Of course, there are wonderful databases with vulnerabilities globally, but they are suitable only for manual use because they don’t know how to filter search results.
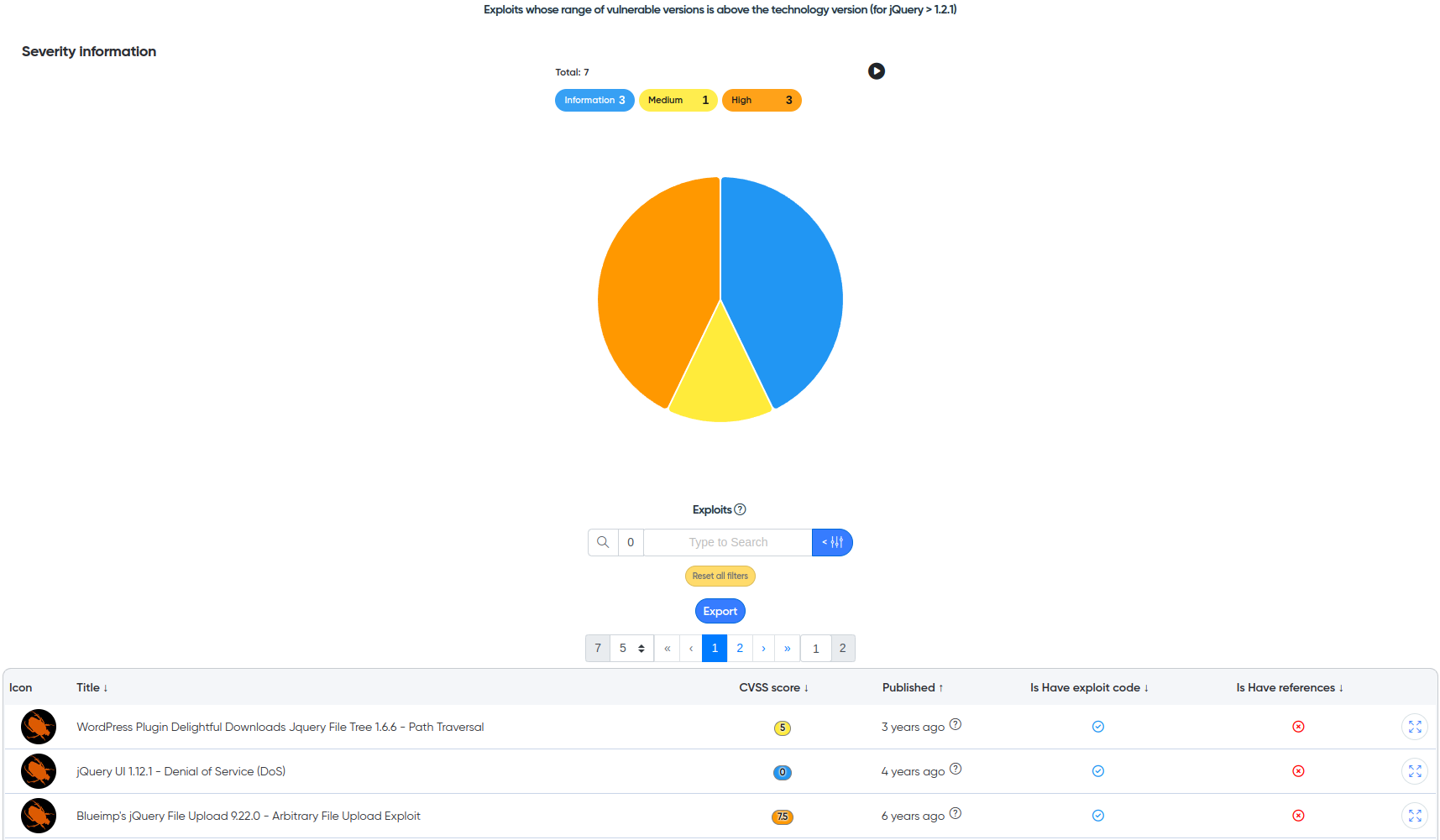
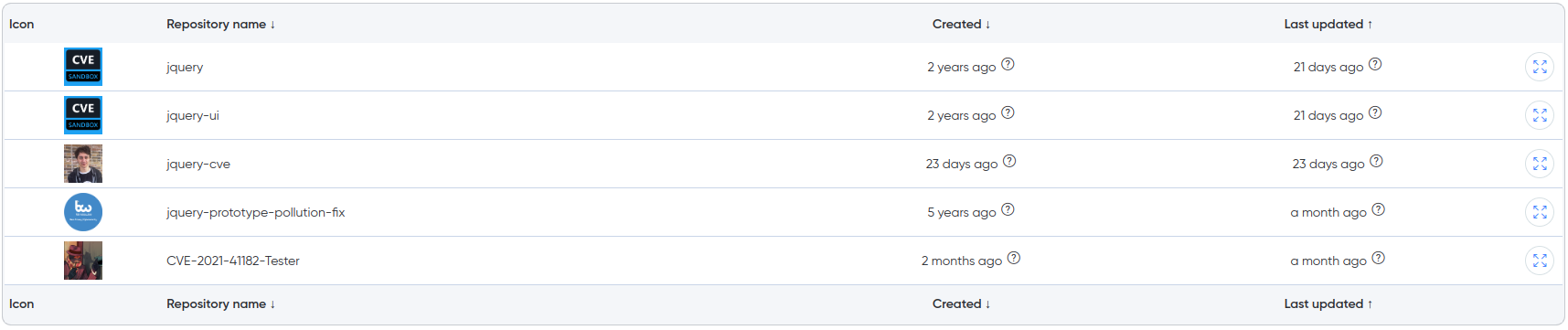
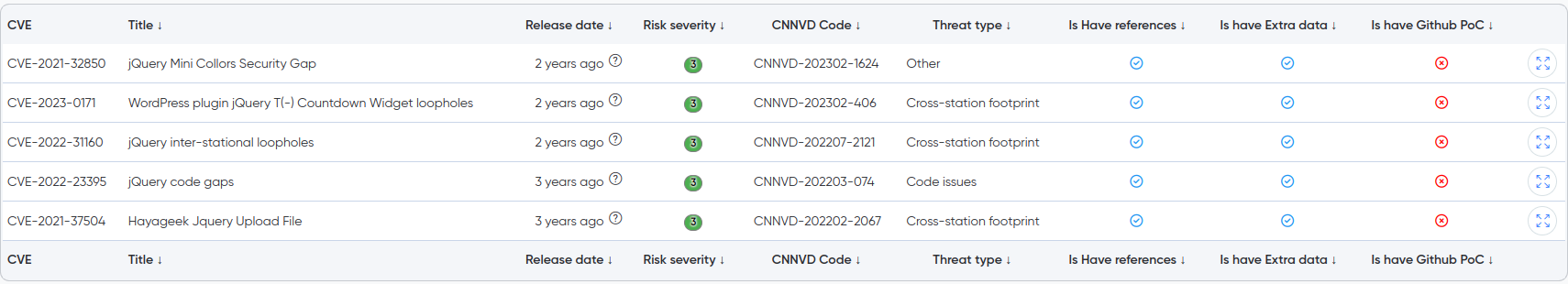
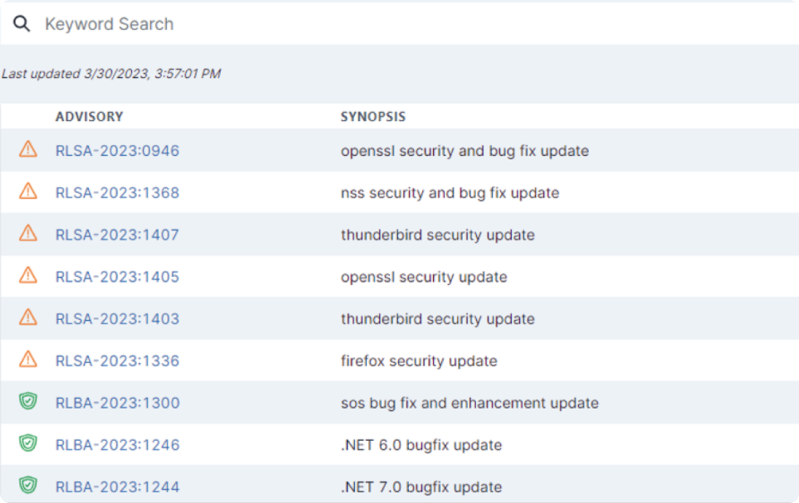
¶ Integration with Redhat Feeds
Redhat database integrated into Darknet monitoring
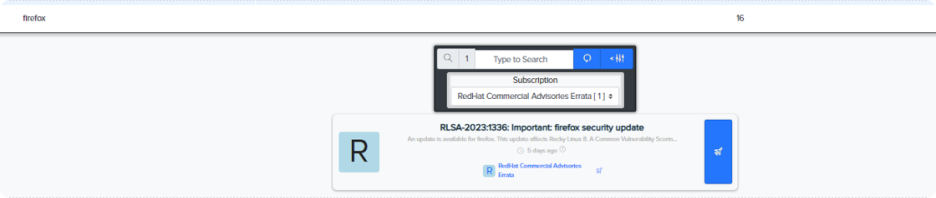
Example of Redhat Feed integration
¶ Mobile app scanning
Scans mobile applications for Android and iOS mobile operating systems for vulnerabilities.
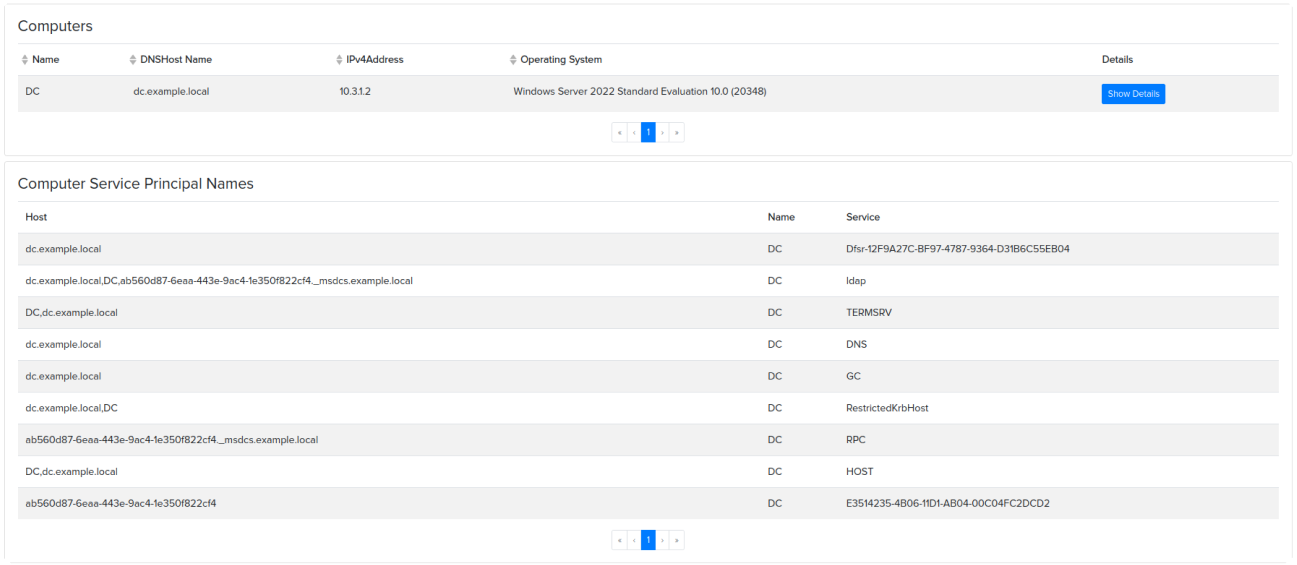
¶ Active directory services
Automatic Active Directory audits will help verify the security of your environment and identify potential vulnerabilities in your infrastructure.
¶ Infrastructure security
Infrastructure code security scanning , also known as Infrastructure as Code (IaC) security scanning, is the process of evaluating the security of the code used to define and configure an organization's infrastructure. Infrastructure code refers to the scripts, templates, or configuration files that are used to automate the deployment and management of infrastructure resources such as servers, networks, and storage.
.png)
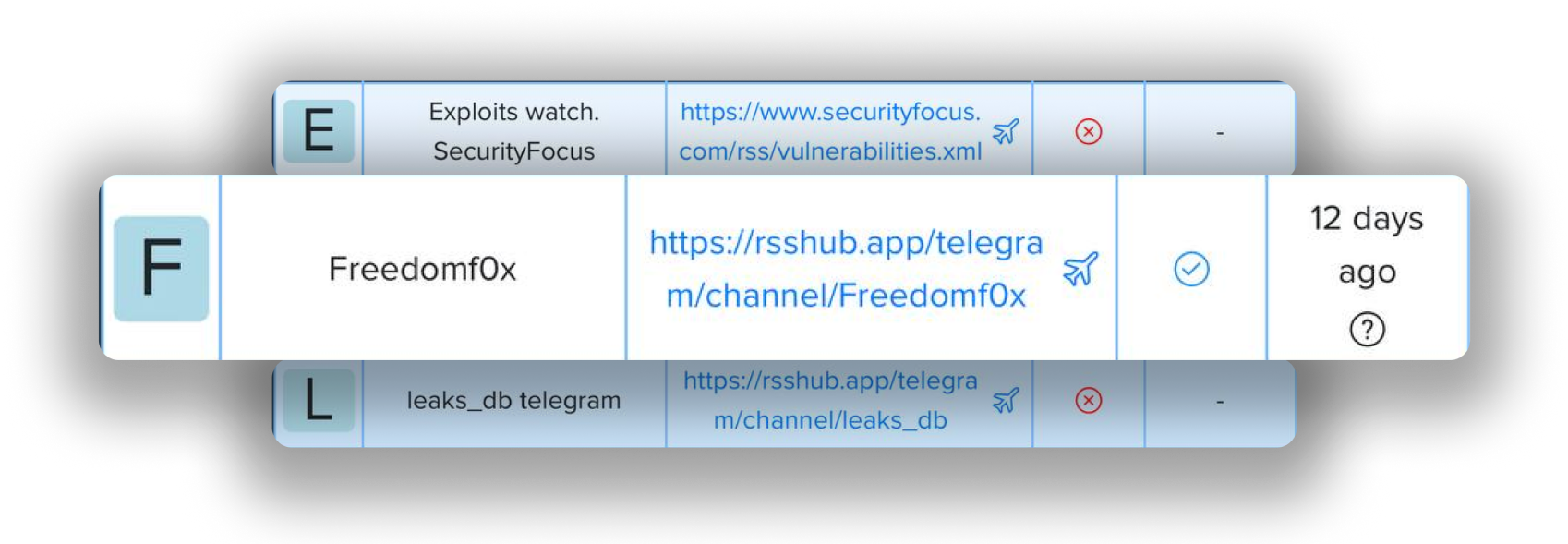
¶ Darknet monitoring
Darknet Monitoring This tool helps in collecting data from different text-based channels and reacting to it. If your data is seen on the darknet, you will be the first to know about it.
¶ Breach detection
The main purpose of Breach Detection is to automate the remote breach detection process and alert the user to the potential risk to the asset.
To achieve the purpose, the user is given the opportunity to safely add their assets to the regular monitoring system. For the convenience of using the monitoring system, the user has the ability to configure the frequency of breach detection. If the user deems that monitoring the asset that he has added is no longer practical (useful), the user has the option to delete the corresponding asset.
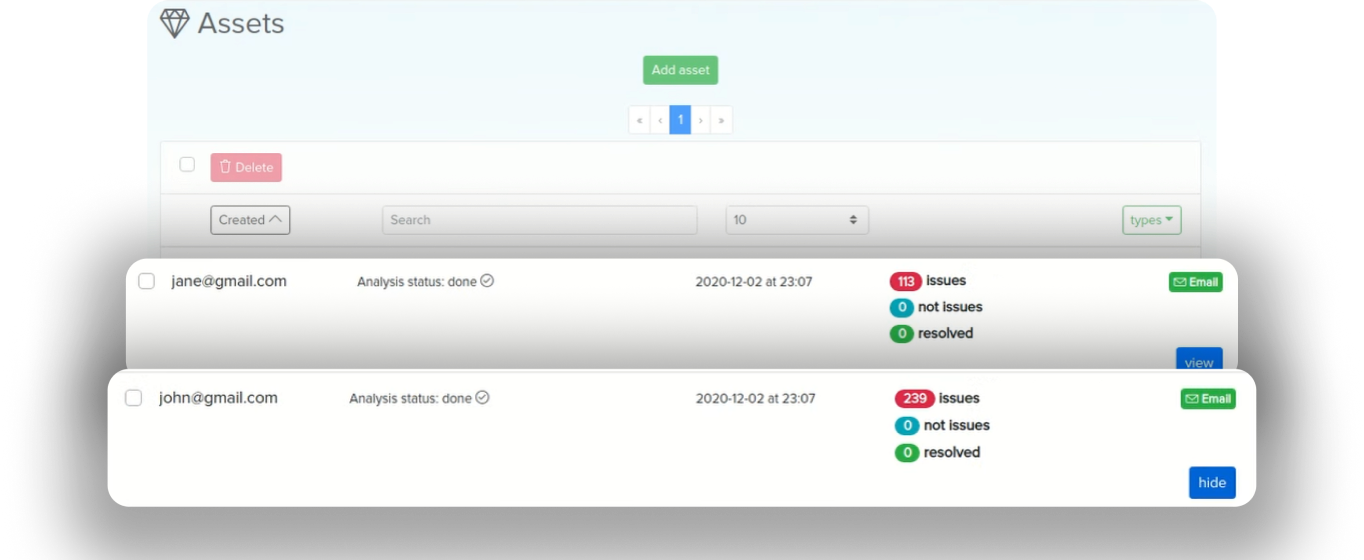
It will show you issues with your project by domain, URL, email address, or any keyword and will automatically scan your assets daily, sending you email information about any problem found.